


|

|
|
|
|
Specifying Principal Names
As the administrator, you use the following configuration parameters to specify principal names for the Workstation Handler (WSH), domain gateway (GWTDOMAIN), and server processes running in your Release 7.1 or later BEA Tuxedo application.
SEC_PRINCIPAL_NAME may be specified any of the following four levels in the configuration hierarchy:
A security principal name at a particular configuration level can be overridden at a lower level. For example, suppose you configure terri as the principal name for machine mach1, and john as the principal name for server serv1 running on mach1. The processes on mach1 behave as follows:
How System Processes Acquire Credentials
During application booting, each WSH, domain gateway, and server process in the application includes its security principal name as an argument when calling the authentication plug-in to (1) acquire security credentials and (2) get authorization and auditing tokens for itself. The following diagram demonstrates the procedure.
Acquiring Credentials and Tokens During Application Booting
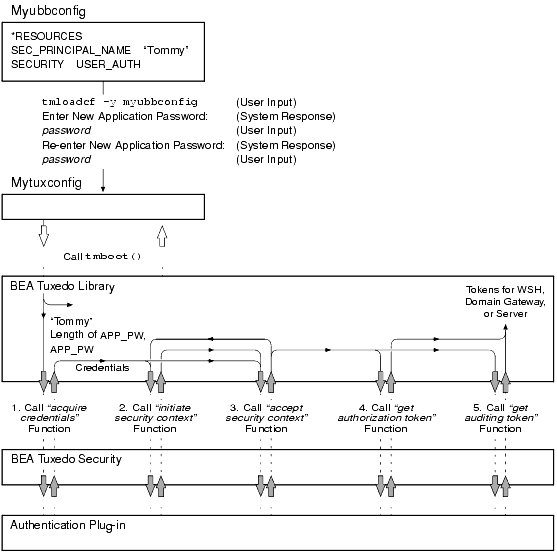
Each domain gateway process in the application calls the authentication plug-in a second time to acquire credentials and tokens for its assigned connection principal name.
Why System Processes Need Credentials
A WSH needs credentials so that it can authenticate Workstation clients that want to join the application, and to get authorization and auditing tokens for the authenticated Workstation clients. A WSH needs its own authorization and auditing tokens when handling requests from pre-Release 7.1 clients (clients running BEA Tuxedo Release 6.5 or earlier software) so that it can call the authentication plug-in to establish identities for the older clients. This behavior is described in Mandating Interoperability Policy.
A domain gateway needs one set of credentials so that it can authenticate remote domain gateways for the purpose of establishing links between BEA Tuxedo applications, as described in Establishing a Link Between Domains. (No authorization or auditing tokens are assigned to authenticated remote domain gateways.) A domain gateway acquires these credentials for the principal name specified in the CONNECTION_PRINCIPAL_NAME parameter.
A domain gateway needs a second set of credentials so that it can handle requests from pre-Release 7.1 clients, which involves calling the authentication plug-in to establish identities for the older clients. This behavior is described in Mandating Interoperability Policy. It also needs these credentials to establish identities when enforcing the local access control list (ACL) policy, as described in Setting ACL Policy. A domain gateway acquires these credentials for the principal name specified in the SEC_PRINCIPAL_NAME parameter.
A system or application server needs its own authorization and auditing tokens when handling requests from pre-Release 7.1 clients so that it can call the authentication plug-in to establish identities for the older clients. This behavior is described in Mandating Interoperability Policy.
A server also needs its own tokens when performing a server permission upgrade, which occurs when the authorization and auditing tokens of the server are assigned to messages that pass through the server but originate at a client. The service upgrade capability is described in Replacing Client Tokens with Server Tokens.
Note: An application server cannot call the authentication plug-in itself. It is the underlying system code that calls the authentication plug-in for the application server.
Example UBBCONFIG Entries for Principal Names
The following example pertains to specifying security principal names in the UBBCONFIG file using the SEC_PRINCIPAL_NAME parameter. For an example of specifying connection principal names in the DMCONFIG file using the CONNECTION_PRINCIPAL_NAME parameter, see Example DMCONFIG Entries for Establishing a Link.
*RESOURCES
SEC_PRINCIPAL_NAME "Tommy"
.
.
.
*SERVERS
"TMQUEUE" SRVGRP="QUEGROUP" SRVID=1
CLOPT="-t -s secsdb:TMQUEUE"
SEC_PRINCIPAL_NAME="TOUPPER"
See Also

|

|

|
|
|
|
Copyright © 2000 BEA Systems, Inc. All rights reserved.
|