3.1.1 Getting Started with Running Compliance Checks
Review these topics to get started with Oracle Autonomous Health Framework compliance checking.
- Running Oracle Orachk or Oracle Exachk as a Non-Root User
You can optionally run Oracle Orachk or Oracle Exachk as a non-root user. - Non-Root Users Running Root Privileged Checks on Database Servers
Non-root user can runrootprivileged checks on the database servers without requiringrootpassword orsudo. - Automatic Compliance Checking
Use the daemon to configure automatic compliance check runs at scheduled intervals. - Email Notification and Report Overview
The following sections provide a brief overview about email notifications and sections of the HTML report output. - Recommended On-Demand Usage
This section summarizes the scenarios that Oracle recommends running compliance checks on-demand. - Running Compliance Checks on a Remote Node
Run compliance checks on remote nodes using RSA/DSA SSH private and public keys. - Creating, Modifying, and Deleting User-Defined Profiles
Specify a comma-delimited list of check IDs to create and modify custom profiles. - Sanitizing Sensitive Information in the Diagnostic Collections
Oracle Autonomous Health Framework uses Adaptive Classification and Redaction (ACR) to sanitize sensitive data. - Problem Repair Automation Options
Starting in release 19.3, Oracle Orachk and Oracle Exachk have the capability to automatically fix problems when found. - Integration of Oracle DBSAT into Oracle Autonomous Health Framework
DBSAT is a lightweight utility that will not impair system performance in a measurable way. - Integration of AutoUpgrade utility into Oracle Autonomous Health Framework
TheAutoUpgradeutility identifies issues before upgrades, performs pre- and postupgrade actions, deploys upgrades, performs postupgrade actions, and starts the upgraded Oracle Database. - Enhanced Activity Logging Framework for Oracle Exachk/Oracle Orachk
AHF 25.11 introduces a new activity logging framework designed to improve diagnostics, observability, and automated analysis across Oracle Exachk and Oracle Orachk executions.
Parent topic: Compliance Checking with Oracle Orachk and Oracle Exachk
3.1.1.1 Running Oracle Orachk or Oracle Exachk as a Non-Root User
You can optionally run Oracle Orachk or Oracle Exachk as a non-root user.
root and if non-root users run Oracle Orachk or Oracle Exachk and want to change the directory to their own output location, then the non-user will not be able to browse any directory using ls -l in the path before their own output location. However, they can directly cd to the output location.$ cd /u01/app/crsusr/oracle.ahf/data/host_name/
$ ls -ltra
ls: cannot open directory .: Permission denied
$ cd orachk
$ ls
ls: cannot open directory .: Permission denied
$ cd user_racusr
$ ls -l
total 7456
-r-xr-xr-x 1 root root 6836 Jun 1 13:37 cgrep
rw-rr- 1 root root 5481 Jun 1 13:37 cgrep.pyc
drwxr-xr-x 7 racusr oinstall 274432 Jun 1 14:05 orachk_host_name_ratcdb_060120_133414
rr---- 1 racusr oinstall 7323951 Jun 1 14:05 orachk_host_name_ratcdb_060120_133414.zip
drwx-----T 2 racusr root 4096 Jun 1 14:05 output
drwx-----T 4 racusr root 4096 Jun 1 14:05 work
Non-root users can copy the path of Oracle Orachk run result and cd directly there, or copy the result. Alternatively, they can run the ahfctl showrepo command and it will show them the correct location where their results are available.
$ ahfctl showrepo
<<output truncated>>
orachk repository: /u01/app/crsusr/oracle.ahf/data/host_name/orachk/user_racusr/outputRelated Topics
Parent topic: Getting Started with Running Compliance Checks
3.1.1.2 Non-Root Users Running Root Privileged Checks on Database Servers
Non-root user can run root privileged checks on the database
servers without requiring root password or
sudo.
privileged-compliance-checks role, non-root user can run Oracle Orachk with the -runasroot option to run root privileged checks.
Parent topic: Getting Started with Running Compliance Checks
3.1.1.3 Automatic Compliance Checking
Use the daemon to configure automatic compliance check runs at scheduled intervals.
Installing Oracle Autonomous Health Framework as root on Linux or Solaris automatically sets up Oracle Orachk or Oracle Exachk to use the Oracle Trace File Analyzer scheduler daemon.
The daemon runs a full local Oracle Orachk check once every week at 3 AM, and a partial run of the most impactful checks at 2 AM every day through the oratier1 or exatier1 profiles. The daemon automatically purges the oratier1 or exatier1 profile run that runs daily, after a week. The daemon also automatically purges the full local run after 2 weeks. You can change the daemon settings after enabling auto start.
orachk -autostopexachk -autostop
orachk -autostop unsetexachk -autostop unset
Note:
- Daemon mode is supported only on the Linux and Solaris operating systems.
- If you have an Oracle Engineered System, then in addition to the following usage steps, follow the system-specific instructions.
Related Topics
Parent topic: Getting Started with Running Compliance Checks
3.1.1.3.1 Running Oracle Orachk or Oracle Exachk Scheduler With the Oracle Trace File Analyzer Daemon
Oracle Trace File Analyzer scheduler:
- Decides which is the master node.
- Picks the Oracle Orachk or Oracle Exachk entries only on the master node.
- Runs only on the master node.
- Runs Oracle Orachk or Oracle Exachk clusterwide.
- Consolidates all the output on the master node.
- Enters which is the master node in the logs.
- Notifies through email that points to the master node where the report output is stored.
Example 3-1 Default configuration of Oracle Oracle Orachk/Oracle Exachk scheduler and daemon information
# orachk -autostatus
Master node = testserver
orachk daemon version = 221000
Install location = /opt/oracle.ahf/orachk
Started at = Wed Jun 22 20:56:51 UTC 2022
Scheduler type = TFA Scheduler
Scheduler PID: 1766980
------------------------------------------------------------
ID: orachk.autostart_client_oratier1
------------------------------------------------------------
AUTORUN_FLAGS = -usediscovery -profile oratier1 -dball -showpass -tag autostart_client_oratier1 -readenvconfig
COLLECTION_RETENTION = 7
AUTORUN_SCHEDULE = 3 2 * * 1,2,3,4,5,6
------------------------------------------------------------
------------------------------------------------------------
ID: orachk.autostart_client
------------------------------------------------------------
AUTORUN_FLAGS = -usediscovery -tag autostart_client -readenvconfig
COLLECTION_RETENTION = 14
AUTORUN_SCHEDULE = 3 3 * * 0
------------------------------------------------------------
Next auto run starts on Jun 23, 2022 02:03:00
ID:orachk.AUTOSTART_CLIENT_ORATIER1Related Topics
3.1.1.4 Email Notification and Report Overview
The following sections provide a brief overview about email notifications and sections of the HTML report output.
- First Email Notification
After completing compliance check runs, the daemon emails the assessment report as an HTML attachment to all users that you have specified in theNOTIFICATION_EMAILlist. - What does the Compliance Check Report Contain?
Compliance check reports contain the health status of each system grouped under different sections of the report. - Subsequent Email Notifications
For the subsequent compliance check runs after the first email notification, the daemon emails the summary of differences between the most recent runs. - Generating a Diff Report
The diff report attached to the previous email notification shows a summary of differences between the most recent runs.
Parent topic: Getting Started with Running Compliance Checks
3.1.1.4.1 First Email Notification
After completing compliance check runs, the daemon emails the assessment report as an HTML attachment to all users that you have specified in the NOTIFICATION_EMAIL list.
Parent topic: Email Notification and Report Overview
3.1.1.4.2 What does the Compliance Check Report Contain?
Compliance check reports contain the health status of each system grouped under different sections of the report.
The HTML report output contains the following:
- Health score
- Summary of compliance check runs
- Table of contents
- Controls for report features
- Findings
- Recommendations
Details of the report output are different on each system. The report is dynamic, and therefore the tools display certain sections only if applicable.
System Health Score and Summary
System Health Score and Summary report provide:
- A high-level health score based on the number of passed or failed checks
- A summary of compliance check run includes:
- Name, for example, Cluster Name
- Version of the operating system kernel
- Path, version, name of homes, for example, CRS, DB, and EM Agent
- Version of the component checked, for example, Exadata
- Number of nodes checked, for example, database server, storage servers, InfiniBand switches
- Version of Oracle Orachk and Oracle Exachk
- Name of the collection output
- Date and time of collection
- Duration of the check
- Name of the user who ran the check, for example,
root - How long the check is valid
Table of Contents and Report Feature
The Table of Contents section provides links to major sections in the report:
- Database Server
- Storage Server
- InfiniBand Switch
- Cluster Wide
- Maximum Availability Architecture (MAA) Scorecard
- Infrastructure Software and Configuration Summary
- Findings needing further review
- Platinum Certification
- System-wide Automatic Service Request (ASR) compliance check
- Skipped Checks
- Top 10 Time Consuming Checks
The Report Feature section enables you to:
- Filter checks based on their statuses
- Select the regions
- Expand or collapse all checks
- View check IDs
- Remove findings from the report
- Get a printable view
Report Findings
The Report Findings section displays the result of each compliance check grouped by technology components, such as Database Server, Storage Server, InfiniBand Switch, and Cluster Wide.
Each section shows:
- Check status (
FAIL,WARNING,INFO, orPASS) - Type of check
- Check message
- Where the check was run
- Link to expand details for further findings and recommendation
Click View for more information about the compliance check results and the recommendations.
- What to do to solve the problem
- Where the recommendation applies
- Where the problem does not apply
- Links to relevant documentation or My Oracle Support notes
- Example of data on which the recommendation is based
Maximum Availability Architecture (MAA) Score Card
Maximum Availability Architecture (MAA) Score Card displays the recommendations for the software installed on your system.
The details include:
- Outage Type
- Status of the check
- Description of the problem
- Components found
- Host location
- Version of the components compared to the recommended version
- Status based on comparing the version found to the recommended version
Related Topics
Parent topic: Email Notification and Report Overview
3.1.1.4.3 Subsequent Email Notifications
For the subsequent compliance check runs after the first email notification, the daemon emails the summary of differences between the most recent runs.
Specify a list of comma-delimited email addresses in the NOTIFICATION_EMAIL option.
The email notification contains:
-
System Health Score of this run compared to the previous run
-
Summary of number of checks that were run and the differences between runs
-
Most recent report result as attachment
-
Previous report result as attachment
-
Diff report as attachment
Parent topic: Email Notification and Report Overview
3.1.1.4.4 Generating a Diff Report
The diff report attached to the previous email notification shows a summary of differences between the most recent runs.
To identify the changes since the last run:
Related Topics
Parent topic: Email Notification and Report Overview
3.1.1.5 Recommended On-Demand Usage
This section summarizes the scenarios that Oracle recommends running compliance checks on-demand.
$ orachk
$ exachkOracle recommends that you run compliance checks in the following on-demand scenarios:
-
Pre- or post-upgrades
-
Machine relocations from one subnet to another
-
Hardware failure or repair
-
Problem troubleshooting
-
In addition to go-live testing
While running pre- or post-upgrade checks, Oracle Autonomous Health Framework automatically detects the databases that are registered with Oracle Clusterware and presents the list of databases to check.
$ orachk –u –o pre
$ exachk –u –o pre$ orachk –u –o post
$ exachk –u –o postRelated Topics
Parent topic: Getting Started with Running Compliance Checks
3.1.1.6 Running Compliance Checks on a Remote Node
Run compliance checks on remote nodes using RSA/DSA SSH private and public keys.
Ensure that passwordless SSH between the local node and remote node is present. ssh –i id_encryption.remote_host.remote_user remote_user@remote_host must be able to log in to the remote_host without any password.
Parent topic: Getting Started with Running Compliance Checks
3.1.1.6.1 Synchronous Remote Run
This is a blocking-call. Outputs the stdout of the remote run. User gets the prompt or control only when the remote run is completed. Once completed, the collection will be available at the working directory.
# orachk –remotehost remote_host remote_args -remoteuser remote_user -remotedestdir remote_dest_dir -identitydir PRIVATEKEYDIR# exachk –remotehost remote_host remote_args -remoteuser remote_user -remotedestdir remote_dest_dir -identitydir PRIVATEKEYDIRorachk -remotehost node2 -profile asm -remoteuser root -remotedestdir /scratch/user/ -identitydir /scratch/user/privatekeys/exachk -remotehost node1 -localonly -c X4-2,MAA -remoteuser oracle -remotedestdir /scratch/user/ -identitydir /scratch/user/privatekeys/$ orachk -remotehost node2 -profile asm -remoteuser root -remotedestdir /scratch/user1/ -identitydir .privatekeys/
Starting orachk run on node2. For more detail about run check /scratch/user1/orachkremote/orachk_node2_112818_040034_run.log
Clusterware stack is running from /scratch/app/11.2.0.4/grid. Is this the correct Clusterware Home?[y/n][y]
Checking ssh user equivalency settings on all nodes in cluster for rootParent topic: Running Compliance Checks on a Remote Node
3.1.1.6.2 Asynchronous Remote Run
This is a non-blocking-call. Oracle Orachk and Oracle Exachk initiate the remote run, display a _run.log file, and give control to the user. Check the _run.log file to ensure the completion of the remote run. Once completed, the collection will be available at the working directory
# orachk –remotehost remote_host remote_args -remoteuser remote_user -remotedestdir remote_dest_dir -identitydir PRIVATEKEYDIR -asynch# exachk –remotehost remote_host remote_args -remoteuser remote_user -remotedestdir remote_dest_dir -identitydir PRIVATEKEYDIR -asynch- remote_host is the host name of the remote node.
- remote_args are the arguments that needs to be passed to the Oracle Orachk and Oracle Exachk run in the remote node.
- remote_user is the remote user who runs Oracle Orachk and Oracle Exachk.
- remote_dest_dir is the remote
directory where
orachk.ziporexachk.zipis extracted. - PRIVATEKEYDIR is the directory contains the private keys of the remote nodes in the specified format.
Note:
If you use DSA keys, then set theRAT_SSH_ENCR environment variable to dsa before running the Oracle Orachk and Oracle Exachk remote run commands.
orachk -remotehost node2 -remoteuser oradb -remotedestdir /scratch/user/ -identitydir /scratch/user/privatekeys/ -asynchexachk -remotehost node1 -cells node1 -c X4-2,MAA -remoteuser root -remotedestdir /scratch/user/ -identitydir /scratch/user/privatekeys/ -asynch$ orachk -remotehost node2 -localonly -remoteuser root -identitydir .privatekeys/ -asynch
Starting orachk run on node2. For more detail about run check /scratch/user1/orachkremote/orachk_node2_112818_041037_run.log$ ls PRIVATEKEYDIR/
id_dsa.node1.oracle id_dsa.node4.root id_dsa.node6.oracle id_dsa.node8.root id_dsa.node11.oracle
id_dsa.node2.root id_dsa.node5.oracle id_dsa.node6.root id_dsa.node9.root
id_dsa.node3.root id_dsa.node5.root id_dsa.node7.root id_dsa.node10.oracleParent topic: Running Compliance Checks on a Remote Node
3.1.1.7 Creating, Modifying, and Deleting User-Defined Profiles
Specify a comma-delimited list of check IDs to create and modify custom profiles.
Parent topic: Getting Started with Running Compliance Checks
3.1.1.8 Sanitizing Sensitive Information in the Diagnostic Collections
Oracle Autonomous Health Framework uses Adaptive Classification and Redaction (ACR) to sanitize sensitive data.
Note:
The -sanitize parameter has been deprecated and
removed in 23.3. Oracle recommends using the ahfctl redact
command instead.
After collecting copies of diagnostic data, Oracle Orachk and Oracle Exachk use Adaptive Classification and Redaction (ACR) to sanitize sensitive data in the collections. ACR uses a machine learning based engine to redact a pre-defined set of entity types in a given set of files. ACR also sanitizes or masks entities that occur in path names.
- Sanitization replaces a sensitive value with random characters.
- Masking replaces a sensitive value with a series of asterisks ("*").
ACR currently sanitizes the following entity types:
- Host names
- IP addresses
- MAC addresses
- Oracle Database names
- Tablespace names
- Service names
- Ports
- Operating system user names
ACR also masks Personally Identifiable Information (PII), that is, user data from the database appearing in block and redo dumps. There is no separate command for it.
To sanitize sensitive information:
orachk -sanitize comma_delimited_list_of_collection_IDsor
exachk -sanitize comma_delimited_list_of_collection_IDs14A533F40 00000000 00000000 00000000 002C0000 [..............,.]
14A533F50 35360C02 30352E30 31322E37 380C3938 [..650.507.2189.8]
14A533F60 31203433 37203332 2C303133 360C0200 [34 123 7310,...6]14A533F40 ******** ******** ******** ******** [****************]
14A533F50 ******** ******** ******** ******** [****************]
14A533F60 ******** ******** ******** ******** [****************]col 74: [ 1] 80
col 75: [ 5] c4 0b 19 01 1f
col 76: [ 7] 78 77 06 16 0c 2f 26col 74: [ 1] **
col 75: [ 5] ** ** ** ** **
col 76: [ 7] ** ** ** ** ** ** **To print the reverse map of sanitized elements:
orachk -rmap all|comma_delimited_list_of_element_IDs
or
exachk -rmap all|comma_delimited_list_of_element_IDsParent topic: Getting Started with Running Compliance Checks
3.1.1.8.1 Sanitizing Sensitive Information in Oracle Orachk or Oracle Exachk Output
Note:
The -sanitize parameter has been deprecated and
removed in 23.3. Oracle recommends using the ahfctl redact
command instead.
3.1.1.8.2 Setting up Staging Server for Adaptive Classification and Redaction (ACR)
Adaptive Classification and Redaction (ACR) is a CPU intensive task as it examines data in each file to redact sensitive entities. ACR spawns multiple processes to redact the files across these processes. Whenever an ACR process is scheduled on a CPU, it may utilise the CPU fully (can reach ~100% CPU utilisation). But, since ACR does not run at an elevated priority, it does not starve other processes on the system. However, since ACR is sharing the resources with other processes running on the production environment, it can affect those processes. Hence, to not affect the processes and applications on the production environment, it is recommended to set up a staging server dedicated for redacting the collections using ACR.
For more information about setting up staging server for Adaptive Classification and Redaction (ACR), see My Oracle Support note 2882798.1.
Related Topics
3.1.1.9 Problem Repair Automation Options
Starting in release 19.3, Oracle Orachk and Oracle Exachk have the capability to automatically fix problems when found.
-showrepair
command.orachk -showrepair check_id
exachk -showrepair check_idorachk -repair all
orachk -repair check_id,[check_id,check_id...]orachk -repair fileexachk -repair all
exachk -repair check_id,[check_id,check_id...]
exachk -repair file- check_id: Refers to specific checks that you want to repair. Specify a check ID or a list of comma-delimited list of check IDs.
-
file: A text file that contains a list of check IDs.
Add one check ID per line.
For example:
check ID1 check ID2 check IDn
Parent topic: Getting Started with Running Compliance Checks
3.1.1.10 Integration of Oracle DBSAT into Oracle Autonomous Health Framework
DBSAT is a lightweight utility that will not impair system performance in a measurable way.
- Analyzes database configurations
- Users and their entitlements
- Security policies
- Identifies where sensitive data resides to uncover security risks (not executed in Oracle Autonomous Health Framework)
- Improves the security posture of Oracle Databases within your organization
Oracle Autonomous Health Framework always includes the latest DBSAT and runs DBSAT on all databases if you use the -security profile. For example, orachk -profile security.
ahfctl compliance -profile security- Fix immediate short-term risks
- Implement a comprehensive security strategy
- Support your regulatory compliance program
- Promote security best practices
Figure 3-1 Oracle Database Security Assessment Report
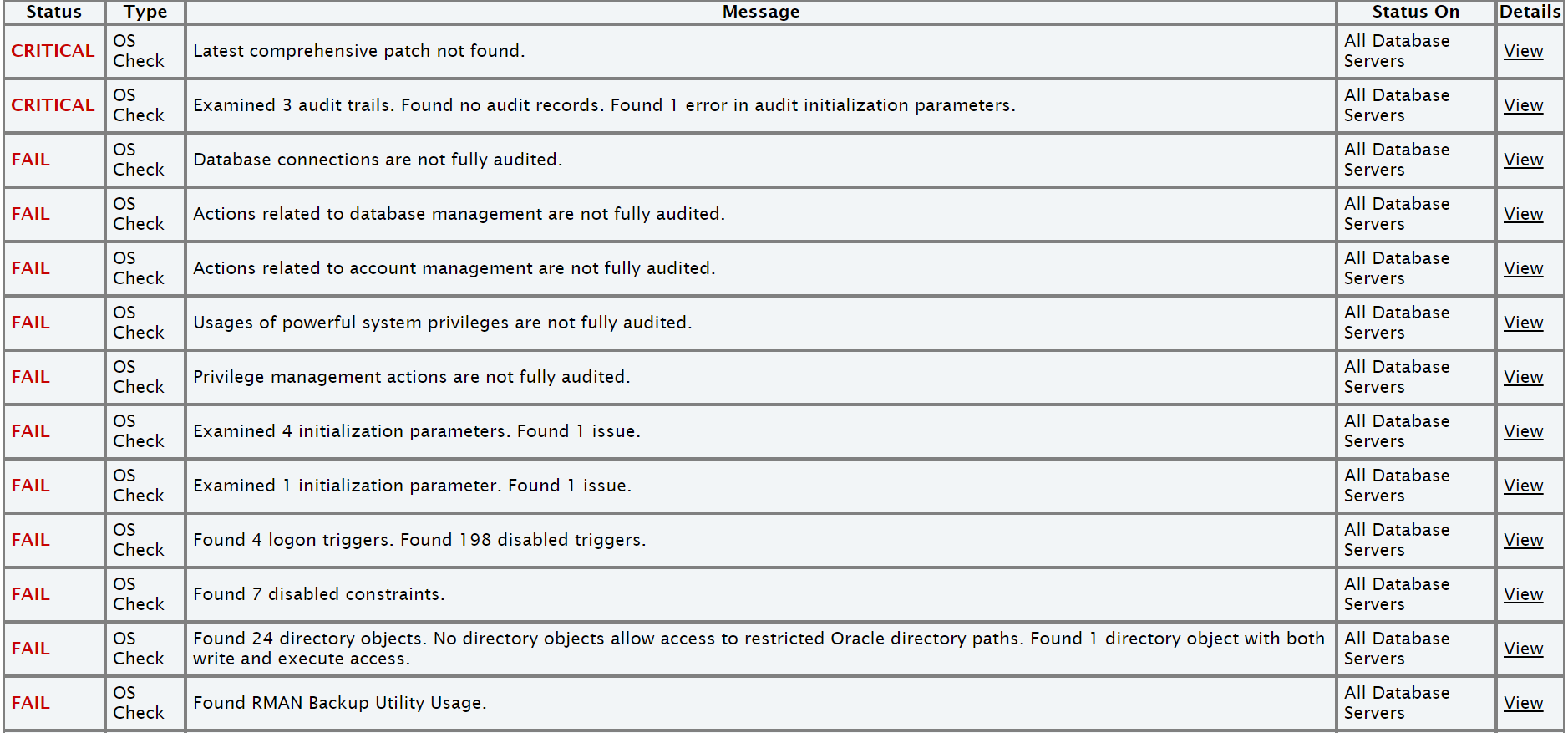
Description of "Figure 3-1 Oracle Database Security Assessment Report"
For more information, see Oracle Database Security Assessment Report.
Related Topics
Parent topic: Getting Started with Running Compliance Checks
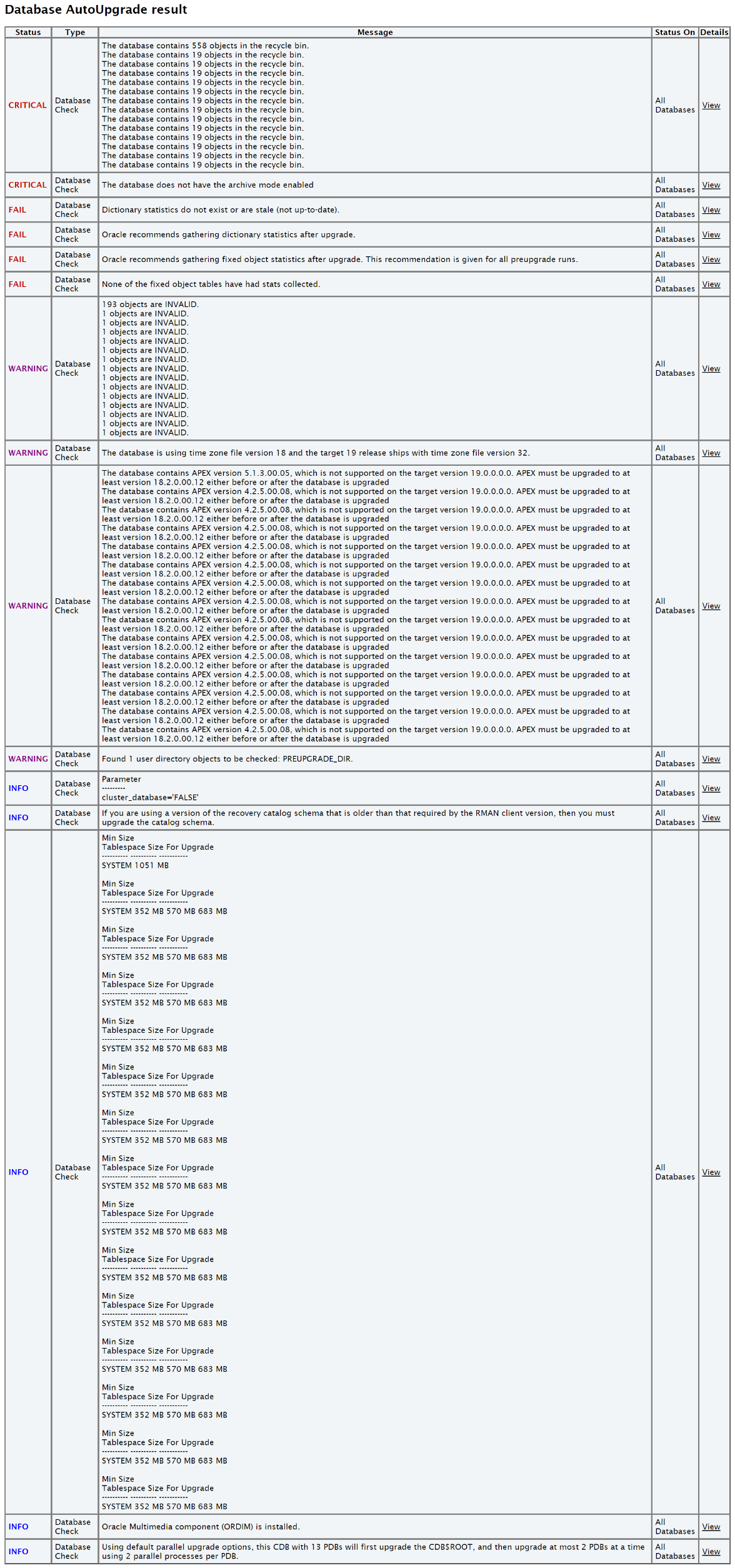
3.1.1.11 Integration of AutoUpgrade utility into Oracle Autonomous Health Framework
The AutoUpgrade utility identifies issues before upgrades, performs pre- and postupgrade actions, deploys upgrades, performs postupgrade actions, and starts the upgraded Oracle Database.
Before the upgrade, in Analyze mode, the AutoUpgrade utility performs read-only analysis of databases before upgrade, so that it can identify issues that require fixing.
When you run Oracle Orachk in pre-upgrade mode, Oracle Orachk in turn runs the AutoUpgrade utility to check if each database is ready to upgrade or not.
For more information, see Using AutoUpgrade for Oracle Database Upgrades.
Related Topics
Parent topic: Getting Started with Running Compliance Checks
3.1.1.12 Enhanced Activity Logging Framework for Oracle Exachk/Oracle Orachk
AHF 25.11 introduces a new activity logging framework designed to improve diagnostics, observability, and automated analysis across Oracle Exachk and Oracle Orachk executions.
This enhancement enables the collection, storage, and correlation of detailed execution logs, making it easier to identify unhealthy systems, and analyze long-term trends.
These activity logs will be automatically collected during Oracle Exachk/Oracle Orachk runs, updated in predefined locations, and included as part of Oracle Trace File Analyzer collections for streamlined troubleshooting.
Objectives
- Capture insightful and structured logs from every Oracle Exachk/Oralce Orachk run.
- Maintain metadata activity logs, check activity logs, environment logs, and runtime logs across multiple runs.
- Provide users with accessible activity logs, ensuring that all registered Exachk users can view logs from their own runs.
What this logging enhances
- Identify unhealthy systems
- Highlight high-severity, high-frequency failures
- Correlate check failures with system degradation
- Detect persistent issues across multiple runs
- Spot increasing error counts indicating system decline
Who can access activity logs?
All registered users authorized to run Oracle Exachk can access the activity logs associated with their runs.
Platform support
This capability is available on all platforms supported by Oracle Exachk/Oracle Orachk.
Log management and lifecycle
Activity logs will be stored and maintained using standard log management practices:
- Log rotation
- Activity log files will be rotated when they exceed 250 KB.
- Retention policy
- Logs from the latest 10 runs will be retained.
- When the count exceeds 10, the oldest log will be deleted.
Summary of benefits
- Improves system health monitoring through historical context
- Enables proactive identification of recurring or escalating issues
Parent topic: Getting Started with Running Compliance Checks