User's Guide
|
|
Get Adobe Reader |
Application Connection - Web Services
The following sections describe connecting to BEA WebLogic Network Gatekeeper through Web Services:
- About Web Services applications
- Distributing the WSDL files
- Registering service providers and applications
- Enabling a secure SSL connection to an application
- About the certificate builder
- Configuring the WebLogic Network Gatekeeper for SSL connections
- Setting up a one-way authenticated SSL connection
- Setting up a two-way authenticated SSL connection
About Web Services applications
For an application to connect to BEA WebLogic Network Gatekeeper through Web Services, the application must have access to the Extended API or Parlay X WSDL files deployed in BEA WebLogic Network Gatekeeper's web server. Both the Extended API and Parlay X WSDL consist of one file for each service and the file's are deployed in BEA WebLogic Network Gatekeeper's web server at BEA WebLogic Network Gatekeeper installation.
If the application have been implemented using WSDL files with the same version but from another source than BEA WebLogic Network Gatekeeper to connect to, the application developer has to re-generate the Java (or other programming language) interface with WSDL files from BEA WebLogic Network Gatekeeper the application will connect to.
Distributing the WSDL files
The Parlay X WSDL files, can be downloaded from :
http:/<IP-address>/parlayx/servlet/AxisServlet
The Extended Web Services WSDL files can be downloaded from:
http:/<IP-address>/wespa/servlet/AxisServlet
The Parlay X WSDL files for the notification interfaces can be downloaded from:
http:/<IP-address>/parlayX/wsdl
The Extended APIs Web Services WSDL files for the notification interfaces can be downloaded from:
Where <IP-address> is the IP address of BEA WebLogic Network Gatekeeper host where the axis servlet engine executes. The files are named <serviceName>Listener.wsdl and parlayx_<serviceName>.wsdl.
Registering service providers and applications
See Service Provider and Application Administration.
Enabling a secure SSL connection to an application
The connection between BEA WebLogic Network Gatekeeper and an application can be encrypted using SSL.
Both variants use X.509 certificates, with a private key and a public certificate.
One-way authenticated connections
When an application uses a Web Service provided by BEA WebLogic Network Gatekeeper, the WebLogic Network Gatekeeper must import it's own private key and the application needs the WebLogic Network Gatekeeper's public certificate.
When an application provides a Web Service, the application's public certificate must be imported to the WebLogic Network Gatekeeper and the application needs it's own private key.
Table 4-1 Certificate exchange for one-way authenticated sessions
Two-way authenticated connections
In addition to the setup necessary for one-way authenticated sessions, the following must also be configured for two-way authenticated sessions.
When an application uses a Web Service provided by BEA WebLogic Network Gatekeeper, the WebLogic Network Gatekeeper must import the application's certificate and the application needs it's own private key.
When an application provides a Web Service, the WebLogic Network Gatekeeper's private key must be imported to the WebLogic Network Gatekeeper and the application needs the WebLogic Network Gatekeeper's public certificate.
Table 4-2 Certificate exchange for two-way authenticated sessions
About the certificate builder
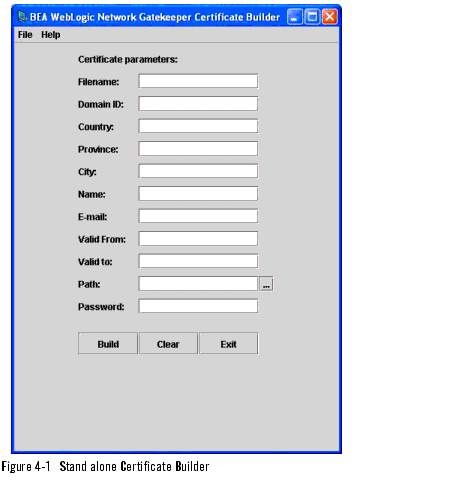
The certificate builder is a tool for generating user certificates and private keys. It can be used stand alone and through an Network Gatekeeper Management Tool. The same functions are provided in both cases. The stand alone version of the certificate builder is shown in Figure 4-1.
Some fields in the certificate builder are used differently depending on what function the user certificate and private key is generated for. The specific usage of all fields are described in Table 4-3.
Table 4-3 Description of the Fields in the Certificate Builder
Using the certificate builder stand alone
Follow the instruction below to generate a user certificate and private key pair.
If you perform the task through an Network Gatekeeper Management Tool, remember that the user certificate and private key will be stored on the server the Network Gatekeeper Management Tool is connected to. That is, where the SLEE runs.
- Enter the user certificate and private key data according to Table 4-3.
Using the certificate builder through an Network Gatekeeper Management Tool
Follow the instruction below to generate a user certificate and private key pair.
If you perform the task through an Network Gatekeeper Management Tool, remember that the user certificate and private key will be stored on the server the Network Gatekeeper Management Tool is connected to. That is, where the SLEE runs.
- Enter the user certificate and private key data according to Table 4-3.
Configuring the WebLogic Network Gatekeeper for SSL connections
Follow the instruction below to configure the WebLogic Network Gatekeeper for SSL. The task includes generating certificates an private keys.
- Follow the instructions given in Using the certificate builder through an Network Gatekeeper Management Tool or Using the certificate builder stand alone.
Now the WebLogic Network Gatekeeper's private key is imported to the WebLogic Network Gatekeeper's keystore and the WebLogic Network Gatekeeper is configured for SSL. In order setup an SSL connection for an individual application, continue with Setting up a one-way authenticated SSL connection or Setting up a two-way authenticated SSL connection, depending on the type of connection to use.
Setting up a one-way authenticated SSL connection
Follow the instruction below to setup a one-way authenticated secure SSL connection between an application and BEA WebLogic Network Gatekeeper. The task includes generating certificates an private keys, exchanging necessary certificates and to setup a HTTPS connection.
Configure the SSL connection when the WebLogic Network Gatekeeper acts as a server
This step is only necessary if the WebLogic Network Gatekeeper acts a server (provider of a a Web service). This is done for each application that shall use SSL connections.
|
Port number for the HTPPS connection. Default port for HTTPS is 443. |
||
|
If the SSLclient should be authenticated. |
Configure the SSL connection when the WebLogic Network Gatekeeper acts as a client
This step is only necessary if the WebLogic Network Gatekeeper acts a client (user of a a Web service). This is done for each application that shall use SSL connections.
- Enter the alias for the application's public certificate in the alias field. The alias must be unique.
- If using Parlay X, make sure that the URLs of the endpoints are registered as HTTPS addresses. The endpoints are registered in the SESPA layer of the respective service capability.
Refer to section Optional - Enable network initiated call notifications for Parlay X and Optional - Enable incoming message notification for Parlay X SMS and MMS.
Note: The Certificate Builder can be used to generate the applications private key and public certificate.
Note: The directory must contain only the certificate.
Setting up a two-way authenticated SSL connection
This is done for each application that shall use two-way authenticated SSL connectons.
- As a first step, set up a one-way authenticated SSL connection as described in Configure the SSL connection when the WebLogic Network Gatekeeper acts as a server.
- Retrieve the file with the application's public certificate and store it in a directory that the WebLogic Network Gatekeeper has access to.
Note: Make sure that the application import it's own private key.