1 Introduction to Security in Oracle Business Intelligence
This chapter introduces the security model, the tools used to configure security, and the road map for configuring security in Oracle Business Intelligence.
Note:
If you have installed Oracle BI Publisher on its own and you plan to use Oracle Fusion Middleware Security, then see Understanding the Security Model in Administrator's Guide for Oracle Business Intelligence Publisher.
This chapter contains the following sections:
High-Level Roadmap for Setting Up Security in Oracle Business Intelligence
Use this high level roadmap to understand typical sequence of actions to maintain security in Oracle Business Intelligence.
- Read the rest of this chapter to get an overview of security concepts, tools, and terminology.
- Decide which authentication provider to use to authenticate users.
- Set up the required users and groups.
- Set up the required application roles.
- Assign each group to an appropriate application role.
- Fine-tune the permissions that users and groups have in the Oracle BI repository.
- Fine-tune the permissions that users and groups have in the Oracle BI Presentation Catalog.
- If required, configure Single Sign-On (SSO).
- If required, configure Secure Sockets Layer (SSL).
Overview of Security in Oracle Business Intelligence
Oracle Business Intelligence 12c is tightly integrated with the Oracle Fusion Middleware Security architecture and delegates core security functionality to components of that architecture. Specifically, any Oracle Business Intelligence installation makes use of the following types of security providers:
-
An authentication provider that knows how to access information about the users and groups accessible to Oracle Business Intelligence and is responsible for authenticating users.
-
A policy store provider that provides access to application roles and application policies, which forms a core part of the security policy and determines what users can and cannot see and do in Oracle Business Intelligence.
-
A credential store provider that is responsible for storing and providing access to credentials required by Oracle Business Intelligence.
By default, an Oracle Business Intelligence installation is configured with an authentication provider that uses the Oracle WebLogic Server embedded LDAP server for user and group information. The Oracle Business Intelligence default policy store provider and credential store provider store credentials, application roles and application policies in a database.
After installing Oracle Business Intelligence you can reconfigure the domain to use alternative security providers, if desired. For example, you might want to reconfigure your installation to use an Oracle Internet Directory, Oracle Virtual Directory, Microsoft Active Directory, or another LDAP server for authentication. You might also decide to reconfigure your installation to use Oracle Internet Directory, rather than a database, to store credentials, application roles, and application policies.
Several Oracle Business Intelligence legacy authentication options are supported for backward compatibility. The best practice is to perform authentication and authorization using an identity store and authentication provider through the default security model. There are certain scenarios where this is not possible or where certain aspects of the legacy approach to authentication and authorization are required. Using alternative methods requires that your user population and groups are not held in the identity store referenced by the authentication provider configured in the Oracle WebLogic domain. Consequently, when using alternative authentication methods, several sections of this chapter are not relevant. Instead, refer to Legacy Security Administration Options. Application roles are used with alternative authentication and authorization mechanisms.
About Authentication
You manage users and groups within the authentication provider.
Each Oracle Business Intelligence 12c installation has an associated Oracle WebLogic Server domain. Oracle Business Intelligence delegates user authentication to the authentication providers configured for that domain.
The default authentication provider accesses user and group information that is stored in the LDAP server that is embedded in the Oracle WebLogic Server domain for Oracle Business Intelligence. You can use the Oracle WebLogic Server Administration Console to create and manage users and groups in the embedded LDAP server.
You might choose to configure an authentication provider for an alternative directory. You can use the Oracle WebLogic Server Administration Console to view the users and groups in the directory. However, you must continue to use the appropriate tools to make any modifications to the directory. For example, if you reconfigure Oracle Business Intelligence to use Oracle Internet Directory (OID), you can view users and groups in Oracle WebLogic Server Administration Console but you must manage them using the OID Console. Refer to the BI certification matrix for information on supported LDAP directories.
See Managing Security Using a Default Security Configuration.
To learn about Oracle WebLogic Server domains and authentication providers, see Administering Security for Oracle WebLogic Server.
About Authorization
Authorization is about ensuring users can do and see what they are authorized to do and see.
After a user has been authenticated, the next critical aspect of security is ensuring that the user can do and see what they are authorized to do and see. Authorization for Oracle Business Intelligence 12c is controlled by a security policy defined in terms of application roles.
About Application Roles
Application roles define the security policy for users.
Instead of defining the security policy in terms of users in groups in a directory server, Oracle Business Intelligence uses a role-based access control model. Security is defined in terms of application roles that are assigned to directory server groups and users. For example, application roles BIServiceAdministrator, BI Consumer, and BIContentAuthor.
Application roles represent a functional role that a user has giving the user the privileges required to perform that role. For example, the Sales Analyst application role might grant a user access to view, edit and create reports on a company's sales pipeline.
This indirection between application roles and directory server users and groups allows the administrator for Oracle Business Intelligence to define the application roles and policies without creating additional users or groups in the corporate LDAP server. Instead, the administrator defines application roles that meet the authorization requirements and assigns those roles to preexisting users and groups in the corporate LDAP server.
In addition, the indirection afforded by application roles allows moving the artifacts of a business intelligence system between development, test and production environments. No change to the security policy is needed as a result of the environment moves, and all that is required is to assign the application roles to the users and groups available in the target environment.
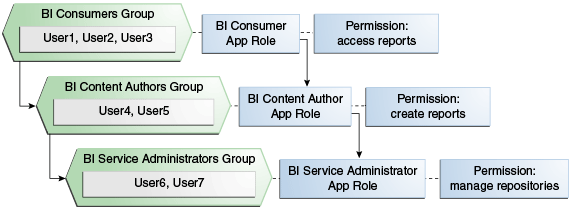
The diagram below shows an example set of groups, users, application roles, permissions, and inheritance.
The diagram shows the following:
-
The group named BIConsumers contains User1, User2, and User3. Users in the group BIConsumers are assigned the application role BIConsumer, which enables the users to view reports.
-
The group named BIContentAuthors contains User4 and User5. Users in the group BIContentAuthors are assigned the application role BIContentAuthor, which enables the users to create reports.
-
The group named BIServiceAdministrators contains User6 and User7. Users in the group BIServiceAdministrators are assigned the application role BIServiceAdministrator, which enables the users to manage repositories.
About the Security Policy
The security policy is split across Oracle BI Presentation Services, the metadata repository, and the policy store.
The security policy definition is split across the following components:
-
Oracle BI Presentation Services
Oracle BI Presentation Services defines the specific catalog objects and functionality that users can access with specific application roles. Access to functionality is defined in the Managing Privileges page for Oracle BI Presentation Services privileges and access to Oracle BI Presentation Catalog objects is defined in the Permission dialog.
-
Repository
The repository defines the metadata items in the repository that user can access with assignment to specific application roles. You can define the security policy using the Oracle BI Administration Tool.
-
Policy Store
The Policy Store defines the BI Server and Oracle BI Publisher functionality that user can access with specific application roles. In the default Oracle Business Intelligence configuration, the policy store is managed using Oracle Enterprise Manager Fusion Middleware Control or by using Oracle WebLogic Scripting Tool (WLST). See Securing Applications with Oracle Platform Security Services.
See Using Tools to Configure Security in Oracle Business Intelligence.
About Users, Groups, and Application Roles
Oracle Business Intelligence application authors can define and name the application roles and permission grants for their applications.
Oracle Business Intelligence application authors do not have to use the default application roles and permission grants that existed in previous versions. However, you can use the default application roles and permission set grants.
When you initially configure Oracle Business Intelligence, you can create the business intelligence service instance using a supplied BI Archive (BAR) file, see Installing and Configuring Oracle Business Intelligence.
The set of application roles and memberships available in your service instance depend on the BAR file that you import into the service instance. The imported security policy includes the application role definitions, the application role memberships, permission set definitions, permission definitions, permission set grants, permission grants, plus Oracle BI Presentation Services and repository security policy.
If you create the initial BI service instance using the Sample App Lite BAR file or the Starter BAR file, your initial service instance imports the sample application roles and application policies for that application.
If you create the initial service instance without using the sample or starter files, the system imports an empty BAR file into your service instance that adds a minimal set of application roles and policies to your service instance. The minimal set is only the BIServiceAdministrator application role. You can create your own security policy specific to your BI application.
Using Tools to Configure Security in Oracle Business Intelligence
To configure security in Oracle Business Intelligence use the following tools:
- Using Oracle WebLogic Server Administration Console
- Using Oracle Fusion Middleware Control
- Using Oracle BI Administration Tool
- Using Presentation Services Administration Page
See Example of Users, Groups, and Application Roles Security Setup.
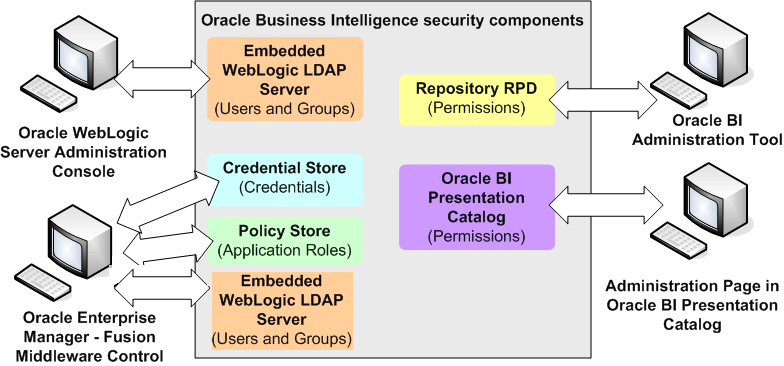
The diagram summarizes the tools used to configure security in an example installation of Oracle Business Intelligence that uses the embedded WebLogic LDAP Server.
See Managing Security Using a Default Security Configuration.
Using Oracle WebLogic Server Administration Console
You use Oracle WebLogic Server Administration Console to manage the WebLogic LDAP Server that enables you to authenticate users and groups.
Oracle WebLogic Server is automatically installed and serves as the default administration server. The Oracle WebLogic Server Administration Console is browser-based and is used, among other things, to manage the embedded directory server.
When you configure Oracle Business Intelligence, the initial security configuration uses the embedded WebLogic LDAP directory, the default authenticator, as the Identity Store. In 11g, the BI installation added some specific users and groups into the LDAP directory. In 12c, the installation does not add default BI groups into the LDAP directory. If your application expects LDAP groups such as the BIConsumers, BIContentAuthors, and BIServiceAdministrators to exist in the Identity Store, you need to add these groups manually or configure the domain to use a different Identity Store, where these groups are already provisioned after the initial BI configuration has finished.
You can launch the Oracle WebLogic Server Administration Console by entering its URL into a web browser. The default URL takes the following form: http://hostname:port_number/console. The port number is the same port number as used for the Administration server. The default port number is 9500. See Oracle WebLogic Server Administration Console Online Help.
The user name and password were supplied during the installation of Oracle Business Intelligence. If these values have since been changed, then use the current administrative user name and password combination.
If you use an alternative authentication provider such as Oracle Internet Directory instead of the default the WebLogic LDAP Server, then you must use the alternative authentication provider administration application, for example, an administration console to manage users and groups.
Using Oracle Fusion Middleware Control
Fusion Middleware Control is a web browser-based graphical user interface that enables you to administer a collection of components.
The components consist of Oracle WebLogic Server domains, one Administration Server, one or more Managed Servers, clusters, and the Fusion Middleware Control components that are installed, configured, and running in the domain. During configuration of Oracle Business Intelligence an Oracle WebLogic Server domain is created and Oracle Business Intelligence is configured into that domain. The domain is named biin Enterprise installations, and is found under the WebLogic Domain folder in the Fusion Middleware Control navigation pane.
You use Oracle Fusion Middleware Control to manage Oracle Business Intelligence security as follows:
- Manage the application roles and application policies that control access to Oracle Business Intelligence resources.
- Configure multiple authentication providers for Oracle Business Intelligence.
The port number is the number of the Administration Server, and the default port number is 9500.
See Administering Oracle Fusion Middleware.
This system-wide administration user name and password was specified during the installation process, and you can use it to log in to Oracle WebLogic Server Administration Console, Fusion Middleware Control, and Oracle Business Intelligence.
Alternatively, enter any other user name and password that has been granted the WebLogic Global Admin role.
- See Managing Application Roles and Application Policies Using Fusion Middleware Control.
- Configure Secure Sockets Level (SSL), see:
Using Oracle BI Administration Tool
You use the Oracle BI Administration Tool to configure permissions for users and application roles against objects in the metadata repository.
If you log in to the Administration Tool in online mode, then you can view all users from the WebLogic Server. If you log in to the Administration Tool in offline mode, then you can only view references to users that have previously been assigned metadata repository permissions directly in the RPD. The best practice is to assign metadata repository permissions to application roles rather than directly to users.
- Log in to the Administration Tool, and open a repository in Online Mode.
- (Optional) Select Manage, then Identity.
- In the Identity Manager dialog, double-click an application role.
- In the Application Role <Name> dialog, click Permissions.
- In the Object Permissions tab view or configure the Read and Write permissions for that application role, in relation to objects and folders in the Oracle BI Presentation Catalog.
- In the Presentation pane, expand a folder, then right-click an object to display the Presentation Table <Table name> dialog.
- Click Permissions to display the Permissions <Table name> dialog.
Process for Setting Up Security in Oracle Business Intelligence
Use this process to set up security in a new Oracle Business Intelligence installation.
After you have installed Oracle Business Intelligence, you can evaluate the installation and functionality using the sample application. Later, you can create and develop your own users, groups, and application roles iteratively to meet your business requirements.
Read:
Note:
If you are using the default SampleAppLite.rpd file in a production system, you should change the password from its installed value, using the Administration Tool. See About the SampleApp.rpd Demonstration Repository in Metadata Repository Builder's Guide for Oracle Business Intelligence Enterprise Edition.
Oracle recommends that you complete these post installation tasks in the following order:
-
Decide which authentication provider to use to authenticate users:
-
Use the default embedded WebLogic LDAP Server
Oracle does not recommend using WebLogic Embedded LDAP Server in an environment with more than 1000 users. If you require a production environment with high-availability and scalability, then you should use a directory server such as Oracle Internet Directory (OID) or a third-party directory server.
See System Requirements and Certification.
-
Use an alternative authentication provider such as Oracle Internet Directory (OID)
-
-
When using the embedded WebLogic LDAP Server as the authentication provider, do the following:
-
Set up the users that you want to deploy, see Creating a New User in the Embedded WebLogic LDAP Server.
-
Create groups and set up the groups that you want to use, see Creating a New Group in the Embedded WebLogic LDAP Server.
-
Assign your users to appropriate groups, seeAssigning a User to a Group in the Embedded WebLogic LDAP Server.
-
Assign groups of users to application roles, see Assigning a User to a New Group, and a New Application Role.
-
-
When using Oracle Internet Directory (OID) as the authentication provider, do the following:
- Configure OID as the authentication provider, see High-Level Steps for Configuring an Alternative Authentication Provider.
Use your authentication provider tools, for example, OID Console to create your users and groups as required.
- Configure OID as the authentication provider, see High-Level Steps for Configuring an Alternative Authentication Provider.
-
Set up the application roles that you want to deploy, see Creating and Deleting Application Roles Using Fusion Middleware Control.
For example, you might use BIConsumer, BIContentAuthor, and BIServiceAdministrator, or you might create your own application roles.
-
Assign each group to an appropriate application role, see Assigning a Group to an Application Role.
-
Use the Administration Tool to update the permissions that users and groups have in the Oracle BI repository, see Managing Metadata Repository Privileges Using the Oracle BI Administration.
For example, you can enable an application role, BISuperConsumer, to create analyses. You use the Administration Tool to change the access from Read to Read/Write access to the specific subject area.
-
To change the permissions for users and groups have in the Presentation Services, see Managing Presentation Services Privileges Using Application Roles.
For example, you can prevent the application role, BISuperConsumer, from viewing scorecards, so you use Presentation Services Administration page to change the Scorecard\View Scorecard privileges for BISuperConsumer from Granted to Denied.
-
If you want to deploy Single Sign-On, see Enabling SSO Authentication.
-
To deploy secure sockets layer (SSL), see Configuring SSL in Oracle Business Intelligence. Oracle Business Intelligence is installed with SSL disabled.
Terminology
The following terms are used throughout this guide:
- Application Policy
-
Oracle Business Intelligence permissions are granted by its application roles. In the default security configuration, each role conveys a predefined set of permissions. An application policy is a collection of Java EE and JAAS policies that are applicable to a specific application. The application policy is the mechanism that defines the permissions each application role grants. Permission grants are managed in the application policy corresponding to an application role.
- Application Role
-
Represents a role a user has when using Oracle Business Intelligence. Is also the container used by Oracle Business Intelligence to grant permissions to members of a role. Application roles are managed in the policy store provider.
- Authentication
-
The process of verifying identity by confirming the credentials presented during log in.
- Authentication Provider
-
A security provider used to access user and group information and responsible for authenticating users. Oracle Business Intelligence default authentication provider is Oracle WebLogic Server embedded directory server and is named DefaultAuthenticator.
- Authorization
-
The process of granting an authenticated user access to a resource in accordance to their assigned privileges.
- Catalog Groups
-
Catalog groups are not supported in Oracle Business Intelligence Release 12.2.1.1 and higher. See Oracle Fusion Middleware Migration Guide for Oracle Business Intelligence.
- Catalog Permissions
-
These rights grant access to objects that are stored in the Oracle BI Presentation Catalog. The rights are stored in the catalog and managed by Presentation Services.
- Catalog Privileges
-
These rights grant access to features of the Oracle BI Presentation Catalog. The rights are stored in the catalog and managed by Oracle BI Presentation Services. These privileges are either granted or denied.
- Credential Store
-
An Oracle Business Intelligence credential store is a file used to securely store system credentials used by the software components. This file is automatically replicated across all machines in the installation.
- Credential Store Provider
-
The credential store is used to store and manage credentials securely that are used internally between Oracle Business Intelligence components. For example, SSL certificates are stored here.
- Encryption
-
A process that enables confidential communication by converting plain text information (data) to unreadable text which can be read-only with the use of a key. Secure Sockets Layer (SSL) enables secure communication over TCP/IP networks, such as web applications communicating through the Internet.
- Impersonation
-
Impersonation is a feature used by Oracle Business Intelligence components to establish a session on behalf of a user without employing the user's password. For example, impersonation is used when Oracle BI Scheduler executes an Agent.
- Oracle WebLogic Server Domain
-
A logically related group of Oracle WebLogic Server resources that includes an instance known as the Administration Server. Domain resources are configured and managed in the Oracle WebLogic Server Administration Console, see Oracle WebLogic Server.
- Identity Store
-
An identity store contains user name, password, and group membership information. In Oracle Business Intelligence, the identity store is typically a directory server and is what an authentication provider accesses during the authentication process. For example, when a user name and password combination is entered at log in, the authentication provider searches the identity store to verify the credentials provided. Oracle Business Intelligence can be re-configured to use alternative identity stores, see System Requirements and Certification.
- Permission Set
-
Represents a set of permissions.
- Policy Store Provider
-
The policy store is the repository of system and application-specific policies. It holds the mapping definitions between the default Oracle Business Intelligence application roles, permissions, users and groups all configured as part of installation. Oracle Business Intelligence permissions are granted by assigning users and groups from the identity store to application roles and permission grants located in the policy store.
- Policy Store
-
Contains the definition of application roles, application policies, and the members assigned such as users, groups, and application roles to application roles. The default policy store is a file that is automatically replicated across all machines in an Oracle Business Intelligence installation. A policy store can be database-based or LDAP-based.
- Secure Sockets Layer (SSL)
-
Provides secure communication links. Depending upon the options selected, SSL might provide a combination of encryption, authentication, and repudiation. For HTTP based links the secured protocol is known as HTTPS.
- Security Policy
-
The security policy defines the collective group of access rights to Oracle Business Intelligence resources that an individual user or a particular application role have been granted. Where the access rights are controlled is determined by which Oracle Business Intelligence component is responsible for managing the resource being requested. A user's security policy is the combination of permission and privilege grants governed by the following elements:
- Oracle BI Presentation Catalog:
Defines which Oracle BI Presentation Catalog objects and Oracle BI Presentation Services functionality can be accessed by users. Access to this functionality is managed in Oracle Business Intelligence user interface. These permissions and privileges can be granted to individual users or by membership in corresponding application roles.
- Repository File:
Defines access to the specified metadata within the repository file. Access to this functionality is managed in the Oracle BI Administration Tool. These permissions and privileges can be granted to individual users or by membership in corresponding application roles.
- Policy Store:
Defines which Oracle Business Intelligence, Oracle BI Publisher, and Oracle Real-Time Decisions functionality can be accessed. Access to this functionality is managed in Oracle Enterprise Manager Fusion Middleware Control. These permissions and privileges can be granted to individual users or by membership in corresponding application roles.
- Oracle BI Presentation Catalog:
- Security Realm
-
During deployment an Oracle WebLogic Server domain is created and Oracle Business Intelligence is deployed into that domain. Security for an Oracle WebLogic Server domain is managed in its security realm. A security realm acts as a scoping mechanism. Each security realm consists of a set of configured security providers, users, groups, security roles, and security policies. Only one security realm can be active for the domain. Oracle Business Intelligence authentication is performed by the authentication provider configured for the default security realm for the WebLogic Server domain in which it is installed. Oracle WebLogic Server Administration Console is the Administration Tool for managing an Oracle WebLogic Server domain.
- Single Sign-On
-
A method of authorization enabling a user to authenticate once and gain access to multiple software application during a single browser session.
- Users and Groups
-
A user is an entity that can be authenticated. A user can be a person, such as an application user, or a software entity, such as a client application. Every user is given a unique identifier within in the identity store.
Groups are organized collections of users that have something in common. A group is a static identifier that is assigned by a system administrator. Users organized into groups facilitate efficient security management. There are two types of groups: an LDAP group and a Catalog group. A Catalog group was used to support the existing user base in Presentation Services to grant privileges in the Oracle Business Intelligence user interface. Catalog groups are obsolete as of 12.2.1.1.