| Oracle® Application Server Upgrade and Compatibility Guide 10g (10.1.4.0.1) for UNIX Part Number B28188-01 |
|
|
View PDF |
| Oracle® Application Server Upgrade and Compatibility Guide 10g (10.1.4.0.1) for UNIX Part Number B28188-01 |
|
|
View PDF |
This chapter describes considerations, restrictions, and recommended procedures for upgrading an Oracle Application Server environment that has been configured for high availability.
This chapter contains the following sections:
Summary of High Availability Upgrade Options, Restrictions, and Prerequisites
Transforming a Distributed 10g (9.0.4) Rack-Mounted Identity Management Environment
Upgrading an OracleAS Cluster (Identity Management) 10g Release 2 (10.1.2) Colocated Configuration
Upgrading an OracleAS Cluster (Identity Management) 10g Release 2 (10.1.2) Distributed Configuration
Oracle Application Server 10g (9.0.4) introduced high availability configurations that you could install as part of the Oracle Application Server installation procedure. These configurations were also available as part of 10g Release 2 (10.1.2.0.0), 10g Release 2 (10.1.2.1.0), and 10g Release 2 (10.1.2.0.2).
Table B-1 shows the upgrade paths supported for the high availability configurations.
Table B-1 Summary of the High Availability Upgrade Options
| Existing Configuration | Upgrade Path | More Information |
|---|---|---|
|
Oracle Application Server Cold Failover Clusters |
Upgrade to Oracle Application Server Cold Failover Clusters for 10g (10.1.4.0.1). |
Section B.2, "Upgrading an OracleAS Cold Failover Cluster Infrastructure" |
|
10g (9.0.4) Rack-Mounted Identity Management |
Transform the environment into a 10g (10.1.4.0.1) OracleAS Cluster (Identity Management) environment. |
Section B.3, "Transforming 10g (9.0.4) Rack-Mounted Identity Management" |
|
10g Release 2 (10.1.2) colocated OracleAS Cluster (Identity Management) |
Upgrade the cluster to OracleAS Cluster (Identity Management) 10g (10.1.4.0.1) |
|
|
10g Release 2 (10.1.2) Distributed OracleAS Cluster (Identity Management) |
Upgrade the distributed Oracle homes to OracleAS Cluster (Identity Management) 10g (10.1.4.0.1) |
|
|
Disaster Recovery |
Upgrade the production site and the standby site separately. |
"Oracle Application Server Disaster Recovery" in the Oracle Application Server High Availability Guide |
The procedures provided in this chapter assume that you used the Oracle Application Server 10g (9.0.4) or 10g Release 2 (10.1.2) installation guide (depending upon the upgrade options you select) to install and configure your high availability configuration and that you have met all of the prerequisites described in the 10g (9.0.4) or 10g Release 2 (10.1.2) installation guide.
For example, these procedures assume you have already installed and configured clusterware such as Sun Cluster, VERITAS Cluster Server, or Fujitsu-Siemens PrimeCluster. For the official list of certified clusterware, visit the Certify section of OracleMetaLink:
http://metalink.oracle.com
To check that the clusterware is running, use the command appropriate for your clusterware. For example, if you are running Sun Cluster, use the scstat command to get the status of the nodes in the cluster.
These procedures also assume you are using the seed database that was installed automatically with the 10g (9.0.4) or 10g Release 2 (10.1.2) installation procedure or with the OracleAS RepCA.
|
See Also: The Oracle Application Server 10g (9.0.4) installation guide for your platform, which is available as part of the platform-specific documentation library on the Oracle Technology Network:http://www.oracle.com/technology/documentation/appserver10g.html The Oracle Application Server 10g Release 2 (10.1.2) installation guide for your platform, which is available as part of the platform-specific documentation library on the Oracle Technology Network: http://www.oracle.com/technology/documentation/appserver101402.html |
To upgrade a 10g (9.0.4) OracleAS Cold Failover Cluster Infrastructure installation:
If vendor clusterware agents or packages are being utilized to automatically monitor and manage the OracleAS Cold Failover Cluster environment, these should be stopped before you perform the 10g (10.1.4.0.1) upgrade.
In addition, to re-enable vendor cluster agents or packages after the upgrade has been completed, verify that certification has been provided by the appropriate vendor for the 10g (10.1.4.0.1) OracleAS Cold Failover Cluster environment.
Make sure that the OracleAS Metadata Repository database and database listener are up and running.
Log in to the computer on which the 10g (9.0.4) OracleAS Cold Failover Cluster is installed, as the same operating system user that performed the 10g (9.0.4) installation.
Make sure the Oracle Internet Directory server is up and running.
To verify that Oracle Internet Directory is running, enter one of the following commands.
|
Note: You may have to temporarily set the ORACLE_HOME environment variable to the Oracle Internet Directory Oracle home before running theldapbind command.
After you verify that the Oracle Internet Directory is running, you must then make sure the ORACLE_HOME environment variable is not defined before you start the 10g (10.1.4.0.1) installer, as directed in Step 5. |
If you are running Oracle Internet Directory on a non-secure port:
SOURCE_ORACLE_HOME/bin/ldapbind -p Non-SSL_port
If you are running Oracle Internet Directory on a secure port:
SOURCE_ORACLE_HOME/bin/ldapbind -p SSL_port -U 1
These commands should return a "bind successful" message.
|
See Also: "Syntax for LDIF and Command-Line Tools" in the Oracle Internet Directory Administrator's Guide for more information about theldapbind utility |
Be sure to set the environment variables, as defined in the section "Environment Variables" in the "Requirements" chapter of the Oracle Application Server Installation Guide.
In particular, be sure to set following variables so they do not reference any Oracle home directories:
In addition, be sure the following environment variables are not set:
Mount the Oracle Application Server 10g (10.1.4.0.1) CD–ROM and start the installer.
|
See Also: Oracle Application Server Installation Guide for detailed instructions about starting Oracle Universal Installer on your platform |
Refer to Table B-2 for information on the options you should select on each screen.
After the End of Installation screen appears, exit Oracle Universal Installer and then verify that Oracle Internet Directory and Oracle Application Server Single Sign-On are functioning and accessible in the new 10g (10.1.4.0.1) Oracle home.
|
See Also: Oracle Application Server Administrator's Guide, Chapter 1, "Accessing the Single Sign-On Server" |
Review Chapter 9, "Component-Specific Post-Upgrade Procedures" and perform any post-upgrade tasks that are required for your configuration.
The following step is required only if you meet both of these requirements:
You plan to use the Automatic Storage Management (ASM) feature of Oracle Database 10g for the OracleAS Metadata Repository.
Your computer does not have an existing Oracle Database 10g.
If you meet these requirements, you need to configure the CSS daemon on the other node. The CSS daemon synchronizes ASM instances with the database instances that use the ASM instances for database file storage.
Stop all the processes in the Oracle Application Server Cold Failover Clusters (Infrastructure) home.
Stop the CSS daemon. You can do this by running the following command as root.
# /etc/init.d/init.cssd stop
Fail over the IP and the disk to the other node.
On the other node, run the following command as root:
# $ORACLE_HOME/root.sh
ORACLE_HOME is where you installed the Oracle Application Server Cold Failover Clusters (Infrastructure).
After you upgrade OracleAS Identity Management in a colocated Infrastructure, refer to the following sections for information about post-upgrade tasks you should consider performing to help you manage and maintain the upgraded database:
If you have installed or upgraded any 10g Release 2 (10.1.2) middle tiers that use the OracleAS Metadata Repository for components such as OracleAS Portal, OracleAS Wireless, or Oracle Application Server Certificate Authority, then run the Metadata Repository Upgrade Assistant (MRUA) to upgrade the component schemas in the OracleAS Metadata Repository.
For instructions on running MRUA, see Chapter 8, "Using MRUA to Upgrade the OracleAS Metadata Repository".
Complete the Oracle Application Server Cold Failover Clusters Post-Installation instructions described in "Post-Installation Steps for OracleAS Cold Failover Cluster" in the Oracle Application Server Installation Guide.
Table B-2 Summary of the Oracle Universal Installer Screens During the OracleAS Cold Failover Cluster Infrastructure Upgrade
| Screen | Description and Recommended Options to Select |
|---|---|
|
Welcome |
Welcomes you to Oracle Universal Installer and the Oracle Application Server installation procedure. |
|
Specify File Locations |
Enter a name and path for the new Oracle home. This new Oracle home will be the destination Oracle home for your Oracle Application Server 10g (10.1.4.0.1) upgrade. Notes:
|
|
Specify Hardware Cluster Installation Mode |
This screen appears only if you have Oracle Cluster Ready Services installed. It is okay if you do not see this screen; Oracle Cluster Ready Services is not required for OracleAS Cold Failover Cluster. Select Local Installation because you are installing OracleAS Infrastructure on the shared storage. Click Next. |
|
Select a Product to Install |
Select OracleAS Infrastructure 10g. If multiple languages are used in the OracleAS Infrastructure you are upgrading, then click Product Languages. |
|
Language Selection |
The screen appears only if you clicked Product Languages on the Select a Product to Install screen. If multiple languages are used in the OracleAS Infrastructure you are upgrading, select those languages. If you are not sure which languages were installed, but want languages other than English, click the double arrow button (>>) to select all languages. |
|
Select Installation Type |
Select Identity Management and OracleAS Metadata Repository. Note: It is very important that you select the same installation type that is used in the Oracle home you are upgrading. |
|
Upgrade Existing Infrastructure |
This screen appears when Oracle Universal Installer detects an existing Oracle Application Server installation of the same type as the one you selected on the Select Installation Type screen. Select the option to upgrade an existing OracleAS Infrastructure, and then select the Oracle home you want to upgrade from the drop-down list. (If there is only one Infrastructure of the selected time on the computer, then the drop-down list is inactive.) |
|
Specify Login for Oracle Internet Directory |
Enter the Oracle Internet Directory superuser distinguished name (DN) in the Username field. The superuser DN Enter the password for the superuser DN in the Password field. |
|
Specify Infrastructure Database Connection |
Enter |
|
Warning dialog box |
This dialog box warns you that all the clients of the OracleAS Metadata Repository database must now be stopped. Oracle Universal Installer will automatically stop any clients within the current Oracle home.Foot 1 However, you must manually stop any database clients and OracleAS Metadata Repository clients that reside in another Oracle home. Clients of the OracleAS Metadata Repository include:
Within each middle tier that uses this OracleAS Metadata Repository, you must be sure to stop all components, including Oracle HTTP Server and OracleAS Web Cache. For more information, see the chapter "Starting and Stopping " in the Oracle Application Server Administrator's Guide. |
|
Database Listener Warning Dialog Box |
If a database listener is running on the host, a warning dialog box displays. Review the dialog box determine whether or not you need to stop the listener manually. For more information, see Section 6.3.1.3, "Stopping the Database Listener When Prompted During the OracleAS Identity Management Upgrade". |
|
Specify Instance Name and ias_admin Password |
Enter a name for the new Oracle Application Server 10g (10.1.4.0.1) instance and a password for the You use the In general, the minimum length of the For more information, see the section "The ias_admin User and Restrictions on its Password" in the Oracle Application Server Installation Guide. |
|
Summary |
Use this screen to confirm the choices you've made. Click Install to begin upgrading to the new 10g (10.1.4.0.1) Oracle home. A dialog box appears when the copying is complete. This dialog box prompts you to run a configuration script as the root user. Follow the instructions in the dialog box and click OK when script is finished. |
|
The Configuration Assistants |
After the initial software is installed, a set of configuration assistants automatically set up the components in the new 10g (10.1.4.0.1) Oracle home. Use this screen to follow the progress of each assistant and to identify any problems during this phase of the installation. Notes:
|
|
End of Installation |
When the installation and upgrade is complete, this screen provides important details about the 10g (10.1.4.0.1) Oracle home, such as the URL for the Application Server Control Console and the location of the After you review the information on this screen, you can exit Oracle Universal Installer and proceed to the post-upgrade tasks. |
Footnote 1 You can access a log of the automated shutdown procedure executed by Oracle Universal Installer in the following directory: ORACLE_HOME/cfgtoollogs/shutdownprocesses.log
The following sections describe how to transform a 10g (9.0.4) Rack-Mounted Identity Management environment to OracleAS Cluster (Identity Management):
About Rack-Mounted Identity Management and OracleAS Cluster (Identity Management)
Task 1: Review the Requirements for Transforming the 10g (9.0.4) Rackmounted Identity Management
Task 2: Upgrade the Database That Hosts the OracleAS Metadata Repository
Task 3: If Necessary, Upgrade Any Middle Tiers That Use the OracleAS Metadata Repository
Task 4: Upgrade the First OracleAS Identity Management Instance
Task 6: Install Subsequent OracleAS Cluster (Identity Management) Instances
Task 7: Verify the Upgrade and Decommission the 10g (9.0.4) Oracle Homes
Following the release of Oracle Application Server 10g (9.0.4), a procedure was released for deploying multiple Identity Management instances against one Infrastructure Metadata Repository. This procedure was released in the form of a whitepaper titled Highly Available Identity Management example - Rack Mounted Identity Management and it was made available to customers on the Oracle Technology Network (OTN) at:
http://www.oracle.com/technology/products/ias/hi_av/index.html
Note that the link to the whitepaper on OTN might actually be shown as Highly Available Identity Management Deployment Example - Multi-box Identity Management.
Starting with the release of Oracle Application Server 10g Release 2 (10.1.2), an "out-of-the-box" Multiple Identity Management solution is now available. This configuration is known as OracleAS Cluster (Identity Management).
|
See Also: "Installing in High Availability Environments: OracleAS Cluster (Identity Management)" in the Oracle Application Server Installation Guide |
The following sections provide step-by-step instructions for customers who wish to upgrade their 10g (9.0.4) Multiple Identity Management deployment to an OracleAS Clusters (Identity Management) 10g (10.1.4.0.1) deployment.
The testing and steps provided in this document are based upon an OracleAS Identity Management implementation deployed on RedHat Linux 3.0. The steps provided in this document, however, apply to any Unix platform.
The following sections describe the requirements you must meet in order to transform your highly available environment from 10g (9.0.4) Rack-Mounted Identity Management to OracleAS Cluster (Identity Management):
Before you use this procedure, you must consider the following configuration requirements:
You must have followed the exact set of steps outlined in the paper Highly Available Identity Management example - Rack Mounted Identity Management
The Identity Management instances you are upgrading must be 10g (9.0.4) intances; previous releases of OracleAS are not supported for this configuration.
The Metadata Repository must have been created in an Oracle9i Release 2 (9.2.0.1) or greater database, using the 10g (9.0.4) OracleAS RepCA (MRCA).
OracleAS Identity Management consists of components that can also be installed separately:
Oracle Internet Directory (OID)
OracleAS Single Sign-On (SSO)
Oracle Delegated Administration Services (DAS)
Oracle Directory Integration Platform (DIP)
This procedure does not include support for Oracle Application Server Certificate Authority (OCA).
In this procedure, the primary focus is on installations where all Identity management components are installed in one Oracle home. This is known as a colocated OracleAS Infrastructure, which includes Oracle Internet Directory, Oracle Delegated Administration Services, and OracleAS Single Sign-On, all installed within the same Oracle home.
To upgrade a distributed OracleAS Identity Management configuration where the Identity Management components are separated into two tiers, see Section B.4, "Transforming a Distributed 10g (9.0.4) Rack-Mounted Identity Management Environment". Such a configuration might be required, for example, where an organization needs the OracleAS Single Sign-On and Oracle Delegated Administration Services components running in a the DMZ and the Oracle Internet Directory running on the internal network inside the firewall.
This procedure assumes the database that hosts the OracleAS Metadata Repository is an Oracle Real Application Clusters (RAC) Database. Specifically, the procedure described in this section was tested on a two-node RAC environment. However, it is assumed that this procedure also applies to:
A single-instance database
A Real Application Clusters database consisting of more than two nodes
The requirement for Real Application Clusters is a shared-storage configuration. The implementation of the shared volume is vendor-specific. The procedures in this section should be applicable to all Operating systems and clusters but were developed and tested in a Linux environment. Specifically, the following shared storage options are supported:
Raw devices
Cluster filesystem (for example, OCFS on Linux)
Network filesystem (for example, supported NAS devices)
Although cluster and volume management software is vendor-specific, the steps and considerations provided in this section apply specifically to customers wishing to optionally implement Oracle's Automated Storage Management (ASM).
Before you begin this transformation procedure, take a complete, full software backup of everything in the Oracle Home and related directories for the OracleAS Metadata Repository and the OracleAS Identity Management instances.
In addition, shut down all processes and perform a full cold database backup of the middle tiers and Infrastructure Oracle homes.
Before you can upgrade to OracleAS Cluster (Identity Management), you must upgrade the database that hosts the OracleAS Metadata Repository to a supported database.
For detailed instructions on upgrading the database that hosts the OracleAS Metadata Repository, see Chapter 6, "Upgrading the Database That Hosts the OracleAS Metadata Repository".
|
Note: When applying database patchsets, be sure to carefully review the patchset README for your specific platform. The instructions for installing patchsets can vary significantly from platform to platform. For example, some platforms, such as Linux, might require you to install a specific version of Oracle Universal Installer before proceeding with the patchset installation. |
There are certain upgrade scenarios where you might have to upgrade any 10g (9.0.4) middle tiers in your Oracle Application Server environment to 10g Release 2 (10.1.2).
For more information, refer to Chapter 5, "Upgrading 10g (9.0.4) Middle Tiers to 10g Release 2 (10.1.2)".
After the database that hosts the OracleAS Metadata Repository has been upgraded to a supported version, and after any middle tiers have been upgraded to 10g Release 2 (10.1.2), you can now upgrade the first OracleAS Identity Management Oracle home in the Rack-Mounted Identity Management configuration.
When you upgrade the first OracleAS Identity Management Oracle home, you also upgrade the OracleAS Identity Management schemas in the OracleAS Metadata Repository.
Note that in an OracleAS Cluster (Identity Management), the Identity Management instances are clustered together in a Distributed Configuration Management (DCM) Cluster. This ensures synchronization between the configurations of the different Identity Management components on all of the Identity Management instances.
To upgrade the first OracleAS Identity Management Oracle home, use the following steps.
Make sure that the other OracleAS Identity Management Instances in the Rack-Mounted Identity Management environment are down.
Only the OracleAS Identity Management instance that you are upgrading first should be up and running. If necessary, shut down the other OracleAS Identity Management instances.
Configure the Load Balancer to direct traffic only to the OracleAS Identity Management instance you are about to upgrade
All Requests should be directed only to the OracleAS Identity Management instance you are about to upgrade. The other OracleAS Identity Management instances in the Rack-Mounted Identity Management environment should be shut down.
Use the Oracle Application Server 10g (10.1.4.0.1) installation procedure to upgrade the OracleAS Identity Management instance.
Refer to Chapter 7, "Using Oracle Universal Installer to Upgrade Oracle Identity Management" for complete instructions on upgrading the first OracleAS Identity Management Oracle home.
Perform any post-upgrade procedures that apply to your OracleAS Identity Management environment.
Refer to Chapter 9, "Component-Specific Post-Upgrade Procedures" for more information.
Perform the steps described in Section B.5.4.3.3, "Configuration Steps When Oracle HTTP Server and the Load Balancer are Not Using SSL".
Create a Distributed Configuration Management (DCM) cluster that the other OracleAS Identity Management instances can join:
Enter the DCM command-line shell:
ORACLE_HOME/dcm/bin/dcmctl shell
Create a new Cluster:
DCM> createcluster -cl IMcluster
In this example, IMCluster is the name you assign to the cluster.
Join the DCM cluster as the first instance:
DCM> joincluster -cl IMcluster
At this point the instance will be stopped.
Restart the instance:
opmnctl startall
A new cluster has now been created with the upgraded IM instance as its sole member.
Perform the steps described in Section B.5.4.4, "Task 4d: Finish the Upgrade of the First OracleAS Identity Management Instance".
Make sure that the OracleAS Identity Management instance (including Oracle Internet Directory) that you upgraded in Section B.3.5, "Task 4: Upgrade the First OracleAS Identity Management Instance" is up and running.
If it is not running, start the Identity Management instance (including Oracle Internet Directory) as follows:
ORACLE_HOME/opmn/bin/opmnctl startall
Upgrade the Metadata Repository in the newly upgraded database as described in Chapter 8, "Using MRUA to Upgrade the OracleAS Metadata Repository", with the following exception:
On the MRUA command line, enter the address of the load balancer in place of the oid_host and oid_ssl_port arguments.
Note that the values you enter for the -oid_host argument and -oid_ssl_port arguments must match the value of the corresponding properties defined in following configuration file in the Identity Management Oracle home:
IDENTITY_MANAGEMENT_HOME/config/ias.properties
For example:
OIDhost=sys42.acme.com OIDsslport=636
When MRUA finishes processing, verify that the schemas have been upgraded, as described in Section 8.3, "Task 3: Verify the Success of the OracleAS Metadata Repository Upgrade".
Complete the OracleAS Metadata Repository upgrade using the instructions in the section, Section 9.4, "Task 4: Perform OracleAS Portal Post-Upgrade Steps".
After you upgrade the first OracleAS Identity Management instance in the cluster, and after you upgrade the OracleAS Metadata Repository, you can then install the additional OracleAS Identity Management instances in the OracleAS Cluster (Identity Management):
Make sure that the Oracle Internet Directory is up and running on the first OracleAS Identity Management instance.
Make sure that the OracleAS Metadata Repository database and listener are up and running.
Make sure that the Load Balancer is configured to direct traffic only to the first Identity Management instance.
Install the new 10g (10.1.4.0.1) OracleAS Identity Management Oracle home by following the instructions in the section "Installing OracleAS Cluster (Identity Management) on Subsequent Nodes," in the Oracle Application Server Installation Guide.
Reconfigure Load Balancer and test the installation.
After a successful installation of the subsequent OracleAS Identity Management Oracle home, configure the Load Balancer to route requests to the new instance.
Repeat this procedure for any additional and subsequent OracleAS Identity Management installations that will be part of the cluster.
After you have upgraded the first Oracle Identity Management instance in the cluster and you have added the remaining cluster members, you can then verify that the upgrade was successful and then decommission the 10g (9.0.4) Oracle homes.
For more information, refer to Chapter 10, "Verifying the Upgrade and Decommissioning the Source Oracle Homes".
In a distributed Rack-Mounted Identity Management environment, the Oracle Internet Directory is installed in a separate Oracle home from the other OracleAS Identity Management components.
The procedure for transforming distributed Rack-Mounted Identity Management components is the same as that for transforming a colocated Rack-Mounted Identity Management installation, except for the following exceptions. The following steps summarize the distributed transformation procedure:
Table B-3 Summary of the Steps for Transforming a Distributed Rack-Mounted Identity Management Environment to OracleAS Cluster (Identity Management)
| Task No. | Description | More Information |
|---|---|---|
|
1 |
Review the requirements for transforming Rack-Mounted Identity Management. |
|
|
2 |
Upgrade the database that hosts the OracleAS Metadata Repository. |
Section B.3.3, "Task 2: Upgrade the Database That Hosts the OracleAS Metadata Repository" |
|
3 |
If necessary, upgrade any 10g (9.0.4) middle tiers. |
|
|
4 |
Upgrade the first Oracle Internet Directory Oracle home. |
Steps 1 through 4 of Section B.3.5, "Task 4: Upgrade the First OracleAS Identity Management Instance" |
|
5 |
Upgrade the first OracleAS Single Sign-On Oracle home. |
Steps 1 through 4 of Section B.6.5, "Task 5: Upgrade the First OracleAS Single Sign-On Oracle Home" |
|
6 |
Create a Distributed Configuration Management (DCM) cluster for the OracleAS Single Sign-On instances. |
Step 6 of Section B.3.5, "Task 4: Upgrade the First OracleAS Identity Management Instance". |
|
7 |
Configure Oracle HTTP Server and OracleAS Single Sign-On in the OracleAS Single Sign-On Oracle home. |
|
|
8 |
Finish the upgrade of the first OracleAS Single Sign-On instance. |
Section B.5.4.4, "Task 4d: Finish the Upgrade of the First OracleAS Identity Management Instance" |
|
9 |
Use the Metadata Repository Upgrade Assistant to Upgrade the Component Schemas in the OracleAS Metadata Repository |
|
|
10 |
Install Subsequent OracleAS Cluster (Identity Management) Instances |
Section B.3.7, "Task 6: Install Subsequent OracleAS Cluster (Identity Management) Instances" |
|
11 |
Verify the Upgrade and Decommission the 10g (9.0.4) Oracle Homes |
Section B.3.8, "Task 7: Verify the Upgrade and Decommission the 10g (9.0.4) Oracle Homes" |
A colocated OracleAS Identity Management installation includes all the OracleAS Identity Management components in each Oracle home. Compare the procedures in this section with those in Section B.6, "Upgrading an OracleAS Cluster (Identity Management) 10g Release 2 (10.1.2) Distributed Configuration".
The following sections describe how to upgrade a colocated 10g Release 2 (10.1.2) OracleAS Cluster (Identity Management) environment to 10g (10.1.4.0.1).
Task 1: Review the OracleAS Cluster (Identity Management) Upgrade Requirements
Task 2: Upgrade the Database That Hosts the OracleAS Metadata Repository
Task 3: If Necessary, Upgrade any 10g (9.0.4) Middle Tiers to 10g Release 2 (10.1.2.0.2)
Task 4: Upgrade the First OracleAS Identity Management Instance
Task 6: Installing Subsequent OracleAS Cluster (Identity Management) Instances
Task 7: Verify the Upgrade and Decommission the 10g Release 2 (10.1.2) Oracle Homes
The following sections describe the requirements you must meet in order to upgrade your 10g Release 2 (10.1.2) colocated OracleAS Cluster (Identity Management) configuration to OracleAS Cluster (Identity Management) 10g (10.1.4.0.1):
Before you use this procedure, note that the Identity Management instances you are upgrading must be 10g Release 2 (10.1.2) intances that were installed using the procedures documented in "Installing in High Availability Environments: OracleAS Cluster (Identity Management)" in the 10g Release 2 (10.1.2) Oracle Application Server Installation Guide.
OracleAS Identity Management consists of components that can also be installed separately:
Oracle Internet Directory (OID)
OracleAS Single Sign-On (SSO)
Oracle Delegated Administration Services (DAS)
Oracle Directory Integration Platform (DIP)
This procedure does not include support for Oracle Application Server Certificate Authority (OCA).
This procedure describes how to upgrade installations where all Identity management components are installed in each Oracle home. This is known as a colocated OracleAS Infrastructure, where Oracle Internet Directory, Oracle Delegated Administration Services, Oracle Directory Integration Platform, and OracleAS Single Sign-On are installed within the same Oracle home.
|
See Also: Section B.6, "Upgrading an OracleAS Cluster (Identity Management) 10g Release 2 (10.1.2) Distributed Configuration" for information about upgrading a distributed OracleAS Identity Management configuration. |
Figure B-1 shows a typical colocated OracleAS Cluster (Identity Management) 10g Release 2 (10.1.2) environment.
Figure B-1 10g Release 2 (10.1.2) Colocated OracleAS Cluster (Identity Management) Upgrade Starting Point
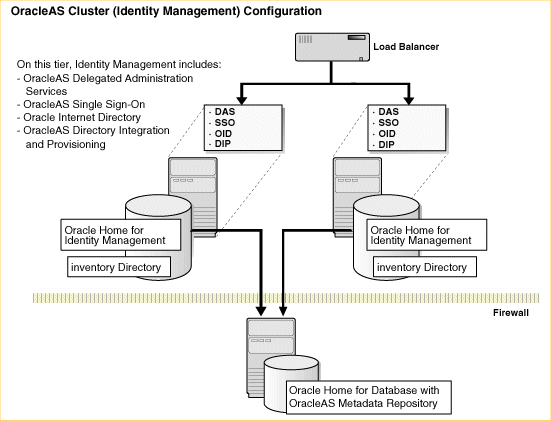
Before you begin this procedure, perform a complete, full software backup of everything in the Oracle Home and related directories for the OracleAS Metadata Repository and the OracleAS Identity Management instances.
In addition, shut down all processes and perform a full cold database backup of the middle tiers and Infrastructure Oracle homes.
Before you can upgrade to OracleAS Cluster (Identity Management), you must upgrade the database that hosts the OracleAS Metadata Repository to a supported database.
For detailed instructions on upgrading the database that hosts the OracleAS Metadata Repository, see Chapter 6, "Upgrading the Database That Hosts the OracleAS Metadata Repository".
|
Note: When applying database patchsets, be sure to carefully review the patchset README for your specific platform. The instructions for installing patchsets can vary significantly from platform to platform. For example, some platforms, such as Linux, might require you to install a specific version of Oracle Universal Installer before proceeding with the patschset installation. |
There are certain upgrade scenarios where you might have to upgrade any 10g (9.0.4) middle tiers in your Oracle Application Server environment to 10g Release 2 (10.1.2).
For more information, refer to Chapter 5, "Upgrading 10g (9.0.4) Middle Tiers to 10g Release 2 (10.1.2)".
After the database that hosts the OracleAS Metadata Repository has been upgraded to a supported version, and after any middle tiers have been upgraded to 10g Release 2 (10.1.2), you can now upgrade the first OracleAS Identity Management Oracle home in the OracleAS Cluster (Identity Management) configuration.
When you upgrade the first OracleAS Identity Management Oracle home, you also upgrade the OracleAS Identity Management schemas in the OracleAS Metadata Repository.
Note that in a colocated OracleAS Cluster (Identity Management), all the OracleAS Identity Management instances are clustered in a Distributed Configuration Management (DCM) Cluster. This ensures synchronization between the configurations of the different Identity Management components on all of the Identity Management instances.
To upgrade the first OracleAS Identity Management Oracle home, refer to the following sections:
Task 4c: Configure Oracle HTTP Server and OracleAS Single Sign-On
Task 4d: Finish the Upgrade of the First OracleAS Identity Management Instance
Use the following steps to upgrade the first OracleAS Identity Management instance in the OracleAS Cluster (Identity Management) environment:
Make sure that the other OracleAS Identity Management Instances in the environment are down.
Only the OracleAS Identity Management instance that you are upgrading first should be up and running. If necessary, shut down the other OracleAS Identity Management instances.
Configure the Load Balancer to direct traffic only to the OracleAS Identity Management instance you are about to upgrade.
All Requests should be directed only to the OracleAS Identity Management instance you are about to upgrade. The other OracleAS Identity Management instances in the environment should be shut down.
Use the Oracle Universal Installer and the Oracle Application Server 10g (10.1.4.0.1) installation procedure to upgrade the OracleAS Identity Management instance.
Refer to Chapter 7, "Using Oracle Universal Installer to Upgrade Oracle Identity Management" for complete instructions on upgrading the first OracleAS Identity Management instance.
Perform any post-upgrade procedures that apply to the Oracle Internet Directory Oracle home.
Refer to Section 9.2, "Task 2: Perform Oracle Internet Directory Post-Upgrade Steps" for more information.
Use the following steps to reconfigure the cluster and to prepare for installing the remaining OracleAS Identity Management instances:
Remove the OracleAS Identity Management 10g Release 2 (10.1.2) instances from the cluster:
Start the Distributed Configuration Management (DCM) shell:
DESTINATION_ORACLE_HOME/dcm/bin/dcmctl shell
Display a list of the currently defined clusters:
DCM> listclusters
Note the name of the OracleAS Cluster (Identity Management) and then list the OracleAS Identity Management instances that are members of the cluster:
DCM> listInstances -cl name_of_Identity_Management_cluster
For each OracleAS Identity Management instance in the cluster, enter the following command:
DCM> leavecluster -i 1012_instance_name
Add the newly upgraded Oracle Identity Management 10g (10.1.4.0.1) instance to the cluster:
Join the cluster using the following command:
DCM> joincluster -cl name_of_Identity_Management_cluster
Note that the joincluster command stops the 10g (10.1.4.0.1) instance and all of its processes.
Start the Oracle Identity Management 10g (10.1.4.0.1) instance:
DESTINATION_ORACLE_HOME/opmn/bin/opmnctl stopall DESTINATION_ORACLE_HOME/opmn/bin/opmnctl startall
Use the following steps to configure Oracle HTTP Server, OracleAS Single Sign-On, and OPMN after you have upgraded the first OracleAS Identity Management instance.
The steps you follow to configure these components vary, depending upon whether or not you have configured Oracle HTTP Server or your load balancer to accept HTTPS requests.
Refer to the following sections for more information:
Configuration Steps When Both Oracle HTTP Server and the Load Balancer Are Configured for SSL
Configuration Steps When Only the Load Balancer Is Configured for SSL
Configuration Steps When Oracle HTTP Server and the Load Balancer are Not Using SSL
The following steps apply if both the Oracle HTTP Server and the load balancer are configured to listen for the HTTPS protocol;
Configure the Oracle HTTP Server listener as follows:
Edit the following Oracle HTTP Server configuration file:
DESTINATION_ORACLE_HOME/Apache/Apache/conf/ssl.conf
Make sure that the ServerName directive is set to the virtual host (for example, imhost.domain.com) and not to the physical host.
Save and close the ssl.conf configuration file.
Update DCM to recognize the changes made to the Oracle HTTP Server component using the following command:
DESTINATION_ORACLE_HOME/dcm/bin/dcmctl updateConfig -ct ohs -d -v
Configure OracleAS Single Sign-On to accept authentication requests on the SSL port over the HTTPS protocol by using the following command:
ORACLE_HOME/sso/bin/ssocfg.sh https imhost.domain.com 4444
In this example:
imhost.domain.com is the address configured at the load balancer for HTTPS requests.
The default HTTPS Listener port is 4444, but this port may differ for your specific installation. You can obtain the correct value for your installation by examining the assigned to the "port" variable in the ssl.conf configuration file.
Edit the OPMN configuration file to enable SSL for the Oracle HTTP Server:
Locate and open the following OPMN configuration file with a text editor:
DESTINATION_ORACLE_HOME/opmn/conf/opmn.xml
Locate the following entry for the HTTP_Server component:
<ias-component id="HTTP_Server">
<process-type id="HTTP_Server" module-id="OHS">
<module-data>
<category id="start-parameters">
<data id="start-mode" value="ssl-disabled"/>
</category>
</module-data>
<process-set id="HTTP_Server" numprocs="1"/>
</process-type>
</ias-component>
Change the value of the start-mode entry to ssl-enabled.
The resulting entry in the opmn.xml file should appear as follows:
<ias-component id="HTTP_Server">
<process-type id="HTTP_Server" module-id="OHS">
<module-data>
<category id="start-parameters">
<data id="start-mode" value="ssl-enabled"/>
</category>
</module-data>
<process-set id="HTTP_Server" numprocs="1"/>
</process-type>
</ias-component>
Re-register the instance with OracleAS Single Sign-On:
Run the following command to re-register the instance with OracleAS Single Sign-On:
ORACLE_HOME/sso/bin/ssoreg.sh -oracle_home_path orcl_home_path -site_name instance_name_you_specified_during_upgrade -config_mod_osso TRUE -mod_osso_url effective_URL_of_the_partner_application -u userid
In this example:
The effective_URL_of_the_partner_application is in this URL format:
http://virtual_servername:ssl_port
Replace userid with the Oracle owner.
Note that at this point in the procedure, the upgraded OracleAS Identity Management Oracle home should be a fully working 10g (10.1.4.0.1) OracleAS Identity Management instance running against the OracleAS Metadata Repository database. The load balancer is still pointing to only this new, upgraded instance.
Change the Oracle Delegated Administration Services orcldasurlbase attribute in the directory server, using the following steps:
Start Oracle Directory Manager (oidadmin) and connect to the Oracle Internet Directory.
The oidadmin tool is located in the following directory in the destination Oracle home:
DESTINATION_ORACLE_HOME/bin/
Make sure you select the SSL Enabled check box when connecting to the directory server.
In the System Objects Navigator, navigate to the cn=OperationURLs entry as follows:
Entry Management ->
cn=OracleContext ->
cn=Products ->
cn=DAS ->
cn=OperationURLs
After you select the cn=OperationURLs entry, locate the orcldasurl attribute on the Properties tab in the right pane of the Oracle Directory Manager window.
Change the orcldasurlbase attribute so it references the SSL URL for the Oracle Delegated Administration Services:
https://virtual_server_name:load_balancer_ssl_listen_port
The following steps apply if both the Oracle HTTP Server and the load balancer are configured to listen for the HTTPS protocol:
Configure the Oracle HTTP Server listener as follows:
Use a text editor to locate and open the following Oracle HTTP Server configuration file:
DESTINATION_ORACLE_HOME/Apache/Apache/conf/httpd.conf
Make sure that the ServerName directive is set to the virtual host (for example, imhost.domain.com) and not to the physical host.
Save and close the httpd.conf configuration file.
Update DCM to recognize the changes made to the Oracle HTTP Server component using the following command:
DESTINATION_ORACLE_HOME/dcm/bin/dcmctl updateConfig -ct ohs -d -v
Configure OracleAS Single Sign-On to accept authentication requests on the SSL port over the HTTPS protocol by using the following command:
ORACLE_HOME/sso/bin/ssocfg.sh https imhost.domain.com 4444
In this example:
imhost.domain.com is the virtual host address configured at the load balancer for HTTPS requests.
The default HTTPS Listener port is 4444, but this port may differ for your specific installation. You can obtain the correct value for your installation by examining the assigned to the "port" variable in the ssl.conf configuration file.
Re-register the instance with OracleAS Single Sign-On:
Run the following command to re-register the instance with OracleAS Single Sign-On:
ORACLE_HOME/sso/bin/ssoreg.sh -oracle_home_path orcl_home_path -site_name instance_name_you_specified_during_upgrade -config_mod_osso TRUE -mod_osso_url effective_URL_of_the_partner_application -u userid
In this example:
The effective_URL_of_the_partner_application is in this URL format:
http://virtual_servername:load_blancer_ssl_port
Replace userid with the Oracle owner.
Note that at this point in the procedure, the upgraded OracleAS Identity Management Oracle home should be a fully working 10g (10.1.4.0.1) OracleAS Identity Management instance running against the OracleAS Metadata Repository database. The load balancer is still pointing to only this new, upgraded instance.
Change the Oracle Delegated Administration Services orcldasurlbase attribute in the directory server, using the following steps:
Start Oracle Directory Manager (oidadmin) and connect to the Oracle Internet Directory.
The oidadmin tool is located in the following directory in the destination Oracle home:
DESTINATION_ORACLE_HOME/bin/
Make sure you select the SSL Enabled check box when connecting to the directory server.
In the System Objects Navigator, navigate to the cn=OperationURLs entry as follows:
Entry Management ->
cn=OracleContext ->
cn=Products ->
cn=DAS ->
cn=OperationURLs
After you select the cn=OperationURLs entry, locate the orcldasurl attribute on the Properties tab in the right pane of the Oracle Directory Manager window.
Change the orcldasurlbase attribute so it references the SSL URL for the Oracle Delegated Administration Services:
https://virtual_server_name:load_balancer_ssl_listen_port
The following steps apply if both the Oracle HTTP Server and the load balancer are configured to listen for the HTTPS protocol;
Configure the Oracle HTTP Server listener as follows:
Use a text editor to locate and open the following Oracle HTTP Server configuration file:
DESTINATION_ORACLE_HOME/Apache/Apache/conf/httpd.conf
Make sure that the ServerName directive is set to the virtual host (for example, imhost.domain.com) and not to the physical host.
Save and close the httpd.conf configuration file.
Update DCM to recognize the changes made to the Oracle HTTP Server component using the following command:
DESTINATION_ORACLE_HOME/dcm/bin/dcmctl updateConfig -ct ohs -d -v
Configure OracleAS Single Sign-On to accept authentication requests on the SSL port over the HTTPS protocol by using the following command:
ORACLE_HOME/sso/bin/ssocfg.sh http imhost.domain.com 7777
In this example:
imhost.domain.com is the address configured at the load balancer for HTTP requests.
The default HTTP Listener port is 7777, but this port may differ for your specific installation. You can obtain the correct value for your installation by examining the assigned to the "port" variable in the httpd.conf configuration file.
Re-register the instance with OracleAS Single Sign-On:
Run the following command to re-register the instance with OracleAS Single Sign-On:
ORACLE_HOME/sso/bin/ssoreg.sh -oracle_home_path orcl_home_path -site_name instance_name_you_specified_during_upgrade -config_mod_osso TRUE -mod_osso_url effective_URL_of_the_partner_application -u userid
In this example:
The effective_URL_of_the_partner_application is in this URL format:
http://virtual_servername:load_balancer_port
Replace userid with the Oracle owner.
Note that at this point in the procedure, the upgraded OracleAS Identity Management Oracle home should be a fully working 10g (10.1.4.0.1) OracleAS Identity Management instance running against the OracleAS Metadata Repository database. The load balancer is still pointing to only this new, upgraded instance.
Change the Oracle Delegated Administration Services orcldasurlbase attribute in the directory server, using the following steps:
Start Oracle Directory Manager (oidadmin) and connect to the Oracle Internet Directory.
The oidadmin tool is located in the following directory in the destination Oracle home:
DESTINATION_ORACLE_HOME/bin/
In the System Objects Navigator, navigate to the cn=OperationURLs entry as follows:
Entry Management ->
cn=OracleContext ->
cn=Products ->
cn=DAS ->
cn=OperationURLs
After you select the cn=OperationURLs entry, locate the orcldasurl attribute on the Properties tab in the right pane of the Oracle Directory Manager window.
Change the orcldasurlbase attribute so it references the URL for the Oracle Delegated Administration Services:
http://virtual_server_name:load_balancer_non_ssl_listen_port
Perform the following steps to finish the upgrade of the first OracleAS Identity Management instance in the OracleAS Cluster (Identity Management) environment:
Enable the monitoring of the instance by Oracle Enterprise Manager Application Server Control by following the instructions in Section 9.1.2.1, "Enabling Monitoring of OracleAS Single Sign-On and Oracle Delegated Administration Services in Application Server Control".
Update the mod_oc4j load balancing directive in the destination Oracle home:
Update the DCM configuration:
DESTINATION_ORACLE_HOME/dcm/bin/dcmctl updateConfig -d -v
Note that using only the -d and -v arguments to the dcmctl updateConfig command updates all the component information for DCM. The command also stops some of the processes in the Oracle Identity Management Oracle home.
Stop and then start all the processes in the Oracle Identity Management Oracle home:
DESTINATION_ORACLE_HOME/opmn/bin/opmnctl stopall DESTINATION_ORACLE_HOME/opmn/bin/opmnctl startall
To ensure that Oracle Application Server maintains the state of stateful Web applications across DCM-Managed OracleAS Cluster, you need to configure state replication for the Web applications.
Configure state replication only on the first node where Oracle Delegated Administration Services is installed.
To configure state replication for the OC4J_Security instance, do the following:
Using the Application Server Control Console, navigate to the Application Server Home page for the instance that contains Oracle Delegated Administration Services.
Click OC4J_SECURITY link on the Application Server Home page.
Click Administration link on the OC4J Home Page.
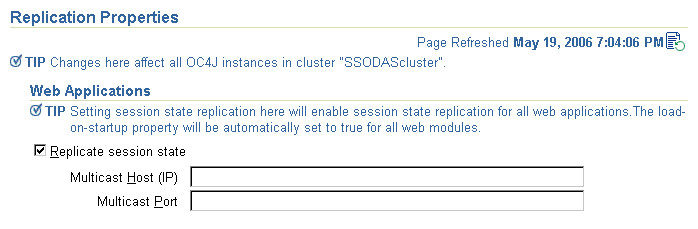
Click Replication Properties link in the Instance Properties area.
Scroll to the Web Applications section of the page (Figure B-2).
Select the Replicate session state checkbox.
Optionally, you can provide the multicast host IP address and port number. If you do not provide the host and port for the multicast address, it defaults to host IP address 230.230.0.1 and port number 9127. The host IP address must be between 224.0.0.2 through 239.255.255.255. Do not use the same multicast address for both HTTP and EJB multicast addresses.
|
Note: When choosing a multicast address, ensure that the address does not collide with the addresses listed in:
Also, if the low order 23 bits of an address is the same as the local network control block, |
Figure B-2 Web State Replication Configuration
Make sure that the OracleAS Identity Management instance (including Oracle Internet Directory) that you upgraded in Section B.3.5, "Task 4: Upgrade the First OracleAS Identity Management Instance" is up and running.
If it is not running, start the Identity Management instance (including Oracle Internet Directory) as follows:
ORACLE_HOME/opmn/bin/opmnctl startall
Upgrade the Metadata Repository in the newly upgraded database as described in Chapter 8, "Using MRUA to Upgrade the OracleAS Metadata Repository", with the following exception:
On the MRUA command line, enter the address of the load balancer in place of the oid_host and oid_ssl_port arguments.
Note that the values you enter for the -oid_host argument and -oid_ssl_port arguments must match the value of the corresponding properties defined in following configuration file in the Identity Management Oracle home:
IDENTITY_MANAGEMENT_HOME/config/ias.properties
For example:
OIDhost=sys42.acme.com OIDsslport=636
When MRUA finishes processing, verify that the schemas have been upgraded, as described in Section 8.3, "Task 3: Verify the Success of the OracleAS Metadata Repository Upgrade".
After you upgrade the first OracleAS Identity Management instance in the cluster, and after you upgrade the OracleAS Metadata Repository, you can then install the additional OracleAS Identity Management instances in the OracleAS Cluster (Identity Management):
Make sure that the Oracle Internet Directory is up and running on the first OracleAS Identity Management instance.
Make sure that the OracleAS Metadata Repository database and listener are up and running.
Make sure that the Load Balancer is configured to direct traffic only to the first Identity Management instance.
Install the new 10g (10.1.4.0.1) OracleAS Identity Management Oracle home by following the instructions in the section "Installing OracleAS Cluster (Identity Management) on Subsequent Nodes," in the Oracle Application Server Installation Guide.
Reconfigure Load Balancer and test the installation.
After a successful installation of the subsequent OracleAS Identity Management Oracle home, configure the Load Balancer to route requests to the new instance.
Repeat this procedure for any additional and subsequent OracleAS Identity Management installations that will be part of the cluster.
After you have upgraded the first Oracle Identity Management instance in the cluster and you have added the remaining cluster members, you can then verify that the upgrade was successful and then decommission the 10g Release 2 (10.1.2) Oracle homes.
For more information, refer to Chapter 10, "Verifying the Upgrade and Decommissioning the Source Oracle Homes".
The following sections describe how to upgrade from a distributed 10g Release 2 (10.1.2) OracleAS Cluster (Identity Management) environment to 10g (10.1.4.0.1):
Task 1: Review the Distributed OracleAS Cluster (Identity Management) Upgrade Requirements
Task 4: Upgrade the First Oracle Internet Directory Oracle Home in the Distributed Environment
Task 5: Upgrade the First OracleAS Single Sign-On Oracle Home
Task 7: Installing Subsequent Oracle Internet Directory Instances
Task 8: Installing Subsequent OracleAS Single Sign-On Instances
Task 9: Verify the Upgrade and Decommission the 10g Release 2 (10.1.2) Oracle Homes
The following sections describe the requirements you must meet in order to upgrade from a 10g Release 2 (10.1.2) distributed OracleAS Cluster (Identity Management) configuration to a 10g (10.1.4.0.1) distributed OracleAS Cluster (Identity Management) configuration:
Before you use this procedure, note that the Identity Management instances you are upgrading must be 10g Release 2 (10.1.2) intances that were installed using the procedures documented in "Installing in High Availability Environments: OracleAS Cluster (Identity Management)" in the 10g Release 2 (10.1.2) Oracle Application Server Installation Guide.
OracleAS Identity Management consists of components that can also be installed separately:
Oracle Internet Directory (OID)
OracleAS Single Sign-On (SSO)
Oracle Delegated Administration Services (DAS)
Oracle Directory Integration Platform (DIP)
This procedure does not include support for Oracle Application Server Certificate Authority (OCA).
This procedure describes how to upgrade a distributed OracleAS Cluster (Identity Management) 10g Release 2 (10.1.2) installation, where the Identity Management components are separated into two tiers. One tier contains the Oracle Application Server Single Sign-On and Oracle Delegated Administration Services components and the second tier contains the Oracle Internet Directory and Oracle Directory Integration Platform components.
|
See Also: Section B.5, "Upgrading an OracleAS Cluster (Identity Management) 10g Release 2 (10.1.2) Colocated Configuration" for information about upgrading a colocated OracleAS Identity Management configuration, where all Identity management components are installed in one Oracle home. |
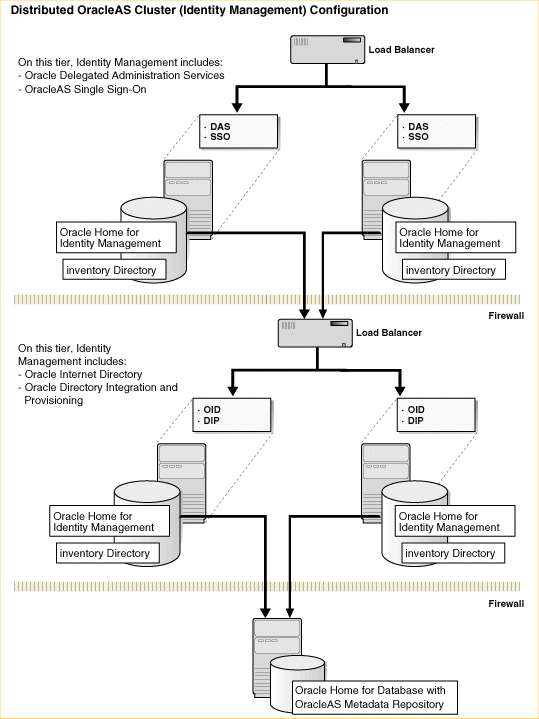
A distributed OracleAS Cluster (Identity Management) configuration allows administrators to install the OracleAS Single Sign-On and Oracle Delegated Administration Services components in a the DMZ and the Oracle Internet Directory on the internal network inside the firewall.
Figure B-3 shows such a distributed OracleAS Cluster (Identity Management) 10g Release 2 (10.1.2) environment.
Figure B-3 10g Release 2 (10.1.2) OracleAS Cluster (Identity Management) Distributed Upgrade Starting Point
This procedure assumes the database that hosts the OracleAS Metadata Repository is an Oracle Real Application Clusters (RAC) Database. Specifically, the procedure described in this section was tested on a two-node RAC environment. However, it is assumed that this procedure also applies to:
A single-instance database
A Real Application Clusters database consisting of more than two nodes
The requirement for Real Application Clusters is a shared-storage configuration. The implementation of the shared volume is vendor-specific. The procedures in this section should be applicable to all Operating systems and clusters but were developed and tested in a Linux environment. Specifically, the following shared storage options are supported:
Raw devices
Cluster filesystem (for example, OCFS on Linux)
Network filesystem (for example, supported NAS devices)
Although cluster and volume management software is vendor-specific, the steps and considerations provided in this section apply specifically to customers wishing to optionally implement Oracle's Automated Storage Management (ASM).
Before you begin this transformation procedure, take a complete, full software backup of everything in the Oracle Home and related directories for the OracleAS Metadata Repository and the OracleAS Identity Management instances.
In addition, shut down all processes and perform a full cold database backup of the middle tiers and Infrastructure Oracle homes.
Before you can upgrade to OracleAS Cluster (Identity Management), you must upgrade the database that hosts the OracleAS Metadata Repository to a supported database.
For detailed instructions on upgrading the database that hosts the OracleAS Metadata Repository, see Chapter 6, "Upgrading the Database That Hosts the OracleAS Metadata Repository".
|
Note: When applying database patchsets, be sure to carefully review the patchset README for your specific platform. The instructions for installing patchsets can vary significantly from platform to platform. For example, some platforms, such as Linux, might require you to install a specific version of Oracle Universal Installer before proceeding with the patschset installation. |
There are certain upgrade scenarios where you might have to upgrade any 10g (9.0.4) middle tiers in your Oracle Application Server environment to 10g Release 2 (10.1.2).
For more information, refer to Chapter 5, "Upgrading 10g (9.0.4) Middle Tiers to 10g Release 2 (10.1.2)".
After the database that hosts the OracleAS Metadata Repository has been upgraded to a supported version, and after any middle tiers have been upgraded to 10g Release 2 (10.1.2), you can now upgrade the first OracleAS Identity Management Oracle home in the Rack-Mounted Identity Management configuration.
When you upgrade the first OracleAS Identity Management Oracle home, you also upgrade the OracleAS Identity Management schemas in the OracleAS Metadata Repository.
Note that in a distributed OracleAS Cluster (Identity Management) configuration, the OracleAS Single Sign-On instances are clustered together in a Distributed Configuration Management (DCM) Cluster. This ensures synchronization between the configurations of the different Identity Management components on all of the Identity Management instances.
To upgrade the first Oracle Internet Directory Oracle home, use the following steps.
|
Note: If you are upgrading a distributed OracleAS Cluster (Identity Management) environment, be sure that the first OracleAS Identity Management instance you upgrade represents one of the OracleAS Single Sign-On Oracle homes. |
Make sure that the other OracleAS Identity Management Instances in the environment are down.
Only the Oracle Internet Directory instance that you are upgrading first should be up and running. If necessary, shut down the other OracleAS Identity Management instances.
Configure the Oracle Internet Directory Load Balancer to direct traffic only to the OracleAS Identity Management instance you are about to upgrade.
All Requests should be directed only to the Oracle Internet Directory instance you are about to upgrade. The other OracleAS Identity Management instances in the environment should be shut down.
Use the Oracle Universal Installer and the Oracle Application Server 10g (10.1.4.0.1) installation procedure to upgrade the Oracle Internet Directory instance.
Refer to Section 7.5.3, "Upgrading Distributed OracleAS Identity Management Configurations" for complete instructions on upgrading the first Oracle Internet Directory instance.
Perform any post-upgrade procedures that apply to your OracleAS Identity Management environment.
Refer to Section 9.2, "Task 2: Perform Oracle Internet Directory Post-Upgrade Steps" for more information.
Follow the steps described in Table B-4 to upgrade the first OracleAS Single Sign-On Oracle home in the distributed OracleAS Cluster (Identity Management) 10g Release 2 (10.1.2) environment.
Table B-4 Steps Required to Upgrade the First OracleAS Single Sign-On Oracle Home in a Distributed OracleAS Cluster (Identity Management) Environment
| Step | Description | More Information |
|---|---|---|
|
1 |
Start the OracleAS Single Sign-On instance that you are about to upgrade. |
Only the Oracle Internet Directory instance that you upgraded first and the current OracleAS Single Sign-On instance that you plan to upgrade next should be up and running. If necessary, shut down the other OracleAS Identity Management instances. |
|
2 |
Configure the OracleAS Single Sign-On Load Balancer to direct traffic only to the OracleAS Identity Management instance you are about to upgrade. |
All requests should be directed only to the OracleAS Single Sign-On instance you are about to upgrade. The other OracleAS Single Sign-On instances in the environment should be shut down. |
|
3 |
Use the Oracle Universal Installer and the Oracle Application Server 10g (10.1.4.0.1) installation procedure to upgrade the OracleAS Single Sign-On instance. |
Refer to Section 7.5.3, "Upgrading Distributed OracleAS Identity Management Configurations" for complete instructions on upgrading the first OracleAS Single Sign-On instance. |
|
4 |
Perform any post-upgrade procedures that apply to the OracleAS Single Sign-On Oracle home. |
Refer to Section 9.3, "Task 3: Perform OracleAS Single Sign-On Post-Upgrade Steps" for more information. |
|
5 |
Reconfigure the DCM cluster to which the OracleAS Single Sign-On instance belongs. |
Refer to Section B.5.4.2, "Task 4b: Reconfigure the DCM Cluster" and perform the steps defined in that section in the OracleAS Single Sign-On Oracle home. |
|
6 |
Configure the Oracle HTTP Server and OracleAS Single Sign-On to work with the newly upgraded OracleAS Single Sign-On instance. |
Refer to Section B.5.4.3, "Task 4c: Configure Oracle HTTP Server and OracleAS Single Sign-On" and perform the steps defined in that section in the OracleAS Single Sign-On Oracle home. |
|
7 |
Complete the upgrade of the first OracleAS Single Sign-On Oracle home. |
Refer to Section B.5.4.4, "Task 4d: Finish the Upgrade of the First OracleAS Identity Management Instance" and perform the steps in that section in the OracleAS Single Sign-On Oracle home. |
Make sure that the OracleAS Identity Management instance (including Oracle Internet Directory) that you upgraded in Section B.3.5, "Task 4: Upgrade the First OracleAS Identity Management Instance" is up and running.
If it is not running, start the Identity Management instance (including Oracle Internet Directory) as follows:
ORACLE_HOME/opmn/bin/opmnctl startall
Upgrade the Metadata Repository in the newly upgraded database as described in Chapter 8, "Using MRUA to Upgrade the OracleAS Metadata Repository", with the following exception:
On the MRUA command line, enter the address of the load balancer in place of the oid_host and oid_ssl_port arguments.
Note that the values you enter for the -oid_host argument and -oid_ssl_port arguments must match the value of the corresponding properties defined in following configuration file in the Identity Management Oracle home:
IDENTITY_MANAGEMENT_HOME/config/ias.properties
For example:
OIDhost=sys42.acme.com OIDsslport=636
When MRUA finishes processing, verify that the schemas have been upgraded, as described in Section 8.3, "Task 3: Verify the Success of the OracleAS Metadata Repository Upgrade".
After you upgrade the first Oracle Internet Directory instance, upgrade the first OracleAS Single Sign-On instance, and upgrade the OracleAS Metadata Repository, you can then install the second Oracle Internet Directory and Oracle Delegated Administration Services instance in the OracleAS Cluster (Identity Management):
Make sure that the first Oracle Internet Directory is up and running on the first OracleAS Identity Management instance.
Make sure that the OracleAS Metadata Repository database and listener are up and running.
Make sure that the Oracle Internet Directory Load Balancer is configured to direct traffic only to the first Oracle Internet Directory instance.
Install a new 10g (10.1.4.0.1) Oracle Internet Directory Oracle home by following the instructions specific to Oracle Internet Directory installation in the section "Installing OracleAS Cluster (Identity Management) on Subsequent Nodes," in the Oracle Application Server Installation Guide.
This step involves running Oracle Universal Installer and installing a new 10g (10.1.4.0.1) Oracle Internet Directory and Oracle Delegated Administration Services Oracle home. During the installation, respond to the installation prompts. In particular, be sure to do the following:
On the Select Installation Type screen, select Oracle Identity Management.
On the Select Configuration Options screen:
Select Oracle Internet Directory. Do not select Oracle Application Server Single Sign-On.
Do not select Oracle Application Server Delegated Administration Services.
Select Oracle Directory Integration Platform if you need this component.
Do not select Oracle Application Server Certificate Authority (OCA).
Select High Availability and Replication.
Reconfigure the Load Balancer and test the installation.
After a successful installation of the subsequent Oracle Internet Directory Oracle home, configure the Load Balancer to route requests to the new instance.
Repeat this procedure for any additional and subsequent Oracle Internet Directory installations that will be part of the cluster.
After you upgrade the first Oracle Internet Directory instance, upgrade the first OracleAS Single Sign-On instance, upgrade the OracleAS Metadata Repository, and install any subsequent Oracle Internet Directory instances, you can then install any subsequent OracleAS Single Sign-On instances in the OracleAS Cluster (Identity Management):
Make sure that the Oracle Internet Directory instances and the first OracleAS Single Sign-On is up and running.
Make sure that the OracleAS Metadata Repository database and listener are up and running.
Make sure that the OracleAS Single Sign-On Load Balancer is configured to direct traffic only to the first OracleAS Single Sign-On instance.
Install a new 10g (10.1.4.0.1) OracleAS Single Sign-On Oracle home by following the instructions specific to OracleAS Single Sign-On installation in the section "Installing OracleAS Cluster (Identity Management) on Subsequent Nodes," in the Oracle Application Server Installation Guide.
This step involves running Oracle Universal Installer and installing a new 10g (10.1.4.0.1) Oracle Internet Directory and Oracle Delegated Administration Services Oracle home. During the installation, answer the installation prompts. In particular, be sure to do the following points:
On the Select Installation Type screen, select Oracle Identity Management.
On the Select Configuration Options screen:
Do not select Oracle Internet Directory.
Select Oracle Application Server Single Sign-On.
Select Oracle Application Server Delegated Administration Services.
Select Oracle Directory Integration Platform if you need this component.
Do not select Oracle Application Server Certificate Authority (OCA).
Select High Availability and Replication.
On the Create or Join an OracleAS Cluster (Identity Management) page, select Join an Existing Cluster.
On the Specify Existing OracleAS Cluster Name screen enter the name of the Oracle Identity Management cluster you want to join.
On the Specify HTTP Load Balancer Host and Ports screen, be sure to enter the same values for every OracleAS Single Sign-On node in the cluster:
HTTP Listener: Port: Enter the port number that you want Oracle HTTP Server to listen on. Enable SSL: Select this option if you want to configure Oracle HTTP Server for SSL on this port.
HTTP Load Balancer: Hostname: Enter the name of the HTTP virtual server configured on your load balancer. Enter the same virtual server name that you configured on the load balancer.
HTTP Load Balancer: Port: Enter the port for the HTTP virtual server. Enable SSL: Select this option if this port is for SSL communications only.
Reconfigure the Load Balancer and test the installation.
After a successful installation of the subsequent Oracle Internet Directory Oracle home, configure the Load Balancer to route requests to the new instance.
Repeat this procedure for any additional and subsequent Oracle Internet Directory installations that will be part of the cluster.
After you have upgraded the first Oracle Identity Management instance in the cluster and you have added the remaining cluster members, you can then verify that the upgrade was successful and then decommission the 10g Release 2 (10.1.2) Oracle homes.
For more information, refer to Chapter 10, "Verifying the Upgrade and Decommissioning the Source Oracle Homes".