Chapter 4 Configuring a Directory Server
This chapter explains how to configure a directory server using the Admin Console. It describes the following tasks:
-
Starting the Admin Console
-
Performing a minimal configuration
-
Configuring security
-
Configuring LDAP parameters
-
Creating and configuring a data store
-
Indexing directory data
-
Creating and modifying access control rules
-
Configuring logging
This chapter also describes the default configuration for Sun Directory Services.
However, before you configure each directory server individually, you must define a global plan for your directory service. Chapter 3, Planning a Directory Service guides you through the decisions you need to make to set up an overall plan that covers your directory needs, naming service needs, and authentication and accounting needs.
Use the table below to find the section that describes the tasks that are not covered in this chapter.
|
Task |
Section |
|---|---|
|
Configuring the NIS service | |
|
Configuring the RADIUS service | |
|
Viewing and modifying the schema | |
|
Configuring replication | |
|
Configuring the web gateway |
Logging In for the First Time
If you have installed Sun Directory Services for the first time, you must specify a password for the administrator user. To do this, type the following command as root:
# /opt/SUNWconn/ldap/sbin/dsadmintool
You are prompted to provide a password. When you have done this, the Admin Console is displayed. You are logged in as user admin, with the password that you specified. You can change this name and password at any time from the Security section of the Admin Console. This procedure is explained in "Configuring Security".
All of the examples in this manual use the administrator name admin and the password secret.
Note -
When you log in to the Admin Console for the first time, you cannot start dsadmintool as a background process.
Displaying the Admin Console
Before you follow the instructions in this section to display the Admin Console, make sure that the Sun Directory Services administration daemon, dsadm, is running. If it is not, start it as explained in "Starting the Sun Directory Services".
This section explains three methods of displaying the Admin Console:
-
Starting the application version locally
-
Through a web server. You can download the Sun WebServer free of charge from http://www.sun.com/webserver
-
Without a web server, by pointing a web browser at the Sun Directory Services administration files
To Start the Admin Console Application
If you do not have a web server colocated with Sun Directory Services, you can also run the Admin Console locally as an application. To start it, type the following command as root:
/opt/SUNWconn/ldap/sbin/dsadmintool &
The Admin Console is displayed, as shown in Figure 4-1.
Figure 4-1 Admin Console Main Window
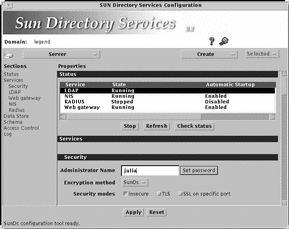
To Display the Admin Console Remotely through a Web Server
-
Create a symbolic link from the documentation root directory for your web server to /opt/SUNWconn/html:
prompt% cd docroot_dir prompt% ln -s /opt/SUNWconn/html sds
where docroot_dir is the documentation root directory for your web server.
Your web server must be running on the same machine as the dsservd daemon.
-
If you are using the HotJava browser, change the default security level by editing the .hotjava/properties file in your home directory.
Use any text editor to change the following line from:
hotjava.default.security=medium
to:
hotjava.default.security=low
If you have not used the HotJava browser before, you must create the .hotjava/properties file and add the line hotjava.default.security=low.
-
Start the HotJava browser on any machine, and point it at the Admin Console:
prompt% /usr/dt/bin/hotjava http://hostname/sds/dsadmin.html
where hostname is the hostname of the machine running the Sun Directory Services and the web server.
-
Log in to the Admin Console using the name and password of the administrator user.
The Admin Console is displayed.
To Display the Admin Console Locally without a Web Server
-
If you are using the HotJava browser , change the default security level by editing the .hotjava/properties file in your home directory. Use any text editor to change the following line from:
hotjava.default.security=medium
to:
hotjava.default.security=low
If you have not used the HotJava browser before, you must create the .hotjava/properties file and add the line hotjava.default.security=low.
-
Start the HotJava browser with the following path to point it at the administration files:
prompt% /usr/dt/bin/hotjava file:/opt/SUNWconn/html/dsadmin.html
-
Log in to the Admin Console using the name and password of the administrator user.
The Admin Console is displayed.
Minimal Configuration
When you install the Sun Directory Services, most configurable characteristics are given default settings that enable you to start and run a directory server. However, you must:
-
Give a name to the naming context held in the data store. For details, see "Configuring the Data Store".
-
Specify the location of the data store on the disk. For details, see "Configuring the Data Store".
When you have specified this information your directory server has a default configuration.
Default LDAP Configuration
The LDAP directory service has the following characteristics:
-
Alias dereferencing on bind operations is enabled.
-
Searches are limited to 5000 entries or 3600 seconds (1 hour). A search stops when the first of these limits is reached.
-
5000 entries are cached. A cache file of 100,000 bytes is created for each data store.
-
Default indexing is used, as described in "Indexing Directory Data".
-
Passwords are stored in encrypted format.
-
Default access control is used, as described in Example 1-1.
-
The schema is checked for each directory operation, as described in "Schema Checking".
-
The directory contains no entries (the name and password for the administrator are stored in the configuration file).
Default RADIUS Configuration
The RADIUS service has the following characteristics:
-
The ports used for RADIUS communications are port 1645 for authentication traffic, and port 1646 for accounting traffic. However, recent standardization work suggests to use port 1812 for authentication traffic, and port 1813 for accounting traffic. If you want to use these ports, you can specify them using the Admin Console.
-
The RADIUS server is disabled.
Default Web Gateway Configuration
The web gateway has the following characteristics:
-
The templates used to configure the display of directory information are /etc/opt/SUNWconn/ldap/current/locale/C/dswebtmpl.conf.
Default NIS Configuration
The NIS service is disabled.
Starting and Stopping Services
At any time, you can independently start or stop the following components of Sun Directory Services from the Admin Console.
-
LDAP
-
NIS
-
RADIUS
-
Web gateway
The Admin Console also enables you to specify whether you want any of these components except LDAP to restart automatically when the server daemon, dsservd, is restarted.
-
From the Admin Console main window, in the Status section, select the service that you want to start or stop.
-
For each service, verify the status for Automatic Restart at boot time. Change it as necessary.
-
Click Apply to save your changes.
Configuring Security
You can configure the security level you require for your directory server by setting the administrator's name and password, defining the encryption method for all passwords stored in the directory, and specifying the security mode for your server.
Specifying the Administrator Name and Password
You can change the name and password of the administrator user at any time.
-
From the Admin Console main window, in the Security section, specify the name and password for the directory administrator.
The administrator name and password are stored in the configuration file dsserv.conf, so that the administrator always has access to the directory. This is necessary so that the administrator can solve problems with access control, for example.
By default, the administrator's password is encrypted using the default encryption method. If you want the password to be stored unencrypted, choose None from the Encryption method menu.
-
Click Apply to save your changes.
Specifying the Encryption Method
The encryption method you specify is used to encrypt the userPassword attribute that you can store in directory entries. There are two encryption methods:
-
sunds: a reversible encryption mechanism compatible with CRAM MD5 authentication
-
crypt(3): the encryption mechanism commonly applied to passwords stored in the /etc/passwd file. This method is not reversible and is incompatible with the CRAM MD5 authentication mechanism.
-
From the Admin Console main window, in the Security section, select the Encryption method for passwords from the menu button.
The possible choices are: None, sunds, crypt.
-
Click Apply to save your changes.
Specifying the Security Mode
You can specify a security mode that guarantees that authentication takes place between the server and the client during the bind process, or that the entire communication between the server and the client is encrypted. You can also allow insecure binding. These options are not mutually exclusive. The security mode used for a particular connection is actually negotiated between the client and the server.
-
From the Admin Console main window, in the Security section, specify the Security modes supported by the server.
The options are:
-
TLS: establishes a secure connection at any time during an LDAP session by calling the Start TLS extended operation
-
SSL on Specific Port: opens a secure connection on the specified port (by default, port 636)
You can enable several options.
-
Specify the following parameters:
If you have selected TLS or SSL on Specific Port:
-
The SSL key package (usually the IP address of the host)
-
Whether you want the server to authenticate clients: set the SSL Client Verification flag to On
If you have selected SSL on Specific Port:
-
A port number to use for SSL connections
-
-
Click Apply to save your changes.
Note -Due to legal restrictions in certain countries, SSL is not available worldwide.
Configuring LDAP Parameters
In the Admin Console, use the LDAP section under Services to configure the following properties of the LDAP server:
-
The port used by the directory server daemon, dsservd.
-
Whether alias entries are to be dereferenced when a bind request is received.
-
Search limits (number of entries and time).
-
The default directory server for referrals, and the LDAP port number of the referral server. Give the name of a server that holds knowledge information on subtrees not managed by the current server. This should be a server that holds a broader view of the same tree, to allow searches in the current tree to be extended through the referral. To define referrals to different trees, use referral entries.
Configuring the Data Store
To configure a data store, you must specify the distinguished name of the naming context that identifies the data store, and the name of the directory where the database files reside. Optional configuration information includes:
-
Additional naming contexts stored (see "Naming Contexts")
-
Cache size (see "Caching" for information about caching)
-
Congestion thresholds (see "Congestion Thresholds" for information about the congestion monitoring system and setting thresholds)
-
Which attributes are indexed (see "Indexing Directory Data" for information about indexing)
-
Whether any of the naming contexts held in the data store are replicated to other servers (see "Setting Up Replication")
"To Create a Data Store" gives step-by-step instructions for creating a new data store. "To Modify a Data Store or Naming Context" explains how to modify an existing data store.
To Rename the Default Data Store
In your initial configuration, you must specify the distinguished name of the naming context that identifies the data store on the server, and the directory where the data store files are held.
-
In the Admin Console main window, highlight the default data store o=XYZ, c=US, in the Data Store section and choose Modify from the Selected menu.
Alternatively, you can double-click on the default data store o=XYZ, c=US. The Modify Data Store window is displayed, as shown in Figure 4-2.
Figure 4-2 Modify Data Store Window
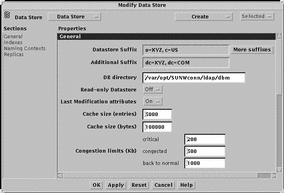
-
Modify the data store suffix to reflect the distinguished name of the naming context that the directory server will store.
If you intend to initialize the NIS service, you must modify the suffix made up of dc elements so that this naming context can contain the NIS domain managed by the server.
If you want the data store to hold more than one naming context, you can specify additional naming suffixes by clicking the More Suffixes button. If necessary, use the Set button to specify the distinguished name. "Using the DN Editor" explains how to enter a DN in the Admin Console.
-
Specify the path name to the directory where the data store is to be held.
For a default configuration, you do not need to specify any other information. For more information about creating a data store, see "Creating or Modifying a Data Store".
Creating or Modifying a Data Store
This section gives information on the options you can configure when creating or modifying a data store. It also guides you through the steps for performing these tasks.
Naming Contexts
A data store can be identified by up to four suffixes. A suffix corresponds to a naming context. The term naming context also applies to any subtree under a data store suffix. In the Admin Console, the Data Store section displays the naming contexts held in the data store. This list contains the data store suffixes plus any naming contexts created under the data store suffixes.
The distinguished name of a naming context corresponds to the base DN you specify when you perform a directory operation such as a search, or when you configure an LDAP client application.
You can specify a DN that conforms to the OSI tree structure (for example o=XYZ, c=US), or a DN that reflects your organization's DNS naming structure, through a sequence of domain components (for example dc=XYZ, dc=com).
A data store can contain a mixture of master and replica (slave) naming contexts, some or all of which can be replicated to other servers. For information on replication, refer to Chapter 9, Implementing Replication.
Note -
You can modify the DN of a data store only when the data store is empty.
Caching
As information is retrieved from the directory it is saved in the cache. When the cache is full, the oldest entry is discarded to make room for new information. Retrieving information from the cache is faster than retrieving entries from the database, but a large cache occupies more memory.
Default value for cache size is 5000 entries.
Congestion Thresholds
Congestion thresholds ensure that the directory does not become overloaded, by preventing new operations from starting when there are insufficient resources.
-
When the available disk space reaches the congested limit, add operations are no longer permitted, though modify, modify RDN (modrdn), search, read, and delete operations are allowed. The default limit is 500 Kbytes.
-
When the database reaches the critical limit, only search, read, and delete operations are allowed, and add, modify, and modrdn operations are not permitted. The default limit is 200 Kbytes.
-
The restrictions remain in force until the remaining disk space becomes greater than the back-to-normal limit. The default limit is 1000 Kbytes.
If your database reaches the congested limit, after deleting unnecessary entries, you must still regenerate the database to optimize the use of disk space. Refer to "Regenerating the Database".
Threshold values are given in Kbytes free on the disk holding the data store. The default location for the data store is /var/opt/SUNWconn/ldap/dbm.
To Create a Data Store
-
In the Admin Console, choose Data Store from the Create menu.
The Create Data Store window is displayed. It is similar to the Modify Data Store window shown in Figure 4-2.
-
In the General Section, in the Data Store Suffix field, specify the distinguished name of the naming context stored in this data store.
To specify more than one naming context, click the More Suffixes button.
-
Specify the path name to the directory where this database is to be stored.
-
Specify whether the data store is read-only or not.
By default, it is not.
-
Specify whether the last modification attributes should be recorded.
When this option is enabled, the creator's DN, a creation timestamp, the modifier's DN, and a modification timestamp are added in the entry. This enables you to search the directory for entries created or modified since a particular date or time. This can be useful if you are synchronizing changes across data stores, or you are using partial replication.
-
Specify the cache size limit, in entries and in bytes.
See "Caching" for details.
-
Specify congestion thresholds.
See "Congestion Thresholds" for details.
-
Optionally, you can specify which attributes to index in the database.
See "To Create Indexes" for details.
-
In the Naming Contexts section, specify the master and slave subtrees held in this data store.
These are naming contexts that are subtrees or objects under the naming context used to name the data store. If you do not specify any naming contexts, the distinguished name of the data store itself is added to the list of master naming contexts automatically, but it is not displayed until you save the naming contexts information. See "Naming Contexts" for details.
-
Choose Naming Context from the Create menu.
The Add Naming Context window is displayed. Figure 4-3 shows the appearance of the window when Slave mode is selected.
Figure 4-3 Add Naming Context window (Slave Mode)
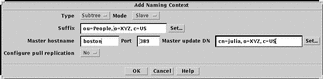
-
Specify:
-
The subtree type (subtree or object)
-
The DN of the subtree or object in the Suffix field
-
The mode (master or slave)
-
-
If the naming context is a replica (slave), specify:
-
The name of the server from which it is replicated in the Master hostname field
-
The Master Update DN that dspushd will use when the master initiates the bind to replicate changes.
-
Whether you want the slave to pull updates from the master. If so, see "To Create Replicas" for details on how to specify the bind parameters.
-
-
Click OK to save the naming context information.
The new naming context is displayed in the Naming Contexts section.
-
-
Optionally, you can replicate any of the stored naming contexts to a different server.
If you do, you must create the naming context on the target server following the procedure described in Step 9, because the replication procedure does not create it automatically. See "Setting Up Replication" for details.
-
Click OK in the Create Data Store window to save the data store definition.
-
Add a directory entry for the root of the data store.
See "Creating the Root Entry" for details of how to add an entry to the directory. You cannot add any entries to this data store until this root entry exists.
To Modify a Data Store or Naming Context
To modify a data store, select the data store you want to modify from the Data Store list, and choose Modify Data Store or Modify Naming Context from the Selected menu.
Alternatively, you can double-click on your selection. The current characteristics of the data store or naming context are displayed. You can modify any part of the configuration, apart from a data store suffix, when the data store is not empty.
Indexing Directory Data
A data store can contain a number of attribute indexes to help optimize the speed of access to directory information. An attribute index is a list of entries containing a given attribute or attribute value. You can index attributes using any of the following matching rules:
-
Equality - Optimizes direct access to entries where an exact attribute value is supplied.
-
Presence - Optimizes searches with filters specifying the presence of an attribute but no specific value (cn=*, for example).
-
Substring - Optimizes searches with filters containing a partially-specified attribute value (cn=adr*, for example). Substring indexing uses all possible combinations of three successive letters. For example, if cn=adrianne, the substring indexes are: adr, dri, ria, ian, ann, nne. This type of index is longer to generate and is the most costly in terms of disk space.
-
Approximate - Optimizes searches with approximate match filters. The method used in approximate indexing is to discard vowels.
In a data store having the default characteristics, the following attributes are indexed:
-
commonName, surname, mail, mailHost, and givenName are indexed by presence, equality, approximate match and substring match
-
uid is indexed by presence and equality
-
preferredRfc822Recipient, rfc822Mailbox, cCMailAddress, pROFSAddresses, mSMailAddresses are indexed by presence and equality
The advantage of indexing is that it optimizes access for indexed attributes. The disadvantages are that it uses more disk space, and that adding and modifying entries takes longer.
When you add or modify an entry after an index has been created, the index is automatically updated. However, if you create a new index and the data store already contains entries, those entries are not automatically included in the index. Indexes are not automatically updated when entries are removed from the directory, so the size of the index files does not reduce as entries are removed.
To update all the indexes defined in a data store, choose Refresh Index from the Data Store menu of the data store window (see "Directory Maintenance".) Regenerating the indexes for a data store can take several minutes, depending on the number and complexity of the indexes defined. For example, regenerating the default indexes for a data store of 20,000 entries takes approximately five minutes.
To Create Indexes
-
Whether you are creating a new data store or modifying an existing one, select Index from the Create menu.
The Add Index window is displayed.
-
Specify the name of the indexed attribute and the index types.
Use the Set button to select attributes from a list. You can specify several attributes separated by commas. These indexed attributes will have the same index types.
-
Click Apply to add the index.
Backing Up and Restoring a Data Store
The backup function enables you to create a backup of the information held in your directory database in text format. The restore option enables you to restore your database from a set of backup files.
To Back Up a Data Store
-
To back up a data store, double-click on the data store in the Data Store list to display it.
The Modify Data Store window is displayed.
-
Click the Data Store pull-down menu, and select Backup.
A selector window is displayed.
-
Use the selector window to select or create a directory for your backup.
-
Click Save.
To Restore a Data Store
-
To restore a data store, double-click on the data store in the Data Store list to display it.
The Modify Data Store window is displayed.
-
Click the Data Store pull-down menu, and select Restore.
A selector window is displayed.
-
Select the directory containing the backed up data store that you want to restore.
The default selection is the previous backup directory.
-
Click Load.
The directory service is restarted with the restored data store.
Configuring Access Control
Access controls determine who has access to a given directory entry, and what level of access is granted. "Access Control" explains how to design an access control policy for your directory. The following sections explain how to configure default access, and add, modify, and delete access control rules.
An access control rule defines the level of access to specific directory information given to a particular user. There are two stages to defining a new access control rule:
-
Specify the directory information to which the rule applies. This is the information that you want to protect.
-
Specify the level of access granted to each user for this information. From the most restrictive to the most permissive, levels of access are: none, compare, search, read, write.
Access control rules are ordered, with the most specific rules first, followed by more general rules. The first rule in the list that matches the requested operation is applied, the following rules in the list are ignored.
Default access is the level of access granted to entries and attributes for which access control is not specifically defined.
Configuring Default Access
-
In the Admin Console main window, go to the Access Control section.
-
Use the Default Access menu button to select a level of access.
By default, this option is set to read.
To Add an Access Control Rule
-
Choose Access Control from the Create menu.
The Create Access Control Rule window is displayed.
-
Specify the information to which the new rule will apply, as follows:
-
From the Selected Entries menu, select the method of specifying the entries.
You can specify entries using a DN-based regular expression, an LDAP filter, or you can specify that the rule applies to all entries.
-
If you selected DN-based regular expression, type the regular expression in the Distinguished name field, or click Set to use the Distinguished Name Editor to specify the regular expression.
If you want to protect only certain attributes within the set of entries defined by the regular expression, click the Attribute Set button and select the attributes to be protected. If you do not specify any attributes, all attributes in the specified entries are protected.
-
If you selected LDAP filter, click the LDAP filter Set button to launch the LDAP Filter Editor. Specify the filter, and click Apply.
If you want to protect only certain attributes within the set of entries defined by the regular expression, click the Attribute Set button and select the attributes to be protected. If you do not specify any attributes, all attributes in the specified entries are protected.
-
-
Type the name of an attribute to be protected in the Attributes field.
To see a list of attributes, click the Set button. You can specify any number of attributes.
-
-
Choose Access Rule from the Create menu.
The Add User Rule window is displayed.
-
Select the Rule type. This defines the set of users to which the rule applies.
You can specify a rule for Everyone, DN-based Regular Expression, Self (that is, the entity described by the entry), Address, Domain, or Member Attribute.
-
If you selected Everyone, the rule will apply to all users whose directory entries contain this attribute.
-
If you selected DN-based Regular Expression, specify the regular expression for the set of users to which the rule applies. The rule will apply to all users who bind with a distinguished name that matches the regular expression.
You can type the distinguished name directly in the field, or you can click Set to use the Distinguished Name editor to construct the distinguished name. See "Using the DN Editor" for more information about how to specify a distinguished name.
-
If you selected Address, specify an IP address.
The IP address can contain wildcards. The rule will apply to all users who bind from the specified IP address.
-
If you selected Domain, specify a domain name.
The domain name can contain wildcards. The rule will apply to all users who bind from the specified domain.
-
If you selected Member Attribute, specify an attribute.
The rule will allow the DN used in the bind to be added to or removed from the list of members specified by the attribute.
-
-
Specify the access rights to be granted to the specified set of users.
-
Click Apply to add the rule.
You can then define other rules for entries you have selected. When you have created and added all the rules for these entries, click Cancel to dismiss the Add User Rule window. Figure 4-4 shows a new ACL created to authorize users to update their own homePhone and homePostalAddress attributes.
Figure 4-4 Create Access Control Window
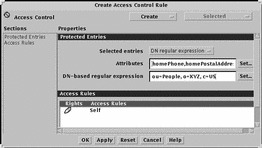
-
In the Create Access Control Rule window, click Apply to store the new rules.
You can then select another set of entries and define access controls for them, as described in Step a.
Configuration changes are implemented when you restart the dsservd daemon.
To Modify an Access Control Rule
-
Select the set of entries whose access control you want to modify, and choose Modify ACL from the Selected menu.
The Modify Access Control Rule window is displayed. If you double-click a rule, this window is displayed automatically.
-
Select the rule that you want to modify, and choose Modify Access Rule from the Selected menu.
The Modify User Rule window is displayed. If you double-click the rule you want to modify, the Modify User Rule window is displayed automatically.
-
Make the modification you require.
-
Click Apply.
Make any other modifications you require. When you have made and applied all the modifications, click Cancel to dismiss the Modify User Rule window.
-
Click OK in the Modify Access Control Rule window.
These changes will take effect when you restart the dsservd daemon.
To Delete an Access Control Rule
To delete all access control rules for a set of entries, select the entry set and choose Delete ACL from the Selected menu.
You are prompted to confirm that you want to delete all access controls for the set of entries.
To delete one rule from an ACL:
-
Select the set of entries and choose Modify ACL from the Selected menu.
The Modify Access Control Rule window is displayed.
-
Select the rule you want to delete and choose Delete User Rule from the Selected menu.
You are prompted to confirm that you want to delete this rule.
To Reorder Access Control Rules
In the Access Control section of the main window, select the rule you want to move, and choose Move Up or Move Down from the Selected menu.
When the rules are reordered as you require, click Apply to save the changes to the configuration file. The changes are implemented when you restart the dsservd daemon.
Note -
The Admin Console will display a warning message if you break the convention of placing the rules from the more specific to the more general.
Configuring Logging
You can configure the following parameters for the log:
-
Log directory
-
Log file size
-
Trace level
-
Which logs to display (LDAP, web gateway, NIS, RADIUS), and the length of the display
Go to the Log section of the Admin Console main window to configure these parameters.
The log directory /var/opt/SUNWconn/ldap/log contains the following log files:
-
dsnmpserv.log -- the log file for the SNMP agent that monitors the dsservd daemon
-
dsnmprad.log -- the log file for the SNMP agent that monitors the dsradiusd daemon
-
dsserv_admin.log -- the log file for the Admin Console server
-
dspush.log -- the log file for the dspushd replication process
-
dspull.log -- the log file for the dspulld replication process
You can change the name of the default log directory but you cannot modify the names of the log files themselves.
By default the maximum size of a log file is 500Kb. The maximum size is the same for all log files. When this limit is reached, the log is renamed by appending a .1 suffix, and a new log file is created. When that log reaches the size limit, it is in turn renamed. You can have up to ten files for each log.
Note -
Log files can use up to 40 Mbytes of disk space, or more if you increase the default log file size. Therefore, it is necessary to clean up log files regularly.
The available trace levels are:
-
None
-
Light
-
Medium
-
Full
Backing Up and Restoring the Configuration
The Admin Console enables you to back up your directory service configuration at any time and save as many configurations as you want. You can restore any of your backed up directory service configurations.
To Back Up the Configuration
-
In the Admin Console, click the Server pull-down menu and choose Backup Config.
If the directory service damon dsservd is running, you are prompted to stop it. When it is stopped, a selector window is displayed.
-
Use the selector window to select or create a directory for your backup.
-
Click Save.
To Restore a Configuration
-
In the Admin Console, click the Server pull-down menu and select Restore Config.
If the directory service damon dsservd is running, you are prompted to stop it. When it has stopped, a selector window is displayed.
-
Select the directory containing the backed up configuration that you want to restore.
The default selection is the /etc/opt/SUNWconn/ldap/backup directory.
-
Click Load.
The directory service is restarted with the restored configuration.
Displaying Server Characteristics
You can display the characteristics of the directory server at any time, using the following command:
/opt/SUNWconn/bin/ldapsearch -h host -b "" -s base 'objectclass=*'
host is the hostname of the directory server whose characteristics you want to display. The output from this command is similar to:
objectclass=top namingcontexts=O=XYZ,C=US namingcontexts=DC=XYZ,DC=COM subschemasubentry=cn=schema supportedsaslmechanisms=CRAM-MD5 supportedcontrol=1.2.840.113556.1.4.319 supportedcontrol=2.16.840.1.113730.3.4.2 supportedcontrol=1.3.6.1.4.1.1466.20035 supportedldapversion=2 supportedldapversion=3 |
Using the DN Editor
A distinguished name (DN) is a sequence of relative distinguished names (RDNs), separated by a comma, for example o=XYZ, c=US. When you have to specify a DN in the Admin Console, you can type it directly into the field supplied, or you can construct it using the Distinguished Name Editor.
Regular Expressions in Distinguished Names
You can specify a DN that contains a regular expression to indicate a set of entries. This is useful when configuring access control, for example, but not when specifying a naming context. The Admin Console does not prevent you from entering a regular expression in any DN, but you should use wildcards only where it is appropriate. See the regex(1F) man page for information about regular expressions.
You can specify a regular expression for the distinguished name of an entry. For example, the regular expression dn="cn=Joe Smith, ou=.*, o=XYZ, c=US" specifies the set of entries for people called Joe Smith in the whole of the XYZ Corporation.
You can also use a DN-based regular expression to specify a set of values for an attribute whose values are DNs. For example, you can grant write access to a distribution list entry to any person whose DN is a value of the member attribute, using the regular expression member="dn=.*".
To Create a Distinguished Name with the DN Editor
-
Start the DN Editor by clicking the Set Button to the right of the field where you must enter a DN.
The DN Editor dialog box is displayed.
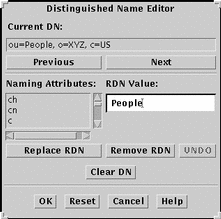
Figure 4-5 Distinguished Name Editor
-
Use the Previous and Next buttons to position the cursor where you want to add an RDN, or to highlight an RDN that you want to replace.
If you position the cursor between two RDNs, the dialog box has an Add RDN button. If you highlight an RDN, this button is replaced by a Replace RDN button.
-
Select the Naming Attribute for the RDN, and type the value in the RDN value field.
-
Click the Add RDN button or Replace RDN button.
-
Click Apply to save the new DN, and click Cancel to dismiss the DN Editor dialog box.
To Modify a Distinguished Name with the DN Editor
-
Start the DN Editor by clicking the Set Button to the right of the field containing the DN to modify.
The DN Editor dialog box is displayed.
-
Use the Previous and Next buttons to position the cursor where you want to insert an RDN, or select the existing RDN that you want to replace.
-
Select the Attribute Type for the RDN, and type the value in the RDN value field.
-
Click the Modify RDN button.
-
Click Apply to save the new DN, and click Cancel to dismiss the DN Editor dialog box.
Using the Filter Editor
An LDAP filter is a way of specifying a set of entries, based on the presence of a particular attribute or attribute value. You can use an LDAP filter in an access control rule. For example, the default access control rules include a filter specifying that users can add their own DNs to the member attribute of any entry that contains the attribute joinable with a value of TRUE. This allows users to add or remove their names from distribution lists.
The Current Filter field shows the filter you are modifying, or the current state of the filter you are creating.
To Create an LDAP Filter
-
Click the Set button to the right of the field where you need to specify a filter.
The Filter Editor is displayed.
Figure 4-6 Filter Editor Dialog Box
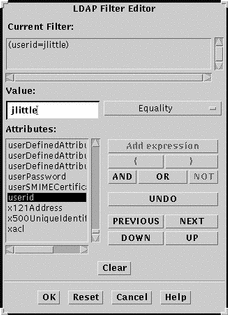
-
Select an attribute from the list displayed.
-
Type a value in the Value field.
-
Select a match type from the pull-down menu.
-
Click AND, OR, or NOT, to indicate how this expression is used in the filter.
-
Click Add Expression to add the expression to the filter.
The Current Filter field shows the modified filter.
-
Repeat from Step 3 to Step 6 until the Current Filter field shows the filter as you want it.
-
Click Apply to save the filter, and click Cancel to dismiss the Filter Editor dialog box.
To Modify an LDAP Filter
-
Click the Set button to the right of the field where you need to specify a filter.
The Filter Editor is displayed, as shown in Figure 4-6.
The Current Filter field shows the filter to be modified.
-
Position the cursor where you want to add an expression, or select the expression that you want to modify.
-
Select an attribute from the list displayed.
-
Type a value in the Value field.
-
Select a match type from the pull-down menu.
-
Click AND, OR, or NOT, to indicate how this expression is used in the filter.
-
Click Add Expression to add the expression to the filter.
The Current Filter field shows the modified filter.
-
Repeat from Step 3 to Step 7 until the Current Filter field shows the filter as you want it.
-
Click Apply to save the filter, and click Cancel to dismiss the Filter Editor dialog box.
- © 2010, Oracle Corporation and/or its affiliates
