


|

|
|
|
|
Message-based Digital Signature
Message-based digital signatures enhance BEA Tuxedo security by allowing a message originator to prove its identity, and by binding that proof to a specific message buffer. Mutually authenticated and tamper-proof communication is considered essential for most applications that transport data over the Internet, either between companies or between a company and the general public. It also is critical for applications deployed over insecure internal networks.
The scope of protection for a message-based digital signature is end-to-end: a message buffer is protected from the time it leaves the originating process until the time it is received at the destination process. It is protected at all intermediate transit points, including temporary message queues, disk-based queues, and system processes, and during transmission over inter-server network links.
The following figure shows how end-to-end message-based digital signature works.
BEA Tuxedo PKCS-7 End-to-End Digital Signing
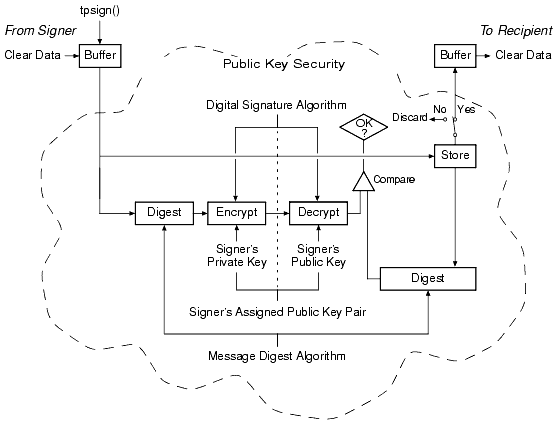
Message-based digital signature involves generating a digital signature by computing a message digest on the message, and then encrypting the message digest with the sender's private key. The recipient verifies the signature by decrypting the encrypted message digest with the signer's public key, and then comparing the recovered message digest to an independently computed message digest. The signer's public key either is contained in a digital certificate included in the signer information, or is referenced by an issuer-distinguished name and issuer-specific serial number that uniquely identify the certificate for the public key.
Digital Certificates
Digital certificates are electronic files used to uniquely identify individuals and resources over networks such as the Internet. A digital certificate securely binds the identity of an individual or resource, as verified by a trusted third party known as a Certification Authority, to a particular public key. Because no two public keys are ever identical, a public key can be used to identify its owner.
Digital certificates allow verification of the claim that a specific public key does in fact belong to a specific subscriber. A recipient of a certificate can use the public key listed in the certificate to verify that the digital signature was created with the corresponding private key. If such verification is successful, this chain of reasoning provides assurance that the corresponding private key is held by the subscriber named in the certificate, and that the digital signature was created by that particular subscriber.
A certificate typically includes a variety of information, such as:
The most widely accepted format for certificates is defined by the ITU-T X.509 international standard. Thus, certificates can be read or written by any application complying with X.509. BEA Tuxedo public key security recognizes certificates that comply with X.509 Version 3, or X.509v3.
Certification Authority
Certificates are issued by a Certification Authority, or CA. Any trusted third-party organization or company that is willing to vouch for the identities of those to whom it issues certificates and public keys can be a CA. When it creates a certificate, the CA signs the certificate with its private key, to obtain a digital signature. The certification authority then returns the certificate with the signature to the subscriber; these two parts-the certificate and the CA's signature-together form a valid certificate.
The subscriber and others can verify the issuing CA's digital signature by using the CA's public key. The CA makes its public key readily available by publicizing that key or by providing a certificate from a higher-level CA attesting to the validity of the lower-level CA's public key. The second solution gives rise to hierarchies of CAs.
The recipient of an encrypted message can develop trust in the CA's private key recursively, if the recipient has a certificate containing the CA's public key signed by a superior CA whom the recipient already trusts. In this sense, a certificate is a stepping stone in digital trust. Ultimately, it is necessary to trust only the public keys of a small number of top-level CAs. Through a chain of certificates, trust in a large number of users' signatures can be established.
Thus, digital signatures establish the identities of communicating entities, but a signature can be trusted only to the extent that the public key for verifying the signature can be trusted.
Note that BEA Systems has no plans to become a CA. By offering a public key plug-in interface, BEA Systems extends the opportunity to all BEA Tuxedo customers to select a CA of their choice.
Certificate Repositories
To make a public key and its identification with a specific subscriber readily available for use in verification, the digital certificate may be published in a repository or made available by other means. Repositories are databases of certificates and other information available for retrieval and use in verifying digital signatures. Retrieval can be accomplished automatically by having the verification program directly request certificates from the repository as needed.
Public-Key Infrastructure
The Public-Key Infrastructure (PKI) consists of protocols, services, and standards supporting applications of public key cryptography. Because the technology is still relatively new, the term PKI is somewhat loosely defined: sometimes "PKI" simply refers to a trust hierarchy based on public key certificates; in other contexts, it embraces digital signature and encryption services provided to end-user applications as well.
There is no single standard public key infrastructure today, though efforts are underway to define one. It is not yet clear whether a standard will be established or multiple independent PKIs will evolve with varying degrees of interoperability. In this sense, the state of PKI technology today can be viewed as similar to local and wide-area network technology in the 1980s, before there was widespread connectivity via the Internet.
The following services are likely to be found in a PKI:
The following diagram shows the PKI process flow.
PKI Process Flow
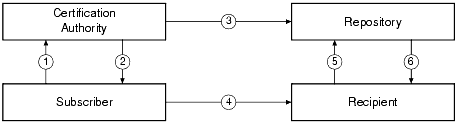
Note that BEA Systems has no plans to become a PKI vendor. By offering a public key plug-in interface, BEA Systems extends the opportunity to all BEA Tuxedo customers to use a PKI security solution with the PKI software from their vendor of choice.
See Also

|

|

|
|
|
|
Copyright © 2000 BEA Systems, Inc. All rights reserved.
|