| Oracle® Application Server Administrator's Guide 10g (10.1.4.0.1) Part Number B28185-01 |
|
|
View PDF |
| Oracle® Application Server Administrator's Guide 10g (10.1.4.0.1) Part Number B28185-01 |
|
|
View PDF |
When you installed Oracle Application Server, you chose an installation type and the components you wanted to configure. For Identity Management installations, you could choose whether or not to configure Oracle Delegated Administration Services or OracleAS Single Sign-On. After installation, you may want to configure these components. Or, you may want to start using Infrastructure Services with your J2EE and Web Cache installation. This chapter describes how to make these types of changes.
It contains the following topics:
If you have disabled anonymous binds in Oracle Internet Directory, you must enable them before you make configuration changes. See Section 7.5, "Disabling and Enabling Anonymous Binds" for more information.
|
Note: In this chapter, discussions of middle-tier installations or J2EE and Web Cache installations refer to Release 2 (10.1.2) or Release 3 (10.1.3) instances. |
When you installed Oracle Application Server, you were allowed to select the components you wanted to configure. You may decide later you want to configure one of the components you did not select during installation. For example, if you installed Oracle Infrastructure and did not choose to configure Single Sign-On Authority, you can configure Single Sign-On Authority after installation.
You can configure components after installation using the Select Component page in the Application Server Control Console. From the Home page, click Configure Component. The Select Component page is displayed, as shown in Figure 7-1.
Figure 7-1 Configuring Components with Application Server Control Console
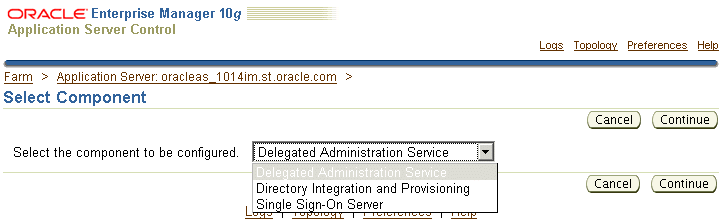
Table 7-1 lists which components can be configured after installation and provides pointers to instructions for using Application Server Control Console to configure and verify each component.
Table 7-1 Components That Can Be Configured After Installation
| To configure this component: | In these Installation types: | For instructions, refer to: |
|---|---|---|
|
Single Sign-On |
Infrastructure |
|
|
Delegated Administration Service |
Infrastructure |
|
|
Oracle Directory Integration Platform |
Infrastructure |
|
This section describes how to configure OracleAS Single Sign-On after installation.
To configure OracleAS Single Sign-On, take the following steps:
Using the Application Server Control Console, navigate to the Application Server Home page for the Infrastructure instance in which you want to configure OracleAS Single Sign-On.
On the Application Server Home page, in the System Components section, click Configure Component.
On the Select Component page, select Single Sign-On Server. Click Continue.
On the Login page:
User Name: Enter cn=orcladmin, or the distinguished name of a user in the iASAdmins group.
Password: Enter the password for the user.
The SSL Only check box is grayed out because you cannot change this feature in this operation.
Click Finish.
When the configuration is finished, take the following steps:
In the Application Server Control Console Confirmation page, click OK. The Application Server Home page appears.
If you did not have an OC4J_SECURITY instance before, you will have one now. The OC4J_SECURITY instance will have a status of Down. You will also have a Single Sign-On:orasso instance with a status of Down. Select the check box next to OC4J_SECURITY and click Start.
Note: You cannot start the Single Sign-On:orasso instance. This feature is started and stopped when you start and stop HTTP_Server and OC4J_SECURITY.
When the operation completes, verify that OC4J_SECURITY has a status of Up.
Note: The Single Sign-On:orasso status may be displayed as Down. This is normal. The status should be updated approximately five minutes after configuration.
Select HTTP_Server and click Restart.
Verify that you can access OracleAS Single Sign-On at the following URL:
http://hostname.domain:port/pls/orasso
In the URL, hostname.domain is the host on which OracleAS Single Sign-On is installed and port is the Infrastructure HTTP Server port.
In the OracleAS Single Sign-On Welcome page, log in as orcladmin with the orcladmin password.
|
See Also: Oracle Application Server Single Sign-On Administrator's Guide for more information on configuring OracleAS Single Sign-On |
This section describes how to configure Oracle Delegated Administration Services after installation.
When you configure Oracle Delegated Administration Services after installation, you will see the following results:
The URL for Oracle Delegated Administration Services is set up.
The appropriate privileges are created.
Oracle Delegated Administration Services are deployed in the OC4J_SECURITY instance.
Before you configure Oracle Delegated Administration Services, you must make sure mod_osso is configured, as follows:
Check if mod_osso is configured in the Oracle home where you want to configure Oracle Delegated Administration Services. Examine the following file:
On UNIX systems:
ORACLE_HOME/Apache/Apache/conf/httpd.conf
Look for the following line in the file:
include "ORACLE_HOME/Apache/Apache/conf/mod_osso.conf"
On Windows systems:
ORACLE_HOME\Apache\Apache\conf\httpd.conf
Look for the following line in the file:
include "ORACLE_HOME\Apache\Apache\conf\mod_osso.conf"
ORACLE_HOME refers to the directory where you want to configure Oracle Delegated Administration Services.
If the line starts with #, then it is commented out and mod_osso is not configured in this installation. Perform step 2 to configure mod_osso.
If the line is not commented out, mod_osso is already configured. You can proceed and configure Oracle Delegated Administration Services using Application Server Control, as described in Section 7.1.2.2.
To configure mod_osso, perform these steps:
Set the ORACLE_HOME environment variable to the full path of the directory where you want to configure Oracle Delegated Administration Services.
On UNIX systems, set the LD_LIBRARY_PATH, LD_LIBRARY_PATH_64, LIB_PATH, or SHLIB_PATH environment variables to the proper values, as shown in Table 1-1. The actual environment variables and values that you have to set depend on the type of your UNIX operating system.
On Windows systems, set the PATH environment variable to contain %ORACLE_HOME%\lib.
Run the following command (all on one line). Note: for the -classpath parameter, do not type any space characters after the colon (:) and semicolon (;) characters, as indicated by <no spaces>.
On UNIX:
$ORACLE_HOME/jdk/bin/java -classpath .:$ORACLE_HOME/sso/lib/ossoreg.jar:<no spaces> $ORACLE_HOME/jlib/ojmisc.jar:<no spaces> $ORACLE_HOME/jlib/repository.jar:<no spaces> $ORACLE_HOME/j2ee/home/jazn.jar:$ORACLE_HOME/jdk/lib/dt.jar:<no spaces> $ORACLE_HOME/jdk/lib/tools.jar:$ORACLE_HOME/jlib/infratool.jar oracle.ias.configtool.UseInfrastructure i -f $ORACLE_HOME/config/infratool_mod_osso.properties -h OIDhost -p OIDport -u OIDadminName -w OIDclearTextPassword -o ORACLE_HOME -m ASinstanceName -infra infraGlobalDBName -mh host -sso true -sslp sslPort -sslf false
On Windows:
%ORACLE_HOME%\jdk\bin\java -classpath .;%ORACLE_HOME%\sso\lib\ossoreg.jar;<no spaces> %ORACLE_HOME%\jlib\ojmisc.jar;<no spaces> %ORACLE_HOME%\jlib\repository.jar;<no spaces> %ORACLE_HOME%\j2ee\home\jazn.jar;<no spaces> %ORACLE_HOME%\jdk\lib\dt.jar;<no spaces> %ORACLE_HOME%\jdk\lib\tools.jar;%ORACLE_HOME%\jlib\infratool.jar oracle.ias.configtool.UseInfrastructure i -f %ORACLE_HOME%\config\infratool_mod_osso.properties -h OIDhost -p OIDport -u OIDadminName -w OIDclearTextPassword -o ORACLE_HOME -m ASinstanceName -infra infraGlobalDBName -mh host -sso true -sslp sslPort -sslf false
Table 7-2 describes the parameters that require values.
Table 7-2 Parameters for Configuring mod_osso
| Parameter | DescriptionFoot 1 |
|---|---|
|
|
Specifies the name of the computer where Oracle Internet Directory is running. You can determine this value from the |
|
Specifies the port number on which Oracle Internet Directory is listening. You can determine this value from the |
|
|
|
Specifies the login name for Oracle Internet Directory. Use the superuser: |
|
|
Specifies the password for the Oracle Internet Directory user. |
|
|
Specifies the full path to the directory where you installed OracleAS Infrastructure 10g. |
|
|
Specifies the name of the OracleAS Infrastructure 10g instance where you want to configure mod_osso. You can determine this value from the |
|
|
Specifies the name of the OracleAS Metadata Repository database. You can determine this value from the |
|
|
Specifies the full hostname (including the domain name) of the computer where you want to configure Oracle Delegated Administration Services. |
|
|
Specifies whether or not SSO is enabled. Specify true or false. |
|
|
Specifies whether or not the instance is configured for SSL-only access. Specify true or false. |
|
Specifies the SSL port for Oracle Internet Directory. You can determine this value from the |
Footnote 1 Paths are shown in UNIX format; invert the slashes for Windows.
If you needed to perform the previous step, restart OC4J and Oracle HTTP Server, using the opmnctl command:
On UNIX systems:
ORACLE_HOME/opmn/bin/opmnctl restartproc ias-component=OC4J ORACLE_HOME/opmn/bin/opmnctl restartproc ias-component=HTTP_Server
On Windows systems:
ORACLE_HOME\opmn\bin\opmnctl restartproc ias-component=OC4J ORACLE_HOME\opmn\bin\opmnctl restartproc ias-component=HTTP_Server
To configure Oracle Delegated Administration Services, take the following steps:
Using the Application Server Control Console, navigate to the Application Server Home page for the Infrastructure instance in which you want to configure Oracle Delegated Administration Services.
On the Application Server Home page, in the System Components section, click Configure Component.
On the Select Component page, select Delegated Administration Service. Click Continue.
On the Login page:
User Name: Enter cn=orcladmin.
Password: Enter the password for the user.
The SSL Only check box is grayed out because you cannot change this feature in this operation.
Click Finish.
When the configuration is finished, take the following steps:
In the Application Server Control Console Confirmation page, click OK. The Application Server Home page appears.
If you did not have an OC4J_SECURITY instance before, you will have one now. The OC4J_SECURITY instance will have a status of Down. Select the check box next to OC4J_SECURITY and click Start.
Select HTTP_Server and click Restart.
Stop and restart all components, using the opmnctl command:
On UNIX systems:
ORACLE_HOME/opmn/bin/opmnctl stopall ORACLE_HOME/opmn/bin/opmnctl startall
On Windows systems:
ORACLE_HOME\opmn\bin\opmnctl stopall ORACLE_HOME\opmn\bin\opmnctl startall
Verify that Oracle Delegated Administration Services is started by navigating to the following URL:
http://hostname.domain:port/oiddas
In the URL, hostname.domain is the host on which Oracle Delegated Administration Services is installed and port is the Infrastructure HTTP Server port.
|
See Also: Oracle Internet Directory Administrator's Guide for more information on configuring Oracle Delegated Administration Services |
To configure Oracle Directory Integration Platform after installation, take the following steps:
Using the Application Server Control Console, navigate to the Application Server Home page for the Infrastructure instance in which you want to configure Oracle Directory Integration Platform.
On the Application Server Home page, in the System Components section, click Configure Component.
On the Select Component page, select Directory Integration and Provisioning. Click Continue.
On the Login page:
User Name: Enter cn=orcladmin.
Password: Enter the password for the user.
The SSL Only check box is grayed out because you cannot change this feature in this operation.
Click Finish.
When the configuration is finished, click OK. The Application Server Home page appears.
|
See Also: Oracle Internet Directory Administrator's Guide for more information on configuring Oracle Directory Integration Platform |
After you have configured a component, you cannot deconfigure it. An alternative is to disable the component, which prevents it from starting when you start your application server instance. It also removes the component from the System Components list in the Application Server Control Console, and from the opmnctl status output. Section 3.4, "Enabling and Disabling Components" describes how to disable a component.
Guidelines for deleting OC4J instances are as follows:
You cannot delete OC4J instances that were created by Oracle Application Server during installation.
These include OC4J_FED and OC4J_SECURITY. An alternative is to disable an OC4J instance, which prevents it from starting when you start your application server instance. It also removes the component from the System Components list on the Application Server Control Console, and from the opmnctl status output.
You can delete OC4J instances that were created by a user after installation.
Deleting these instances removes all applications deployed to the instance. You can delete an OC4J instance using dcmctl or the Application Server Control Console.
To delete an OC4J instance using dcmctl:
(UNIX) ORACLE_HOME/dcm/bin/dcmctl removeComponent -co OC4J_instance_name (Windows) ORACLE_HOME\dcm\bin\dcmctl removeComponent -co OC4J_instance_name
For example, on UNIX:
ORACLE_HOME/dcm/bin/dcmctl removeComponent -co OC4J_myapps
To delete an OC4J instance using the Application Server Control Console:
Navigate to the Application Server Home page for the instance that contains the OC4J instance.
In the System Components section, select the check box for the OC4J instance and click Delete OC4J Instance.
You can configure a Release 2 (10.1.2.0.2) J2EE and Web Cache or a Release 3 (10.1.3) middle-tier instance to use a 10g (10.1.4.0.1) OracleAS Infrastructure.
You do this by using the Infrastructure page on the Application Server Control Console. Figure 7-2 shows the Infrastructure page for a Release 2 (10.1.2.0.2) middle tier.
Figure 7-2 Application Server Control Console Infrastructure Page
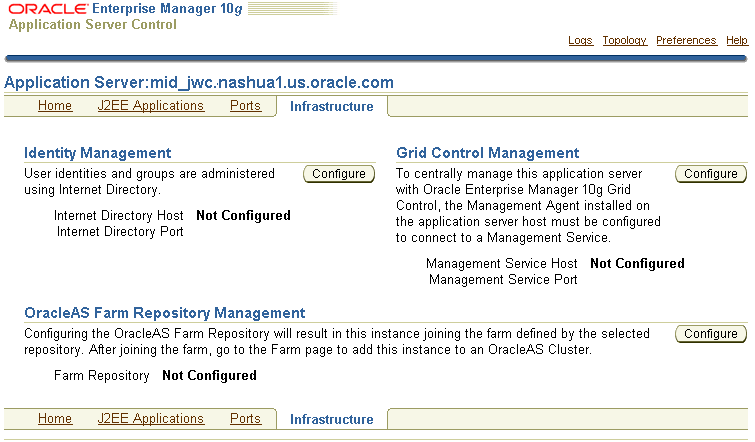
This section contains the following procedures for configuring a middle-tier instance to use Infrastructure services:
To configure a Release 2 (10.1.2.0.2) J2EE and Web Cache instance to use Oracle Identity Management, refer to Section 7.4.1.
To configure a Release 2 (10.1.2.0.2) J2EE and Web Cache instance to use OracleAS Metadata Repository, refer to Section 7.4.2. Note that the instance must already use Oracle Identity Management.
To configure a Release 2 (10.1.2.0.2) J2EE and Web Cache instance to use an Existing Database (an OracleAS Metadata Repository that is not registered with Oracle Internet Directory used by this instance), refer to Section 7.4.3. Note that the instance may or may not use Oracle Identity Management.
To configure a Release 3 (10.1.3) middle-tier instance to use Identity Management, see Section 7.4.4.
This section describes how to configure a J2EE and Web Cache, Release 2 (10.1.2.0.2), instance to use Oracle Identity Management, 10g (10.1.4.0.1), as shown in Figure 7-3.
Figure 7-3 J2EE and Web Cache Using Identity Management
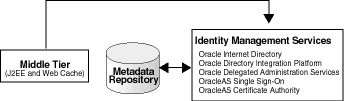
Before you start, make sure that:
The Oracle Identity Management instance is started (status is Up).
You know the Oracle Internet Directory host and port numbers.
You know the password for cn=orcladmin, or another user who is a member of the iASAdmins group.
Then, take the following steps:
Using the Application Server Control Console, navigate to the Application Server Home page for the J2EE and Web Cache instance.
Click Infrastructure.
On the Infrastructure page, in the Identity Management section, click Configure.
On the Internet Directory page:
Host: Enter the fully-qualified name of the Oracle Internet Directory host.
Port: If you do not check Use only SSL connections with Internet Directory, enter the non-SSL Oracle Internet Directory port number. Otherwise, enter the SSL Oracle Internet Directory port number.
Use only SSL connections with Internet Directory: By default, some middle-tier components connect to Oracle Internet Directory using non-SSL connections. If you want components to connect only to Oracle Internet Directory using SSL, check this box and make sure you entered the SSL Oracle Internet Directory port number in the Port field.
|
Note: If you enter an SSL port number and inadvertently do not select Use only SSL connections with Internet Directory, the SSL port number takes precedence and connections to the Oracle Internet Directory are limited to secure connections only.If this is not the behavior you intended, you can return to the Identity Management Wizard, enter a non-SSL port in the Port field, and make sure that Use only SSL connections with Internet Directory is cleared. |
Click Next.
On the Login page:
User Name: Enter cn=orcladmin, or the distinguished name of a user in the iASAdmins group.
Password: Enter the password for the user.
Click Next.
On the Validation page, you receive informational messages regarding the validation of this operation and a warning that all of the components in the instance will be stopped. If you receive any error message, follow the instructions for investigating them. Otherwise, if the operation is valid, click Finish.
When the operation is finished, you must restart the components in the J2EE and Web Cache instance.
Click Home to navigate to the Home page for the middle-tier instance.
Click Start All.
Your J2EE and Web Cache instance is now configured to use Oracle Identity Management services.
This section describes how to configure a J2EE and Web Cache, Release 2 (10.1.2.0.2), instance to use OracleAS Metadata Repository, 10g (10.1.4.0.1). This procedure requires that the J2EE and Web Cache instance is already using Oracle Identity Management, and OracleAS Metadata Repository is registered with that Oracle Identity Management, as shown in Figure 7-4.
Figure 7-4 J2EE and Web Cache (with Identity Management) Using OracleAS Metadata Repository
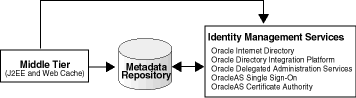
Before you start, make sure that:
OracleAS Metadata Repository is started (status is Up).
The Oracle Identity Management instance is started (status is Up).
You know the password for cn=orcladmin, or another user who is a member of the iASAdmins group.
Then, take the following steps:
Using the Application Server Control Console, navigate to the Application Server Home page for the J2EE and Web Cache instance.
Click Infrastructure.
On the Infrastructure page, in the OracleAS Farm Repository Management section, click Configure.
On the Source page, choose OracleAS Metadata Repository. Then, click Next.
On the Internet Directory page:
User Name: Enter cn=orcladmin or the distinguished name of a user in the iASAdmins group.
Password: Enter the password for the user.
Notice that Use Only SSL connections with Internet Directory is grayed out. This is because you cannot specify this option in this operation.
Click Next.
On the Location page, select the OracleAS Metadata Repository you want to use from the Repository list. The Default Schema is always DCM. Then, click Next.
On the Validation page, you receive informational messages regarding the validation of this operation and a warning that components will be stopped. If you receive any error message, follow the instructions for investigating them. Otherwise, if the repository you specified is valid, click Finish.
When the operation is finished, you must restart the components in the J2EE and Web Cache instance.
Click Home to navigate to the Home page for the middle-tier instance.
Click Start All.
Your J2EE and Web Cache instance is now in the OracleAS Metadata Repository's farm and can join an instance of OracleAS Clusters in that farm.
|
See Also: Oracle Application Server High Availability Guide for information on creating and using OracleAS Clusters |
This section describes how to configure a J2EE and Web Cache, Release 2 (10.1.2.0.2), instance to use an existing Database (a 10g (10.1.4.0.1) OracleAS Metadata Repository that is not registered with Oracle Internet Directory) as the metadata repository. The J2EE and Web Cache instance may use Oracle Identity Management, as shown in Figure 7-5, or it may not, as shown in Figure 7-6.
Figure 7-5 J2EE and Web Cache (with Identity Management) Using an Existing Database
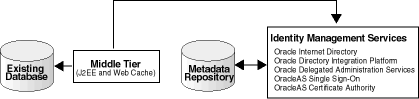
Figure 7-6 shows the J2EE and Web Cache instance using an existing database as a metadata repository, but not using Oracle Identity Management.
Figure 7-6 J2EE and Web Cache (Without Identity Management) Using an Existing Database

Before you start, make sure that:
The Existing Database is started (status is Up).
You know the Net listener port and the service name for the Existing Database. These are listed in the entry for the Existing Database in the following file:
On UNIX systems:
EXISTING_DB_ORACLE_HOME/network/admin/tnsnames.ora
On Windows systems:
EXISTING_DB_ORACLE_HOME\network\admin\tnsnames.ora
You know the password for the DCM schema in the database.
If you have just installed the Existing Database and have not used the DCM schema yet, note that the password is generated randomly during installation. To change the random password to a known value, use the ALTER USER command in SQL*Plus, as shown in the following example (be sure to set the ORACLE_HOME and ORACLE_SID environment variables first):
sqlplus "SYS/sys_password as SYSDBA" SQL> ALTER USER dcm IDENTIFIED BY new_password;
Then, take the following steps:
Using the Application Server Control Console, navigate to the Application Server Home page for the J2EE and Web Cache instance.
Click Infrastructure.
On the Infrastructure page, in the OracleAS Farm Repository Management section, click Configure.
On the Source page, choose Existing Database. (Note: If the OracleAS Metadata Repository option is grayed out, it is because the J2EE and Web Cache instance is not using Oracle Identity Management). Then, click Next.
On the Login page, fill in the following fields:
User Name: DCM.
Password: Enter the DCM schema password.
Hostname and Port: Enter the hostname and Net listener port for the Existing Database. For example: myhost:1521.
Service Name: Enter the service name for the Existing Database. For example, orcl.myco.com.
Click Next.
On the Validation page, you receive informational messages regarding the validation of this operation. If you receive any error message, follow the instructions for investigating them. Otherwise, if the operation is valid, click Finish.
When the operation is finished, you must restart the components in the J2EE and Web Cache instance.
Click Home to navigate to the Home page for the instance.
Click Start All.
Your J2EE and Web Cache instance is now in the Existing Database's farm and can join an instance of OracleAS Clusters in that farm.
This section describes how to configure a 10.1.3 middle-tier instance to use Oracle Identity Management, 10g (10.1.4.0.1), as shown in Figure 7-3.
Figure 7-7 10.1.3 Middle Tier Using 10.1.4 Identity Management
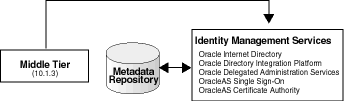
Before you start, make sure that:
The Oracle Identity Management instance is started (status is Up).
You know the Oracle Internet Directory host and port numbers.
You know the password for cn=orcladmin, or another user who is a member of the iASAdmins group.
Task 1: Enable SSO Authentication (Optional)
If you want to enable SSO authentication for deployed applications, you must take the following steps before you use the Identity Management wizard described in "Task 2: Configure the Middle-Tier Instance for Identity Management":
On the Identity Management host, set the environment variables ORACLE_HOME and ORACLE_SID.
On the Identity Management host, run the ssoreg script, using the -remote_midtier option. The file is located at:
(UNIX) ORACLE_HOME/sso/bin/ssoreg.sh (Windows)ORACLE_HOME\sso\bin\ssoreg.bat
For example, on LINUX:
$ORACLE_HOME/sso/bin/ssoreg.sh -oracle_home_path $ORACLE_HOME -config_mod_osso TRUE -site_name myhost.com:7778 -remote_midtier -config_file $ORACLE_HOME/Apache/Apache/conf/osso/myosso.conf -mod_osso_url http://myhost.com:7778
The resulting configuration file (mysso.conf in the example) is an obfuscated osso configuration file.
Copy the obfuscated osso configuration file to the middle-tier instance.
On the middle-tier host, run the following script to complete the registration:
(UNIX) ORACLE_HOME/Apache/Apache/bin/osso1013 config_file (Windows) perl ORACLE_HOME\Apache\Apache\bin\osso1013 config_file
Task 2: Configure the Middle-Tier Instance for Identity Management
To configure the middle-tier instance to use Identity Management, take the following steps:
Using the Application Server Control Console, navigate to the OC4J Home page for the middle-tier instance.
Click Administration.
In the Task Name column of the table, expand Security if it is not already expanded. Then, in the Identity Management row, click the Go to Task icon.
On the Identity Management page, click Configure.
On the Configure Identity Management: Connect Information page:
Oracle Internet Directory Host: Enter the fully-qualified name of the Oracle Internet Directory host.
Oracle Internet Directory User: Enter the distinguished name of a user, such as cn=orcladmin, in the iASAdmins group.
Password: Enter the password for the user.
This password will be used as the default password for the oc4jadmin user created in Oracle Internet Directory.
Use only SSL connections to the Internet Directory: Select this option if you want middle-tier components to connect to Oracle Internet Directory using only SSL.
Then, in the Oracle Internet Directory SSL Port field, enter the Oracle Internet Directory SSL port number.
Use non-SSL connections to the Internet Directory: Select this option if you want middle-tier components to connect to Oracle Internet Directory using non-SSL connections.
Then, in the Oracle Internet Directory Port field, enter the Oracle Internet Directory non-SSL port number.
Click Next.
On the Configure Identity Management: Application Server Control page, you can specify if you want to configure the Application Server Control to use Identity Management as its security provider, for authentication and authorization of administrative users. If you do, select Use Oracle Identity Management Security Provider.
Note the following:
Any Application Server Control administrator users created for the current security provider will not be able to access the Application Server Control after you make this change. Only users and groups defined in Oracle Internet Directory will be able to access the Application Server Control Console.
You can change the Application Server Control security provider later by clicking Setup, then Security Provider.
On the Configure Identity Management: Deployed Applications page, you can specify security options for applications deployed in this OC4J instance. For each application:
Use OID Security Provider: Select this option to configure applications to use Identity Management as its security provider for authentication and authorization.
Note that you cannot change the security provider for the default application.
Enable SSO Authentication: If you selected Use OID Security Provider, you can select this option to use Single Sign-On authentication. Note, however, that you must have first registered your instance of Oracle Application Server with the OracleAS Single Sign-On server. See "Task 1: Enable SSO Authentication (Optional)" for more information.
Click Configure.
When the operation is finished, you need to restart the OC4J instance. Do not click Restart on the Confirmation page. Instead, navigate to the Cluster Topology page, select the OC4J instance, and click Restart.
Your middle tier is now configured to use Oracle Identity Management services.
Beginning with Release 2 (10.1.2.0.2), you can enable and disable anonymous binds (anonymous authentication) in Oracle Internet Directory. By default, anonymous binds are enabled.
Although disabling anonymous binds is useful in many runtime environments, most configuration changes, such as the following, require that anonymous binds are enabled:
Installing new components with Oracle Universal Installer
Configuring components with Application Server Control Console
Changing the host name, domain name, or IP address of a host on which you have installed Oracle Application Server
Cloning
To disable anonymous binds, take the following steps:
Shut down all middle tiers that are connected to the OracleAS Infrastructure, as described in Section 3.2.4.
Shut down OracleAS Infrastructure, in all Infrastructure Oracle homes:
(UNIX) ORACLE_HOME/opmn/bin/opmnctl stopall (Windows) ORACLE_HOME\opmn\bin\opmnctl stopall
Start Oracle Internet Directory, because it must be started while you perform the procedure:
(UNIX) ORACLE_HOME/bin/oidmon connect=db_connect_string start (Windows) ORACLE_HOME\bin\oidmon connect=db_connect_string start
Edit the ias.properties file for each middle tier connected to the OracleAS Infrastructure and for the Infrastructure Oracle home that contains OracleAS Single Sign-On and Oracle Delegated Administration Services. The ias.properties file is located in the following directory:
(UNIX) ORACLE_HOME/config (Windows) ORACLE_HOME\config
In the ias.properties file, add the OIDAnonymousDisabled property to the file and set it to true:
OIDAnonymousDisabled=true
Edit the dads.conf file for each middle tier connected to the OracleAS Infrastructure and for the Infrastructure Oracle home that contains OracleAS Single Sign-On and Oracle Delegated Administration Services. The dads.conf file is located in the following directory:
(UNIX) ORACLE_HOME/Apache/modplsql/conf (Windows) ORACLE_HOME\Apache\modplsql\conf
By default, the PlsqlDatabaseConnectString parameter contains a value that uses the LDAP name resolution format, for example:
PlsqlDatabaseConnectString cn=orcl, cn=oraclecontext NetServiceNameFormat
Comment out this line. (Do not delete it because you will need to revert to it if you want to enable anonymous binds in the future.)
Add the following line, which changes the value of the PlsqlDatabaseConnectString parameter to use the host:port:service format instead of LDAP name resolution:
PlsqlDatabaseConnectString db_host:db_hostdb_listener_port:db_service_name
In the example, db_host is the name of the host on which the OracleAS Metadata Repository for OracleAS Single Sign-On is installed, db_listener_port is the listener port for that OracleAS Metadata Repository, and db_service_name is the service name for the OracleAS Metadata Repository.
Use the ldapmodify command to disable anonymous binds. Use the command on the Oracle home that contains Oracle Internet Directory.
Take the following steps:
Create a text file with the following lines:
dn: changetype: modify replace: orclanonymousbindsflag orclanonymousbindsflag: 0
Use the ldapmodify command, calling the text file created in the previous step as input. In the following example, the text file is named anon_off.ldif:
(Unix) ORACLE_HOME/bin/ldapmodify -h host -p port -D cn=orcladmin -w password -v -f anon_off.ldif (Windows) ORACLE_HOME\bin\ldapmodify -h host -p port -D cn=orcladmin -w password -v -f anon_off.ldif
Stop Oracle Internet Directory:
(UNIX) ORACLE_HOME/bin/oidmon connect=db_connect_string stop (Windows) ORACLE_HOME\bin\oidmon connect=db_connect_string stop
Start OracleAS Infrastructure, including Oracle Internet Directory, in the Oracle Internet Directory Oracle home, then in any other OracleAS Infrastructure Oracle homes:
(UNIX) ORACLE_HOME/opmn/bin/opmnctl startall (Windows) ORACLE_HOME\opmn\bin\opmnctl startall
Start all middle tiers that are connected to the Infrastructure, as described in Section 3.2.3, "Starting a Middle-Tier Instance".
If you have disabled anonymous binds, you must take the following steps to enable anonymous binds before you can make configuration changes to Oracle Application Server middle tiers or OracleAS Infrastructure:
Shut down all middle tiers that are connected to the OracleAS Infrastructure, as described in Section 3.2.4, "Stopping a Middle-Tier Instance".
Shut down OracleAS Infrastructure, in all Infrastructure Oracle homes:
(UNIX) ORACLE_HOME/opmn/bin/opmnctl stopall (Windows) ORACLE_HOME\opmn\bin\opmnctl stopall
Start Oracle Internet Directory, because it must be started while you perform the procedure:
(UNIX) ORACLE_HOME/bin/oidmon connect=db_connect_string start (Windows) ORACLE_HOME\bin\oidmon connect=db_connect_string start
Edit the ias.properties file for each middle tier connected to the OracleAS Infrastructure and for the Infrastructure Oracle home that contains OracleAS Single Sign-On and Oracle Delegated Administration Services. The ias.properties file is located in the following directory:
(UNIX) ORACLE_HOME/config (Windows) ORACLE_HOME\config
In the ias.properties file, set the OIDAnonymousDisabled property to false:
OIDAnonymousDisabled=false
If the property does not exist in the file, or if it is set to false, anonymous binds are enabled.
Edit the dads.conf file for each middle tier connected to the OracleAS Infrastructure and for the Infrastructure Oracle home that contains OracleAS Single Sign-On and Oracle Delegated Administration Services. The dads.conf file is located in the following directory:
(UNIX) ORACLE_HOME/Apache/modplsql/conf (Windows) ORACLE_HOME\Apache\modplsql\conf
If you previously commented out the line that contains the PlsqlDatabaseConnectString parameter with a value that uses the LDAP name resolution format, uncomment out that line. If you deleted the line, add a line using the following format:
PlsqlDatabaseConnectString cn=orcl, cn=oraclecontext NetServiceNameFormat
If you previously added a line similar to the following, which contains the PlsqlDatabaseConnectString parameter with a value that use host:port:service format, comment out the line:
PlsqlDatabaseConnectString db_host:db_hostdb_listener_port:db_service_name
Use the ldapmodify command to enable anonymous binds. Use the command on the Oracle home that contains Oracle Internet Directory.
Take the following steps:
Create a text file with the following lines:
dn: changetype: modify replace: orclanonymousbindsflag orclanonymousbindsflag: 1
Use the ldapmodify command, calling the text file created in the previous step as input. In the following example, the text file is named anon_on.ldif:
(Unix) ORACLE_HOME/bin/ldapmodify -h host -p port -D cn=orcladmin -w password -v -f anon_on.ldif (Windows) ORACLE_HOME\bin\ldapmodify -h host -p port -D cn=orcladmin -w password -v -f anon_on.ldif
Stop Oracle Internet Directory:
(UNIX) ORACLE_HOME/bin/oidmon connect=db_connect_string stop (Windows) ORACLE_HOME\bin\oidmon connect=db_connect_string stop
Start OracleAS Infrastructure, including Oracle Internet Directory, in the Oracle Internet Directory Oracle home, then in any other OracleAS Infrastructure Oracle homes:
(UNIX) ORACLE_HOME/opmn/bin/opmnctl startall (Windows) ORACLE_HOME\opmn\bin\opmnctl startall
Start all middle tiers that are connected to the Infrastructure, as described in Section 3.2.3, "Starting a Middle-Tier Instance".