B Understanding the Default Security Configuration
Controlling access to system resources is achieved by requiring users to authenticate at log in (authentication) and by restricting users to only the resources for which they are authorized (authorization). Security providers are configured to manage user identities, credentials, and permission grants.
This appendix contains the following sections:
Note:
Use the tasks in this section to manage privileges in the policy store provider such as the Oracle Business Intelligence Presentation Services privileges. Catalog permissions are distinct because they are maintained in the Oracle BI Presentation Catalog. See Managing Presentation Services Privileges.
About Securing Oracle Business Intelligence
You can divide securing Oracle Business Intelligence into two areas, system access security and data access security
-
System access security controls the access to the components and features that make up Oracle Business Intelligence.
System access security includes topics such as how to limit system access to authorized users, control software resources based on permission grants, and enable secure communication among components.
-
Data access security controls access to business source data and metadata used by Oracle Business Intelligence.
You can read about data access security in Metadata Repository Builder's Guide for Oracle Business Intelligence Enterprise Edition.
About the Security Framework
The Oracle Fusion Middleware security model is built upon the Oracle Fusion Middleware platform, which incorporates the Java security model.
The Java model is a role-based, declarative model that employs container-managed security where resources are protected by roles that are assigned to users. However, extensive knowledge of the Java-based architecture is unnecessary when using the Oracle Fusion Middleware Security model. By being based upon this security model, Oracle Business Intelligence can furnish uniform security and identity management across the enterprise.
Oracle Business Intelligence is installed into an Oracle WebLogic Server domain during installation, which is a logically related group of resources that are managed as a unit. During installation, an Oracle WebLogic Server domain named bi is created and Oracle Business Intelligence is installed into this domain. This name might vary depending upon the installation type performed. One instance of Oracle WebLogic Server in each domain is configured as an Administration Server. The Administration Server provides a central point for managing an Oracle WebLogic Server domain. The Administration Server hosts the Administration Console, which is a web application accessible from any supported web browser with network access to the Administration Server. Oracle Business Intelligence uses the active security realm configured for the Oracle WebLogic Server domain into which it is installed. See Oracle WebLogic Server.
See Introduction to Oracle Platform Security Services in Securing Applications with Oracle Platform Security Services. See Understanding Security for Oracle WebLogic Server and Administering Security for Oracle WebLogic Server to learn about Oracle WebLogic Server domain and security realm.
Oracle Platform Security Services
Oracle Platform Security Services (OPSS) is the underlying platform on which the Oracle Fusion Middleware security framework is built.
Oracle Platform Security Services is standards-based and complies with role-based access control (RBAC), Java Enterprise Edition (Java EE), and Oracle Application Server Java Authentication and Authorization Service (JAAS) Provider. Oracle Platform Security Services enables the shared security framework to furnish uniform security and identity management across the enterprise.
See Introduction to Oracle Platform Security Services in Securing Applications with Oracle Platform Security Services.
Oracle WebLogic Server
An Oracle WebLogic Server administration domain is a logically related group of Java components.
A domain includes a special WebLogic Server instance called the Administration Server, which is the central point from which you configure and manage all resources in the domain. You typically configure a domain to include additional WebLogic Server instances called Managed Servers. You deploy Java components, such as web applications, EJBs, and web services, and other resources to the Managed Servers and use the Administration Server for configuration and management purposes only.
Oracle WebLogic Server Administration Console and Fusion Middleware Control run in the Administration Server. Oracle WebLogic Server Administration Console is the Web-based administration console used to manage the resources in an Oracle WebLogic Server domain, including the Administration Server and Managed Servers. Fusion Middleware Control is a Web-based administration console used to manage Oracle Fusion Middleware, including the components that comprise Oracle Business Intelligence. See Oracle Business Intelligence Components in System Administrator's Guide for Oracle Business Intelligence Enterprise Edition.
Oracle Business Intelligence authentication is handled by the Oracle WebLogic Server authentication providers. An authentication provider performs the following functions:
-
Establishes the identity of users and system processes
-
Transmits identity information
Upon installation Oracle Business Intelligence is configured to use the directory server embedded in Oracle WebLogic Server as both the default authentication provider and the repository for users and groups. Alternative authentication providers can be used if desired, and managed in the Oracle WebLogic Server Administration Console. See System Requirements and Certification.
Key Security Elements
The Oracle Fusion Middleware security platform depends upon the following key elements to provide uniform security and identity management across the enterprise.
See Introduction to Oracle Platform Security Services in Securing Applications with Oracle Platform Security Services.
Oracle Business Intelligence uses these security platform elements as follows:
- Application Policy
-
See Terminology.
An application stripe defines a subset of policies in the policy store. TheOracle Business Intelligence application stripe is named obi.
- Application Role
-
For example, having the Sales Analyst application role can grant a user access to view, edit and create reports relating to a company's sales pipeline. The application role is also the container used to grant permissions and access to its members. When members are assigned to an application role, that application role becomes the container used to convey access rights to its members. For example:
-
Oracle Business Intelligence Permissions
These permission grants are defined in an application policy. After an application role is assigned to a policy, the permissions become associated with the application role through the relationship between policy and role. If groups of users have been assigned to that application role, the corresponding permissions are in turn granted to all members equally. More than one user or group can be members of the same application role.
-
Data Access Rights
Application roles can be used to control access rights to view and modify data in the repository file. Data filters can be applied to application roles to control object level permissions in the Business Model and Mapping layer and the Presentation layer. See Metadata Repository Builder's Guide for Oracle Business Intelligence Enterprise Edition.
-
Presentation Services Object-Level Access
Application roles can be used to grant access rights to reports and other objects in Oracle BI Presentation Services. See Managing Presentation Services Privileges Using Application Roles.
-
- Authentication Provider
-
See About Authentication.
Security Configuration Using the Sample Application
When operating in a development or test environment you might find it convenient to use the security configuration provided when you use the default directory server and the sample application. You then add user definitions and credentials specific to your business, and customize the existing application roles and permission grants to meet your requirements.
After the authentication, policy, and credential providers are fully configured and populated with data specific to your business, they provide all user, policy, and credential information needed by the Oracle Business Intelligence components during authentication and authorization.
Oracle BI EE security with the embedded directory server and sample application has three security providers that are integrated to ensure safe, controlled access to system and data resources. These security providers are configured during installation as follows:
-
See Default Authentication Provider.
The authentication provider is DefaultAuthenticator, which authenticates against Oracle WebLogic Server embedded directory server (identity store). The default identity store is managed using Oracle WebLogic Server Administration Console.
-
The policy store provider is the database specified during the initial BI configuration. It contains the application role definitions with their corresponding Oracle Business Intelligence permission grants, and the mapping definitions between groups and application roles. The assigning of a group to an application role serves to convey the corresponding permissions to members of the group. The default policy store provider is managed using Fusion Middleware Control.
-
Credential Store Provider
The credential store provider is the database specified during the initial BI configuration. It contains the passwords and other security-related credentials either supplied or system-generated. The default credential store is managed using Fusion Middleware Control.
The table summarizes the security providers and their initial state after installation.
| Security Provider Type | Purpose | Default Provider | Options |
|---|---|---|---|
|
Authentication provider |
Used to control authentication. |
|
Oracle Business Intelligence can be reconfigured to use different authentication providers and directory servers. See System Requirements and Certification. |
|
Policy store provider |
|
|
Oracle Business Intelligence can be configured to use Oracle Internet Directory. |
|
Credential store provider |
Trusted store for holding system passwords and other security-related credentials. The data stored here is used for connecting to external systems, opening repositories, or for SSL. |
|
Oracle Business Intelligence can be configured to use Oracle Internet Directory. |
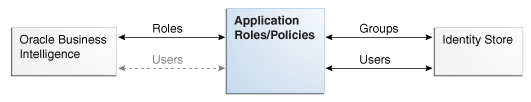
The diagram shows the relationship between Oracle Business Intelligence and the authentication and policy store providers.
Default Authentication Provider
An authentication provider accesses user and group information and is responsible for authenticating users..
An identity store contains user name, password, and group membership information and in Oracle Business Intelligence. The default security configuration authenticates against the Oracle WebLogic Server embedded directory server using an authentication provider named DefaultAuthenticator
When a user logs in to a system with a user name and password combination, Oracle WebLogic Server validates identity based on the combination provided. During this process, a Java principal is assigned to the user or group that is undergoing authentication. The principal can consist of one or more users or groups and is stored within subjects. A subject is a JAAS element used to group and hold identity information.
Upon successful authentication, each principal is signed and stored in a subject. When a program call accesses a principal stored in a subject, the default authenticator provider verifies the principal has not been altered since signing, and the principal is returned to the program making the call. For example, in the Oracle WebLogic Server default authenticator, the subject contains a principal for the user (WLSUserPrincipal) and a principal for the group (WLSGroupsPrincipals) of which the user is a member. If an authentication provider other than the installation default is configured, consult that provider's documentation because how identity information is stored might differ.
Groups and Members
Groups are logically ordered sets of users. Creating groups of users who have similar system resource access needs enables easier security management. Managing a group is more efficient than managing a large number of users individually. Groups are then assigned to application roles to grant rights. Oracle recommends that you organize your users into groups for easier maintenance.
No default groups are created during the installation of BI.
Default Users and Passwords
When you configure your BI deployment a WebLogic domain is created and populated with a single user that is specified as part of the configuration steps.
-
This user name is entered by the person performing the configuration and can be any desired name.
-
The password entered during installation can be changed later using the administration interface for the identity store provider.
-
During the configuration of the BI service instance, the WebLogic domain administrator is automatically made the owner of the service instance and made a member of the application role that confers administrative privileges such as BIServiceAdministrator or BIAdministrator.
Policy Store Provider
The policy store provider contains the Oracle Business Intelligence application-specific policies, application roles, permission grants, and membership mappings.
A policy store can is database-based or LDAP-based. The Oracle Business Intelligence default installation provides a database-based policy store.
Catalog privileges and permissions are not maintained in the policy store provider.
All Oracle Business Intelligence permissions and permission sets are provided. You cannot create additional permissions or permission sets. If you chose to configure your service instance based on the Sample Application, sample application policies and application roles are pre-configured to assign these permission sets according to the access requirements of the Oracle Business Intelligence common user types: administrator, author, and consumer.
If you chose to import an 11g upgrade bundle into your service instance, the 11g permission grants are used along with any new permission sets that were not available in 11g. You can change permission grants using Fusion Middleware Control.
Note:
You can view only permission set grants in Fusion Middleware Control. You must use WLST commands to change permission set grants.
Granting Permissions To Users Using Groups and Application Roles
The default Oracle Business Intelligence security configuration provides preconfigured permission sets that group together related permissions.
If you import the sample or starter application into your service instance the preconfigured permission sets are granted to the application roles included in the sample and starter applications. If you import the empty BAR file into your service instance, you must use WLST commands to assign permission sets to the application roles that you create. Application roles have groups as members, and permissions are inherited by users through their membership in groups. A group assigned to an application role conveys the role's permissions to all members of the group.
You grant permissions through Oracle Business Intelligence application roles by establishing the following relationships:
-
A group defines a set of users having similar system access requirements. Users are added as members of one or more groups according to the level of access required.
-
An application role defines the role a user typically performs when using Oracle Business Intelligence. The security policy in the Sample Application provides the following roles: administrator (BIServiceAdministrator), author (BIContentAuthor), and consumer (BIConsumer).
-
A group is assigned to one or more application roles that match the type of access required by each group.
-
An application policy defines Oracle Business Intelligence permissions that grant a set of access rights corresponding to each role type.
-
An application role is assigned to an application policy that grants the set of permissions required by the role type, for example administrator, author, consumer. Once configured, the application role is the grantee of the application policy.
-
Group membership can be inherited by nature of the group hierarchy. Application roles assigned to inherited groups are also inherited, and their permissions are likewise conveyed.
How the system determines a user's permissions:
-
A user enters credentials into a web browser at login. The user credentials are authenticated by the authentication provider against data contained the identity store.
-
After successful authentication, a Java subject and principal combination is issued, which is populated with the user name and the user's groups.
-
A list of the user's groups is checked against the application roles. A list is created of the application roles that are assigned to each of the user's groups.
-
A user's permission grants are determined from knowing which application roles the user is a member of. The list of groups is generated only to determine what roles a user has, and is not used for any other purpose.
For example, the ability to open a repository file in online mode from the Oracle BI Administration Tool requires the relevant permission, the oracle.bi.repository resource type with a resource scope of * and an action of manage. In the sample and starter application security policies, permission is granted by membership in the BIServiceAdministrator application role. The BIServiceAdministrator application policy contains the actual permission grant definitions. The BIServiceAdministrator application policy contains the permission set grant that includes the relevant permission. The Oracle Business Intelligence installation does not automatically create any (LDAP) groups. To convey this permission set to a user in your environment, create a suitable group such as a BIAdministrators group in the WebLogic LDAP or the Identity Store that you have configured Oracle Business Intelligence against if any, add that user to the BIServiceAdministrators group, then use EM FMW control or WLST to map the BIServiceAdministrators group to the BIServiceAdministrator application role. Every user who needs to manage a repository in online mode should be added to this group (for example, BIServiceAdministrators) instead of granting the required permission to each user individually. If a user no longer requires the manage repository permission, you then remove the user from the BIServiceAdministrators group. After removal from the BIServiceAdministrators group, the user no longer has the BIServiceAdministrator application role or the manage repository permission granted by role membership.
Users can also obtain permissions by inheriting group membership and application roles. For an example of how this is accomplished, see Permission Inheritance and Role Hierarchy.
Permission Inheritance and Role Hierarchy
InOracle Business Intelligence the members of an application role can include groups and other application roles. The result is a hierarchical application role structure where permissions can be inherited in addition to being explicitly granted.
A group that is a member of an application role is granted both the permissions of the application role and the permissions for all application roles descended from that application role. It is important when constructing an application role hierarchy that circular dependencies are not introduced.
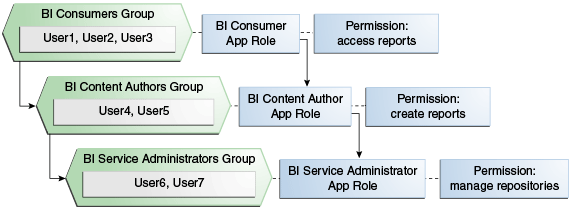
The diagram shows the relationship between application roles and how permissions are granted to members.
In the diagram, the role hierarchy grants permissions using several of the Oracle Business Intelligence default groups and application roles. In the Sample and Starter applications, the default BIServiceAdministrator role is a member the BIContentAuthor role, and BIContentAuthor role is a member of BIConsumer. The result is that members of the BIServiceAdministrator application role are granted all the permissions of the BIServiceAdministrator role, the BIContentAuthor role, and the BIConsumer role. So a user who is a member of a particular group mapped to an application role is granted both explicit permissions and any additional inherited permissions.
Note:
Groups and group hierarchies do not provide access rights to application resources. Privileges are conveyed by the permission set grants defined in an application policy. A user, group, or application role becomes a grantee of the application policy. The application policy grantee conveys the permissions and this is done by direct association such as a user, or by becoming a member of the grantee, such as a group or application role.
Common Security Tasks After Installation
The common security tasks performed after a successful Oracle Business Intelligence software installation are different according to purpose.
Common reasons to install Oracle Business Intelligence are:
-
Evaluate the product
-
Implement the product
Implementation typically involves moving through the product lifecycle of using the product in one or more of the following environments:
-
Development
-
Test
-
Production
-
Common Security Tasks to Evaluate Oracle Business Intelligence
The table contains common security tasks performed to evaluate Oracle Business Intelligence and provides links for more information.
| Task | Description | For Information |
|---|---|---|
|
Understand the Oracle Fusion Middleware security model and the Oracle Business Intelligence default security configuration. |
Familiarize yourself with the key elements of the Oracle Fusion Middleware security model and the Oracle Business Intelligence default security configuration after a successful installation. |
Introduction to Security in Oracle Business Intelligence Security Configuration Using the Sample Application Securing Applications with Oracle Platform Security Services |
|
Add users and groups to the default identity store. |
Create new User and group definitions for the embedded directory server using Oracle WebLogic Server Administration Console. |
Creating a New User in the Embedded WebLogic LDAP Server Oracle WebLogic Server Administration Console Online Help |
|
Add a new member to an application role. |
Add a new user or group as a member to an application role such as BIConsumer. |
Modifying Application Roles Using Fusion Middleware Control Securing Applications with Oracle Platform Security Services |
|
Create a new application role based on an existing application role. |
Create a new application role based on an existing application role by copying it and naming the copy. |
Creating and Deleting Application Roles Using Fusion Middleware Control Securing Applications with Oracle Platform Security Services |
Common Security Tasks to Implement Oracle Business Intelligence
The table contains common security tasks performed when you implement Oracle Business Intelligence and provides links for more information. The following tasks are performed in addition to the tasks listed in Common Security Tasks to Evaluate Oracle Business Intelligence.
| Task | Description | For Information |
|---|---|---|
|
Transition to using your enterprise directory server as the authentication provider and identity store. |
Configure your enterprise directory server to become the authentication provider and identity store. |
Configuring Oracle Business Intelligence to Use Alternative Authentication Providers |
|
Create a new application role. |
Create a new application role and make the role a grantee of an application policy. |
Creating and Deleting Application Roles Using Fusion Middleware Control |
|
Assign a group to a newly created application role. |
Assign a group to a newly created application role to convey the permission grants to group members. |
|
|
Decide whether to use SSL. |
Decide whether to use SSL communication and devise a plan to implement. |
|
|
Decide whether to use an SSO provider in your deployment. |
Decide whether to use SSO authentication and devise a plan to implement. |