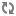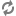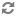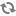Access control within secured repositories is managed by building ACLs that associate certain access rights with certain identities (not just individual users, but also groups, organizations, and roles that may be associated with many users). The following table lists the access rights defined by the secured repository system. Not all access rights are necessarily available in all implementations or instances of a secured repository.
Access Right | Available Scopes | Description |
|---|---|---|
CREATE | RepositoryItemDescriptor | Determines the ability to create a new repository item with an item descriptor. In order to add the new item to the repository you must also have WRITE access to the item descriptor. |
DELETE | RepositoryItemDescriptor | Determines the ability to remove a repository item from an item descriptor. In order to delete an Item you must also have DESTROY access for that Item. |
DESTROY | RepositoryItem | Determines the ability to remove the repository item from the repository, destroying its contents. Note that most secured repositories will also require DELETE access on the item descriptor. |
LIST | RepositoryItem | Determines the ability for a repository item to be queried. If LIST access is not given for a repository item, the item will never be returned from a query. If you wish to also grant access to a repository item’s properties, you should additionally use the READ access right. An item’s owner implicitly has LIST access. |
READ | RepositoryItemDescriptor | Determines the ability to request a repository item from an item descriptor, or to inspect the contents of a repository item or a property in a repository item. |
READ_ACL | RepositoryItem | Determines the ability to inspect the ACL of a repository item. This access right is implicitly granted to the owner of a repository item. |
READ_OWNER | RepositoryItem | Determines the ability to inspect the owner of a repository item. |
WRITE | RepositoryItemDescriptor | Determines the ability to add a repository item to an item descriptor, or to change the contents of a repository item or a property in a repository item. If the WRITE access right is granted for the item descriptor, it does not affect the ability to update a repository item, only the ability to add new repository items. |
WRITE_ACL | RepositoryItem | Determines the ability to change the ACL of a repository item. This access right is implicitly granted to the owner of a repository item. |
WRITE_OWNER | RepositoryItem | Determines the ability to change the owner of a repository item. |
It is important to remember that the secured repository does not provide complete security within an application, since the unprotected repository that it sits on top of is still available within the Nucleus name space. The intent is to provide a repository that aids in creating secure applications, not one that protects the data from rogue programmers. The ATG Control Center may be configured to hide unprotected repositories, and an application may choose not to use an unprotected repository, so as not to expose unprotected data to an end user.