29.2 Registering OSSO Agents Using Oracle Access Management Console
You can manage OSSO Agent registrations (mod_osso) using the Oracle Access Management Console.
See:
29.2.1 Understanding the Create OSSO Agent Registration Page and Parameters
OSSO Agent registration use the Oracle Access Management Console.
Note:
Before you register an OSSO Agent, ensure that the Oracle HTTP Server is installed on the client computer and that the Web server is configured for mod_osso.
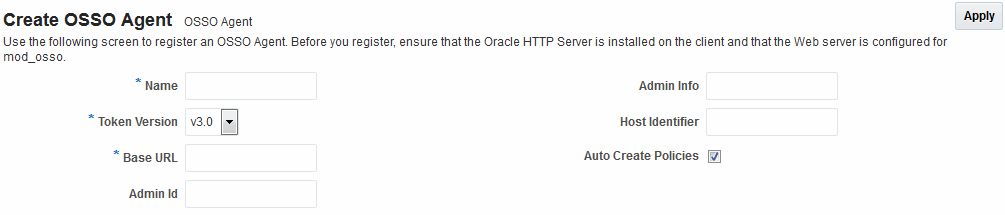
Table 29-3 shows a Create OSSO Agent page, under the System Configuration tab in the Oracle Access Management Console.
On the Create OSSO Agent page, required information is identified by the asterisk (*). Table 29-3 describes the required and optional details that you can specify when you register a new agent.
Table 29-3 Create OSSO Agent Page Elements
| Element | Description |
|---|---|
|
Name |
The identifying name for this mod_osso Agent. |
|
Token Version |
The default version of the token is 3.0; the following options are available:
|
|
Base URL Required for OSSO agents. |
The required protocol, host, and port of the computer on which the Web server for the agent is installed. For example, http://host.example.domain.com:port or https://example.domain.com:port. Note: The host and port are used as defaults for the expanded registration. See Table 29-5. |
|
Admin ID |
Optional Administrator log in ID for this mod_osso instance. For example, SiteAdmin. |
|
Admin Info |
Optional Administrator details for this mod_osso instance. For example, Application Administrator. |
|
Host Identifier |
The host identifier is filled in automatically based on the Agent name. |
|
Auto Create Policies |
During agent registration, you can have authentication and authorization policies created automatically. This option is checked (enabled) by default. The OSSO Proxy requires an Application Domain that includes a resource with the generic URL (/**) protected by a policy based on the LDAP scheme (default). This is why a generic URL is used at the server side. Default: Enabled Notes: If you already have a domain and policies registered, you can simply add new resources to it. If you clear (uncheck) this option, no Application Domain or policies are generated automatically. In an upgraded deployment, you must change the Authentication Scheme in your Authentication Policy to use SSOCoExistMigrateScheme. |
To help streamline Agent registration, several elements are concealed and default values are used during registration with the console. When you view an agent's registration page in the Oracle Access Management Console, all elements and values appear.
29.2.1.1 About the OSSO Agent Configuration File
The OSSO Agent configuration file, osso.conf, is updated during agent registration and configuration changes. It is stored on the console host (AdminServer).
Following registration or configuration updates, you must relocate the artifacts to the mod_osso directory path on the Agent host as shown in Table 29-4.
Table 29-4 Relocating OSSO Artifacts
| From AdminServer . . . | To OHS_dir/osso.conf |
|---|---|
|
$DOMAIN_HOME/output/$Agent_Name/ |
|
29.2.2 Registering an OSSO Agent (mod_osso) Using the Console
Users with Oracle Access Management Administrator credentials can register an OSSO Agent using the Oracle Access Management Console.
You must meet the following prerequisites for the registration of an OSSO agent:
The Oracle HTTP Server must be installed and run on the client computer, and must also be configured for mod_osso.
To register an OSSO Agent: