









Chapter 14 |
Sun Management Center Security |
Security in Sun Management Center software is based on JavaTM security classes and SNMPv2 usec (SNMP version 2, user-based security model) security standards. This chapter discusses security features, users and groups, and their privileges.
The software offers the following layers of security:
This chapter describes the following:
The software offers the following ACL categories:
To understand ACL categories, you first need to understand Sun Management Center software users and groups. The following sections explain users and groups.
Sun Management Center users are valid UNIX users on the server host. As such, the system administrator has to add valid users into the following file;
/var/opt/SUNWsymon/cfg/esusers.If a user's name is not in this file, that user cannot log into the Sun Management Center software unless the user logs in as espublic or esmaster since these two user names are part of this file. (See the following section for more information.)
During the Sun Management Center server setup, the file /var/opt/SUNWsymon/cfg/esusers is created and the following users are added to the file automatically:
The administrator has to add the additional list of user IDs for all other users who need to log into Sun Management Center software. All users in this file have "general" access privileges, by default, unless they are given additional privileges using the procedures described in "Using Access Control".
Note - The user names espublic and esmaster are not configurable during installation. They must specifically be defined as espublic and esmaster.
General Users
Any user who is part of the esusers file is known as a "general" user. Sun Management Center general users can, by default, perform the following functions:
Sun Management Center Superuser
Implicitly, the Sun Management Center superuser belongs to all the groups described in the following sections. Sun Management Center superuser has "admin" privileges as described in "Sun Management Center Administrators or esadm".
The following groups are created by default on the server host during the Sun Management Center server setup:
In addition, all the Sun Management Center users belong to a hypothetical group, called ANYGROUP.
The above groups must be defined on the machine where the Sun Management Center Configuration manager is running. They do not need to be defined on other machines. These groups are described in greater detail in the sections that follow.
Note - The preceding groups are defined in the /etc/group file. Note that although Sun Management Center esmaster and espublic users are configured as members of the preceding groups, they are not explicitly mentioned in the
/etc/group file.
Sun Management Center software users belonging to the group esops are usually referred to as operator users who run, monitor, and to some extent, configure some parameters on the managed systems. As you can see in the following list, esops can perform operations, including some that are allowed for general users:
Software users belonging to the group esadm can perform "admin" operations, which are a superset of the operations that can be performed by operator users as described in "Sun Management Center Operators or esops". In addition to all the operations that "operator" users (esops) can perform, these "admin" users (esadms) can perform the following operations:
The users belonging to the group esdomadm can perform the following "domain administrator" operations:
Note - Other than the privileges listed above, a user belonging to "esdomadm" is just a "general" user, unless configured otherwise.
TABLE 14-1 contains the different types of functions users can do by default.
This table is general in nature and applies to all modules. Individual modules may also have specific restrictions, which are under the control of the module.
In Sun Management Center software, the above categories maintain inclusive relationships or privileges. This means that, by default, a user who has esadm privileges can do anything that a user who has esops privileges can. But an administrator has the option to change the default permissions so that a user who has esops privileges can do more than a esadm user. Inclusive relationships means that these three groups, esops, esadm, and esdomadm, do not have any code enforcement behind them which makes one group more powerful than the other.
For more information on how to override default privileges, see "Overriding the Default Privileges".
The administrators (esadm group) can specify ACL features for users and groups for the following:
An ACL specification consists of establishing or defining one or more of the following:
Users can access and view data from sessions running on remote Sun Management Center servers. When a user tries to gain access to such information, that user is provided access as espublic (guest) with read-only privileges. The behavior of Sun Management Center sessions running on different servers is defined in terms of each session's server context. See "Sun Management Center Server Context" for more information.
As a user, you can access and set up a different server context for a variety of reasons:
By linking to a different server context, you can view the top level status of the objects in the other server context.
A server context is defined as agents running on many hosts, all sharing a single set of the following central components:
A server context is defined as a collection of Sun Management Center agents and the particular server layer to which the console is connected. Agents within the same server context can talk to each other. Agents in remote server contexts can talk using read-only privileges.
Every Sun Management Center component or agent is configured at installation to know the location of its Trap handlers and Event managers. Sun Management Center software identifies the Trap handlers and the Event managers by their IP or port addresses. This means that if you want to determine if you are within your server context or are accessing information from another server context, you need to know the respective IP or port addresses of the servers that you access. Different server contexts have different port numbers.
A remote server context refers to a collection of agents and a particular server layer with which the remote agents are associated.
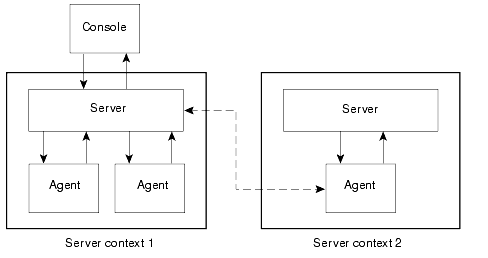
An agent gets its security configuration from the server layer. For example:
Some security restrictions apply when a user tries to communicate across server contexts.
In the current Sun Management Center environment, you can access information from another server with a few limitations:
Note - From a graphical user interface perspective, it is important to note that it may not be obvious that you are accessing a different server context. To identify if you are accessing a different server, check the server's IP port number or address in the Info tab of the Details window.
The following sections describe how to perform the following key ACL functions:
 |
To Add Sun Management Center Users |
| 1. | Become superuser (on the Sun Management Center server host). |
| 2. | Edit the file /var/opt/SUNWsymon/cfg/esusers. Make sure that the user name is that of a valid UNIX user. |
| 3. | Add the user name on a new line. |
| 4. | Save the file and exit the editor. |
Note - By adding a user to the users list, the user has default privileges. See "Default Privileges" and "Overriding the Default Privileges" for more information.
 |
To Access ACL on a Module |
| 1. | Proceed with one of the following: |
 Attribute Editor in the main console window.
Attribute Editor in the main console window.
| The Attribute Editor is displayed. The buttons at the bottom of the window are grayed out, with the exception of the Cancel and Help buttons. The remaining buttons become active if you modify any field in the window. |
| 2. | Select the Security tab within the Attribute Editor window (FIGURE 14-2). |
| 3. | Change the values as required. |
| For example, you may enter data as follows: |
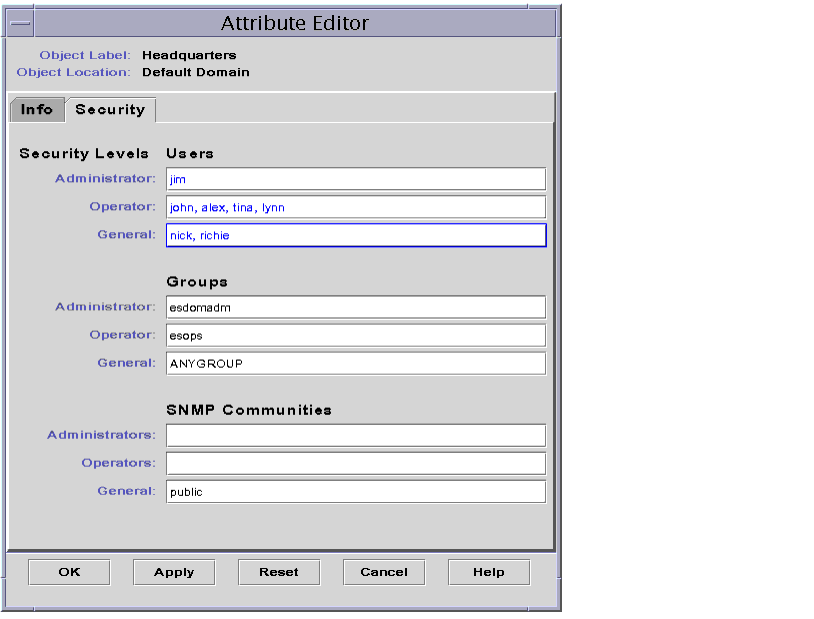
FIGURE 14-2 Example of Security Fields in the Attribute Editor
Note - Use spaces or commas between multiple entries as illustrated in the entries for "Operator" under "Users."
The preceding example of the Attribute Editor with the Security tab selected contains the following field entries:
Note - For more information on security privileges, see "Access Control Categories".
 |
To Add a User-Defined Group to an ACL |
| 1. | Become superuser. |
| 2. | Create a group:
|
| 3. | Add users to the newly created group: |
| a. | Edit the /etc/group file. |
| b. | Add users to the group. |
| c. | Save the file and exit the editor. |
| 4. | Add the new group to the ACL of interest. |
| See "To Access ACL on a Module" for more information. |
 |
To Grant a User esadm, esops, or esdomadm Privileges |
| 1. | Become superuser. |
| 2. | Make sure that the user is a valid Sun Management Center user. |
| You may do this by adding the user to the /var/opt/SUNWsymon/cfg/esusers file. |
| 3. | Edit the /etc/group file. |
| 4. | Add the user to one of the following lines as applicable: esadm, esops, or esdomadm. |
| 5. | Save the file and exit the editor. |
 |
To Delete Sun Management Center Users |
| 1. | Become superuser on the Sun Management Center server host. |
| 2. | Edit the file /var/opt/SUNWsymon/cfg/esusers. |
| 3. | Delete the line corresponding to the user name you want to delete. |
| 4. | Save the file and exit the editor. |
| 5. | Delete the user names from additional groups. |
After a user is deleted from the list of Sun Management Center users, the user can no longer log into the Sun Management Center server. Make sure to delete that user from all the ACLs.
Administrative domains are manipulated by the Topology manager. This section illustrates the default privileges for the Topology manager and for other agents and modules.
The default privileges for Topology manager (where administrative domains are maintained) are listed in the following table.
The default privileges for all other components and modules are listed in the following table.
The keyword ANYGROUP is not a true UNIX group, but is a special keyword that means that "any user who can log into Sun Management Center software is given general access to the objects."
In Sun Management Center software, only administrators can override default privileges using the Attribute Editor to modify the ACL lists for that particular object.
The following section illustrates how to override default list privileges.
 |
To Override Default Privileges |
 |
Create the following override files in the /var/opt/SUNWsymon/cfg directory: |