

| Download Docs | Site Map | Glossary | |
|
|
|||
| bea.com | products | dev2dev | support | askBEA |
 |
 |
|
|||||||
| e-docs > WebLogic Platform > WebLogic Integration > Deploying Solutions > Using WebLogic Integration Security |
|
Deploying Solutions
|
Using WebLogic Integration Security
The following sections describe how to set up and manage security for WebLogic Integration solution deployments:
Before you proceed with the remainder of this topic, see Introducing WebLogic Platform 7.0 Security, which is available at the following URL:
http://download.oracle.com/docs/cd/E13196_01/platform/docs70/secintro/index.html
This document provides an overview of the security features of the entire WebLogic Platform, and provides important notes about managing security when using WebLogic Integration with other WebLogic Platform components.
Overview of WebLogic Integration Security
The foundation of every secure deployment of a WebLogic Integration solution is the set of security features provided by WebLogic Server. Therefore, after you configure security for the underlying WebLogic Server layer of your environment, you need to configure and manage security for those WebLogic Server entities that are specific to WebLogic Integration:
As the security manager for your environment, you need to focus your efforts on a set of predefined principals and resources that are created along with a WebLogic Integration domain.
This introduction presents the following topics to give you a high-level view of WebLogic Integration security:
Note: For a secure deployment, avoid running WebLogic Integration in the same WebLogic Server instance as any applications for which security is not provided. Internal WebLogic Integration API calls are not protected from such collocated applications.
Security and WebLogic Integration Domains
When you create a WebLogic Integration domain using the BEA Configuration Wizard, the domain is configured, by default, to use compatibility security. Compatibility security enables a domain to do the following:
By default, all WebLogic Integration users, groups, and ACLs are stored in a security realm known as the compatibility realm.
Note: A typical installation of WebLogic Integration includes WebLogic Server and WebLogic Workshop components. By default, the Configuration Wizard configures WebLogic Integration security to use compatibility security and allocates the WebLogic Server 6.x File realm for storing users and groups. The File realm is used in all WebLogic Integration samples. The WebLogic Server and WebLogic Workshop samples are based on a security configuration that is, in turn, based on an embedded LDAP server, which WebLogic Integration does not support in this release. Therefore, the samples delivered with WebLogic Server and WebLogic Workshop may not work with the default configuration for the WebLogic Integration samples.
For more information about the BEA Configuration Wizard, see Using the Configuration Wizard, which is available at the following URL:
http://download.oracle.com/docs/cd/E13196_01/platform/docs70/confgwiz/index.html
WebLogic Server Security Principals and Resources Used in WebLogic Integration
When you create a WebLogic Integration domain via the Configuration Wizard, the following WebLogic Server principals and resources are predefined:
The following diagram provides an overview of the WebLogic Server security principals used in WebLogic Integration.
Figure 5-1 WebLogic Server Security Principals Used in WebLogic Integration
For example, during the course of a B2B-based business operation, the WebLogic Server principals may function as follows: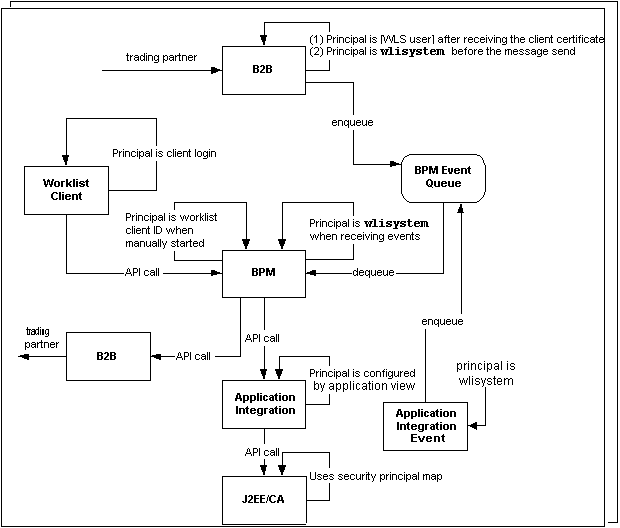
http://download.oracle.com/docs/cd/E13222_01/wls/docs70/jconnector/security.html
Considerations for Configuring Security
Before you configure the security for your WebLogic Integration domain, consider the following:
The following sections present a high-level discussion of these considerations and describe how they affect your WebLogic Integration security configuration.
About Digital Certificates
Digital certificates are electronic documents used to identify principals and objects as unique entities over networks such as the Internet. A digital certificate securely binds the identity of a user or object, as verified by a trusted third party known as a certificate authority, to a particular public key. The combination of the public key and the private key provides a unique identity for the owner of the digital certificate.
When you set up a WebLogic Integration environment as the foundation of your interenterprise commerce, using the B2B capabilities, you need to obtain and configure a specific set of digital certificates and keys. This set includes the following:
Digital Certificate Formats
Make sure that the formats and packaging standards of your digital certificates are compatible with WebLogic Server. Digital certificates have various encoding schemes, including the following:
The public key infrastructure (PKI) in WebLogic Server recognizes digital certificates that comply with either versions 1 and 3 of X.509, X.509v1 and X.509v3. We recommend obtaining digital certificates from a certificate authority, such as Verisign or Entrust.
Note: If a trading partner in a conversation uses Microsoft IIS as a proxy server, all the certificates used in the conversation must be trusted by a well-known Certificate Authority, such as Verisign or Entrust. The use of self-signed certificates will cause a request passed through the IIS proxy server to fail. This is a restriction in IIS, not WebLogic Integration.
For more details, see Configuring Security in Implementing Security with B2B Integration.
Using the Secure Sockets Layer (SSL) Protocol
The SSL protocol provides secure connections by supporting two functions:
An SSL connection begins with a handshake during which the applications exchange digital certificates, agree on the encryption algorithms to be used, and generate encryption keys that are then used for the remainder of the session.
If you are using SSL for trading partner authentication and authorization, which we strongly recommend for B2B collaborations, you need to configure the following:
For more information about configuring certificates, see Configuring Security in Implementing Security with B2B Integration.
Not required by SSL, but strongly recommended, is the creation and use of keystores for storing all the certificates and keys used in your WebLogic Integration domain. WebLogic Server provides a utility called the WebLogic Keystore provider based on the reference Keystore implementation supplied by Sun Microsystems in the Java Development Kit.
The WebLogic Keystore provider is based on the standard JKS keystore type, which implements the keystore as a file. For this release of WebLogic Server, JKS is the only keystore provider available. A keystore configured with the WebLogic Keystore provides protects each private key with an individual password. Two keystore files are associated with the WebLogic Keystore provider: One holds the CA certificates used by SSL to verify client certificates; the other holds users' private keys. WebLogic Server retrieves a private key from this keystore to initialize SSL.
For more information about setting up keystores for your WebLogic Integration domain, see Configuring the Keystore in Implementing Security with B2B Integration.
Using an Outbound Proxy Server or Proxy Plug-In
This section discusses the implications of using either an outbound proxy server or the WebLogic proxy plug-in.
Using an Outbound Proxy Server
A proxy server allows trading partners to communicate across intranets or the Internet without compromising security. If you are using WebLogic Integration in a security-sensitive environment, you may want to use WebLogic Integration behind a proxy server. Specifically, a proxy server is used to:
When proxy servers are configured on the local network, network traffic (sent with the SSL and HTTP protocols) is tunneled through the proxy server to the external network.
If an outbound proxy server is used in your environment, be careful when specifying the transport URI endpoints for the local trading partner. If you are using an HTTPS proxy, then you need to specify the ssl.ProxyHost and ssl.ProxyPort Java system properties. For details, see "Configuring WebLogic Integration B2B to Use an Outbound HTTP Proxy Server" in Configuring Security in Implementing Security with B2B Integration.
Using a Web Server with the WebLogic Proxy Plug-In
As an alternative to using an outbound proxy server, you may want to configure WebLogic Integration with a Web server, such as an Apache server, that is programmed to handle business messages from a remote trading partner. The Web server can provide the following services:
The Web server then uses the WebLogic proxy plug-in, which you can configure to provide the following services:
To configure the WebLogic proxy plug-in, consider the following:
Using a Firewall
If your WebLogic Integration environment is configured with a firewall, make sure your firewall is configured properly so that business messages can flow freely to and from local trading partners via the HTTP or HTTPS protocols.
Setting Up a Secure Deployment
The following sections provide instructions for the tasks you must complete to set up a secure deployment:
Step 1: Create the Domain
We recommend that you use the BEA Configuration Wizard to create the WebLogic Integration domain for which you want to configure security. To create a WebLogic Integration domain, complete the following steps:
http://download.oracle.com/docs/cd/E13196_01/platform/docs70/confgwiz/index.html
Note: Make sure you use a WebLogic Integration template when creating the new domain; do not use a WebLogic Server or a WebLogic Portal template. By specifying a WebLogic Integration template, you can make sure that the domain created in this step is based on the WebLogic Server 6.x security realm in compatibility mode. The new WebLogic Server 7.0 realm, based on LDAP, is not supported with WebLogic Integration. If you create a new domain by selecting a WebLogic Server template, the new domain uses the new WebLogic Server 7.0 security realm, which is based on LDAP.
Step 2: Configure WebLogic Server Security
When configuring WebLogic Server security, be sure to do the following:
"About Digital Certificates" on page 4-7 lists the supported certificate formats. For server certificates, PEM encoded X.509 V1 or V3 is the most commonly accepted format by SSL servers.
For private keys, PKCS8, which is the password-encrypted private key, is the most common format. Be sure to set the private key password so that WebLogic Server can read the private key.
A certificate chain is an array of digital certificates for trusted CAs, each of which is the issuer of the previous digital certificate.
You may specify one file containing all the intermediate and root CA certificates. (Note that if the file contains more than one CA certificate, WebLogic Server requires a PEM encoded file.) If you use the root CA keystore to store trusted CA certificates, be sure to import the whole chain in to the root CA keystore.
Step 3: Configure BPM Security
The security model provided by WebLogic Integration for business process management (BPM) functions comprises the following entities:
Within a security realm, the administrator (represented by the principal wlisystem) can specify the levels of access given to users and groups who want to use workflows and other resources. Users and groups are maintained in a WebLogic Server security realm. You can define groups and add users to those groups in the WebLogic Integration Studio. Each user you add is automatically and simultaneously added to the list of WebLogic Server users.
Organizations are BPM-specific entities that exist outside the WebLogic Server security realm.
Roles map to WebLogic Server groups.
The task of configuring BPM security is basically one of defining users, groups, roles, organizations, and permission levels. Because you can define organizations and roles, you have a great deal of flexibility in organizing the users and groups that access BPM resources. The Studio provides tools that allow you to create and modify users, groups, roles, and organizations. The Studio also provides a method for managing permissions for users, groups, and roles in minute detail.
For more information about BPM security, see the following topics:
Step 4: Configure B2B Integration Security
WebLogic Integration solutions that involve the exchange of messages between trading partners across firewalls have special security requirements, including trading partner authentication and authorization, as well as nonrepudiation.
To configure B2B security, you must perform the following tasks:
The sections that follow provide recommendations and considerations for each of these tasks.
Obtaining Certificates
Before you begin configuring WebLogic Integration security, particularly if you plan to conduct B2B exchanges, make sure you have the following certificates and keys:
The root CA directory should contain only the root CA certificates for each trading partner's client, encryption, and signature certificate. The root CA directory must not contain the CA certificates for the server certificates. (The server certificates are configured in the domain's config.xml file.)
Creating the Keystores
When you set up a WebLogic Integration domain for B2B collaborations, you must configure the WebLogic Keystore provider to create the following keystores:
Stores the local trading partners' private keys and certificates, such as the client, server, signature, and encryption certificates typically required for B2B collaborations. WebLogic Server retrieves a private key from this keystore to initialize SSL.
Stores the certificates of all the trusted certificate authorities (CAs). The WebLogic Keystore provider creates a trusted CA keystore that WebLogic Server uses, by default, to locate the trusted CAs used by SSL to verify client certificates.
You can use the JavaSoft JDK keytool utility or the WebLogic Server ImportPrivateKey utility to create each keystore and to add private keys to it. If neither keystore exists, it is created the first time you use either of these utilities to add a private key.
After you create the keystores and populate them with initial sets of keys, register them with the WebLogic Keystore provider, as described in "Step 2: Configure WebLogic Server Security" on page 4-11.
Configuring Local Trading Partners
Local trading partners send messages to remote trading partners using either HTTP or HTTPS. If you are using SSL in your B2B collaborations, which we strongly recommend, you need to configure the client certificate and key for each local trading partner.
Note the following about client certificates and keys for local trading partners:
Note the following about signature and encryption certificates and keys for local trading partners:
Configuring Remote Trading Partners
If you are using SSL, as with local trading partners, you need to configure the client certificate and key for each remote trading partner.
Note the following about client certificates and keys for remote trading partners:
Note the following about signature and encryption certificates and keys for remote trading partners:
Note the following about the remote trading partner's server certificate:
Implementing the Security Requirements for Business Protocols
Note that the business protocol with which a Collaboration Agreement is configured may have additional specific security requirements.
The following table lists additional sources of information about various business protocols.
Step 5: Configure Application Integration Security WebLogic Integration provides the following security mechanisms for those parts of an integration solution that are created and maintained with application integration functionality:
|

|

|