ALLOW Action
FIGURE 5-35 shows the Policy Rule Index dialog box for the ALLOW action.
Figure 5-35 Policy Rule Index Dialog Box for ALLOW action

TABLE 5-36 describes the controls in Policy Rule Index dialog box for ALLOW action.
Table 5-36 Controls for ALLOW Action
-
PROXY_HTTP - Presents the dialog box shown in FIGURE 5-36.
Figure 5-36 PROXY_HTTP Dialog Box for ALLOW action
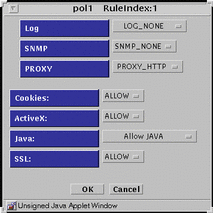
TABLE 5-37 lists the flags for the HTTP proxy.
Table 5-37 HTTP Proxy Flags
-
PROXY_FTP - Presents the dialog box shown in FIGURE 5-37.
Figure 5-37 PROXY_FTP Dialog Box for ALLOW action
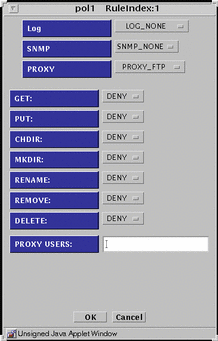
TABLE 5-38 lists the settings available for the flags for the FTP proxy.
Table 5-38 FTP Proxy Flags|
Flag |
Function |
|---|---|
|
GET |
Allow or disallow use of the FTP get command |
|
PUT |
Allow or disallow use of the FTP put command |
|
CHDIR |
Allow or disallow use of the FTP chdir command |
|
MKDIR |
Allow or disallow use of the FTP mkdir command |
|
RENAME |
Allow or disallow use of the FTP rename command |
|
REMOVE |
Allow or disallow use of the FTP remove_dir command |
|
DELETE |
Allow or disallow use of the FTP delete command |
|
PROXY USERS |
Choose the proxy user or the group of proxy users that you want for this rule. You can have only one proxy user or one group of proxy users in this field. You define these proxy users in the proxy user common object. |
-
PROXY_SMTP - Presents the dialog box shown in FIGURE 5-38.
Figure 5-38 PROXY_SMTP Dialog Box for ALLOW action
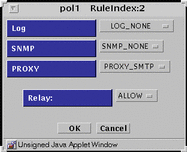
The only flag for the SMTP proxy is to allow or disallow relayed mail.
-
PROXY_Telnet - Presents the dialog box shown in FIGURE 5-39.
Figure 5-39 PROXY_Telnet Dialog Box for ALLOW action
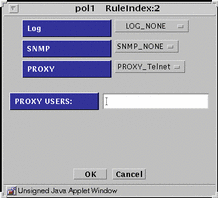
For the PROXY USER field, type the proxy user or the group of proxy users that you want for this rule from the choice list. Specify only one proxy user or one group of proxy users in this field. Define these proxy users in the proxy user common object.
- © 2010, Oracle Corporation and/or its affiliates
