


|

|
|
|
|
Establishing a Link Between Domains
When a domain gateway (GWTDOMAIN) attempts to establish a network link with another domain gateway, the following major events occur.
If one or both of the domain gateways are running BEA Tuxedo pre-Release 7.1 software, the gateway processes use an older (pre-Release 7.1) authentication protocol when setting up the connection.
As the administrator, you use the following configuration parameter to establish a link between domain gateways running BEA Tuxedo Release 7.1 or later software.
The following diagram demonstrates how a link is established between domains using default authentication plug-ins.
Establishing a Link Between Domains Using Default Authentication
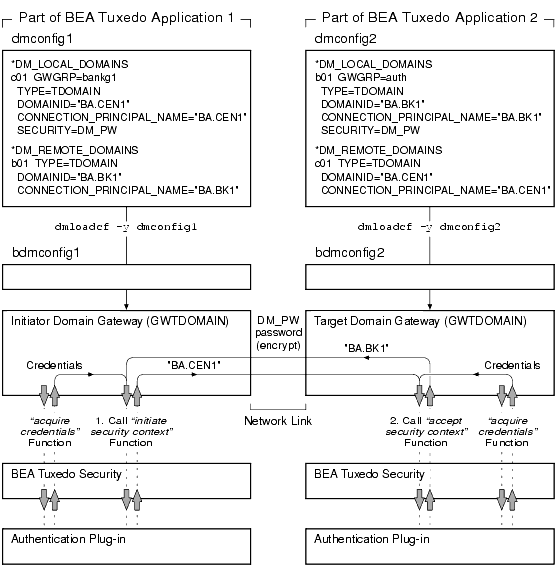
Note: The "Credentials" shown in the preceding diagram were acquired by each domain gateway process at application booting using the CONNECTION_PRINCIPAL_NAME identity configured for the local domain access point.
In the preceding diagram, notice that the information exchanged between the initiator and target domain gateways involves the CONNECTION_PRINCIPAL_NAME strings configured for the domain gateways, as specified in the BDMCONFIG files. Each authentication plug-in uses the password assigned to the remote domain access point (as defined in the DM_PASSWORDS section of the BDMCONFIG file) to encrypt the string before transmitting it over the network, and uses the password assigned to the local domain access point (as defined in the DM_PASSWORDS section of the BDMCONFIG file) to decrypt the received string. The encryption algorithm used is 56-bit DES, where DES is an acronym for the Data Encryption Standard.
For the encryption/decryption operation to succeed, the assigned password for the remote domain access point in the local BDMCONFIG file must be the same as the assigned password for the local domain access point in the remote BDMCONFIG file. (Similarly, if the domain security level is set to APP_PW, the application passwords in the respective TUXCONFIG files must be identical for the encryption/decryption operation to succeed.) For the authentication process to succeed, the received string must match the CONNECTION_PRINCIPAL_NAME string configured for the sender.
When the domain gateways pass the security checks, the link is established, and the gateways can forward service requests and receive replies over the established link.
Example DMCONFIG Entries for Establishing a Link
In the following example, the configurations shown in the local DMCONFIG file are used when establishing a connection through the local domain access point c01 and the remote domain access point b01.
*DM_LOCAL_DOMAINS
# <LDOM name> <Gateway Group name> <domain type>
# <domain id> [<connection principal name>] [<security>]...
c01 GWGRP=bankg1
TYPE=TDOMAIN
DOMAINID="BA.CENTRAL01"
CONNECTION_PRINCIPAL_NAME="BA.CENTRAL01"
SECURITY=DM_PW
.
.
.
*DM_REMOTE_DOMAINS
# <RDOM name> <domain type> <domain id>
# [<connection principal name>]...
b01 TYPE=TDOMAIN
DOMAINID="BA.BANK01"
CONNECTION_PRINCIPAL_NAME="BA.BANK01"
See Also

|

|

|
|
|
|
Copyright © 2000 BEA Systems, Inc. All rights reserved.
|