Topics:
- About the Patch Tool
- Images for Oracle WebCenter for OCI
- Integrate WebCenter with OCI Monitoring and Console Dashboard
- Set Up DNS and SSL Certificate for WebCenter
- Scale Out and Scale In WebCenter Nodes
- Backup and Restore Scripts for WebCenter
- About Quick Start for WebCenter on Marketplace
- Generate an SSH Key Pair for WebCenter (This is not required if Auto Generate SSH Key Pair is selected)
- Configure Dynamic Groups and Policies for Non-Admin Delegated Users
- Package Logs for Troubleshooting
- Integration of WebCenter Content with Microsoft 365 Office for the Web
- Create VCN and Subnets
- Integrate WebCenter on Marketplace with Stack Monitoring
- Cross Region Disaster Recovery Provisioning Guide for WebCenter
- Fix Expired Schema Password Guide for WebCenter Content
- Existing Stack License Change Provisioning Guide for Webcenter Content Stack
- Digital Media Transcoder for Oracle WebCenter Content
- Existing Stack Configure for all external https traffic via 443 load balancer port
- Configure TLSv1.3 ciphers for load balancer listeners for WebCenter
- ClamAV AntiVirus Service for WebCenter Content
- How to update an existing WebCenter Marketplace Content stack to use a new base db
- Automation to unmount and mount FSS with in transit TLS encryption
- How to update an existing WebCenter Marketplace Content stack using basedb to switch over to ATP
- SSH Keys Rotation
- WebCenter WebLogic Server Lifecycle Operations
- How to update an existing WebCenter Marketplace Content stack using basedb to switch over to EXAData database
- Appendix
About the Patch Tool
Oracle WebCenter on Marketplace in Oracle Cloud Infrastructure (OCI) provides a patching utility tool to download and apply patches for the WebCenter instances.
You can apply a patch on the WebCenter compute instances using this patch tool.
The patch tool should be executed only on WebCenter Weblogic Admin server instance which has a hostname ending with '-wls-1'.
The patch tool allows patch application in both online and offline modes.
- Users with internet connectivity from WebCenter nodes can use the online mode.
- Users using WebCenter private service with no internet connectivity from WebCenter nodes can use the offline mode for patching.
- Offline mode users who do not have service gateway in their VCN will need to configure all routes to OCI services via DRG (e.g object storage, yum etc).
Patch Management Using the Patch Tool
Patch Management Using the Patch Tool
Use the patch tool utility in Oracle WebCenter on Marketplace on OCI to list available patches, to apply a patch, or to rollback a patch.
Prerequisite
Prerequisite - Network Access
Patch tool needs network access to download required packages for patching.
Prerequisite - Service Gateway
Service gateway is required to access OCI services. We use a number of OCI services e.g. Object Storage, IDCS etc.
Please check if webcenter VCN already has an existing Service Gateway.
If there is no Service Gateway then create service gateway.
Edit webcenter instance subnet route table and add Service Gateway route.
- Target Type: Service Gateway
- Destination Service: All
Services In Oracle Services Network - Target Service Gateway Compartment: Compartment where you created the Service Gateway.
- Target Service Gateway: Select Service gateway from dropdown list
- Description: Route rule for patching
Prerequisite - NAT Gateway
Skip this section if you plan to apply offline patch.
Private services deployed in ashburn datacenter can skip this section.
NAT Gateway is required for all private services deployed in non ashburn region during patching. NAT Gateway can be removed after patching is completed.
Please create NAT Gateway if there is no exiting NAT Gateway in VCN.
Add following routes in the route table for webcenter instance subnet
Add route for CIDR: 134.70.24.0/21
- Target Type: NAT Gateway
- Destination CIDR Block: 134.70.24.0/21
- Target NAT Gateway Compartment: Compartment where you created the NAT gateway.
- Target NAT Gateway: Select NAT gateway from dropdown list
- Description: Route rule for patching
Add route for CIDR: 134.70.32.0/22
- Target Type: NAT Gateway
- Destination CIDR Block: 134.70.32.0/22
- Target NAT Gateway Compartment: Compartment where you created the NAT gateway.
- Target NAT Gateway: Select NAT gateway from dropdown list
- Description: Route rule for patching
Prerequisite - Offline Patch
- Patch application needs access to OCI object storage and other OCI services. If you do not have service gateway configured in your VCN then please add all required routes via DRG.
- Download the patch tool package from here: WebCenter Patch
-
Copy the downloaded package to all WebCenter compute instances.
For each webcenter compute instance compute_wls-1_private_ip, execute the following command to copy the patch package to the compute instance.
scp -i path_to_private_key <downloaded-package.zip> opc@compute_wls-1_private_ip:/tmp -
Copy ssh key to compute instance ‘wls-1’ and change ownership to oracle
scp -i path_to_private_key path_to_private_key opc@compute_wls-1_private_ip:/tmp/id_rsa && ssh -i path_to_private_key opc@compute_wls-1_private_ip 'sudo chown oracle:oracle /tmp/id_rsa' -
Execute the following steps on each webcenter compute instance.
- Connect to WebCenter Compute Instance.
-
Change to 'Oracle' user.
[opc@**-wls-1 ~]$ sudo su - oracle -
Change to /tmp directory where the patch zip file was copied.
[oracle@**-wls-1 ~]$ cd /tmp -
Extract the patch zip file.
[oracle@**-wls-1 tmp]$ unzip <patch-filename>.zip
Prerequisite - Online Patch
-
Execute the following steps on each webcenter compute instance.
- Connect to WebCenter Compute Instance.
-
Change to 'Oracle' user.
[opc@**-wls-1 ~]$ sudo su - oracle -
Go to the patch tool path.
[oracle@**-wls-1 ~]$ cd /u01/scripts/patch/ - Download the patch tool wrapper script from here: WebCenter Patch Tool Script and replace the script 'patch_tool.sh'.
Connecting to WebCenter Compute Instance
-
Connect to bastion instance as opc user. Users using a private service can skip this as we do not provision bastion for a private service.
ssh -i path_to_private_key opc@bastion_public_ip -
Copy ssh key to compute instance ‘wls-1’
scp -i path_to_private_key path_to_private_key opc@compute_wls-1_private_ip:/tmp/id_rsa && ssh -i path_to_private_key opc@compute_wls-1_private_ip 'sudo chown oracle:oracle /tmp/id_rsa' -
Connect to Webcenter admin or managed compute instance.
-
Connect to the weblogic admin server compute instance which has a name ending with
'wls-1'.ssh -i path_to_private_key opc@compute_wls-1_private_ip -
Connect to the weblogic managed server compute instance which has a name ending with
'wls-*'. For example:'wls-2','wls-3', etc.ssh -i path_to_private_key opc@compute_wls-2_private_ip
-
List Available Patches
- Connect to WebCenter Compute Admin Instance.
-
Change to 'Oracle' user.
[opc@**-wls-1 ~]$ sudo su - oracle -
Go to the patch tool path.
[oracle@**-wls-1 ~]$ cd /u01/scripts/patch/ -
List available patches.
sh patch_tool.sh --list_available_patches -
List available patches in offline mode for private service.
Where –patch-dir is patch to extracted patch from prerequisite. For example:
/tmp/25.6.1.sh patch_tool.sh --list_available_patches --offline --patch_dir /tmp/25.6.1
Apply Patch
Patch
- Connect to WebCenter Compute Admin Instance.
-
Change to 'Oracle' user.
[opc@**-wls-1 ~]$ sudo su - oracle -
Go to the patch tool path.
[oracle@**-wls-1 ~]$ cd /u01/scripts/patch/ - Select the patch to apply from available patches.
-
Apply patch.
sh patch_tool.sh --apply_patch --patch_version <patch-version> --ssh_key_path <provide ssh private key for opc> --health_checkExample:
sh patch_tool.sh --apply_patch --patch_version 25.6.1 --ssh_key_path /tmp/id_rsa --health_checkUse additional input option
--silentto avoid user confirmation prompt. -
Apply patch in offline mode for private service.
Where –patch-dir is patch to extracted patch from prerequisite. For example:
/tmp/25.6.1sh patch_tool.sh --apply_patch --patch_version <patch-version> --ssh_key_path <provide ssh private key for opc> --offline --patch_dir <extracte-patch-dir-path> --health_checkExample:
sh patch_tool.sh --apply_patch --patch_version 25.6.1 --ssh_key_path /tmp/id_rsa --offline --patch_dir /tmp/25.6.1 --health_checkUse additional input option
--silentto avoid user confirmation prompt.
Apply Only Pre Patch
To apply pre patch only.
- Connect to WebCenter Compute Admin Instance.
-
Change to 'Oracle' user.
[opc@**-wls-1 ~]$ sudo su - oracle -
Go to the patch tool path.
[oracle@**-wls-1 ~]$ cd /u01/scripts/patch/ - Select the patch to apply from available patches.
-
Apply pre patch.
sh patch_tool.sh --apply_pre_patch --patch_version <patch-version> --ssh_key_path <provide ssh private key for opc>Example:
sh patch_tool.sh --apply_pre_patch --patch_version 25.6.1 --ssh_key_path /tmp/id_rsa
Apply Only Post Patch
To apply post patch only. Do not use post patch only operation before applying patch. Post patch will have dependencies on available patches.
- Connect to WebCenter Compute Admin Instance.
-
Change to 'Oracle' user.
[opc@**-wls-1 ~]$ sudo su - oracle -
Go to the patch tool path.
[oracle@**-wls-1 ~]$ cd /u01/scripts/patch/ - Select the patch to apply from available patches.
-
Apply post patch.
sh patch_tool.sh --apply_post_patch --patch_version <patch-version> --ssh_key_path <provide ssh private key for opc>Example:
sh patch_tool.sh --apply_post_patch --patch_version 25.6.1 --ssh_key_path /tmp/id_rsa
List Available Backups
- Connect to WebCenter Compute Admin Instance.
-
Change to 'Oracle' user.
[opc@**-wls-1 ~]$ sudo su - oracle -
Go to the patch tool path.
[oracle@**-wls-1 ~]$ cd /u01/scripts/patch/ -
List available backups.
sh patch_tool.sh --list_available_backupsSample output:
------------------------- Middleware backups ------------------------- 1/1. <..>-mw-home-backup-<..>.tar.gz ---------------------------------------------------------------------- -
List available backups in offline mode for private service.
Where –patch-dir is patch to extracted patch from prerequisite. For example:
/tmp/25.6.1sh patch_tool.sh --list_available_backups --offline --patch_dir /tmp/25.6.1Sample output:
------------------------- Middleware backups ------------------------- 1/1. <..>-mw-home-backup-<..>.tar.gz ----------------------------------------------------------------------
Rollback Patch
Rollback Middleware
- Connect to WebCenter Compute Admin Instance.
-
Change to 'Oracle' user.
[opc@**-wls-1 ~]$ sudo su - oracle -
Go to the patch tool path.
[oracle@**-wls-1 ~]$ cd /u01/scripts/patch/ - Identify the backup file to rollback from available backups.
-
Rollback patch.
sh patch_tool.sh --rollback_patch --file_name <backupfilename>.tar.gz -
Rollback patch in offline mode for private service.
Where –patch-dir is patch to extracted patch from prerequisite. For example:
/tmp/25.6.1sh patch_tool.sh --rollback_patch --file_name <backupfilename>.tar.gz --offline --patch_dir <extracte-patch-dir-path>
Rollback Domain
Domain rollback is required to be done on every webcenter vm manually.
Please rollback domain changes manually on every vm as follows:
- Connect to webcenter vm.
- Change use to oracle.
- Restore domain from backup on this vm.
[oracle@**-wls-1 ~]$ cd /u01/scripts/lcm/sh [oracle@**-wls-1 ~]$ sh restore_domain.sh -b <bucket_name>Repeat these steps on every webcenter vm.
Images for Oracle WebCenter for OCI
Linux Images for Oracle WebCenter for OCI
Learn about the Linux images for Oracle WebCenter for Oracle Cloud Infrastructure and how to use these images to create instances of Oracle WebCenter products in Oracle Cloud Infrastructure.
- About Oracle WebCenter for OCI Linux Images
- Create Compartment Policies
- Create an Instance from Marketplace
- Installing Oracle WebCenter for OCI Linux Image
About Oracle WebCenter for OCI Linux Images
Oracle WebCenter for OCI Linux images are publicly available in the marketplace from release 25.7.1. These images include binaries of the Oracle WebCenter Products (WebCenter Content - 14.1.2.0), Fusion Middle Infrastructure (14.1.2.0) and the Java Development Toolkit (JDK 21).
Oracle Linux 8.10 images are supported for Oracle WebCenter for OCI images. These Linux images contain:
- Installer jar files of Oracle WebCenter products and Fusion Middleware Infrastructure installations (14.1.2.0) located in
/u01/zips. - JDK 21 installer for Linux x64 located in
/u01/zips.
Oracle WebCenter for OCI Linux images supports Universal Credits (UCM) images.
The following UCM images are available in Marketplace for Oracle WebCenter Content
- Oracle WebCenter Content UCM Image
- Oracle WebCenter Enterprise Capture Standard Edition UCM Image
Create Compartment Policies
If you are not an Oracle Cloud Infrastructure administrator, you must be given management access to Marketplace applications and Resource Manager stacks to be able to create compute instances using Oracle WebCenter Content on OCI images.
The sample policies are shown below:
Allow group MyGroup to use app-catalog-listing in compartment MyCompartment
Allow group MyGroup to manage instance-family in compartment MyCompartment
Allow group MyGroup to manage virtual-network-family in compartment MyNetworkCompartment
See Common Policies in the Oracle Cloud Infrastructure documentation.
Create an Instance from Marketplace
You can create a new instance using Oracle WebCenter Content on OCI images from the Marketplace.
- Sign in to the Oracle Cloud Infrastructure console.
- Click the navigation menu, select Marketplace, and then click All Applications.
- Search and select the following Oracle WebCenter Content on OCI image: Oracle WebCenter Content UCM Image
- From the Version drop-down list, select the image version. Choose 14.1.2.0 release version.
- Review the terms and conditions, and select the Oracle Terms of Use check box.
- Click Launch Instance.
- Select the compartment in which you want to create the instance.
- Under Placement, select the Availability Domain in which you want to create the instance. To specify capacity type and fault domain, click Show advanced options.
- Under Image and Shape, click Change Shape. Select the Instance Type and select the shape. If you’re creating a virtual machine, under Shape series, select a processor group, and then choose a shape. To know the shapes that are supported, see Shapes for the images.
- Configure the network for the instance. To specify advanced network settings, click Show advanced options.
- Under Add SSH keys, generate a key, upload your public key, or paste the keys.
- Under Boot Volume, specify the size and encryption options for the instance’s boot volume.
- Click Show advanced options to configure advanced settings.
- Click Create.
For details, see Creating a Linux instance.
Installing Oracle WebCenter for OCI Linux Image
You can use Oracle WebCenter for OCI Linux image to create Oracle WebCenter product installation in Oracle Cloud Infrastructure compute instances. When using the Oracle WebCenter for OCI Linux images:
- Ensure that you specify an SSH key when you create an instance using the image. You need this SSH key to access the instance and launch the instance.
-
Connect to an instance as the opc user using the SSH command.
ssh –i <private_key_file> opc@<public-ip-address>where,
private_key_fileis the corresponding private key for the public key used during provisioning. - Extend the boot volume.
sudo /usr/libexec/oci-growfs -y lsblk - Switch to oracle user.
sudo su - oracle -
Extract the JDK installer bundle located at
/u01/zipsto Java Home directory and setJAVA_HOMEvariable in system PATH.Example: mkdir /u01/jdk cd /u01/jdk tar -xzvf /u01/zips/jdk-21_linux-x64_bin.tar.gz -
Install FMW Infrastructure and WebCenter product using the installer jars located in
/u01/zipsdirectory.- For WebCenter Content, follow Installing and Configuring Oracle WebCenter Content for installation
Integrate WebCenter with OCI Monitoring and Console Dashboard
For WebCenter on Marketplace, you can monitor the status and performance of WebCenter resources using OCI Monitoring and OCI Console Dashboard. The monitoring resources are configured with default settings during stack provisioning and can be modified to fit their requirements.
List of product types with support for OCI Monitoring and Console Dashboard:
- WebCenter Content
- WebCenter Portal
- WebCenter Sites
WebCenter with OCI Monitoring
WebCenter metrics are collected in OCI Monitoring to display the status and performance of WebCenter and OCI resources.
To view and query metrics:
- Navigate to Observability & Management and then to Metrics Explorer under the Monitoring section.
- Under Query, select the stack’s compartment in the Compartment field.
- Select webcenter_monitoring in the Metric namespace field.
- Select the stack’s resource name prefix in the Resource group field.
- Select a specific metric in the Metric Name drop-down list. Optionally, to view a metric from a specific server, select server under Dimensions and the server name.
- Select Update Chart.
All metrics listed under Metric Names have data from every WebCenter server. The Metrics Explorer also displays metrics from OCI resources such as Compute and Load Balancer in their associated namespaces.
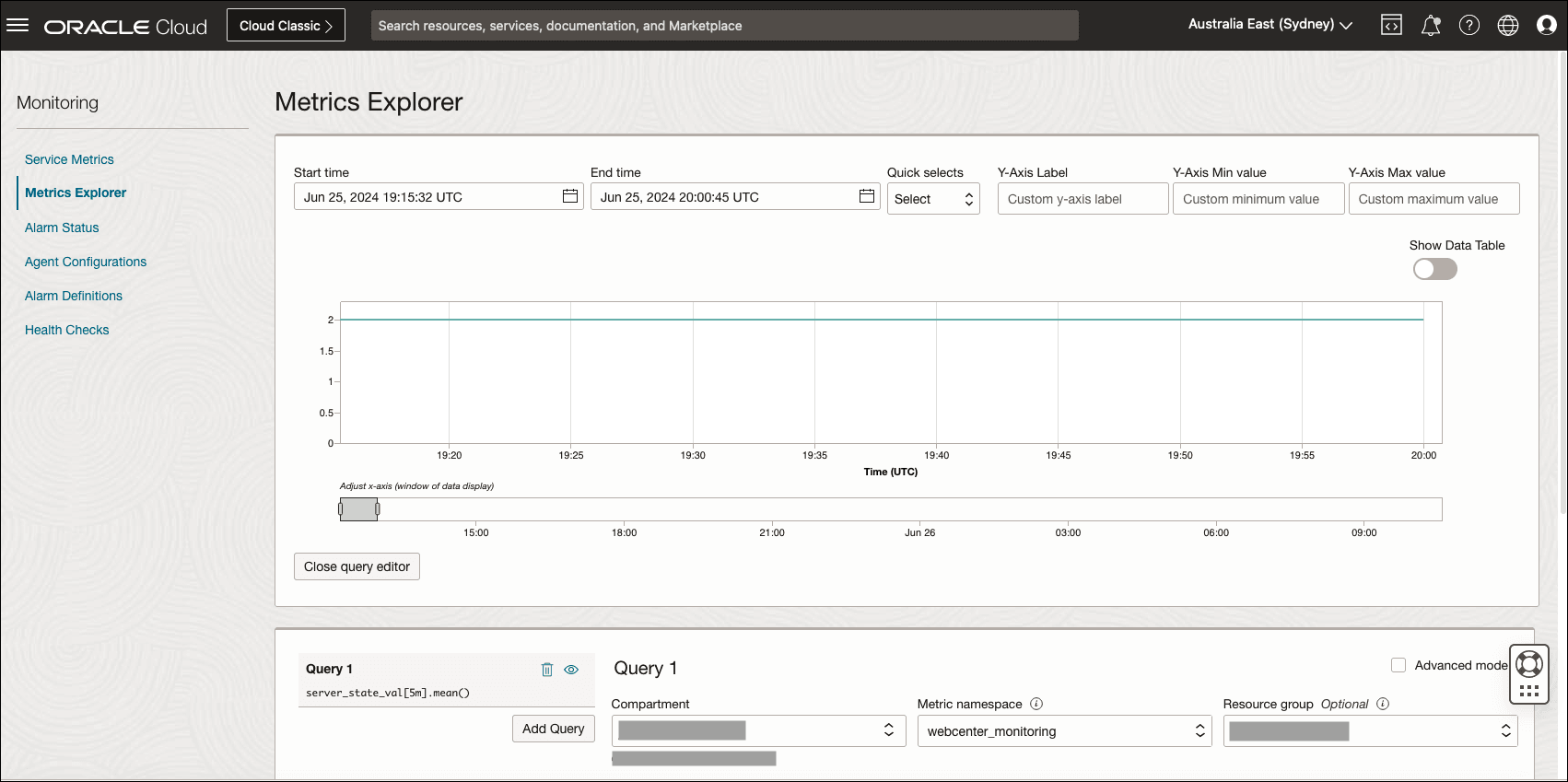
Weblogic metrics are collected and sent to OCI Monitoring in a scheduler in the WebCenter Admin VM instance (wls-1). Every five minutes, metrics are published to OCI Monitoring and the logs for metrics are collected in the log file /u01/data/domains/logs/metrics/publish_metrics.log.
Alarms can be created using the WebCenter metrics to actively monitor health and performance. See the documentation for creating a basic alarm using the webcenter_monitoring namespace: Creating a Basic Alarm.
To turn off monitoring integration with OCI Monitoring, the crontab scheduler can be disabled in the WebCenter Admin VM instance of the admin server (wls-1).
-
Log in to WebCenter Admin VM (wls-1) and verify the scheduler is running.
crontab -lExpected output:
*/5 * * * * python3 /u01/scripts/sh/../python/integrations/publish_metrics.py -
Run the following commands to disable metrics publishing.
sudo su oracle crontab -l | grep -v '.*publish_metrics.py' | crontab - -
Verify that the metrics have stopped collecting after five minutes in OCI Monitoring.
Note: Integration with OCI Monitoring can incur a charge for publishing. See pricing documentation.
WebCenter with OCI Console Dashboard
The WebCenter dashboard is created with OCI Console Dashboard using the WebCenter metrics from the webcenter_monitoring namespace and OCI Compute metrics.
To view the dashboard:
- Navigate to the home page in the OCI console and then the Dashboard tab.
- Under Dashboards, go to Dashboard Groups and select the compartment where the WebCenter resources are provisioned.
- Select the dashboard group for WebCenter webcenter-dashboard-group.
- Select the WebCenter dashboard under the group. The dashboard name is
<resource-name-prefix>-dashboard.
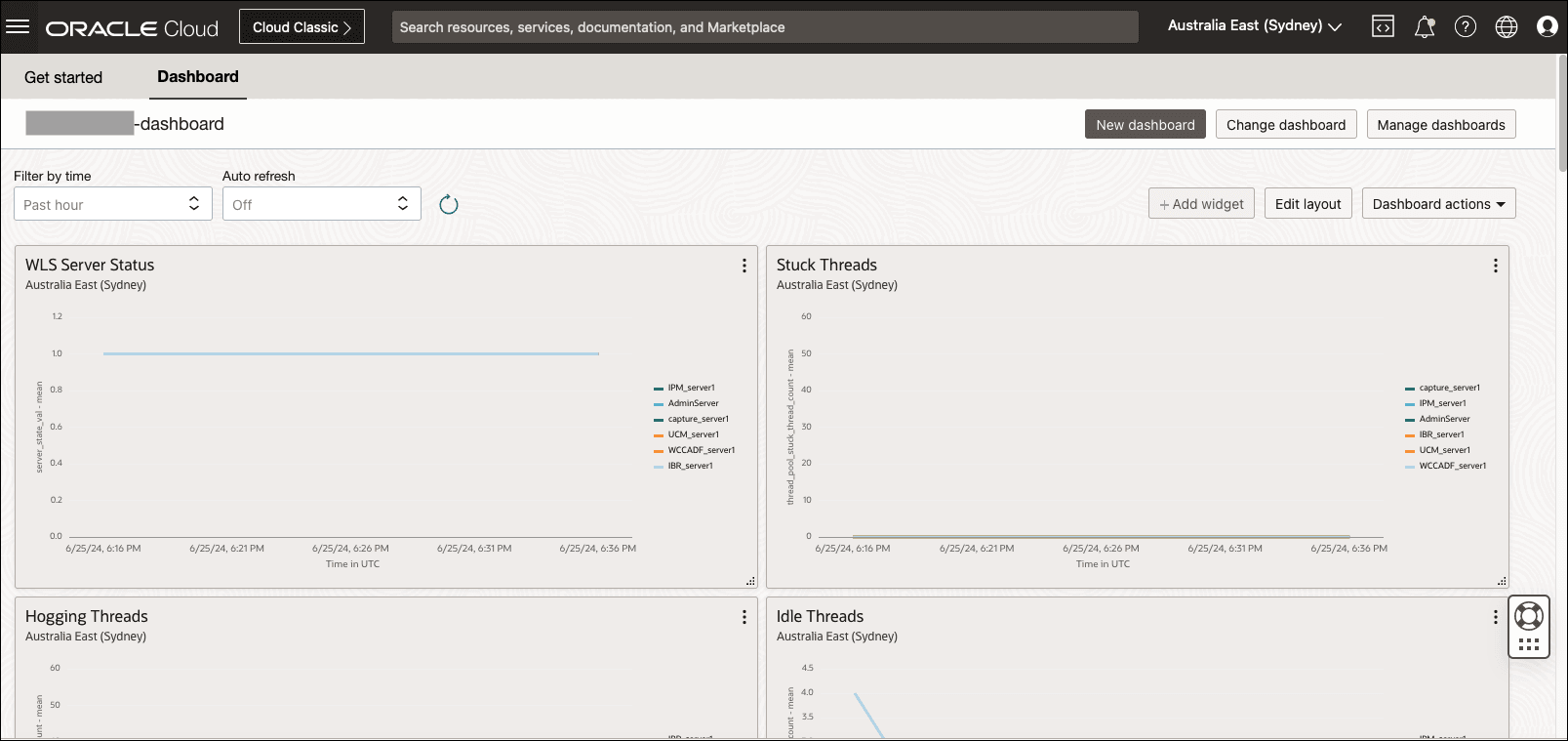
By default, the WebCenter dashboard has monitoring widgets pre-configured for ease of use. These monitoring widgets or charts describe the application status and performance of the Weblogic servers and the Compute instance utilization. The dashboard widgets can be rearranged and redefined to the desired display. To update a widget, click on the ellipses and View and edit settings. The OCI console dashboard has a limit of 20 widgets.
To turn off the dashboard integration with WebCenter and OCI metrics, the console dashboard can be removed in the tenancy:
- Navigate to the WebCenter dashboard.
- Select the Dashboard Action and then delete the dashboard.
Set Up DNS and SSL Certificate for WebCenter
For WebCenter on Marketplace, you can map an external domain host to the public load balancer of the WebCenter stack and configure the SSL certificate.
-
Log in to your OCI console account and create an API key for your user. For this, click the profile picture icon (profile) on the top right, and then click My profile which will take you to your user details page. On the bottom left, click API Keys, and then click Add API Key. Download the private key and then click Add. Copy the OCI configuration.
Note: If you already have an API key for an administrator, you can reuse it without the need to create a new one.
OCI Config should look similar to the following (and values will be different as these are sample values):
[DEFAULT] user=ocid1.user.oc1..aaaaaaaar7e4zuecbqwayvj5ao7h3qqspiaag4hz5doifyvgpts4tgenc2gu fingerprint=fa:bf:59:c4:cb:42:28:50:1e:30:b1:32:ad:23:56:e5 tenancy=ocid1.tenancy.oc1..aaaaaaaahmw6lcpoli7sbqfk2nxdegzlarkmhc3xpymj7yw7m6azsus26hdq region=ca-toronto-1 key_file=<path of private key>Downloaded private key sample:
-----BEGIN PRIVATE KEY----- MIIEvAIBADANBgkqhkiG9w0BAQEFAASCBKYwggSiAgEAAoIBAQCmGs+ziHte3mls ...... ...... RjHw4Kr7eT/frxvghZ7SfIGq1mWxfKfC8ycULyHFAzDPkhV0jIrpXnl6yqruW+da PA6Od5U03CW+o7CaFEDAhQ== -----END PRIVATE KEY-----Note The user needs to have manage dns permission for the compartment where the DNS zone is created. </br> </br> Sample policy: Allow <user-group> to manage dns on compartment <zone-compartment> - SSH to the stack VM for the specific type, for example for WebCenter Content, connect to the Weblogic admin server compute instance for WebCenter Content type which has a name ending with
'wls-1'as Oracle user. Create a temporary directory/u01/certsand copy or download your SSL certificate for the host at this location. You might have a wild card certificate from your registrar or your SSL provider. For example, if you want to use hostwcc1.mycompany.comto map to the load balancer, you may have a wild card certificate for*.mycompany.com. You might get a certificate file, a CA cert, and a private key for the SSL certificate. Copy everything to this location. -
Copy the private key file (which you downloaded earlier while creating the OCI user API key) to this location and name it oci_user_pvt.key. Create the OCI config file using the content from OCI config (OCI config that you copied when creating the OCI user API key) here and update the property key_file to point to this private key file.
key_file=/u01/certs/oci_user_pvt.key -
The certificate file needs to be in a single concatenated pem file with host certificate at the top followed by intermediate certificate. See Uploading Certificate Chains
cat ssl_certificate.crt IntermediateCA.crt >> certbundle.pemThe following example of a concatenated certificate chain file includes leaf and intermediate certificate.
-----BEGIN CERTIFICATE----- Domain Base64-encoded_certificate -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- Intermediate Base64-encoded_certificate -----END CERTIFICATE----- -
Execute
dns_and_cert_manager.shscript as described below to install the load balancer certificate and create the DNS record.# Go to scripts sh folder cd /u01/scripts/lcm/sh # Execute dns and cert manager script passing the required values sh dns_and_cert_manager.sh -c <certificate_file [REQUIRED]> -a <root_ca_cert [OPTIONAL]> -k <certificate_private_key [OPTIONAL]> -p <certificate_private_key_password [OPTIONAL]> -z <zone_name [REQUIRED]> -d <host_name [REQUIRED]> -f <oci_user_config_file [REQUIRED]> -t <DNS|CERT> [OPTIONAL] Arguments: -c : Certificate bundle file -a : Root CA certificate file -k : Certificate private key if available -p : Certificate private key password if applicable -z : DNS zone name -d : Fully qualified domain name -f : DNS oci user config file with API key -t : Type of operation, it can be either DNS or CERT If -t option is passed, it will perform only that particular operation. If this option is not passed, it will perform both the operations i.e. load balancer certificate installation and dns record creation. This option can take either of the two values below: DNS: It will add only the dns record and skip load balancer certificate installation CERT: It will install load balancer certificate and skip creating dns record For example: # To install load balancer certificate as well as create DNS record sh dns_and_cert_manager.sh -c /u01/certs/certbundle.pem -a /u01/certs/root_ca.pem -k /u01/certs/private.key -z mycompany.com -d wcc1.mycompany.com -f /u01/certs/config # To install load balancer certificate only sh dns_and_cert_manager.sh -c /u01/certs/certbundle.pem -a /u01/certs/root_ca.pem -k /u01/certs/private.key -d wcc1.mycompany.com -t CERT # To create DNS record only sh dns_and_cert_manager.sh -z mycompany.com -d wcc1.mycompany.com -f /u01/certs/config -t DNSNote: It will create the DNS record but it might take a couple of hours before the host URL can be used.
-
The script will output the nameserver hosts corresponding to the DNS record. To register the external domain, you will need to add the nameserver hosts to your domain registrar.
Example:
ns1.p201.dns.oraclecloud.net ns2.p201.dns.oraclecloud.net ns3.p201.dns.oraclecloud.net ns4.p201.dns.oraclecloud.net - Log in to your registrar (for example: namecheap, godaddy, etc.) where your external domain is registered. Navigate to your domain management option and add the nameservers that you copied in the previous step as custom DNS for your domain. You may need to go through their documentation or contact your registrar in case you cannot find this configuration.
- If your stack has IDCS configured, then, after registering the nameservers to your external domain, you will need to execute a script to re-configure SAML SSO to map with your service host name. The steps are described in Configuration in WebCenter Content Stack for WebCenter Content and Configuration in WebCenter Portal Stack for WebCenter Portal.
For example, in WebCenter Content, the host URLs will look like:
https://wcc1.mycompany.com:16200/cs
https://wcc1.mycompany.com:16225/wcc
In case you need to map a new hostname to another loadbalancer, for example wcp1.mycompany.com to WebCenter Portal loadbalancer, then you have to log in to the admin server VM of WebCenter Portal and execute the above script again.
| Note |
|---|
| If you have configured the service host forWebCenter Content Marketplace installation, you need to run the following script to update the service host in the product configuration. This is a required step. Execute the following script from Admin compute VM or VM-1 (*-wls-1). |
ssh -o ProxyCommand="ssh -W %h:%p -i <key> opc@<bastion-ip>" -i <key> opc@<vm-ip>
sudo su - oracle
cd /u01/scripts/lcm/sh
nohup sh update_service_host.sh -s <service_host> &
Example: sh update_service_host.sh -s wcc1913.cec.ocp.oc-test.com
The logs can be monitored using command: tail -f /u01/data/domains/logs/provisioning.log
| Note |
|---|
| If you configured the service host forWebCenter Content Marketplace or WebCenter Portal Marketplace installation, and had selected Enable Authentication Using Identity Cloud Service option during stack provisioning, then, you will need to re-apply the SSO configuration with the service host again. This is a required step. See Configure SAML2 IDCS Single Sign-On in WebCenter Content for WebCenter Content and Configure SAML2 IDCS Single Sign-On in WebCenter Portal for WebCenter Portal. |
Scale Out and Scale In WebCenter Nodes
For WebCenter on Marketplace, you can add or remove nodes from the stack using scripts.
-
Connect to the bastion instance as the opc user.
ssh -i path_to_private_key opc@bastion_public_ip -
Connect to the weblogic admin server compute instance which has a name ending with
'wls-1'.ssh -i path_to_private_key opc@compute_wls-1_private_ip -
Change to 'Oracle' user.
[opc@**-wls-1 ~]$ sudo su - oracle -
Change directory as '/u01/scripts/lcm/sh'
[opc@**-wls-1 ~]$ cd /u01/scripts/lcm/sh
Scale Out
To add more nodes to the WebCenter marketplace stack, execute the stack_manager.sh script as described below.
nohup sh stack_manager.sh -o scale_out -n <number_of_nodes_to_add> &> scale_out.log &
tail -f scale_out.log
Example: (to add 2 additional nodes to the stack)
nohup sh stack_manager.sh -o scale_out -n 2 &> scale_out.log &
tail -f scale_out.log
Note: New node provisioning will create the required block volumes with the same size as they on the admin VM during scale out (applicable for stacks created with 25.4.1 or higher).
Scale out based on different license type
Regular scale out script add nodes to the WebCenter marketplace stack using same license type as was used for the original stack provisioning. In case you want to add nodes using a different license type, you can raise a support ticket and provide following details:
- Current WebCenter marketplace stack product type (WebCenter Content/WebCenter Portal/WebCenter Sites)
- Current WebCenter marketplace stack license type (Paid/BYOL)
- New license type to use for new scaled out nodes (Paid/BYOL)
- Current WebCenter marketplace stack listing ID
- Current WebCenter marketplace stack listing version
- Component to scale out (This is required only for WebCenter Portal stack which has two set of nodes, WebCenter Portal and WebCenter Content)
Note: To get WebCenter marketplace stack listing ID and version details, you can login to the OCI console, navigate to the WebCenter stack and click the Application Information tab. You can get the listing details under section Listing
Scale In
To remove nodes from the WebCenter marketplace stack, execute the stack_manager.sh script as described below.
nohup sh stack_manager.sh -o scale_in -n <number_of_nodes_to_remove> &> scale_in.log &
tail -f scale_in.log
Example: (to remove 2 nodes from the stack)
nohup sh stack_manager.sh -o scale_in -n 2 &> scale_in.log &
tail -f scale_in.log
Backup and Restore Scripts for WebCenter
For WebCenter on Marketplace, you can perform backup and restore for weblogic domain and middleware home using scripts. For storing backup, you need to create an object storage bucket in the same tenancy, same region’s stack compartment.
List of product types with support for backup and restore operation:
- WebCenter Content
- WebCenter Portal
- WebCenter Sites
Backup WebCenter
To perform backup, separate scripts are available for the weblogic domain and middleware home. To run these scripts, complete the following steps:
Backup WebCenter Domain
-
Execute the following steps on each WebCenter compute instance.
- Connect to WebCenter Compute Instance.
-
Change to 'Oracle' user.
[opc@**-wls-1 ~]$ sudo su - oracle -
Change the directory to '/u01/scripts/lcm/sh'
cd /u01/scripts/lcm/sh
To perform the backup of the Weblogic domain for WebCenter, run the below command.
sh backup_domain.sh -b <bucket-name>
Backup WebCenter Middleware Home
-
Connect to the Bastion instance as the opc user.
ssh -i path_to_private_key opc@bastion_public_ip -
Connect to the Weblogic administration server compute instance which has a name ending with
'wls-1'.ssh -i path_to_private_key opc@compute_wls-1_private_ip -
Change to 'Oracle' user.
sudo su - oracle -
Change the directory to '/u01/scripts/lcm/sh'
cd /u01/scripts/lcm/shTo perform the backup of Weblogic Middleware Home for WebCenter, run the below command.
sh backup_middleware_home.sh -b <bucket-name>
Restore Backup of WebCenter
For restoring backups, separate scripts are available for the weblogic domain and middleware home. To run these scripts:
-
Execute the following steps on each WebCenter compute instance.
- Connect to WebCenter Compute Instance.
-
Change to 'Oracle' user.
[opc@**-wls-1 ~]$ sudo su - oracle -
Change the directory to '/u01/scripts/lcm/sh'
cd /u01/scripts/lcm/sh
Restore Backup of WebCenter Domain
To restore Weblogic Domain backup for WebCenter, run the below command.
sh restore_domain.sh -b <bucket-name>
Note: The script will show the Weblogic Domain backup available for WebCenter which can be used for the restore operation, and it will prompt for the file name as input.
Restore Backup of WebCenter Middleware Home
To restore Weblogic Middleware Home backup for WebCenter, run the below command.
sh restore_middleware_home.sh -b <bucket-name>
Note: The script will show the Weblogic Middleware Home backup available for WebCenter which can be used for the restore operation, and it will prompt for the file name as input.
About Quick Start for WebCenter on Marketplace
You can use the Oracle WebCenter on Marketplace Quick Start option to quickly provision WebCenter instances along with underlying Oracle Cloud Infrastructure resources. The Quick Start option allows you to provision an Oracle WebCenter environment with minimal set up. This option is available in both the Paid and BYOL offerings for the following Oracle WebCenter products on Marketplace:
- WebCenter Content
- WebCenter Portal
- WebCenter Sites
Resources and Features
The Oracle WebCenter Quick Start option sets up a stack environment with default configurations and resources that are available in the full provisioning process. It provisions a single WebCenter Compute Instance with underlying database, network, and storage resources.
- An Oracle Autonomous Transaction Processing (ATP) database is automatically provisioned with the Oracle WebCenter Quick Start instance.
- 2 ECPU and 1 TB Storage with database version Oracle Database.
- A Bastion instance is provisioned with the selected compute shape and 1 OCPU.
- The following Oracle Cloud Infrastructure network resources are created.
- Virtual Cloud Network (VCN) - 10.0.0.0/16
- Subnets for Compute instance, Bastion instance, Load balancer, and File System Mount Target
- Required Network Security Groups (NSGs), Service and NAT Gateways
- Flexible Load Balancer with a minimum bandwidth of 10 Mbps and a maximum bandwidth of 400 Mbps.
- A key management vault and a master encryption key are created to store the secrets (provided and generated).
- A file system along with a mount target is created in the Mount Target subnet for storing content.
- A block volume is created with 50 GB storage for Oracle WebCenter Quick Start instance.
- The required OCI Policies are created for the stack to manage Oracle Cloud Infrastructure resources.
- The monitoring resources such as OCI Logging and Monitoring agents are configured for OCI Metrics and Console Dashboard integration.
About Stack-Provisioning using Quick Start
Prerequisites
| Product | Related documentation |
|---|---|
| WebCenter Content | See information about system requirements, generating SSH key pair, and creating a compartment inUsing Oracle WebCenter Content on Marketplace. |
| WebCenter Portal | See information about system requirements, generating SSH key pair, and creating a compartment inUsing Oracle WebCenter Portal on Marketplace. |
| WebCenter Sites | See information about system requirements, generating SSH key pair, and creating a compartment inUsing Oracle WebCenter Sites on Marketplace. |
Create Vault
- Log in to the OCI console, search for Vault, and select Vault under Services. Click Create Vault.
- Select the compartment you created. Provide a name and click Create Vault.
Steps to Provision the Stack Using the Quick Start Option
- Launch the stack with the latest WebCenter stack template.
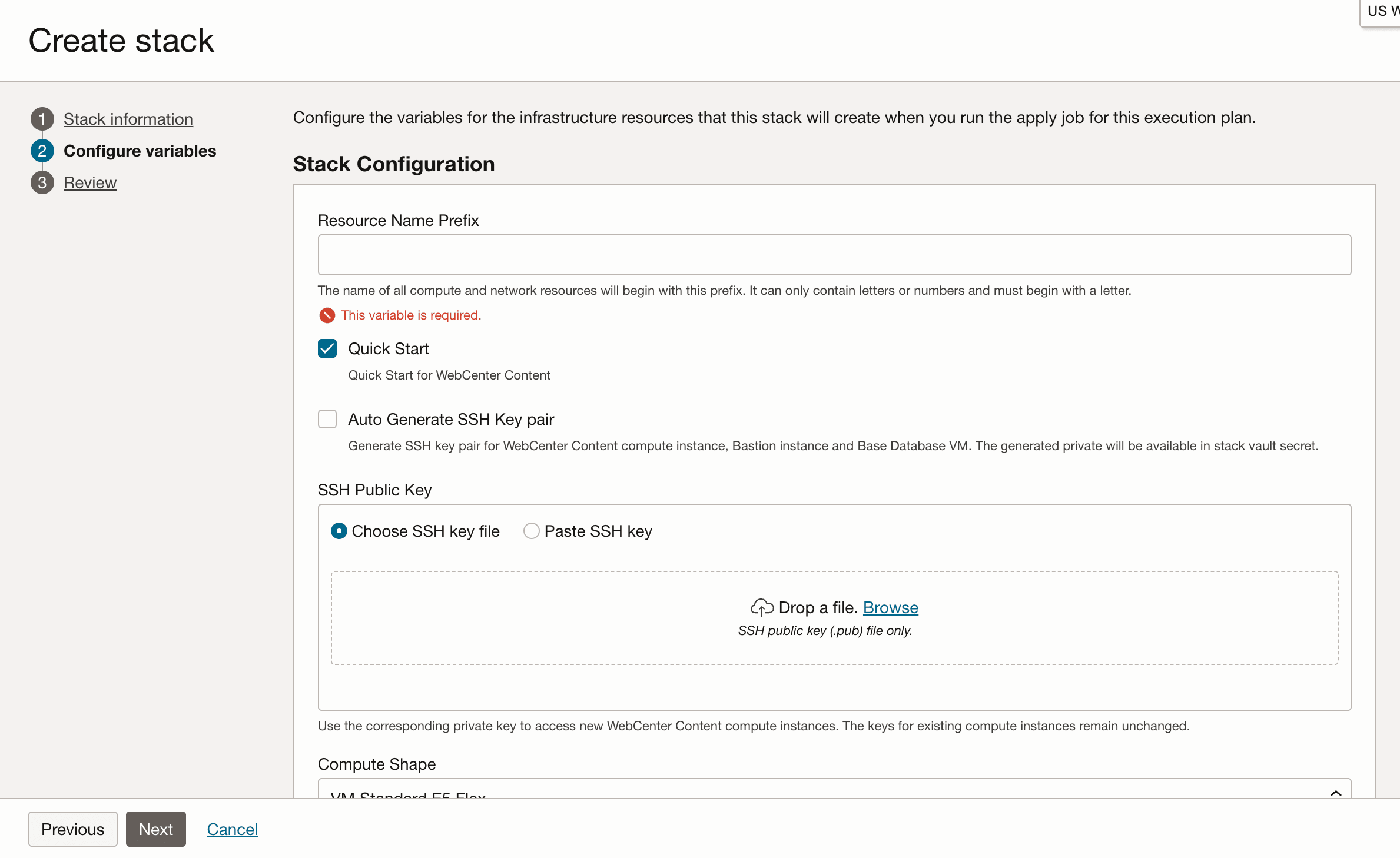
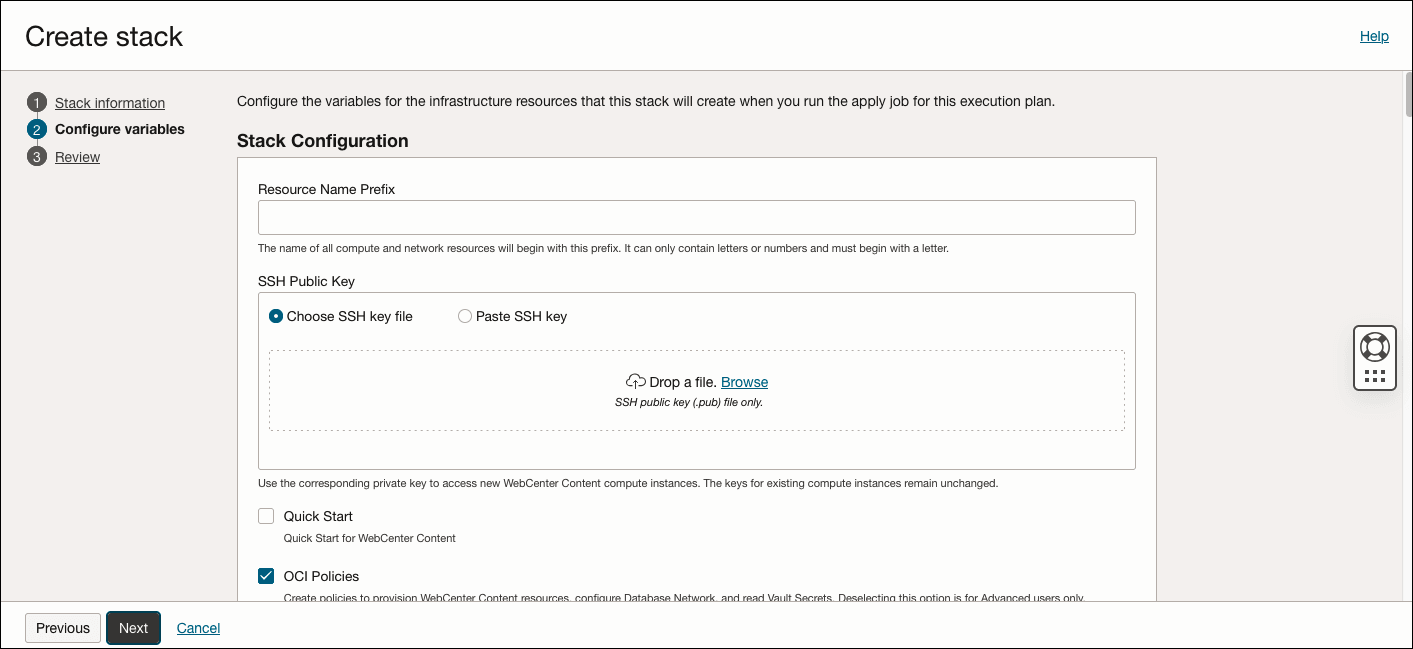
- On the Create stack page, when configuring the variables, in the Stack Configuration section, select the Quick Start check box to enable quick installation.
WebCenter Content
Other Products
-
Select the Auto Generate SSH Key Pair option to generate and use an SSH key pair for the database system, bastion VM, and WLS VM.
Note: The generated private key should be stored in the Stack Vault secret. Currently, the Auto Generate SSH Key Pair is supported only for WebCenter Content.
-
Configure the following variables:
-
Stack Configuration
- Resource Name Prefix: Enter a prefix (for example, WCC). The name of all compute and network resources will begin with this prefix. It must begin with a letter and it can contain only letters or numbers.
- SSH Public key: Provide the SSH public key (created earlier when you generated the SSH key pair). [This is not required if Auto Generate SSH Key Pair is selected].
- Compute Shape: Select the compute shape for Compute and Bastion instances.
-
Secrets Key Management
- OCI Vault compartment: Select the compartment of the OCI Vault created earlier in the Prerequisites section.
- OCI Vault to store secrets: Select the OCI Vault to store new KMS secrets.
-
Database
-
Database Type: Select the type of database to use for provisioning. The supported databases are: Database System 19c, Database System 23ai, Autonomous Transaction Processing Database 19c and Autonomous Transaction Processing Database 23ai.
If you selected Autonomous Transaction Processing Database 19c or Autonomous Transaction Processing Database 23ai as the Database Type, then complete the following that are displayed:
- Autonomous Database Password: Provide the value of Autonomous Database Admin password. Re-enter the password to confirm.
If you selected Database System 19c or Database System 23ai as the Database Type, then complete the following that are displayed:
- Database System: Provide the value of Database System Admin password. Re-enter the password to confirm.
- DB System SSH Private key: Upload the DB System SSH Private key when the “Auto Generate SSH Key pair” option is not selected.
Note: Currently, the Autonomous Transaction Processing Database 23ai, Database System 19c and Database System 23ai are supported only for WebCenter Content.
-
-
Identity Domain
-
Auto-Create Identity Domain App: If this option is selected, then a new IDCS App will be created during stack provisioning. It requires the provisioning user to be granted Identity Domain Administrator role in the selected domain. See Adding Identity Domain Administrators. If this is not feasible, an IDCS application needs to be created by following the steps described in Create IDCS Application.
If you selected Auto-Create Identity Domain App option, then complete the following that are displayed:
- Identity Domain Compartment: Select the compartment of identity domain.
- Identity Domain Name: Provide the name of identity domain.
- Identity Domain Username: Provide the value for IDCS username who will be configured as the product administrator.
If you deselected Auto-Create Identity Domain App option, then complete the following that are displayed:
- Identity Domain URL: Provide the value for IDCS domain URL.
- Identity Domain Username: Provide the value for IDCS username who will be configured as the product administrator.
- Identity Client ID: Provide the value for IDCS Client ID created earlier.
- Identity Client Secret: Provide the value for the IDCS client secret.
-
-
WebCenter WebLogic Domain
- WebCenter Admin User Name (Read only): By default, the user name is ‘weblogic’.
- WebCenter Admin Password: Provide the value for WebCenter Admin password. Re-enter the password to confirm.
-
Tagging
- Add Tags: Optionally add additional service tags.
-
- Review the information and create the stack.
-
After stack-creation, you can view the details for compute, database, and other OCI resources provisioned in the Applications Information tab of the stack.
Note: The WebCenter Schema Password is automatically generated and stored in the OCI Vault.
To access secrets, log in to the OCI console and search for the Vault.
- Select the Vault created earlier in the Prerequisites section.
- Click Secrets on the left navigation and select the secret with the resource name prefix.
- Under the latest active version, click on the options on the right side. Click View Secret Contents and enable Show decoded Base64 digit.
About Stack-Destroy using Quick Start
The ATP database or base database created as part of quick start provisioning should be terminated manually before attempting to destroy the stack provisioned using the quick start option. Failure to do so will cause the destroy job to fail.
Generate an SSH Key Pair for WebCenter
Note: This is not required if Auto Generate SSH Key Pair is selected
This section covers steps related to SSH key generation and conversion as per WebCenter marketplace requirements.
Generate an SSH Key Pair on UNIX or UNIX-Like Systems Using ssh-keygen
-
Run the ssh-keygen command.
ssh-keygen -m PEM -t rsa -b 2048 -
The command prompts you to enter the path to the file in which you want to save the key. A default path and file name are suggested in parentheses. For example: /home/user_name/.ssh/id_rsa. To accept the default path and file name, press Enter. Otherwise, enter the required path and file name, and then press Enter.
Generating public/private rsa key pair. Enter file in which to save the key (/home/user/.ssh/id_rsa): /home/user/.ssh/wc_id_rsa -
The command prompts you for a passphrase. Enter a passphrase. Hit Enter key for no passphrase
Note : If you are generating an SSH for a DB, the SSH key must not have a passphrase. Any other SSH key may or may not have a passphrase. In the tool, the passphrase isn’t displayed when you type it in. Remember the passphrase. If you forget the passphrase, you can’t recover it.
For generating a private key without any passphrase using passphrase-based key, see Convert a Passphrase-Based Private Key to Empty Passphrase Private Key section.
-
When prompted, enter the passphrase again to confirm it. Hit the Enter key for no passphrase.
Example:
Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /home/user/.ssh/wc_id_rsa. Your public key has been saved in /home/user/.ssh/wc_id_rsa.pub. The key fingerprint is: SHA256:IDO5bG4eL4CIPzA9PyDwdhSRYjaRBhwDwok4DEUzw5k user@user-DELL The key's randomart image is: +---[RSA 2048]----+ |&BX=.o | |==E+o. | | = o=.. | |. ..= . | |++ .+ S | |B Bo. | | * *+ | | oo+o | | ..o. | +----[SHA256]-----+ - The command generates an SSH key pair consisting of a public key and a private key, and saves them in the specified path. The file name of the public key is created automatically by appending .pub to the name of the private key file. For example, if the file name of the SSH private key is id_rsa, then the file name of the public key would be id_rsa.pub.
- Make a note of the path where you’ve saved the SSH key pair. When you create instances, you must provide the SSH public key. When you log in to an instance, you must specify the corresponding SSH private key and enter the passphrase when prompted.
Generate an SSH Key Pair on Windows Using the PuTTY Key Generator
- Download and install puttygen.exe from https://www.chiark.greenend.org.uk/~sgtatham/putty/latest.html.
- Find puttygen.exe in the PuTTY folder on your computer and double-click it.
- Accept the default key type, SSH-2 RSA, and set the Number of bits in a generated key to 2048, if it is not already set.
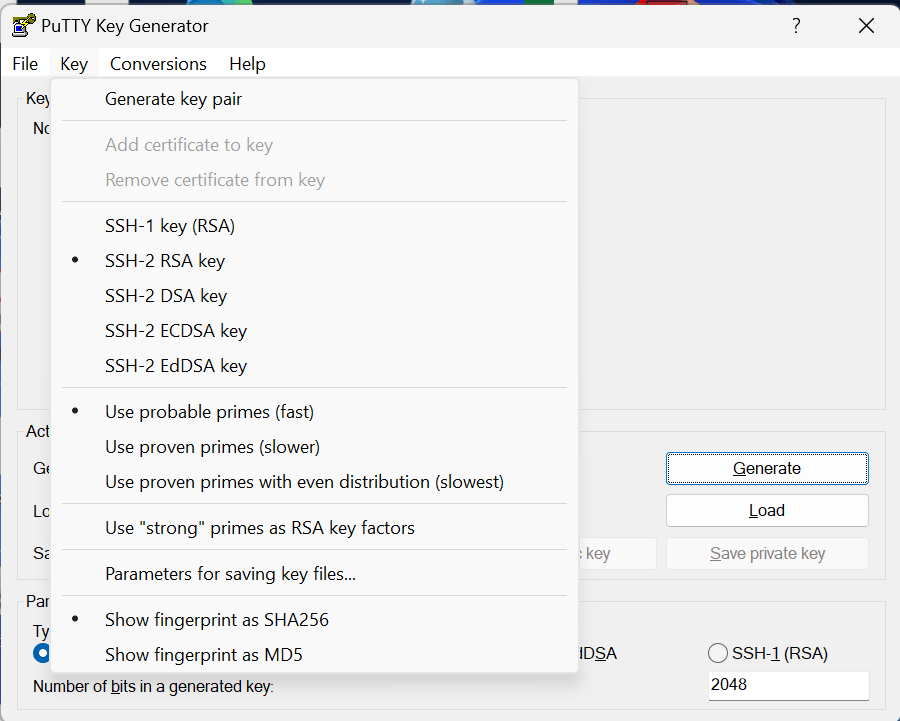
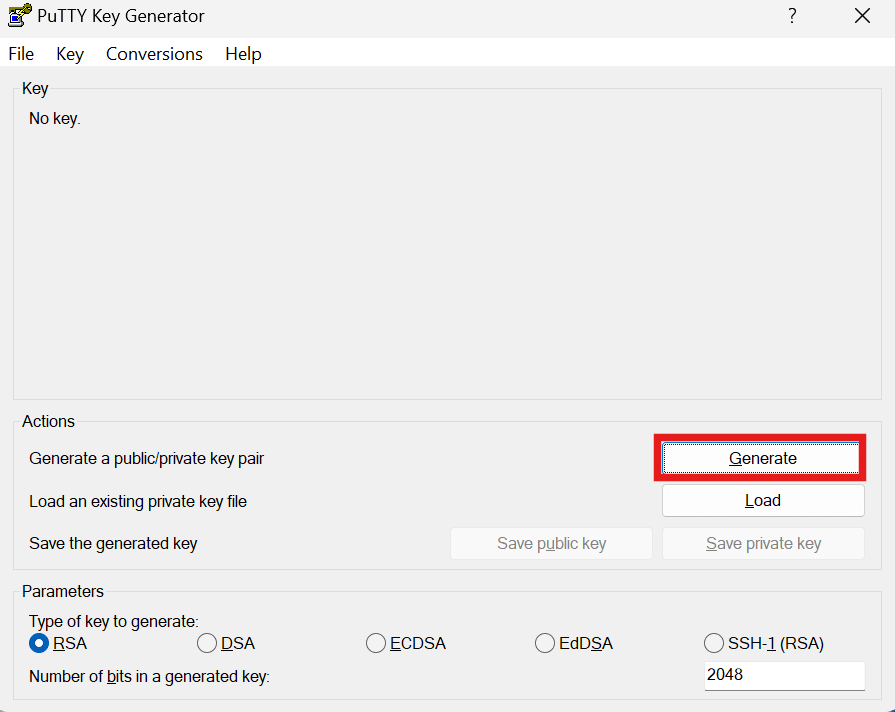
- Then click Generate.
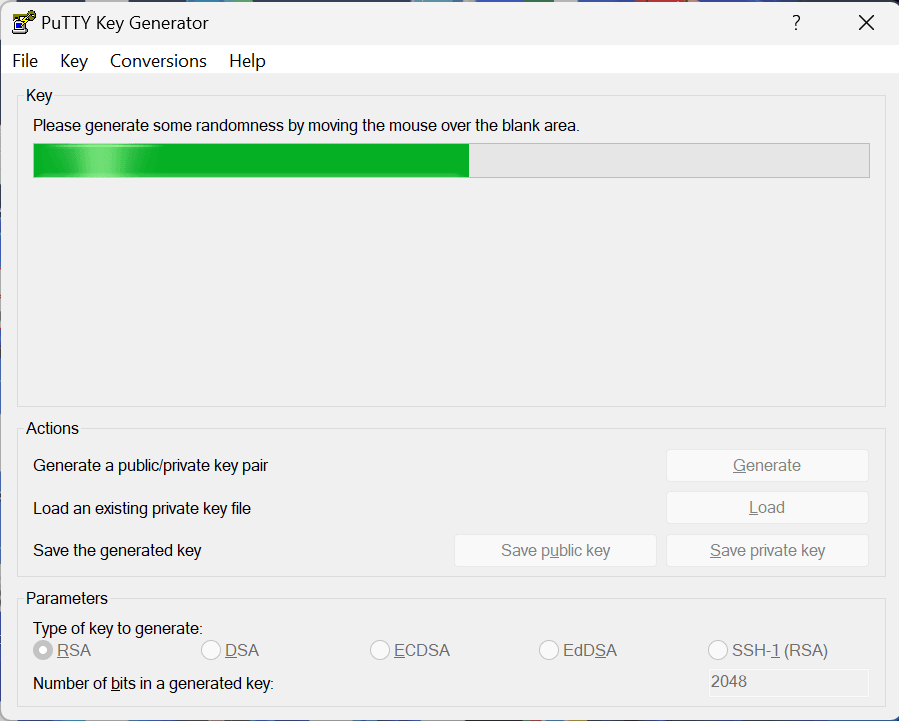
- Move your mouse around the blank area to generate randomness. The SSH key pair will be generated.
-
Save your SSH private key in OpenSSH format.
- The key comment is the name of the key. You can keep the generated key comment or create your own.
-
(Optional) Enter a passphrase in the Key passphrase and the Confirm fields.
Note: If you are generating an SSH for a DB, the SSH key must not have a passphrase. Any other SSH key may or may not have a passphrase. In the tool, the passphrase isn’t displayed when you type it in. Remember the passphrase. If you forget the passphrase, you can’t recover it.
For generating a private key without any passphrase using passphrase-based key, see Convert a Passphrase-Based Private Key to Empty Passphrase Private Key section.
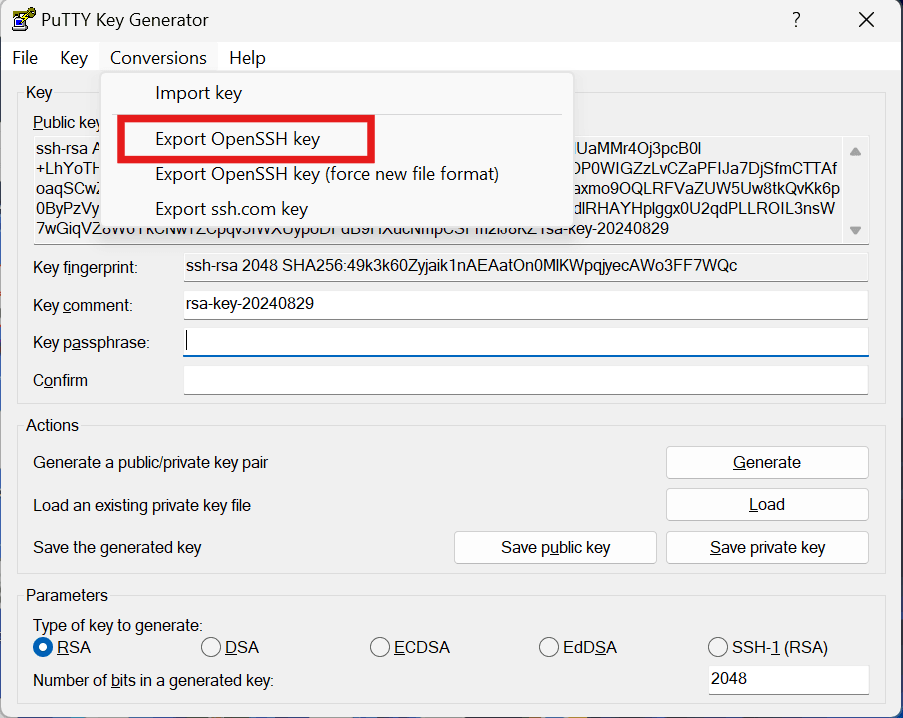
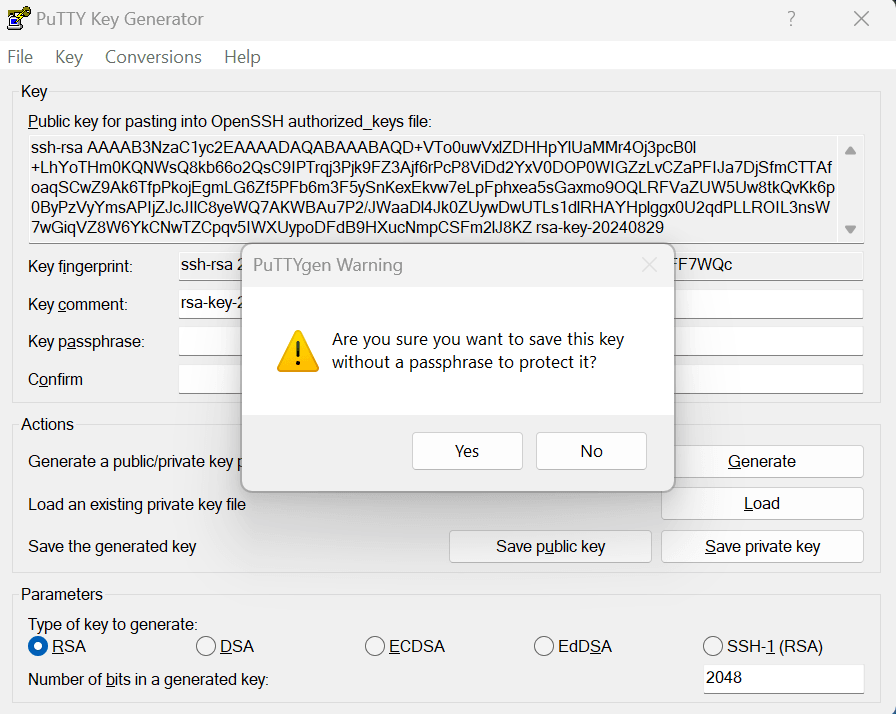
- To save the private key in OpenSSH format, in the Putty Key Generator, click Conversions and then click Export OpenSSH Key.
- Click Yes to save without a passphrase dialog.
- Save your file with a name such as
<webcenter-marketplace-stack-name>_id_rsaand save as typeAll Files (\*.\*).
-
Save your SSH private key in the Putty ppk format.
- The key comment is the name of the key. You can keep the generated key comment or create your own.
-
(Optional) Enter a passphrase in the Key passphrase and the Confirm fields.
Note: If you are generating an SSH for a DB, the SSH key must not have a passphrase. Any other SSH key may or may not have a passphrase. In the tool, the passphrase isn’t displayed when you type it in. Remember the passphrase. If you forget the passphrase, you can’t recover it.
- To save the private key in the PuTTY PPK format, click Save private key.
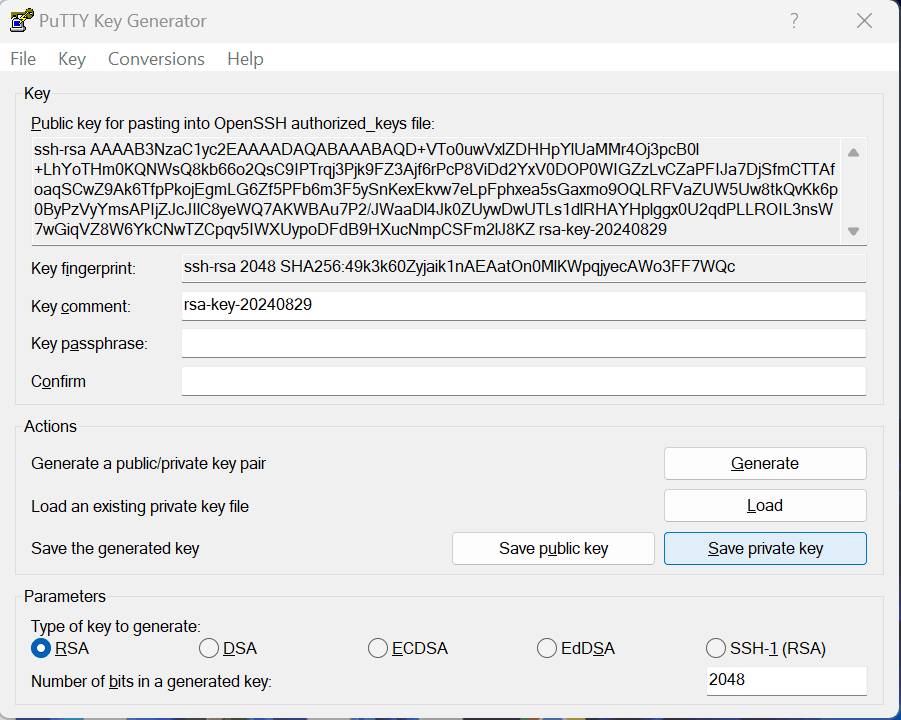
- Click Yes to save without a passphrase dialog (if it is shown).
- Save your file with a name such as
<webcenter-marketplace-stack-name>_sshand save as type ‘Putty Private Key Files (*.ppk)’. The private key is saved in PuTTY’s Private Key (PPK) format, which is a proprietary format that works only with the PuTTY toolset. You can use this key whenever you use PuTTY for SSH.
-
Save your SSH public key.
-
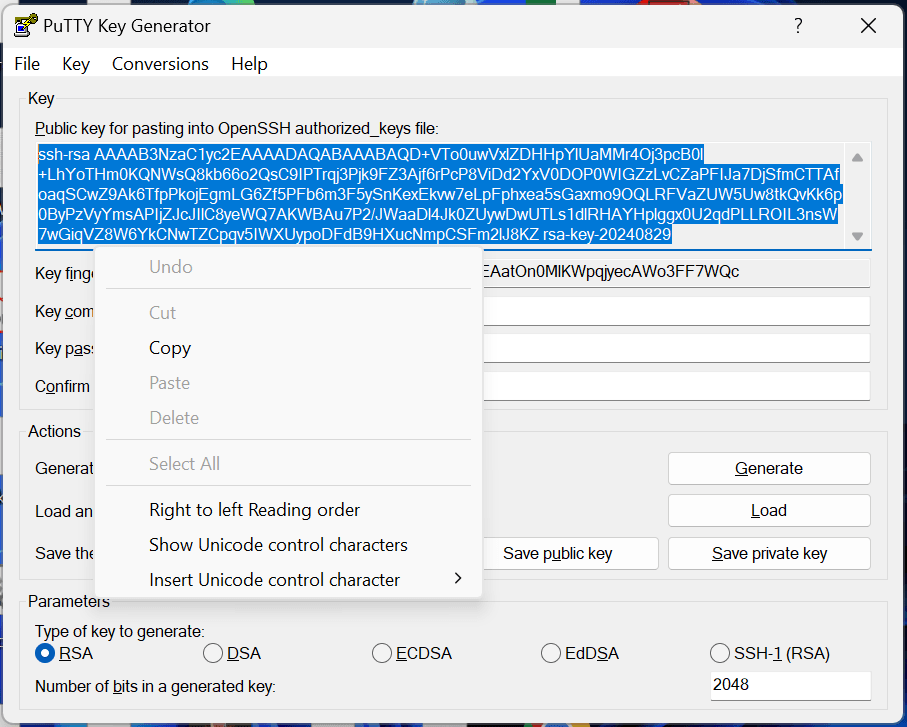
To save the public key, in the PuTTY Key Generator, select all the characters in the Public key for pasting into OpenSSH authorized_keys file field.
Note: Make sure you select all the characters, not just the ones you can see in the narrow window. If there is a scroll bar next to the characters, you aren’t seeing all the characters.
- Right-click somewhere in the selected text and select Copy from the menu.
- Open a notepad editor and paste the characters. Ensure that you paste the text at the first character in the text editor, and don’t insert any line breaks.
- Save your file with a name such as
<webcenter-marketplace-stack-name>_id_rsa.puband save as type ‘All Files (*.*)’. You can give it any extension you want, but .pub is a useful convention to indicate that this is a public key.
-
-
Finally, your SSH key folder should have 3 files like below.
File Name Purpose <webcenter-marketplace-stack-name>_ssh.ppkTo be used only with putty client for SSH. <webcenter-marketplace-stack-name>_id_rsaTo be used for any private SSH key input in OCI console.
To be used in bastion for doing SSH.<webcenter-marketplace-stack-name>_id_rsa.pubTo be used for any public SSH key input in OCI console. 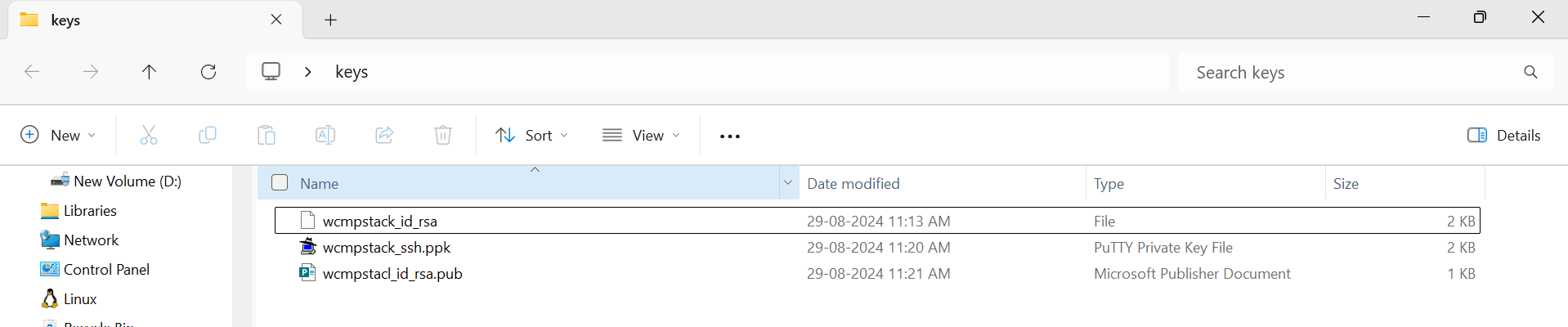
Configure Dynamic Groups and Policies for Non-Admin Delegated Users
Note: This configuration step is needed as part of prerequisites before provisioning the stack only if non-admin users need to provision the stack.
Compartments
Create compartments in the following hierarchy for provisioning WebCenter in OCI Marketplace.
You can choose any name for the new compartments.
-
Root compartment (Level 0)
-
New Parent Compartment (Level 1). We will refer this compartment as
$delegatedin the policies section.-
New Compartment for Database Network Configuration (Level 2)
- Create a Virtual Cloud Network for database in this compartment. We will refer this compartment as
$db_network_compartmentin the policies section.
- Create a Virtual Cloud Network for database in this compartment. We will refer this compartment as
-
New Compartment for Database (Level 2)
- Create a database in this compartment. We will refer this compartment as
$db_compartmentin the policies section.
- Create a database in this compartment. We will refer this compartment as
-
New Compartment for OCI Vault and Secrets (Level 2)
- Create a vault and all the required secrets in this compartment. We will refer this compartment as
$vault_secret_compartmentin the policies section.
- Create a vault and all the required secrets in this compartment. We will refer this compartment as
-
New Compartment for WebCenter Stacks (Level 2)
- Use this compartment for provisioning the WebCenter stacks. We will refer this compartment as
$stack_compartmentin the policies section.
- Use this compartment for provisioning the WebCenter stacks. We will refer this compartment as
-
-
Dynamic Groups
Pre-create a dynamic group for WebCenter usage before initiating provisioning of WebCenter in OCI Marketplace.
- Create a dynamic group with any name
<webcenter-dynamic-group>. We will refer this dynamic group as$dynamic_groupin the policies section. -
Add the following rule to the dynamic group created above.
instance.compartment.id='<compartment OCID of stack compartment>'
Policy in Root Compartment
Create a policy in the root compartment and add the following policy statements. Following policy statements are required only for Destroy stack operation.
Note: If you don’t have a user group for users, then create one before adding the policy statements.
Allow group '<domain>'/'<user-group>' to manage tag-namespaces in tenancy where target.tag-namespace.name='oracle-tags'
Policy in Delegated Compartment
Create a new policy in the parent compartment at Level 1 as mentioned in Compartments which contains all the child compartments for WebCenter provisioning.
Use one of the following approaches to create policies as needed.
Granular User Group Policies
Stack creation uses policies granted to the current OCI logged-in user. User group policies are required for the resource manager stack to manage resources.
-
User Policy to manage instance resources in stack compartment. This policy is required for stack to create compute instances.
Allow group '<domain>'/'<user-group>' to manage instance-family in compartment $stack_compartment
-
User Policy to manage volume resources in stack compartment. This policy is required for stack to create block volumes.
Allow group '<domain>'/'<user-group>' to manage volume-family in compartment $stack_compartment
-
User Policy to manage virtual network resources in stack compartment. This policy is needed for stack to create or update virtual network, security lists, subnets, etc.
Allow group '<domain>'/'<user-group>' to manage virtual-network-family in compartment $stack_network_compartment
-
User policy to manage load-balancer resources in stack compartment. This policy is needed for stack to create load balancer resources.
Allow group '<domain>'/'<user-group>' to manage load-balancers in compartment $stack_compartment
-
User policy to manage orm resources in stack compartment. This policy is needed to create and manage stack resources in stack compartment. This allows user to create/edit/delete Resource Manager stacks and plan/apply/destroy Resource Manager jobs.
Allow group '<domain>'/'<user-group>' to manage orm-family in compartment $stack_compartment
-
User policy to manage logging resources in stack compartment. This policy is used to manage logging service resources in stack compartment.
Allow group '<domain>'/'<user-group>' to manage logging-family in compartment $stack_compartment
-
User policy to manage file resources in stack compartment. This policy permits user to manage file-family resources in stack compartment
Allow group '<domain>'/'<user-group>' to manage file-family in compartment $stack_compartment
-
User policy to manage object in stack compartment. This policy permits user to manage object storage object, bucket, and namespace resources in stack compartment
Allow group '<domain>'/'<user-group>' to manage object-family in compartment $stack_compartment
-
User policy to manage secrets in stack compartment. This policy permits user to manage secrets, secret-versions, and secret-bundles in stack compartment.
Allow group '<domain>'/'<user-group>' to manage secret-family in compartment $vault_secret_compartment
-
User policy to manage keys in stack compartment. This policy permits user to manage vaults and keys in stack compartment.
Allow group '<domain>'/'<user-group>' to manage key-family in compartment $vault_secret_compartment
-
User policy to manage dns-resolvers in stack compartment. This policy permits user to manage dns-resolvers in stack compartment.
Allow group '<domain>'/'<user-group>' to manage dns-resolvers in compartment $stack_compartment
-
User policy to read database resources in database compartment. This policy permits user to have read access for database resources.
Allow group '<domain>'/'<user-group>' to read database-family in compartment $db_compartment
-
User policy to manage virtual network family in db vcn compartment. This policy permits user to manage DB network resources.
Allow group '<domain>'/'<user-group>' to manage virtual-network-family in compartment $db_network_compartment
-
User policy to read dns-resolvers in db vcn compartment.
Allow group '<domain>'/'<user-group>' to read dns-resolvers in compartment $db_network_compartment
-
User policy to read dns-views in db vcn compartment.
Allow group '<domain>'/'<user-group>' to read dns-views in compartment $db_network_compartment
-
User policy to read ATP resources in ATP DB compartment. Required for provisioning with ATP database. You can skip this policy statement if ATP database is not used.
Allow group '<domain>'/'<user-group>' to read autonomous-database-family in compartment $db_compartment
Granular Dynamic Group Policies
Dynamic group policies are required for configuration of OCI resources from instances created by stack.
-
This policy is only required if the stack’s VCN network compartment and stack compartment are different.
Allow dynamic-group '<domain>'/'<dynamic-group>' to read virtual-network-family in compartment $stack_network_compartment
-
Permits WebCenter Compute instance to read all required secrets.
Allow dynamic-group '<domain>'/'<dynamic-group>' to read secret-bundles in compartment $vault_secret_compartment where all { target.secret.id in ( '<OCIDs of pre-created OCI secret ids separated by comma>' ) }
-
Required only if DB System database is used. This policy allows to read database resource from db compartment.
Allow dynamic-group '<domain>'/'<dynamic-group>' to read database-family in compartment $db_compartment
-
Only required for DB System database. Permits read of virtual network resources in db network compartment.
Allow dynamic-group '<domain>'/'<dynamic-group>' to read virtual-network-family in compartment $db_network_compartment
-
Only required for DB System database. Permits to manage database vcn.
Allow dynamic-group '<domain>'/'<dynamic-group>' to manage virtual-network-family in compartment $db_network_compartment where target.vcn.id = '${<OCID of database VCN>}'
-
Only required for ATP serverless and dedicated databases.
Allow dynamic-group '<domain>'/'<dynamic-group>' to use autonomous-database in compartment $db_compartment
-
Permits WebCenter Compute instance to configure OCI Dashboard.
Allow dynamic-group '<domain>'/'<dynamic-group>' to manage dashboards-family in compartment $stack_compartment
-
Permits WebCenter Compute instance to update Load Balancer certificate.
Allow dynamic-group '<domain>'/'<dynamic-group>' to use load-balancers in compartment $stack_compartment
-
Permits WebCenter Compute instance to publish OCI metrics.
Allow dynamic-group '<domain>'/'<dynamic-group>' to use metrics in compartment $stack_compartment
-
Permits WebCenter Compute instance to do object bucket operations in stack compartment. Resource name here refers to the Resource Name Prefix of stack.
Allow dynamic-group '<domain>'/'<dynamic-group>' to {BUCKET_READ, OBJECT_INSPECT, OBJECT_READ, OBJECT_CREATE, OBJECT_OVERWRITE, OBJECT_DELETE, PAR_MANAGE} in compartment $stack_compartment where target.bucket.name='<resourcename>-webcenter-bucket'
-
Permits WebCenter Compute instance to manage instances in stack compartment.
Allow dynamic-group '<domain>'/'<dynamic-group>' to manage instance-family in compartment $stack_compartment
-
Permits WebCenter Compute instance to manage volumes in stack compartment.
Allow dynamic-group '<domain>'/'<dynamic-group>' to manage volumes in compartment $stack_compartment
-
Permits WebCenter Compute instance to manage network security groups in stack compartment.
Allow dynamic-group '<domain>'/'<dynamic-group>' to manage network-security-groups in compartment $stack_network_compartment
-
Permits WebCenter Compute instance to manage virtual network family in stack compartment.
Allow dynamic-group '<domain>'/'<dynamic-group>' to use virtual-network-family in compartment $stack_network_compartment
-
Permits WebCenter Compute instance to manage logging resources in stack compartment.
Allow dynamic-group '<domain>'/'<dynamic-group>' to use logging-family in compartment $stack_compartment
-
Permits runcommand to execute commands on Webcenter Compute instance.
Allow dynamic-group '<domain>'/'<dynamic-group>' to use instance-agent-command-execution-family in compartment $stack_compartment
-
Only required for Cross Region Disaster Recovery. Permits WebCenter Compute instance to manage secrets in vault compartment.
Allow dynamic-group '<domain>'/'<dynamic-group>' to manage secret-family in compartment $vault_secret_compartment
-
Only required for Cross Region Disaster Recovery. Permits WebCenter Compute instance to manage keys in vault compartment.
Allow dynamic-group '<domain>'/'<dynamic-group>' to manage keys in compartment $vault_secret_compartment
-
Only required for Cross Region Disaster Recovery. Permits WebCenter Compute instance to manage vaults in vault compartment.
Allow dynamic-group '<domain>'/'<dynamic-group>' to manage vaults in compartment $vault_secret_compartment
-
Only required for Cross Region Disaster Recovery. Permits WebCenter Compute instance to manage file systems in stack compartment.
Allow dynamic-group '<domain>'/'<dynamic-group>' to manage file-family in compartment $stack_compartment
-
Only required for Cross Region Disaster Recovery. Permits WebCenter Compute instance to manage replications in stack compartment.
Allow dynamic-group '<domain>'/'<dynamic-group>' to manage replication in compartment $stack_compartment
Setup DNS Resolver to resolve Database domain in WebCenter stack VCN
Note: This configuration step is needed as part of prerequisites before provisioning the stack only if the VCNs used for Database and WebCenter Stack pre-exist and are different.
- Navigate to WebCenter Stack VCN and click on DNS Resolver
- In Associated private views section, click on Manage private views
- Select Database VCN from drop-down list and click on Save changes
Package Logs for Troubleshooting
To troubleshoot any failures with the Oracle Support team, you can use the package logs tool in the WebCenter Compute instance for log collection.
-
Connect to the bastion instance as the opc user.
ssh -i <path_to_private_key> opc@<bastion_public_ip> -
Connect to WebCenter compute instance ending with ‘wls-1’.
ssh -i <path_to_private_key> opc@<compute_wls-1_private_ip> -
Switch to 'oracle' user.
sudo su - oracle -
Use the package logs script to collect logs from all servers.
By default, the package_logs.sh script will collect all server logs and configuration files that were modified within the past day. To view or change the parameters, you can run the script with the
-hflag. To collect additional logs, you can further specify which logs to package in the log file patterns. The log file patterns listed in configuration file/u01/scripts/lcm/configuration/package-logs/default-logswill be collected.Method 1: Package the logs and create the zip file in
/u01/data/domains/logs(If -t parameter is not passed, package zip will be created in/tmp.):sh /u01/scripts/lcm/sh/package_logs.sh -t /u01/data/domains/logsLogs will be packaged to a compressed tar archive file with the current timestamp. For example,
/u01/data/domains/logs/package-logs-20250326174703.tar.gz.To download the file to your local machine, you can run the following command locally.
scp -i <path_to_private_key> -oProxyCommand="ssh -i <path_to_private_key> -W %h:%p opc@<bastion_public_ip>" opc@<compute_wls-1_private_ip>:/u01/data/domains/logs/<package-logs-zip> <destination-file-path>/<package-logs-zip>Method 2: If you have a Pre-Authenticated Request (PAR) URL configured in Object Storage, you can upload packaged logs using PAR URL:
sh /u01/scripts/lcm/sh/package_logs.sh -t /u01/data/domains/logs -u <PAR_URL>
Integration of WebCenter Content with Microsoft 365 Office for the Web
Introduction
Documents in WebCenter Content of supported file formats can be viewed and edited in Microsoft 365 Office for the web after completing all the steps described in this chapter.
Users should have Microsoft 365 Office for the web subscription. The environment has to be whitelisted by Microsoft as described in the subsequent sections.
Steps to Configure WebCenter Content with Microsoft 365 Office for the web
Prerequisite
Ensure that you have a friendly domain configured for WebCenter Content URL (see Set Up DNS and SSL Certificate for WebCenter). For Microsoft to whitelist your environment, it needs a https-based domain URL.
Steps
-
Connect to the bastion instance as the opc user.
ssh -i <path_to_private_key> opc@<bastion_public_ip> -
Connect to WebCenter compute instance ending with ‘wls-1’.
ssh -i <path_to_private_key> opc@<compute_wls-1_private_ip> -
Switch to 'oracle' user.
sudo su - oracle -
Execute
configure_ms365_office_online.shscript to configure WebCenter Content for Microsoft 365 office online integration.With default discovery url
# To configure with default discovery url i.e https://onenote.officeapps.live.com/hosting/discovery cd /u01/scripts/lcm/sh ; sh configure_ms365_office_online.shWith custom discovery url
# To configure with custom discovery server url cd /u01/scripts/lcm/sh ; sh configure_ms365_office_online.sh -d <discovery server url> or cd /u01/scripts/lcm/sh ; sh configure_ms365_office_online.sh --discovery_url <discovery server url> # Example cd /u01/scripts/lcm/sh ; sh configure_ms365_office_online.sh -d https://dev.server.com/hosting/discovery or cd /u01/scripts/lcm/sh ; sh configure_ms365_office_online.sh --discovery_url https://dev.server.com/hosting/discoveryWith custom discovery url and proxy
# To configure with custom discovery server url cd /u01/scripts/lcm/sh ; sh configure_ms365_office_online.sh -d <discovery server url> -x <proxy-host> -p <proxy-port> or cd /u01/scripts/lcm/sh ; sh configure_ms365_office_online.sh --discovery_url <discovery server url> --proxy_host <proxy-host --proxy_port <proxy-port> # Example cd /u01/scripts/lcm/sh ; sh configure_ms365_office_online.sh -d https://dev.server.com/hosting/discovery -x dev-proxy.com -p 80 or cd /u01/scripts/lcm/sh ; sh configure_ms365_office_online.sh --discovery_url https://dev.server.com/hosting/discovery --proxy_host dev-proxy.com --proxy_port 80
Steps for Microsoft Office 365 Cloud Storage Partner Program
| Note |
|---|
| Before applying for CSPP Program, please ensure that you qualify for the program, and that you meet all the terms mentioned in cspp-terms. |
- Become a member of the Office 365 - Cloud Storage Partner Program (CSPP) by applying using this link.
- After you are admitted into the program, submit your environment for validation by the CSPP team.
- After provisioning your environment and after it is validated by the CSPP team, you will be asked to provide your production environment configuration to Microsoft.
- Your solution production configuration is added to the Office for the web production domain allow-list.
- Your solution goes live in production.
Create VCN and Subnets
For users planning to use pre-created or existing VCN:
Create VCN
Create Route Tables
Create Gateways
Note: Do not create a NAT gateway for a private service.
Note: Do not create an internet gateway for a private service.
Create Route Table for Public Subnets
Add a route rule for Internet Gateway created here.
Create Route Table for Private Subnets
Add a route rule for NAT Gateway created here.
Add a route rule for Service Gateway created here
Create Subnets
- Create a public subnet for bastion instance
- Create a public subnet for load balancer
- Create a private subnet for WebCenter instances
- Create a private subnet for mount targets
Integrate WebCenter on Marketplace with Stack Monitoring
Webcenter on Marketplace can be integrated with OCI Stack Monitoring to have better visibility on the Weblogic domain and compute hosts. Stack Monitoring provides a complete overview of the health and performance of Weblogic servers which can proactively track WebCenter resources.
Stack Monitoring can incur an additional charge. See pricing documentation.
Prerequisites
Enable Stack Monitoring in OCI Console
To enable Stack Monitoring for WebCenter, you will need to onboard your WebCenter compartment to Stack Monitoring in OCI console. See Enable the Stack Monitoring Service.
- Log in to OCI console as the admin user and navigate to Observability & Management, and then Stack Monitoring under Application Performance Monitoring.
- Switch to the compartment used to provision the WebCenter stack.
- Under the All Resources page (under Resources), the option Enable Stack Monitoring is available. Click that button, review the dynamic groups and policies being created, and confirm set-up.
Add Required IAM Policies for Stack Monitoring
- Navigate to Identity & Security and then Policies. Select the root compartment.
- Select the policy with the following name:
<resource-prefix-name>-<region>-oci-policy. - Add the following policy statements required to enable stack monitoring.
Allow dynamic-group $webcenter-dynamic-group to use management-agents in compartment id $webcenter-stack-compartmentAllow dynamic-group $webcenter-dynamic-group to manage stack-monitoring-family in compartment id $webcenter-stack-compartment
Enable Stack Monitoring for WebCenter
- SSH to WebCenter admin (wls-1) instance.
-
Switch to oracle user.
sudo su oracle -
Run the standalone script with the enabled (-e) flag to discover Weblogic domain and all compute hosts in the stack compartment.
cd /u01/scripts/lcm/sh sh configure_stack_monitoring.sh -e - After execution is successful, view monitored resources in OCI console under All Resources page in Observability & Management > Stack Monitoring.
Stack Monitoring can monitor additional OCI resources such as Autonomous Database, Load Balancer, or File System Storage. To add these resources to Stack Monitoring, you can import the resource as a custom resource under Resource Management > Import Resources on the Stack Monitoring page.
Refresh Stack Monitoring
After scaling out or scaling in WebCenter instances, you will need to refresh the monitored resources in the stack compartment. Run the script with the refresh (-r) flag to refresh the Weblogic domain discovery and update the monitored compute hosts.
Disable Stack Monitoring
To disable Stack Monitoring integration, run the standalone script with the disabled (-d) flag. The script will disable the management agents in compute hosts and stop monitoring all discovered resources.
Cross Region Disaster Recovery Provisioning Guide for WebCenter
This guide provides steps to enable cross region disaster recovery for a WebCenter Marketplace Stack.
Prerequisites
You’ll need to complete the following prerequisites before provisioning a Cross Region Disaster Recovery WebCenter stack.
Provision a Primary Stack with the Latest Version of WebCenter
-
If you have an existing stack, you will need to patch the WebCenter environment to the latest version using the Patch Tool. See About the Patch Tool.
-
Otherwise, you can provision a new WebCenter stack with the latest Marketplace listing.
Note: For setting up your primary WebCenter Stack, you should use a database which is dedicated for this DR environment and not shared with other applications or other stacks. This is required since during switchover process, the database role will change making the primary database read-only. If shared, this could lead to downtime for other applications relying on the same database.
To create a WebCenter Content stack, See Create and View Oracle WebCenter Content on Marketplace Instances for detailed steps.
To create a WebCenter Portal stack, follow Create and View Oracle WebCenter Portal on Marketplace.
To create a WebCenter Sites stack, follow Create and View Oracle WebCenter Sites on Marketplace Instances.
Set Up DNS and SSL Certificate for the Primary Stack
Follow Set Up DNS and SSL Certificate to map an external domain host to the public load balancer of the WebCenter stack and configure the SSL certificate.
(For WebCenter Sites Stack only) You will also need to configure Sites with DNS host name. See Set Up WebCenter Sites Configurator for steps to complete the setup.
Choose a Peer Region with Cross Region Replication Support
You will need to create the standby WebCenter stack in a paired region that supports cross region replication for your database, Block Volume, and File System.
Review System Requirements and Service Limits in Peer Region
For the peer region, review the service quota and limits required for provisioning a WebCenter Stack. For WebCenter Content stack, See WebCenter Content System Requirements. For WebCenter Portal stack, See WebCenter Portal System Requirements.
Enable Data Guard in Database to Peer Region
You will need to enable Data Guard for the database used to provision primary WebCenter Stack to the standby region. See the steps below about enabling Data Guard for the database in your primary stack.
For Autonomous Database
Refer to Enable Autonomous Database Dataguard for detailed steps to enable Data Guard for autonomous database.
For Base Database
For detailed steps to guide the setup process, see Enable Data Guard for Base Database.
If needed, refer to Use Oracle Data Guard on a DB System and Enable Oracle Data Guard on a DB System for further information to enable Data Guard on Base Database.
Set Up Object Storage
This step is required if object storage is used as the content storage strategy for your primary WebCenter Content or WebCenter Portal stack.
-
Set up an OCI user api key with privileges to manage buckets in the stack compartment as this user will be used to enable/disable replication on the object storage buckets. To set up OCI user api key, complete the following steps:
- Sign in to the Oracle Cloud Infrastructure console and click on your avatar in the upper-right corner of the page. Click My profile.
- In the Resources menu on the left side of the page, click API Keys.
- Click Add API Key.
- Download the private key by clicking Download private key.
- Click Add.
- Click Copy to copy the content of the configuration file which has user OCID and fingerprint as this will be required in the next step. Close the dialog.
For more details, see Set up User API Key.
-
Create the file /home/oracle/.oci/oci_api_key.pem with the oci api private key downloaded earlier and /home/oracle/.oci/config with the configuration file on the admin node (wls-1) as oracle user. Update the file permissions to read-only using the following commands:
Note: For WebCenter Portal stack, since we have two different admin vms (*-wcc-wls-1 and *-wcp-wls-1), we need to run the step on both.
# Create .oci folder mkdir -p /home/oracle/.oci # Create both the files /home/oracle/.oci/oci_api_key.pem and /home/oracle/.oci/config manually # Update file permissions chmod go-rwx /home/oracle/.oci/oci_api_key.pem chmod go-rwx /home/oracle/.oci/configSample OCI configuration file:
[DEFAULT] user=ocid1.user.oc1..<unique_ID> fingerprint=<your_fingerprint> key_file=/home/oracle/.oci/oci_api_key.pem tenancy=ocid1.tenancy.oc1..<unique_ID> region=us-ashburn-1 -
Create the object storage bucket in the standby region with the same name and in the same compartment as in the primary region. For this log in to OCI console, change the region to the standby region. Click the navigation menu in the upper left corner of the page and navigate to Storage and then Buckets. Select the stack compartment. Click Create Bucket. In the Bucket Name field, specify the same bucket name as the one used in the primary region for object storage configuration, leave other fields with default values, and click Create.
Note: If your primary stack was created prior to 25.7.1 release, you need to create only one bucket i.e Default Bucket, otherwise you must create three separate buckets: Default Bucket, Archive-Enabled Storage Bucket and Temporary Storage Bucket with the same name as was used in primary region.
-
Add the following object-storage related policy statements required for disaster recovery
- Allow service objectstorage-$primary_region_id to manage object-family in compartment id $stack_compartment
- Allow service objectstorage-$standby_region_id to manage object-family in compartment id $stack_compartment
For example, if primary region is frankfurt and standby region is zurich, policy statements will look like:
- Allow service objectstorage-eu-frankfurt-1 to manage object-family in compartment id $stack_compartment
- Allow service objectstorage-eu-zurich-1 to manage object-family in compartment id $stack_compartment
Replace $stack_compartment with the compartment OCID of the compartment where the stack is created. Replace $primary_region_id with the primary region identifier and $standby_region_id with standby region identifier. To get the region identifier for a region, see Regions and Availability Domains.
For details on how to add the policy, check the below section Add the Required Policies for Disaster Recovery in the Existing WebCenter Stack
Add the Required Policies for Disaster Recovery in the Existing WebCenter Stack
If your primary WebCenter stack was created before version 24.11.1, you will need to add the below required policies (if they do not already exist) for the existing stack’s WebCenter instance to replicate WebCenter resources to the peer region.
- Log in to OCI console, navigate to Identity & Security, and then Policies. Select the stack compartment.
- Select the policy with your resource name prefix. If your policy name does not contain the region, the policy name is
<resource-prefix-name>-oci-policy, otherwise it is<resource-prefix-name>-<primary-region>-oci-policy. For example, if the resource prefix for your primary stack is wccstack and primary region is eu-frankfurt-1, policy name will be wccstack-frankfurt-oci-policy. -
Add the following policy statements to your policy if they do not already exist:
Note: Replace $webcenter_dynamic_group with the stack dynamic group name, replace $vault_secret_compartment with the compartment OCID of the vault compartment, replace $stack_compartment with the compartment OCID of the compartment where the stack is created.
- Allow dynamic-group $webcenter_dynamic_group to manage secret-family in compartment id $vault_secret_compartment
- Allow dynamic-group $webcenter_dynamic_group to manage keys in compartment id $vault_secret_compartment
- Allow dynamic-group $webcenter_dynamic_group to manage vaults in compartment id $vault_secret_compartment
- Allow dynamic-group $webcenter_dynamic_group to manage file-family in compartment id $stack_compartment
- Allow dynamic-group $webcenter_dynamic_group to manage replication in compartment id $stack_compartment
If your primary stack is configured with Base Database, add the following policy statement to the policy if it does not already exist.
- Allow dynamic-group $webcenter_dynamic_group to use databases in compartment id $db_compartment
Add the Root Level Policies Required for Disaster Recovery
Whether you have an existing or a newly provisioned WebCenter stack, you will need to create below policy (if it does not already exist) in root compartment for disaster recovery scripts to work.
- Log in to OCI console, navigate to Identity & Security, and then Policies. Select the root compartment.
- Create a new policy with name
<resource-prefix-name>-oci-dr-policy(if it doesn’t already exist). For example, if the resource prefix for your primary stack is wccstack, policy name will be wccstack-oci-dr-policy. -
Add the following policy statements to your policy if they do not already exist:
Note: Replace $webcenter_dynamic_group with the stack dynamic group name. Stack dynamic group name will be in format
<resource-prefix-name>-<region>-webcenter-principal-group.- Allow dynamic-group $webcenter_dynamic_group to use tag-namespaces in tenancy
Replicate Primary Stack WebCenter Resources to Standby Region
You will need to execute the following script to replicate WebCenter resources to the peer (standby) region for standby provisioning.
Note: For WebCenter Portal stack, we have two different admin VMs (*-wcc-wls-1 and *-wcp-wls-1). We only need to execute the following script on WCC admin VM (*-wcc-wls-1).
-
Additional Prerequisite for WebCenter Portal stack only
-
Copy the opc user SSH private key to Bastion host of the stack. Now, perform SSH to Bastion of the stack as opc user and copy the opc user private key from Bastion host to WebCenter Content admin node (*-wcc-wls-1).
scp -i <opc_ssh_pvt_key> <opc_ssh_pvt_key> opc@<admin_node_private_ip>:/tmp -
Change ownership and permission of the key file in WebCenter Content admin node to allow only read access by oracle user.
chmod 600 <opc_ssh_pvt_key>chown oracle:oracle <opc_ssh_pvt_key>For example:
[opc@wccdr-bastion-instance ~]$ scp -i key key opc@192.168.128.20:/tmp/key [opc@wccdr-bastion-instance ~]$ ssh -i key opc@192.168.128.20 [opc@wccdr-wcc-wls-1 ~]$ [opc@wccdr-wcc-wls-1 ~]$ chmod 600 /tmp/key [opc@wccdr-wcc-wls-1 ~]$ chown oracle:oracle /tmp/key -
If the opc user ssh private key needs a passphrase, create a file for the passphrase on the admin node (*-wcc-wls-1) as oracle user.
# Switch to oracle user if current user is opc sudo su - oracle # Create passphrase file echo "<passphrase>" > /tmp/passphrase_file Example: echo "mypassphrase" > /tmp/passphrase_file
-
Replication Setup Steps
- SSH to WebCenter admin (wls-1) instance as opc user.
-
Switch to oracle user.
sudo su - oracle -
Navigate to the scripts directory.
cd /u01/scripts/lcm/sh -
Run the following script to replicate vault, secrets, file system, and block volumes to the peer region.
sh dr_manager.sh -o setup -r -e -s -t <peer-region-id>If object storage is configured, pass the oci-config-file and oci-config-profile as shown below (oci-config-profile is only needed if the profile to use is different from DEFAULT in the oci config file. For more details about profiles, see OCI Config File).
sh dr_manager.sh -o setup -r -e -s -t <peer-region-id> -p <oci-config-file> -q <oci-config-profile>For example, if the peer region is zurich, and object storage is enabled, then the command will look like below:
sh dr_manager.sh -o setup -r -e -s -t eu-zurich-1 -p /home/oracle/.oci/config -q DEFAULTFor WebCenter Portal stack only, we need to include the SSH private key path and the passphrase file if the key requires a passphrase:
sh dr_manager.sh -o setup -r -e -s -t <peer-region-id> -k <opc_ssh_private_key_path> -f <opc_ssh_private_key_passphrase_file> -p <oci-config-file> -q <oci-config-profile>For example with WebCenter Portal stack, if the peer region is zurich, object storage is enabled, and the SSH key includes a passphrase, then the command will look like below:
sh dr_manager.sh -o setup -r -e -s -t eu-zurich-1 -k /tmp/key -f /tmp/passphrase_file -p /home/oracle/.oci/config -q DEFAULT
Provision a Disaster Recovery Standby WebCenter Stack
- In OCI console, navigate to the chosen peer region and select the WebCenter Marketplace listing with the latest version. Launch the stack.
-
Provide information about the WebCenter stack.
- Stack Template information:
- Enter a name and description for the stack template.
- Create in Compartment: Select the compartment where the primary stack is created.
- Configure WebCenter variables:
-
Stack Configuration
- Standby Stack Provisioning for Disaster Recovery: Select this option for standby stack provisioning.
- SSH Public key: Provide the SSH public key for the standby stack. You can use the same SSH public key as the primary stack.
- OCI Policies: Select this option if policies were created for primary stack. Deselecting this option is for Delegated users only.
-
Disaster Recovery Configuration
- Primary Stack Resource Name Prefix: Enter the resource prefix name that was used to provision the primary stack. It is required to have the same name.
- Primary Stack Vault Compartment: Select the compartment where the OCI Vault was replicated. The compartment is the same as the primary stack’s vault compartment.
- Primary Stack Vault: Select the name of the OCI Vault. The vault name is the same as the primary stack’s vault.
-
Virtual Cloud Network
To use a new VCN for standby provisioning, select the Create the Virtual Cloud Network check box and complete the following:
- Network Compartment: Select the compartment of the primary stack.
- Virtual Cloud Network Name: Specify the name of the VCN created in the primary stack.
- Virtual Cloud Network CIDR: Specify the CIDR of the VCN created in the primary stack.
If you’re using an existing VCN for standby provisioning, complete the following:
- Network Compartment: Select the compartment of existing VCN.
- Existing WebCenter Content Virtual Cloud Network: Select the VCN provisioned for WebCenter Content.
Ensure the existing VCN has the required subnets and route tables as mentioned in Create VCN.
-
Bastion Instance
- Existing Subnet for Bastion Host: If you chose to use an existing VCN, select an existing public subnet to use for a Bastion compute instance.
- Bastion Host Shape: Select the appropriate Bastion host shape for standby stack.
- WebCenter Content Compute Instance
- Existing Subnet for WebCenter Content Compute Instances: If you chose to use an existing VCN, select an existing subnet to use for WebCenter Content compute instances.
- Compute Shape: Select the appropriate Compute instance shape for standby stack.
- WebCenter Portal Compute Instance (NOTE: This section is available only for WebCenter Portal stack)
- Existing Subnet for WebCenter Portal Compute Instances: If you chose to use an existing VCN, select an existing subnet to use for WebCenter Portal compute instances.
- Compute Shape: Select the appropriate Compute instance shape for standby stack.
- WebCenter Sites Compute Instance (NOTE: This section is available only for WebCenter Sites stack)
- Existing Subnet for WebCenter Sites Compute Instances: If you chose to use an existing VCN, select an existing subnet to use for WebCenter Sites compute instances.
- Compute Shape: Select the appropriate Compute instance shape for standby stack.
- File System
- File System Compartment: Choose the compartment where the WebCenter Content stack will be created.
- File System Availability Domain: Select the Availability Domain.
- Existing Subnet for Mount Target: If you chose to use an existing VCN, select an existing subnet for the mount target.
- Load Balancer
- Existing Subnet for Load Balancer: If you chose to use an existing VCN, select an existing subnet to use for the load balancer.
- Tagging
- Add Tags: Optionally add tags to the standby WebCenter resources.
-
- Stack Template information:
-
Click Next. Review all the configuration variables and then select the Run apply check box under Run apply on the created stack section. Click Create.
-
Plan and apply the stack. After stack apply is successful, you have successfully provisioned the Disaster Recovery WebCenter Standby stack.
-
Once the standby stack is created, you need to configure the SSL certificate on standby for the domain used during DNS setup for primary stack. Copy load balancer certificate, private key, OCI user config which was configured for DNS setup in primary to standby admin node (wls-1). Follow Set Up DNS and SSL Certificate, make sure you run the dns_and_cert_manager.sh script to install only the certificate and not set up the dns record. The below command is what you need to run as oracle user after passing appropriate values.
Note: For WebCenter Portal stack, since we have two different admin vms (*-wcc-wls-1 and *-wcp-wls-1), we need to run the step on both.
cd /u01/scripts/lcm/sh nohup sh dns_and_cert_manager.sh -c <certificate-file> -k <private-key-file> -d <primary-stack-dns-host> -t CERT &> dns_and_cert_manager.log & tail -f dns_and_cert_manager.log
Add the Root Level Policies Required for Disaster Recovery for Standby Stack
- Log in to OCI console, navigate to Identity & Security, and then Policies. Select the root compartment.
- Look for policy with name
<resource-prefix-name>-oci-dr-policy(it must have been created as part of Add the Root Level Policies Required for Disaster Recovery). For example, if the resource prefix for your primary stack is wccstack, policy name will be wccstack-oci-dr-policy. -
Add the following policy statements to your policy:
Note: Replace $webcenter_dynamic_group with the standby stack dynamic group name. Standby stack dynamic group name will be in format
<resource-prefix-name>-<standby-region>-webcenter-principal-group.- Allow dynamic-group $webcenter_dynamic_group to use tag-namespaces in tenancy
Switchover to Original Standby Region
To switchover from primary region to standby region, complete the following steps:
Note: For WebCenter Portal stack, we have two different admin VMs (*-wcc-wls-1 and *-wcp-wls-1). We only need to execute the following steps on WCC admin VM (*-wcc-wls-1). The switchover script will execute switchover for WCC and WCP in parallel to keep the switchover time to minimum.
-
Copy the opc user SSH private key to Bastion host of the standby stack (if not copied already). Now, perform SSH to Bastion of the standby stack as opc user and copy the opc user private key from Bastion host to WebCenter admin node (*-wls-1).
scp -i <opc_ssh_pvt_key> <opc_ssh_pvt_key> opc@<admin_node_private_ip>:/tmp -
Change ownership and permission of the key file in WebCenter admin node to allow only read access by oracle user.
chmod 600 <opc_ssh_pvt_key>chown oracle:oracle <opc_ssh_pvt_key>For example:
[opc@wccdr-bastion-instance ~]$ scp -i key key opc@192.168.128.20:/tmp/key [opc@wccdr-bastion-instance ~]$ ssh -i key opc@192.168.128.20 [opc@wccdr-wls-1 ~]$ [opc@wccdr-wls-1 ~]$ chmod 600 /tmp/key [opc@wccdr-wls-1 ~]$ chown oracle:oracle /tmp/key -
If the opc user ssh private key needs a passphrase, create a file for the passphrase on the admin node (*-wls-1) as oracle user
# Switch to oracle user if current user is opc sudo su - oracle # Create passphrase file echo "<passphrase>" > /tmp/passphrase_file Example: echo "mypassphrase" > /tmp/passphrase_file -
If your primary stack is configured with object storage, create file /home/oracle/.oci/oci_api_key.pem and /home/oracle/.oci/config on the standby stack admin node (*-wls-1) as oracle user and update the file permissions. This is the same private key and configuration file you created on the admin node of the primary stack. See Set up object storage
# Switch to oracle user if current user is opc sudo su - oracle # Create .oci folder mkdir -p /home/oracle/.oci # Create both the files /home/oracle/.oci/oci_api_key.pem and /home/oracle/.oci/config manually # Update file permissions chmod go-rwx /home/oracle/.oci/oci_api_key.pem chmod go-rwx /home/oracle/.oci/config -
Perform SSH to WebCenter admin node (*-wls-1) of original standby stack as opc user and switch to oracle. Execute the dr_manager.sh script. Note that oci-config-file and oci-config-profile are needed only if object storage is enabled.
Usage: sh dr_manager.sh -o switchover -t <dr_region> # dr_region is the original primary region id -k <opc_ssh_private_key_path> -f <opc_ssh_private_key_passphrase_file> -p <oci_config_file> -q <oci_config_profile> # Switch to oracle user if current user is opc sudo su - oracle cd /u01/scripts/lcm/sh nohup sh dr_manager.sh -o switchover -t <original-primary-region> -k <opc-user-pvt-key> -f <opc-user-pvt-key-passphrase-file> -p <oci-config-file> -q <oci-config-profile> &> /tmp/switchover.log & tail -f /tmp/switchover.log Example: (If original primary region is frankfurt and object storage is enabled) nohup sh dr_manager.sh -o switchover -t eu-frankfurt-1 -k /tmp/key -f /tmp/passphrase_file -p /home/oracle/.oci/config -q DEFAULT &> /tmp/switchover.log & tail -f /tmp/switchover.logNote: If the switchover script fails, simply rerun it. If the issue persists, submit a support ticket in My Oracle Support.
-
Map the DNS host for the stack to point to the standby stack load balancer. If you have configured original DNS host using OCI, you can use Set Up DNS and SSL Certificate to update the DNS record by executing the script dns_and_cert_manager.sh from original standby admin node (*-wls-1).
Note: _For WebCenter Portal stack, since we have two different admin VMs (*-wcc-wls-1 and *-wcp-wls-1), we need to run the step on both. Remember that domain name should be different for WCC and WCP. For example, domain name for WCC is wcpdr-wcc.example.com and for WCP is wcpdr-wcp.example.com. So we need to pass the corresponding value for
in the command below based on which admin VM the command is getting executed._ # Switch to oracle user if current user is opc sudo su - oracle cd /u01/scripts/lcm/sh nohup sh dns_and_cert_manager.sh -z <zone-name> -d <domain-name> -f <path-to-user-config> -t DNS &> dns_and_cert_manager.log & tail -f dns_and_cert_manager.log Example: nohup sh dns_and_cert_manager.sh -z example.com -d wccdr.example.com -f /u01/certs/config -t DNS &> dns_and_cert_manager.log & tail -f dns_and_cert_manager.logIf you have configured the DNS record for the primary stack via a third party, you will need to update the record to map to the load balancer for the standby stack. To get the load balancer IP for the standby stack, log in to OCI console, change region to standby region, change compartment to the compartment of the stack, navigate to Networking and then Load Balancers. The loadbalancer for the standby stack will be
<stack-name>-lb. In case of a Webcenter Portal stack, you will have two different load balancers<stack-name>-wcp-lband<stack-name>-wcc-lb. Note down the IP for these load balancer(s). -
(For WebCenter Sites Stack only) You will need to execute the following steps to reconfigure the Sites cluster with the original standby node’s host IP address. See the steps in Appendix Post Switchover Steps for WebCenter Sites Cross Region Disaster Recovery.
Switchback to Original Primary Region
To switchback from original standby region to original primary region, complete the following steps:
Note: For WebCenter Portal stack, we have two different admin VMs (*-wcc-wls-1 and *-wcp-wls-1). We only need to execute the following steps on WCC admin VM (*-wcc-wls-1). The switchback script will execute switchback for WCC and WCP in parallel to keep the switchback time to minimum.
-
Copy the opc user ssh private key to Bastion host of the original primary stack (if not copied already). Now perform SSH to Bastion of the original primary stack as opc user and copy the opc user private key from the Bastion host to WebCenter admin node (*-wls-1).
scp -i <opc_ssh_pvt_key> <opc_ssh_pvt_key> opc@<admin_node_private_ip>:/tmp -
Change ownership and permission of the key file in WebCenter admin node to allow only read access by oracle user.
chmod 600 <opc_ssh_pvt_key>chown oracle:oracle <opc_ssh_pvt_key>For example:
[opc@wccdr-bastion-instance ~]$ scp -i key key opc@192.168.128.18:/tmp/key [opc@wccdr-bastion-instance ~]$ ssh -i key opc@192.168.128.18 [opc@wccdr-wls-1 ~]$ [opc@wccdr-wls-1 ~]$ chmod 600 /tmp/key [opc@wccdr-wls-1 ~]$ chown oracle:oracle /tmp/key -
If the opc user ssh private key needs a passphrase, create a file for the passphrase on the admin node (*-wls-1) as oracle user
# Switch to oracle user if current user is opc sudo su - oracle # Create passphrase file echo "<passphrase>" > /tmp/passphrase_file Example: echo "mypassphrase" > /tmp/passphrase_file -
Perform SSH to WebCenter admin node (*-wls-1) of the original primary stack as opc user and switch to oracle. Execute the dr_manager.sh script. Note that oci-config-file and oci-config-profile are needed only if object storage is enabled.
Usage: sh dr_manager.sh -o switchback -t <dr_region> # dr_region is the original standby region id -k <opc_ssh_private_key_path> -f <opc_ssh_private_key_passphrase_file> -p <oci_config_file> -q <oci_config_profile> # Switch to oracle user if current user is opc sudo su - oracle cd /u01/scripts/lcm/sh nohup sh dr_manager.sh -o switchback -t <original-standby-region> -k <opc-user-pvt-key> -f <opc-user-pvt-key-passphrase-file> -p <oci-config-file> -q <oci-config-profile> &> /tmp/switchback.log & tail -f /tmp/switchback.log Example: (If original standby region is zurich and object storage is enabled) nohup sh dr_manager.sh -o switchback -t eu-zurich-1 -k /tmp/key -f /tmp/passphrase_file -p /home/oracle/.oci/config -q DEFAULT &> /tmp/switchback.log & tail -f /tmp/switchback.logNote: If the switchback script fails, simply rerun it. If the issue persists, submit a support ticket in My Oracle Support.
-
Map the DNS host for the stack to point to the original primary stack load balancer. If you have configured original DNS host using OCI, you can use Set Up DNS and SSL Certificate to update the DNS record by executing the script dns_and_cert_manager.sh from original primary admin node (*-wls-1).
Note: _For WebCenter Portal stack, since we have two different admin VMs (*-wcc-wls-1 and *-wcp-wls-1), we need to run the step on both. Remember that domain name should be different for wcc and wcp. For example, domain name for WCC is wcpdr-wcc.example.com and for WCP is wcpdr-wcp.example.com. So we need to pass the corresponding value for
in the command below based on which admin VM the command is getting executed._ # Switch to oracle user if current user is opc sudo su - oracle cd /u01/scripts/lcm/sh nohup sh dns_and_cert_manager.sh -z <zone-name> -d <domain-name> -f <path-to-user-config> -t DNS &> dns_and_cert_manager.log & tail -f dns_and_cert_manager.log Example: nohup sh dns_and_cert_manager.sh -z example.com -d wccdr.example.com -f /u01/certs/config -t DNS &> dns_and_cert_manager.log & tail -f dns_and_cert_manager.logIf you have configured the DNS record for the primary stack via a third party, you will need to update the record to map to the load balancer for the primary stack. To get the load balancer IP for the primary stack, log in to OCI console, change region to primary region, change compartment to the compartment of the stack, navigate to Networking and then Load Balancers. The loadbalancer for the primary stack will be
<stack-name>-lb. In case of a Webcenter Portal stack, you will have two different load balancers<stack-name>-wcp-lband<stack-name>-wcc-lb. Note down the IP for these load balancer(s). -
(For WebCenter Sites Stack only) You will need to execute the following steps to reconfigure the Sites cluster with the original primary node’s host IP address. See the steps in Appendix Post Switchover Steps for WebCenter Sites Cross Region Disaster Recovery.
Fix Expired Schema Password Guide For Webcenter Content
Command Usage
$ cd /u01/scripts/lcm/sh/
$ sh manage_schema_auth.sh -h
usage: manage_schema_auth.sh [-h] [--debug-level DEBUG_LEVEL] [--duration DURATION] [--ignore-error] {list_webcenter_schemas,reset_password} ...
Toolkit to manage schema for WebCenter marketplace installation.
options:
-h, --help show this help message and exit
--debug-level DEBUG_LEVEL
Specify logging level. (default: INFO)
--duration DURATION Expiring in duration, please specify, using duration followed by d for days or M for months. (default: 45d)
--ignore-error Ignore error that may occur. (default: False)
subcommands:
Specify either of list or reset operation.
{list_webcenter_schemas,reset_password}
Please select options
list_webcenter_schemas
List Webcenter Schemas
reset_password Reset password for Webcenter
List Expired Password
-
To verify if currently any schema password has expired, in the admin node, please execute below command, in the directory
/u01/scripts/lcm/sh/:$ cd /u01/scripts/lcm/sh/ $ sh manage_schema_auth.sh list_webcenter_schemasFor example a sample output as below would be be produced:
% Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 100 9620 0 9620 0 0 3131k 0 --:--:-- --:--:-- --:--:-- 3131k <Jan 27, 2025 07:38:19 AM GMT> <INFO> <loadProperties> <Loading /u01/scripts/props/webcenter.properties ...> <Jan 27, 2025 07:38:20 AM GMT> <INFO> <db_utils> <(host:wcs92z8usp8fwld-wls-1) - ATP name is wccpipeline_tpurgent> <Jan 27, 2025 07:38:20 AM GMT> <INFO> <db_utils> <(host:wcs92z8usp8fwld-wls-1) - Downloading atp wallet at [/u01/data/atp/wallet] ...> <Jan 27, 2025 07:38:23 AM GMT> <INFO> <db_utils> <(host:wcs92z8usp8fwld-wls-1) - ATP wallet downloaded successfully> <Jan 27, 2025 07:38:23 AM GMT> <INFO> <manage_schema_auth> <(host:wcs92z8usp8fwld-wls-1) - Starting operation: [list_webcenter_schemas] ...> <Jan 27, 2025 07:38:23 AM GMT> <INFO> <manage_schema_auth> <(host:wcs92z8usp8fwld-wls-1) - Schema prefix: WCS92Z8U1> <Jan 27, 2025 07:38:23 AM GMT> <INFO> <manage_schema_auth> <(host:wcs92z8usp8fwld-wls-1) - No schema found expiring in 45d.> <Jan 27, 2025 07:38:23 AM GMT> <INFO> <manage_schema_auth> <(host:wcs92z8usp8fwld-wls-1) - Completed operation: [list_webcenter_schemas] with RC Code 0. Time taken: 1s> -
By default, only 45d are considered for checking expiry. If you wish to check password expiring in 90d, then execute as below:
$ sh manage_schema_auth.sh --duration 90d list_webcenter_schemasA sample output as below would be available:
% Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 100 10552 0 10552 0 0 2576k 0 --:--:-- --:--:-- --:--:-- 2576k <Jan 30, 2025 06:32:20 AM GMT> <INFO> <loadProperties> <Loading /u01/scripts/props/webcenter.properties ...> <Jan 30, 2025 06:32:21 AM GMT> <INFO> <manage_schema_auth> <(host:wcmp4431-wls-1) - Starting operation: [list_webcenter_schemas] ...> <Jan 30, 2025 06:32:21 AM GMT> <INFO> <manage_schema_auth> <(host:wcmp4431-wls-1) - Schema prefix: WCCC3001255> <Jan 30, 2025 06:32:23 AM GMT> <INFO> <manage_schema_auth> <(host:wcmp4431-wls-1) - Schema: WCCC3001255_APEX_PUBLIC_USER is expiring in 6d 23h 19m 49s.> <Jan 30, 2025 06:32:23 AM GMT> <INFO> <manage_schema_auth> <(host:wcmp4431-wls-1) - Schema: WCCC3001255_CAPTURE is expiring in 6d 23h 18m 40s.> <Jan 30, 2025 06:32:23 AM GMT> <INFO> <manage_schema_auth> <(host:wcmp4431-wls-1) - Schema: WCCC3001255_IAU is expiring in 6d 23h 18m 38s.> <Jan 30, 2025 06:32:23 AM GMT> <INFO> <manage_schema_auth> <(host:wcmp4431-wls-1) - Schema: WCCC3001255_IAU_APPEND is expiring in 6d 23h 18m 35s.> <Jan 30, 2025 06:32:23 AM GMT> <INFO> <manage_schema_auth> <(host:wcmp4431-wls-1) - Schema: WCCC3001255_IAU_VIEWER is expiring in 6d 23h 18m 36s.> <Jan 30, 2025 06:32:23 AM GMT> <INFO> <manage_schema_auth> <(host:wcmp4431-wls-1) - Schema: WCCC3001255_IPM is expiring in 6d 23h 18m 40s.> <Jan 30, 2025 06:32:23 AM GMT> <INFO> <manage_schema_auth> <(host:wcmp4431-wls-1) - Schema: WCCC3001255_MDS is expiring in 6d 23h 18m 36s.> <Jan 30, 2025 06:32:23 AM GMT> <INFO> <manage_schema_auth> <(host:wcmp4431-wls-1) - Schema: WCCC3001255_OCS is expiring in 6d 23h 18m 39s.> <Jan 30, 2025 06:32:23 AM GMT> <INFO> <manage_schema_auth> <(host:wcmp4431-wls-1) - Schema: WCCC3001255_OPSS is expiring in 6d 23h 18m 39s.> <Jan 30, 2025 06:32:23 AM GMT> <INFO> <manage_schema_auth> <(host:wcmp4431-wls-1) - Schema: WCCC3001255_ORDS_PUBLIC_USER is expiring in 6d 23h 19m 49s.> <Jan 30, 2025 06:32:23 AM GMT> <INFO> <manage_schema_auth> <(host:wcmp4431-wls-1) - Schema: WCCC3001255_STB is expiring in 6d 23h 18m 34s.> <Jan 30, 2025 06:32:23 AM GMT> <INFO> <manage_schema_auth> <(host:wcmp4431-wls-1) - Schema: WCCC3001255_WCCREPORTS is expiring in 6d 23h 19m 49s.> <Jan 30, 2025 06:32:23 AM GMT> <INFO> <manage_schema_auth> <(host:wcmp4431-wls-1) - Schema: WCCC3001255_WLS is expiring in 6d 23h 18m 37s.> <Jan 30, 2025 06:32:23 AM GMT> <INFO> <manage_schema_auth> <(host:wcmp4431-wls-1) - Schema: WCCC3001255_WLS_RUNTIME is expiring in 6d 23h 18m 37s.> <Jan 30, 2025 06:32:23 AM GMT> <INFO> <manage_schema_auth> <(host:wcmp4431-wls-1) - Completed operation: [list_webcenter_schemas] with RC Code 0.
Reset Expired Schema Password
To reset expired schema password, please execute command as below in the directory: /u01/scripts/lcm/sh/:
cd /u01/scripts/lcm/sh/
sh manage_schema_auth.sh reset_password
If you wish to reset password that are expiring in say 100 days then you can execute command as below:
cd /u01/scripts/lcm/sh/
sh manage_schema_auth.sh --duration 100d reset_password
Please note that during the execution you will be prompted to provide a valid schema password. Please make a note of it and provide it during execution.
A sample output as below will be produced:
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 10113 0 10113 0 0 2468k 0 --:--:-- --:--:-- --:--:-- 3291k
<Jan 30, 2025 6:33:02 PM GMT> <INFO> <loadProperties> <Loading /u01/scripts/props/webcenter.properties ...>
<Jan 30, 2025 6:33:04 PM UTC> <INFO> <db_utils> <(host:wc3768uqjmbedgg-wls-1) - ATP name is wccpipeline_tpurgent>
<Jan 30, 2025 6:33:05 PM UTC> <INFO> <manage_schema_auth> <(host:wc3768uqjmbedgg-wls-1) - Starting operation: [reset_password] ...>
<Jan 30, 2025 6:33:06 PM UTC> <INFO> <manage_schema_auth> <(host:wc3768uqjmbedgg-wls-1) - Expired user: WC3768F7EE_WCCREPORTS>
<Jan 30, 2025 6:33:06 PM UTC> <INFO> <manage_schema_auth> <(host:wc3768uqjmbedgg-wls-1) - Expired user: WC3768MFDT_IAU>
...
...
...
<Jan 30, 2025 6:46:12 AM GMT> <Info> <wc_server_mgr> <BEA-000000> <(host:wcmp4431-wls-1) - - WC Server [UCM_server2] is in [RUNNING] state>
<Jan 30, 2025 6:46:12 AM GMT> <Info> <wc_server_mgr> <BEA-000000> <(host:wcmp4431-wls-1) - - WC Server [WCCADF_server2] is in [RUNNING] state>
<Jan 30, 2025 6:46:12 AM GMT> <Info> <wc_server_mgr> <BEA-000000> <(host:wcmp4431-wls-1) - - WC Server [capture_server2] is in [RUNNING] state>
<Jan 30, 2025 6:46:12 AM GMT> <Info> <wc_server_mgr> <BEA-000000> <(host:wcmp4431-wls-1) - - WC Server [IPM_server2] is in [RUNNING] state>
<Jan 30, 2025 6:46:12 AM GMT> <Info> <wc_server_mgr> <BEA-000000> <(host:wcmp4431-wls-1) - Polling for WC Servers completed>
Disconnected from weblogic server: AdminServer
<Jan 30, 2025 6:46:12 AM GMT> <Info> <wc_server_mgr> <BEA-000000> <(host:wcmp4431-wls-1) - WC Servers [start] completed successfully>
]
Execution Error/Warning: [Jan 30, 2025 6:34:36 AM oracle.security.jps.internal.config.xml.XmlConfigurationFactory validateFileLocation
INFO: JPS Config: /u01/data/domains/wcc_domain/config/fmwconfig/jps-config-jse.xml
Jan 30, 2025 6:34:37 AM oracle.security.opss.internal.runtime.ServiceContextManagerImpl getContext
WARNING: Bootstrap services are used by OPSS internally and clients should never need to directly read/write bootstrap credentials. If required, use Wlst or configuration management interfaces.
]>
<Jan 30, 2025 06:46:13 AM GMT> <INFO> <manage_schema_auth> <(host:wcmp4431-wls-1) - Completed operation: [reset_password] with RC Code 0. Time taken: 13m 16s>
Please note that warning as below can be safely ignored:
WARNING: Bootstrap services are used by OPSS internally and clients should never need to directly read/write bootstrap credentials. If required, use Wlst or configuration management interfaces.
RC Code: 0 indicates that the password has been successfully updated.
Existing Stack License Change Provisioning Guide for Webcenter Content Stack
This section covers procedure steps for WebCenter Content stack license change. Stack License Change can be useful for various use cases like updating license type or underlying operating system/infrastructure.
Prerequisites
You will need to execute the following script to upload stack metadata as a secret in vault for license change type of provisioning.
- SSH to WebCenter admin (wls-1) instance as opc user.
-
Switch to oracle user.
sudo su - oracle - Update the scripts to the latest version using Update the Current Node with Scripts from the Latest Release Version.
-
Navigate to the scripts directory.
cd /u01/scripts/lcm/sh -
Run the following script to upload stack metadata as a secret in vault.
sh backup_stack_metadata.sh -
Stop all servers using below command (Update the command before running it based on number of servers in WCC domain)
cd /u01/scripts/lcm/sh sh webcenter_server_manager.sh -a shutdown -s 'UCM_server2,UCM_server1,capture_server2,capture_server1,IPM_server2,IPM_server1,WCCADF_server2, WCCADF_server1,IBR_server1,AdminServer'
Steps for License Change
Create new stack with license change mode provisioing
-
Login to oci console and Launch the desired Webcenter Content stack.
-
Provide stack name and description and click Next.
-
On next page provide new resource prefix for new stack and check the Check for license change of an existing stack checkbox.
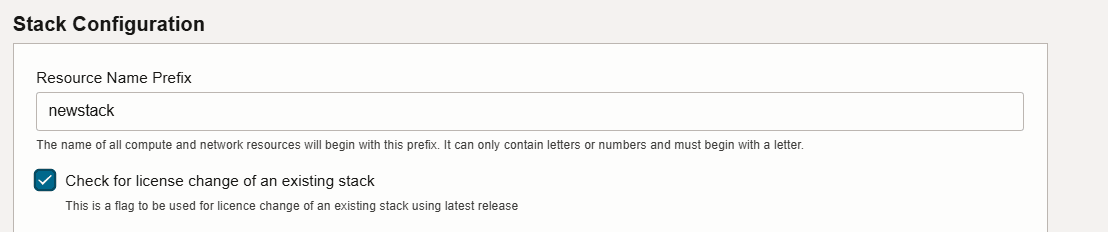
- Provide resource prefix for source stack carefully as that is case sensitive.
- Provide all other inputs and apply stack. ( Please note to select the same Availability Domain as that of source stack in the File System section )
- If apply job is successful login to VM-1 of new stack and run following as per requirement
- Update DNS entry so it points to new load balancer IP (if applicable).
- Run /u01/scripts/lcm/sh/update_service_host.sh with desired service host value. Refer Set Up DNS and SSL Certificate for WebCenter.
- Re-configure SAML SSO to map with your service host name. The steps are described in Configuration in WebCenter Content Stack for WebCenter Content.
Note: If apply job fails proceed with rollback steps from next section.
- Do functional validation and check if all endpoints are accessible.
Cleanup Steps for Source Stack
- For source stack you need upload an empty terraform state using OCI console with below json content
{ "version": 4, "serial": 1, "outputs": {}, "resources": [] } -
For source stack deletion, need to add below statement in policy created for new stack so from new stack VM you will be able to delete these resources.
Add following policy statments into stack compartment level policy for new stack (Update for dynamic group name and compartment ids before adding)
Allow dynamic-group <new-stack-prefix>-<region>-webcenter-principal-group to read orm-family in compartment id <stack-comp-id> Allow dynamic-group <new-stack-prefix>-<region>-webcenter-principal-group to manage load-balancers in compartment id <stack-comp-id> Allow dynamic-group <new-stack-prefix>-<region>-webcenter-principal-group to manage logging-family in compartment id <stack-comp-id>Add following policy statments into root compartment level policy for newly created stack (Update for dynamic group name and compartment ids before adding)
Allow dynamic-group <new-stack-prefix>-<region>-webcenter-principal-group to manage network-security-groups in tenancy Allow dynamic-group <new-stack-prefix>-<region>-webcenter-principal-group to manage dynamic-groups in tenancy Allow dynamic-group <new-stack-prefix>-<region>-webcenter-principal-group to manage policies in tenancy - SSH to WebCenter admin (wls-1) instance of new stack as opc user.
-
Switch to oracle user.
sudo su - oracle
-
-
Navigate to the scripts directory.
cd /u01/scripts/lcm/sh -
Run the following script to delete source stack related resources.
sh delete_source_stack.sh -s <resource-prefix-for-source-stack> -c <resource-prefix-for-new-stack>Note: Update this command for resource prefixes carefully before running.
- Once source stack resources are deleted via script, License change type of provisioning is completed and you can start using new stack.
Rollback Steps
If for any reason new stack is not working fine and you want to rollback to source stack, you need do following
- SSH to WebCenter admin (wls-1) instance of source stack as opc user.
-
Switch to oracle user.
sudo su - oracle -
Start all servers using below command . (Update the command before running it based on number of servers in WCC domain)
cd /u01/scripts/lcm/sh sh webcenter_server_manager.sh -a start -s 'UCM_server2,UCM_server1,capture_server2,capture_server1,IPM_server2,IPM_server1,WCCADF_server2, WCCADF_server1,IBR_server1,AdminServer' - Run /u01/scripts/lcm/sh/update_service_host.sh with desired service host value. Refer Set Up DNS and SSL Certificate for WebCenter.
-
Re-configure SAML SSO to map with your service host name. The steps are described in Configuration in WebCenter Content Stack for WebCenter Content.
- Run destroy stack operation for newly created stack from oci console. Once destroy operation job completes, delete the newly created stack.
Deletion/Destroy Steps for New Stack
- For new stack you can run destroy operation for stack detail page of new stack in oci console.
- For remaining resources came via parent/source stack, you will need to find and delete those manually.
Digital Media Transcoder for Oracle WebCenter Content
Digital Media Transcoder Overview
The Digital Media Transcoder component in WCC provides advanced video transcoding capabilities. Its core functionality is to process video files, creating multiple renditions of MP4 format, optimized for various screen sizes, while also generating thumbnails for video previews. Digital Media Transcoder efficiently transcodes video files into multiple renditions, ensuring compatibility and performance across devices.
Installation
The Digital Media Transcoder is included in a WebCenter Content component named DigitalMediaTranscoder. This component is disabled by default in WebCenter Content on Marketplace, but an administrator can enable or disable it using the Component Manager tool found under AdminServer. To verify that the DigitalMediaTranscoder is properly installed, open the Component Manager and ensure that DigitalMediaTranscoder is enabled.
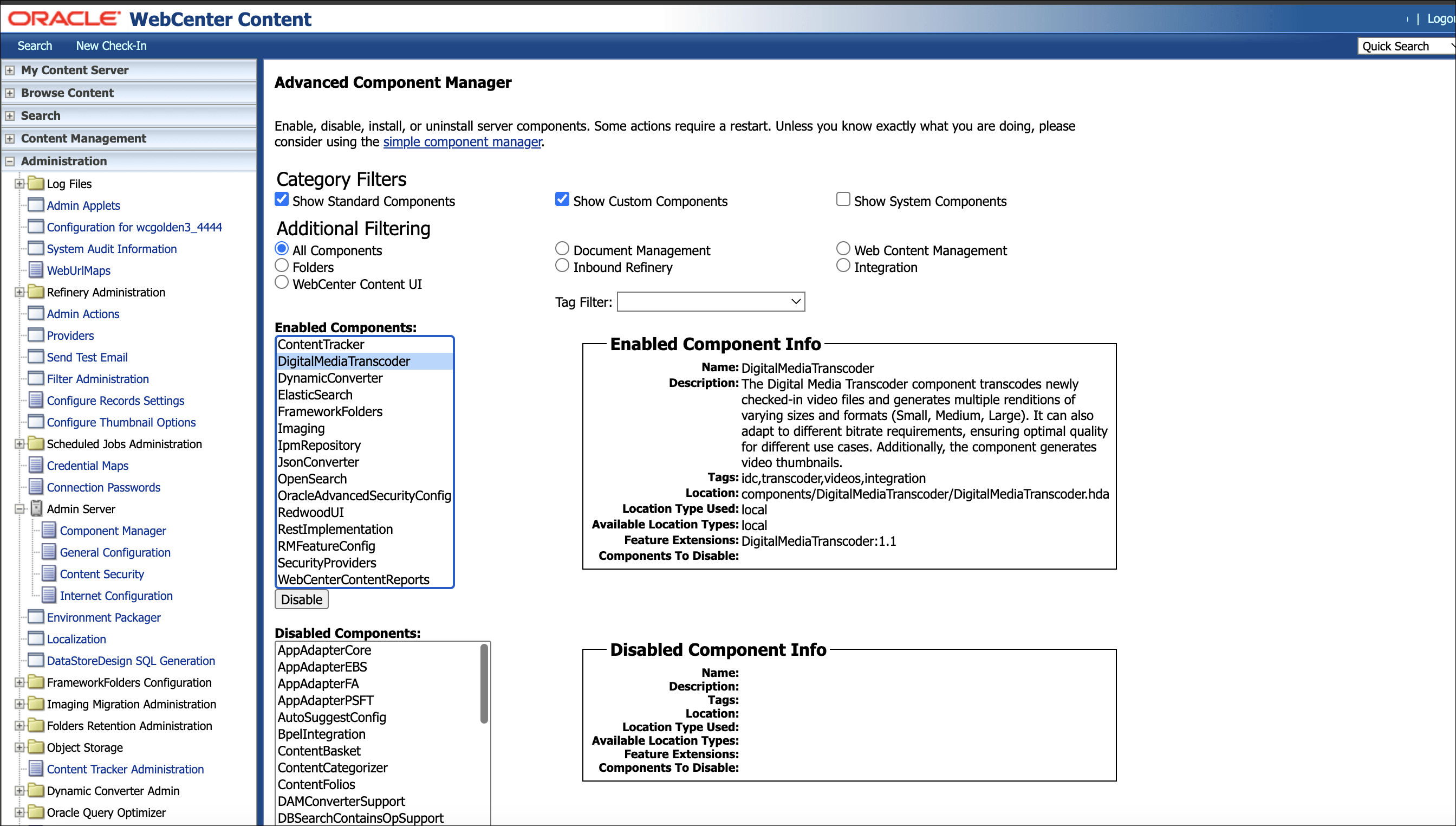
Install Transcoder service
On WebCenter Content Marketplace environment created on version earlier than 25.4.1, it’s required to execute the following script in all WebCenter Content compute instances (ending with -wls-*).
-
Login to compute instance as opc user and execute the script.
cd /u01/scripts/lcm/sh sh configure_wcc_dm_transcoder.sh -
Repeat the step on all WebCenter Content compute instances.
Video Check-In and Supported Formats
Once enabled, all newly checked-in video files will automatically be processed through the DigitalMediaTranscoder. Transcodings will be performed from the source format to MP4, ensuring compatibility across various devices. Multiple renditions and video thumbnails will also be generated during this process.
mp4,mov,mkv,m4v,flv,avi,3gp,webm,mpg,mpeg,3g2,wmv,asf,swf,vob,divx,ogv,mxf
Only video files in these supported formats will be processed in the background by the DigitalMediaTranscoder.
Get Content Info
After the video is processed by DigitalMediaTranscoder, the three MP4 renditions (small, medium, and large) will be available as attachments on the Content Information page.
Renditions:
- Small: 480p
- Medium: 720p
- Large: 1080p
Steps to Generate Video Renditions
Checkin Video File
Select the video file you want to transcode. Add a title and press the Check-In button.
A corresponding entry for the checked-in video file is created in the table for the background job to process.
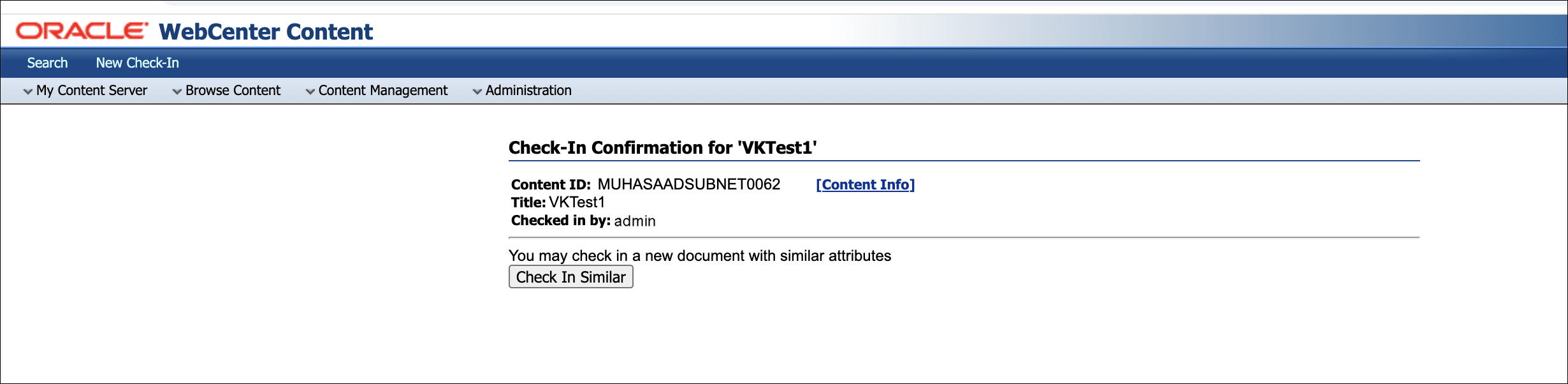
Background Processing
Thumbnail
A video thumbnail is also generated during transcoding and can be viewed when searching for the file within WCC.
Transcoded Renditions
The DigitalMediaTranscoder will generate the following renditions:
- Small Rendition: 480p
- Medium Rendition: 720p
- Large Rendition: 1080p
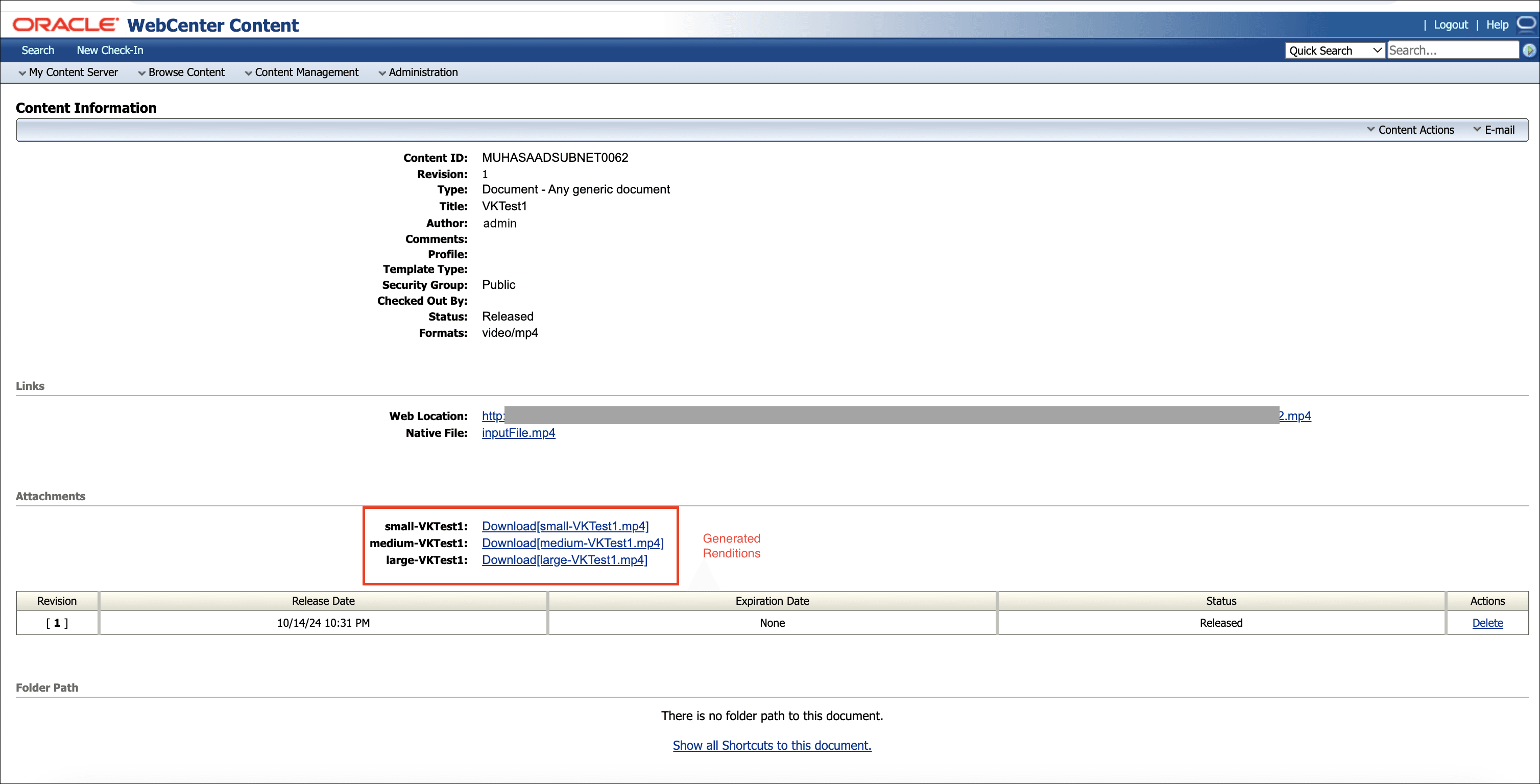
Existing Stack Configure for all external https traffic via 443 load balancer port
This section covers procedure steps to be followed to configure all external https traffic via 443 load balancer port for WebCenter Content installations done using OCI Marketplace.
Prerequisites
Log in to your OCI console account and add below statement in root compartment level policy created for your stack.(Update for dynamic group name and compartment ids before adding)
Allow dynamic-group <stack-prefix>-<region>-webcenter-principal-group to manage network-security-groups in compartment id <network-compartment-ocid>
Note: Network compartment ocid is ocid of compartment where network security group of wcc load balancer is created.
Steps for Configuration
- Connect to WebCenter Compute Instance.
-
Change to 'Oracle' user.
[opc@**-wls-1 ~]$ sudo su - oracle -
Change the directory to '/u01/scripts/lcm/sh'
cd /u01/scripts/lcm/sh -
To configure all external https traffic via 443 port , run the below command.
sh configure_all_traffic_443.sh
Configure TLSv1.3 ciphers for load balancer listeners for WebCenter
This section covers procedure steps to be followed to configure TLSv1.3 ciphers for load balancer listeners in WebCenter marketplace environments.
Steps
- Connect to WebCenter compute instance ending with ‘wls-1’ using Connect to WebCenter Compute Instance.
-
Switch to 'oracle' user.
sudo su - oracle -
Execute
configure_tls13_lb_ciphers.shscript to configure TLSv1.3 ciphers for load balancer listener.cd /u01/scripts/lcm/sh ; sh configure_tls13_lb_ciphers.sh
ClamAV AntiVirus Service for WebCenter Content
This section covers procedure steps to be followed to manage the ClamAV AntiVirus Service for WebCenter Content.
Prerequisites
Provision a stack with the latest version of WebCenter Content (25.4.1 or higher). Provisioning will setup the ClamAV service, along with the required scripts and dependencies.
Connecting to WebCenter Compute Instance and SSH Private Key Set up
-
Connect to the bastion instance as the opc user. Users using a private service can skip this as we do not provision bastion for a private service.
ssh -i path_to_private_key opc@bastion_public_ip -
Connect to any of the weblogic server compute instance.
ssh -i path_to_private_key opc@compute_wls_private_ip -
Change to 'oracle' user.
sudo su - oracle -
Create a file containing opc user’s ssh private key (say - /tmp/opc_key.ssh). It will be the same key used in Step 1 and 2.
-
If your opc user’s ssh private key has a passphrase, then create a file containing opc user’s ssh private key passphrase (say - /tmp/opc_passphrase).
Note: Please make sure the ssh private key and passphrase files are owned by oracle user on the weblogic server compute instance.
Enabling and Starting ClamAV AntiVirus Service
-
Connect to WebCenter Compute Instance and set up ssh private key by following steps as given in Connecting to WebCenter Compute Instance and SSH Private Key Set up
-
To enable and start ClamAV Service on all the compute instances, execute the following commands as 'oracle' user:
cd /u01/scripts/lcm/sh sh clamav_manager.sh -o start \ -k <opc_private_ssh_key_path> \ -p <opc_private_ssh_key_passphrase_file_path> Note: Option -p is optional, when the ssh key does not have a passphrase Examples: Command to execute when the ssh key does not have a passphrase: sh clamav_manager.sh -o start -k /tmp/opc_key.ssh Command to execute when the ssh key has a passphrase: sh clamav_manager.sh -o start -k /tmp/opc_key.ssh -p /tmp/opc_passphrase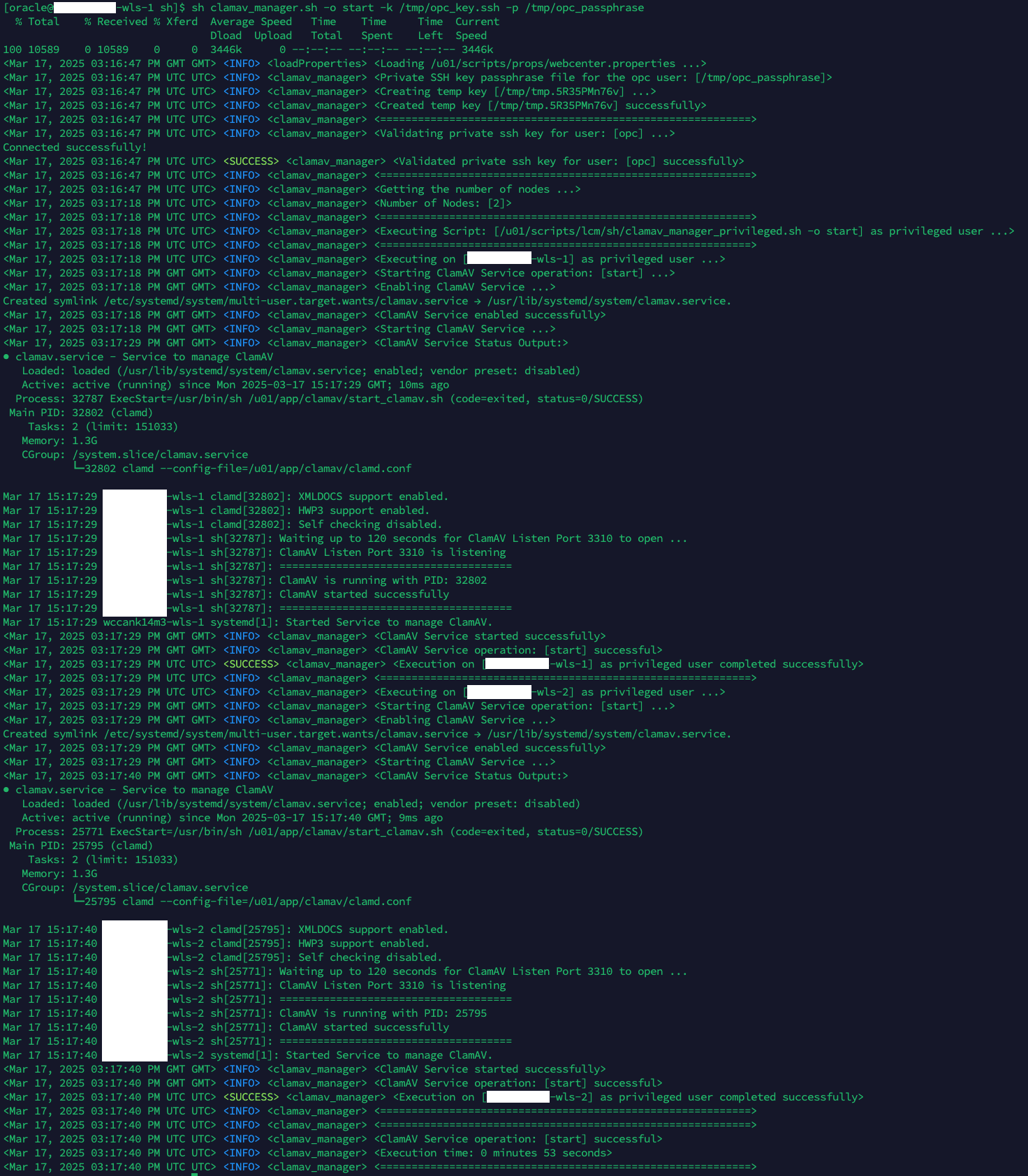
If the service fails to start, refer to Troubleshooting section
Note: Once the service has been enabled, compute reboot will automatically start the ClamAV service.
ClamAV AntiVirus Service Database Update
ClamAV comes with FreshClam, a tool which checks for new database releases and keeps your database up to date.
FreshClam will connect to ClamAV’s virus signature database distribution network (http://database.clamav.net) to download and update the existing databases, pairing them against downloaded CVDs.
Note: FreshClam will work only for stacks with internet connectivity.
-
Connect to WebCenter Compute Instance by following steps 1-3 as given in Connecting to WebCenter Compute Instance
-
To download and update the existing databases on all the compute instances, execute the following commands as 'oracle' user:
cd /u01/scripts/lcm/sh sh clamav_manager.sh -o freshclam_db_update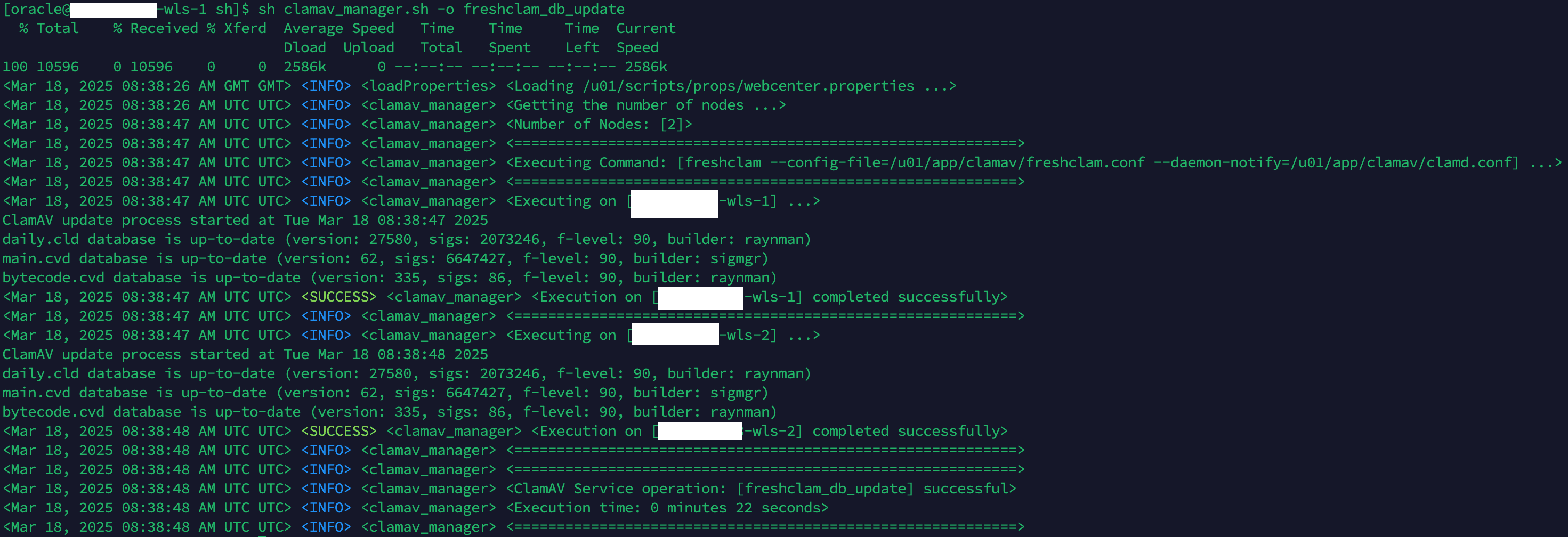
ClamAV AntiVirus Service Troubleshooting
-
ClamAV startup operation will display the error output, which fetches the realtime errors from
/var/log/messages. -
If ClamAV service execution output is not clear about the error, check
/var/log/messageson the compute instance where the failure has happened to check the errors causing the service failure.a. Connect to the bastion instance as the opc user. Users using a private service can skip this as we do not provision bastion for a private service.
ssh -i path_to_private_key opc@bastion_public_ipb. Connect to any of the weblogic server compute instance.
ssh -i path_to_private_key opc@compute_wls_private_ipc. Change to 'root' user:
sudo sud. Check errors in the log file:
/var/log/messages -
If the errors seen indicate permission issues related to SELinux, then follow the below mentioned steps to fix up SELinux permissions, on the compute instance where the failure has happened.
a. Connect to the bastion instance as the opc user. Users using a private service can skip this as we do not provision bastion for a private service.
ssh -i path_to_private_key opc@bastion_public_ipb. Connect to any of the weblogic server compute instance.
ssh -i path_to_private_key opc@compute_wls_private_ipc. Change to 'root' user:
sudo sud. Run the following commands:
semanage fcontext -a -t default_t "/u01/app" semanage fcontext -a -t default_t "/u01/app/clamav" semanage fcontext -a -t antivirus_conf_t "/u01/app/clamav/clamd.conf" semanage fcontext -a -t antivirus_log_t "/u01/data/domains/logs/clamav(/.*)?" semanage fcontext -a -t antivirus_db_t "/u01/app/clamav/lib(/.*)?"e. Change to 'oracle' user:
sudo su - oraclef. Run the following commands:
chcon -t default_t /u01/app chcon -t default_t /u01/app/clamav chcon -R -t antivirus_conf_t /u01/app/clamav/clamd.conf chcon -R -t antivirus_log_t /u01/data/domains/logs/clamav chcon -R -t antivirus_db_t /u01/app/clamav/libg. Check status for
clamav.serviceservice. The service should become active and running. -
If the errors seen indicate missing database files:
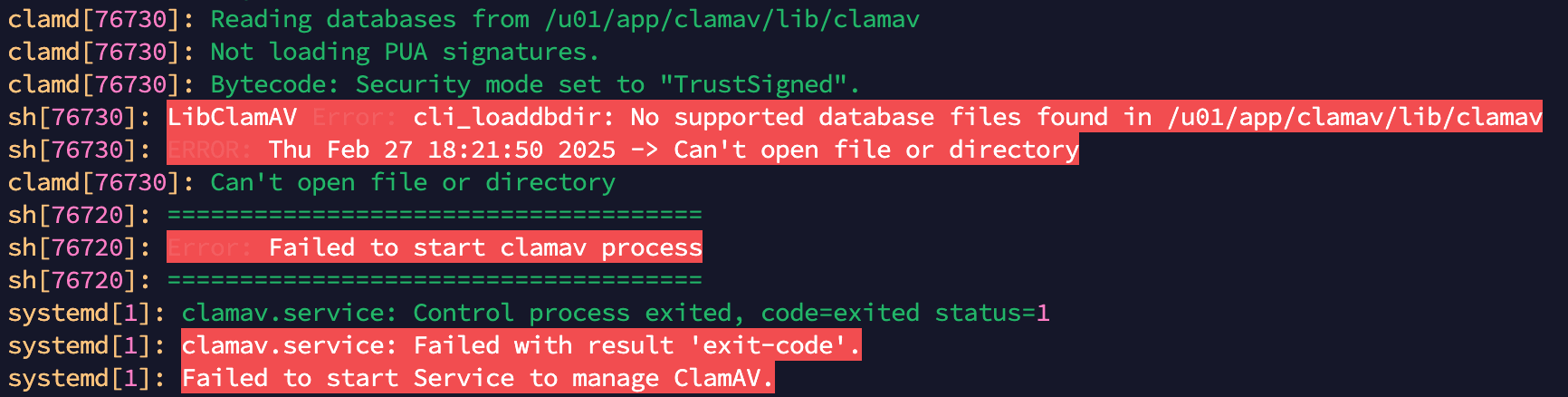
a. To fix the issue, follow ClamAV AntiVirus Service Database Update to update ClamAV database.
b. Check status for
clamav.serviceservice. The service should become active and running.
ClamAV AntiVirus Service Appendix
Enabling ClamAV AntiVirus Service
-
Connect to WebCenter Compute Instance and set up ssh private key by following steps as given in Connecting to WebCenter Compute Instance and SSH Private Key Set up
-
To enable ClamAV Service on all the compute instances, execute the following commands as 'oracle' user:
cd /u01/scripts/lcm/sh sh clamav_manager.sh -o enable \ -k <opc_private_ssh_key_path> \ -p <opc_private_ssh_key_passphrase_file_path> Note: Option -p is optional, when the ssh key does not have a passphrase Examples: Command to execute when the ssh key does not have a passphrase: sh clamav_manager.sh -o enable -k /tmp/opc_key.ssh Command to execute when the ssh key has a passphrase: sh clamav_manager.sh -o enable -k /tmp/opc_key.ssh -p /tmp/opc_passphraseNote: Once the service has been enabled, compute reboot will automatically start the ClamAV service.
Stopping ClamAV AntiVirus Service
-
Connect to WebCenter Compute Instance and set up ssh private key by following steps as given in Connecting to WebCenter Compute Instance and SSH Private Key Set up
-
To stop ClamAV Service on all the compute instances, execute the following commands as 'oracle' user:
cd /u01/scripts/lcm/sh sh clamav_manager.sh -o stop \ -k <opc_private_ssh_key_path> \ -p <opc_private_ssh_key_passphrase_file_path> Note: Option -p is optional, when the ssh key does not have a passphrase Examples: Command to execute when the ssh key does not have a passphrase: sh clamav_manager.sh -o stop -k /tmp/opc_key.ssh Command to execute when the ssh key has a passphrase: sh clamav_manager.sh -o stop -k /tmp/opc_key.ssh -p /tmp/opc_passphrase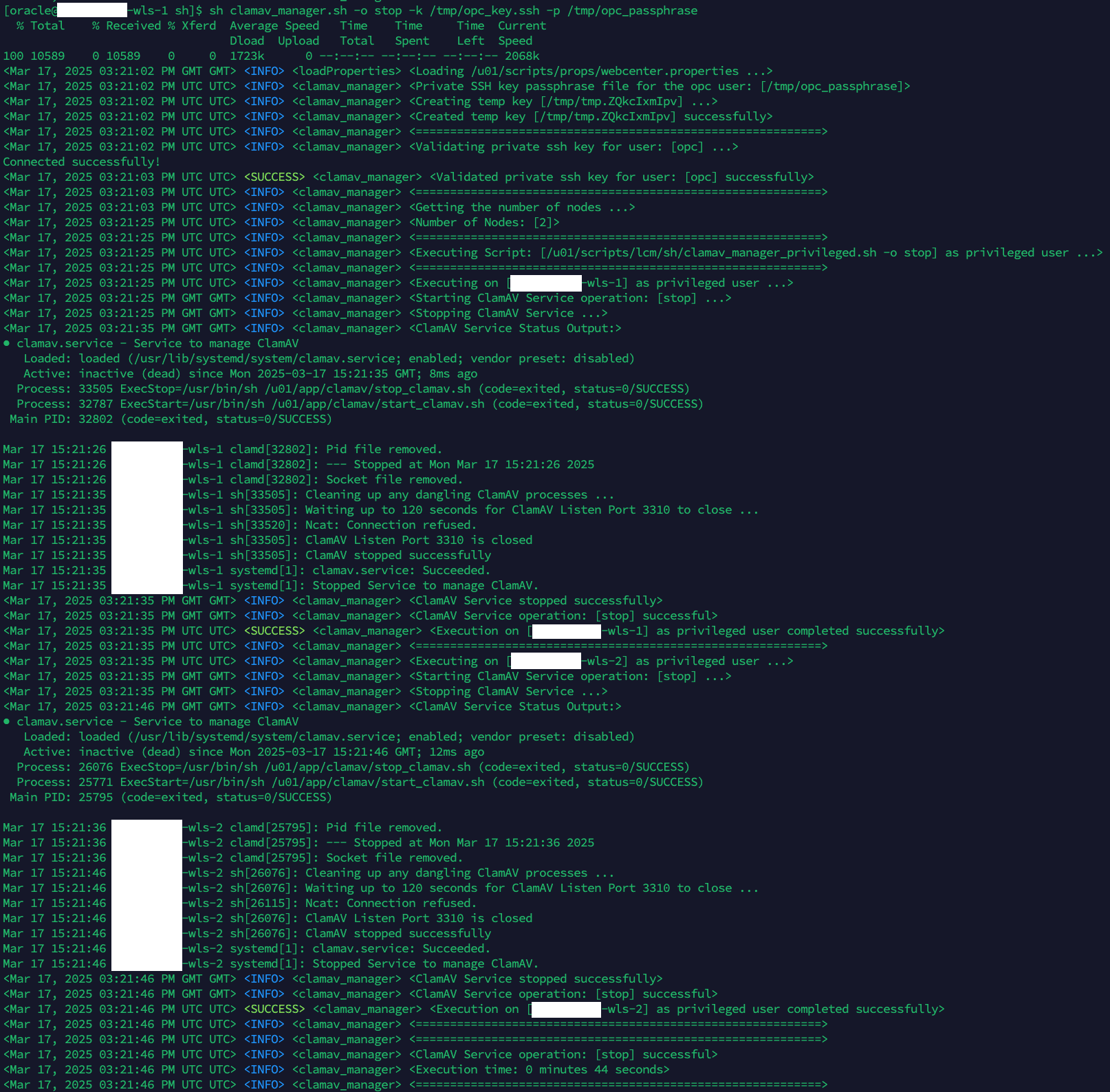
Disabling ClamAV AntiVirus Service
-
Connect to WebCenter Compute Instance and set up ssh private key by following steps as given in Connecting to WebCenter Compute Instance and SSH Private Key Set up
-
To disable ClamAV Service on all the compute instances, execute the following commands as 'oracle' user:
cd /u01/scripts/lcm/sh sh clamav_manager.sh -o disable \ -k <opc_private_ssh_key_path> \ -p <opc_private_ssh_key_passphrase_file_path> Note: Option -p is optional, when the ssh key does not have a passphrase Examples: Command to execute when the ssh key does not have a passphrase: sh clamav_manager.sh -o disable -k /tmp/opc_key.ssh Command to execute when the ssh key has a passphrase: sh clamav_manager.sh -o disable -k /tmp/opc_key.ssh -p /tmp/opc_passphraseNote: Disabling the service, will stop it as well. Also, once the service has been disabled, compute reboot will not automatically start the ClamAV service.
How to update an existing WebCenter Marketplace Content stack to use a new base db
This section covers procedure steps for updating an existing WebCenter Content stack to use a new basedb database.
Prerequisites
- Please ensure that the new database has been sync with the old database.
- You should make note of below information that will be used going forth from the above steps.
| Information | Option | Note |
|---|---|---|
| Database compartment name | --compartment-name |
The compartment name where the database exists. Please ensure that its the same comparment where the stack has been created. |
| Database system name | --db-system-name |
The database system that must be used going forth for Webcenter stack |
| Pluggable database name | --plugging-db-name |
The pluggable database name to be used going forth for Webcenter stack |
| SYS admin password | --read-sys-pw-stdin |
The sys admin password |
| Vault compartment. | --vault-compartment |
The compartment that has vault containing sys password secret. |
| Vault name | --vault |
The vault that has sys password secret. |
| Secret | --secret |
The secret that hosts sys password, this will be updated if the password is changed. |
You will need to execute the following script to upload stack metadata as a secret in vault for license change type of provisioning.
- SSH to WebCenter admin (wls-1) instance as opc user.
- Switch to oracle user.
sudo su - oracle - Update the scripts to the latest version using Update the Current Node with Scripts from the Latest Release Version.
-
Navigate to the scripts directory.
cd /u01/scripts/lcm/sh -
Run the following script to upload stack metadata as a secret in vault.
sh db_manager.sh -h
Command line
[oracle@dev-wls-1 sh]$ sh db_manager.sh -h
usage: db_manager.sh [-h] [--debug-level DEBUG_LEVEL] [--ignore-error]
{HEALTHCHECK,UPDATE-BASEDB,UPDATE-ATP,UPDATE-EXADB} ...
Toolkit to manage db for WebCenter marketplace installation.
options:
-h, --help show this help message and exit
--debug-level DEBUG_LEVEL
Specify logging level. (default: INFO)
--ignore-error Ignore error that may occur. (default: False)
subcommands:
Specify either of list or reset operation.
{HEALTHCHECK,UPDATE-BASEDB,UPDATE-ATP,UPDATE-EXADB}
Please select options
HEALTHCHECK Perform Healthcheck.
UPDATE-BASEDB Update Current DB connection to another Base DB.
UPDATE-ATP Update Current DB connection to another ADB.
UPDATE-EXADB Update Current DB connection to another EXADB.
[oracle@dev-wls-1 sh]$ sh db_manager.sh UPDATE-BASEDB -h
usage: db_manager.sh UPDATE-BASEDB [-h] [--disable-healthcheck]
--compartment-name COMPARTMENT_NAME
[--read-sys-pw-stdin] --vault-compartment
VAULT_COMPARTMENT --vault VAULT --secret
SECRET [--no-wls-bounce] --db-system-name
DB_SYSTEM_NAME --pluggable-db-name
PLUGGABLE_DB_NAME
options:
-h, --help show this help message and exit
--disable-healthcheck
Disable healthcheck. (default: False)
--compartment-name COMPARTMENT_NAME
Please specify DB Comparment name.
--read-sys-pw-stdin Read sys password from stdin. (default: False)
--vault-compartment VAULT_COMPARTMENT
Specify vault compartment to be used.
--vault VAULT Specify vault to be used.
--secret SECRET Specify secret to be used for sys/admin password.
--no-wls-bounce Do not restart WLS Servers.
--db-system-name DB_SYSTEM_NAME
Please specify DB Name.
--pluggable-db-name PLUGGABLE_DB_NAME
Please specify Pluggin DB Name.
Example
For example for an environment as below:
| Information | Option | Value |
|---|---|---|
| Database compartment name | --compartment-name |
devcomp |
| Database system name | --db-system-name |
basedb |
| Pluggable database name | --plugging-db-name |
plgdb |
| SYS admin password | --read-sys-pw-stdin |
dummyPass#123 |
| Specify vault compartment where the db vault is stored. | --vault-compartment |
devcomp |
| Specify vault where the db password secret is stored. | --vault |
db-vault |
| Secret where the admin password will be stored if changed | --secret |
db-password |
The command would be:
[oracle@dev-wls-1 sh]$ echo 'dummyPass#123' | sh db_manager.sh --debug-level DEBUG UPDATE-BASEDB --compartment-name devcomp --db-system-name basedb --pluggable-db-name plgdb --read-sys-pw-stdin --vault-compartment devcomp --vault db-vault --secret db-password
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 10886 0 10886 0 0 1771k 0 --:--:-- --:--:-- --:--:-- 1771k
<Feb 26, 2025 08:49:58 AM GMT> <INFO> <loadProperties> <Loading /u01/scripts/props/webcenter.properties ...>
<Feb 26, 2025 08:50:00 AM GMT> <INFO> <databag> <(host:dev-wls-1) - Getting host fqdn using socket call... >
<Feb 26, 2025 08:50:00 AM GMT> <INFO> <db_manager> <(host:dev-wls-1) - Getting number of total nodes ...>
<Feb 26, 2025 08:50:18 AM GMT> <INFO> <db_manager> <(host:dev-wls-1) - Node Count: 2>
...
...
<Feb 26, 2025 08:57:02 AM GMT> <INFO> <db_manager> <(host:dev-wls-1) - Starting Webcenter Vault operations...>
<Feb 26, 2025 08:57:03 AM GMT> <INFO> <db_manager> <(host:dev-wls-1) - Provided password is same as existing password, skipping updating vault.>
<Feb 26, 2025 08:57:03 AM GMT> <INFO> <db_manager> <(host:dev-wls-1) - Completed Webcenter Vault operations.>
<Feb 26, 2025 08:57:03 AM GMT> <INFO> <db_manager> <(host:dev-wls-1) - Completed operation: [UPDATE-BASEDB] with RC Code 0. Time taken: 7m 2s>
Success scenario
The operation can be considered if the RC Code as mentioned above is 0. Else a suitable error message would be printed.
Failure scneario
In case the datasource reconfiguration fails, please execute the same command, but instead provide the original/source database details.
Automation to unmount and mount FSS with in transit TLS encryption
This section covers procedure steps to be followed to unmount the ucm mount path from the existing filesystem and mount it again with TLS encryption in place for WebCenter Content.
Prerequisites
For an existing or new WebCenter Content stack, you will need 2 policies to support addition of ingress rule for allowing traffic on 2051 port.
Allow dynamic-group <stack-prefix>-<region>-webcenter-principal-group to read mount-targets in tenancy
Allow dynamic-group <stack-prefix>-<region>-webcenter-principal-group to manage network-security-groups in compartment id <network compartment ocid>
Steps for mounting FSS with in transit TLS encryption
For each webcenter compute instance, execute the following steps:
- Connect to WebCenter Compute Instance.
-
Navigate to the scripts directory.
cd /u01/scripts/lcm/sh -
Execute the automation script to mount fss via tls encryption
[opc@**-wls-1 sh]$ sudo sh fss_tcp_mount.sh -p /u01/shared/ucm/cs - After script execution check updated filesystem and entry in fstab table
[opc@**-wls-1 sh]$ df -hP Filesystem Size Used Avail Use% Mounted on /dev/sdb 50G 3.0G 47G 6% /u01/data/domains/wcc_domain /dev/sdc 50G 14G 37G 28% /u01/app [fd40:2c3:7e58:554c::a4]:/stack/stack-27386159/config 8.0E 17G 8.0E 1% /u01/shared/ucm/cs [opc@**-wls-1 sh]$ cat /etc/fstab # /etc/fstab # Created by anaconda on Sat Jan 13 22:30:23 2024 # # Accessible filesystems, by reference, are maintained under '/dev/disk/'. ## ## Example: <mount_ip>:/stack/stack-27386159/config /u01/shared/ucm/cs oci-fss x-systemd.requires=oci-fss-init.service,defaults,nofail 0 0
Rollback
To rollback the changes persisted by the automation script, you can execute unmount script in the same directory.
-
Navigate to the scripts directory.
cd /u01/scripts/lcm/sh -
Execute the automation script to unmount fss via tls encryption
sudo sh fss_tcp_unmount.sh -p /u01/shared/ucm/cs -
After script execution the filesystem and fstab table will go back to original state
[opc@**-wls-1 sh]$ df -hP Filesystem Size Used Avail Use% Mounted on /dev/sdb 50G 3.0G 47G 6% /u01/data/domains/wcc_domain /dev/sdc 50G 14G 37G 28% /u01/app <mount_ip>:/stack/stack-27386159/config 8.0E 17G 8.0E 1% /u01/shared/ucm/cs [opc@**-wls-1 sh]$ cat /etc/fstab # /etc/fstab # Created by anaconda on Sat Jan 13 22:30:23 2024 <mount_ip>:/stack/stack-27386159/config /u01/shared/ucm/cs nfs auto,defaults,nofail 0 0
How to update an existing WebCenter Marketplace Content stack using basedb to switch over to ATP
This section covers procedure steps for updating an existing WebCenter Content stack to switch from a basedb database.
Prerequisites
- Please ensure that following policy has been added at
Identity & Security->Policies-><service name>-<region name>-oci-policy->Statements:Allow dynamic-group <service name>-<region name>-webcenter-principal-group to read autonomous-database-family in compartment id <compartment_id>In above, the
compartment idis theOCIDof the compartment that hosts the ATP database. - Please ensure that the new database has been sync with the old database.
- You should make note of below information that will be used going forth from the above steps.
| Information | Option | Note |
|---|---|---|
| Autonomous Database compartment name | --compartment-name |
The compartment name where the database exists. Please ensure that its the same comparment where the stack has been created. |
| Autonomous Database system name | --adb-name |
The Autonomous database system that must be used going forth for Webcenter stack. |
| Vault compartment name | --vault-compartment |
The vault compartment name to be used for storing autonomous database password. |
| Vault name | --vault |
The name of the vault that holds the secret. |
| Autonomous Database Admin Password Secret name | --secret Specify the secret that would store the admin password. |
You will need to execute the following script to upload stack metadata as a secret in vault for license change type of provisioning.
- SSH to WebCenter admin (wls-1) instance as opc user.
- Switch to oracle user.
sudo su - oracle - Update the scripts to the latest version using Update the Current Node with Scripts from the Latest Release Version.
-
Navigate to the scripts directory.
cd /u01/scripts/lcm/sh -
Run the following steps.
sh db_manager.sh -h
Command line
usage: db_manager.sh [-h] [--debug-level DEBUG_LEVEL] [--ignore-error]
{HEALTHCHECK,UPDATE-BASEDB,UPDATE-ATP,UPDATE-EXADB} ...
Toolkit to manage db for WebCenter marketplace installation.
options:
-h, --help show this help message and exit
--debug-level DEBUG_LEVEL
Specify logging level. (default: INFO)
--ignore-error Ignore error that may occur. (default: False)
subcommands:
Specify either of list or reset operation.
{HEALTHCHECK,UPDATE-BASEDB,UPDATE-ATP,UPDATE-EXADB}
Please select options
HEALTHCHECK Perform Healthcheck.
UPDATE-BASEDB Update Current DB connection to another Base DB.
UPDATE-ATP Update Current DB connection to another ADB.
UPDATE-EXADB Update Current DB connection to another EXADB.
[oracle@dev-wls-1 sh]$ sh db_manager.sh UPDATE-ATP -h
usage: db_manager.sh UPDATE-ATP [-h] [--disable-healthcheck]
--compartment-name COMPARTMENT_NAME
[--read-sys-pw-stdin] --vault-compartment
VAULT_COMPARTMENT --vault VAULT --secret
SECRET [--no-wls-bounce] --adb-name ADB_NAME
options:
-h, --help show this help message and exit
--disable-healthcheck
Disable healthcheck. (default: False)
--compartment-name COMPARTMENT_NAME
Please specify DB Comparment name.
--read-sys-pw-stdin Read sys password from stdin. (default: False)
--vault-compartment VAULT_COMPARTMENT
Specify vault compartment to be used.
--vault VAULT Specify vault to be used.
--secret SECRET Specify secret to be used for sys/admin password.
--no-wls-bounce Do not restart WLS Servers.
--adb-name ADB_NAME Please specify ADB Name.
Example
For example for an environment as below:
| Information | Option | Value |
|---|---|---|
| Autonomous Database compartment name | --compartment-name |
devcomp |
| Autonomous Database system name | --adb-name |
devadb |
| Vault compartment name | --vault-compartment |
devcomp |
| Vault name | --vault |
devvault |
| Autonomous Database Admin Password Secret name | --secret |
ATP_DB_PASSWD |
The command would be:
[oracle@dev-wls-1 sh]$ echo 'dummyPass#123' | sh db_manager.sh UPDATE-ATP --compartment-name devcomp --adb-name devadb --vault-compartment devcomp --vault devvault --secret ATP_DB_PASSWD --read-sys-pw-stdin
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 10886 0 10886 0 0 1771k 0 --:--:-- --:--:-- --:--:-- 1771k
<Mar 22, 2025 08:49:58 AM GMT> <INFO> <loadProperties> <Loading /u01/scripts/props/webcenter.properties ...>
<Mar 22, 2025 08:50:00 AM GMT> <INFO> <databag> <(host:dev-wls-1) - Getting host fqdn using socket call... >
<Mar 22, 2025 08:50:00 AM GMT> <INFO> <db_manager> <(host:dev-wls-1) - Getting number of total nodes ...>
<Mar 22, 2025 08:50:18 AM GMT> <INFO> <db_manager> <(host:dev-wls-1) - Node Count: 2>
...
...
<Mar 22, 2025 08:57:02 AM GMT> <INFO> <db_manager> <(host:dev-wls-1) - Starting Webcenter Vault operations...>
<Mar 22, 2025 08:57:03 AM GMT> <INFO> <db_manager> <(host:dev-wls-1) - Provided password is same as existing password, skipping updating vault.>
<Mar 22, 2025 08:57:03 AM GMT> <INFO> <db_manager> <(host:dev-wls-1) - Completed Webcenter Vault operations.>
<Mar 22, 2025 08:57:03 AM GMT> <INFO> <db_manager> <(host:dev-wls-1) - Completed operation: [UPDATE-BASEDB] with RC Code 0. Time taken: 7m 2s>
Success scenario
The operation can be considered if the RC Code as mentioned above is 0. Else a suitable error message would be printed.
Failure scneario
In case the datasource reconfiguration fails, please execute the same command, but instead provide the original/source database details.
SSH Keys Rotation
You can rotate SSH keys for the webcenter compute instances.
SSH Keys Rotation for opc user
Note: Users using a private service can skip Step 2-3, as we do not provision bastion for a private service.
-
Generate a new SSH Key pair by following steps as given in Generate SSH Key pair
-
Connect to the bastion instance as the opc user with the current private key.
ssh -i path_to_current_private_key opc@bastion_public_ip -
For bastion instance, execute the following steps, all the following steps will be executed as 'opc' user:
a. (Optional) Create backup of
/home/opc/.ssh/authorized_keys:cp -f /home/opc/.ssh/authorized_keys /home/opc/.ssh/authorized_keys.backupb. Inside
/home/opc/.ssh/authorized_keys, replace the current public ssh key with the public ssh key generated in Step 1.Note: The file contains two public ssh keys, replace only the public ssh key provided during stack creation. Please do not update the other public ssh key.
-
For each webcenter compute instance, execute the following steps:
a. Connect to the compute instance (hostname ending with pattern 'wls-*'). All the following steps will be executed as 'opc' user.
ssh -i path_to_current_private_key opc@compute_wls_private_ipb. (Optional) Create backup of
/home/opc/.ssh/authorized_keys:cp -f /home/opc/.ssh/authorized_keys /home/opc/.ssh/authorized_keys_backupc. Inside
/home/opc/.ssh/authorized_keys, replace the current public ssh key with the generated public ssh key in Step 1.Note: The file contains two public ssh keys, replace only the public ssh key provided during stack creation. Please do not update the other public ssh key.
-
Validate SSH login is working with the new private ssh key.
SSH Keys Rotation for oracle user
-
Generate a new SSH Key pair by following steps as given in Generate SSH Key pair
-
Connect to the bastion instance as the opc user with the current private key. Users using a private service can skip this, as we do not provision bastion for a private service.
ssh -i path_to_current_private_key opc@bastion_public_ip -
For each webcenter compute instance, execute the following steps:
a. Connect to the compute instance (hostname ending with pattern 'wls-*').
ssh -i path_to_current_private_key opc@compute_wls_private_ipb. Permit write permission to the 'oracle' user’s private key file:
sudo chmod 600 /home/oracle/.ssh/id_rsac. Switch to 'oracle' user:
sudo su - oracled. (Optional) Create backup of
/home/oracle/.ssh:cp -rf /home/oracle/.ssh /home/oracle/.ssh_backupe. Inside
/home/oracle/.ssh/id_rsa, replace the current private ssh key with the private ssh key generated in Step 1.f. Inside
/home/oracle/.ssh/authorized_keys, replace the current public ssh key with the public ssh key generated in Step 1.g. Permit only read permission for the 'oracle' user’s private key file:
chmod 400 /home/oracle/.ssh/id_rsa -
Validate ssh login for 'oracle' user is working across compute instances.
a. Connect to any of the compute instance (hostname ending with pattern 'wls-*').
ssh -i path_to_private_key opc@compute_wls_private_ipb. Switch to 'oracle' user:
sudo su - oraclec. SSH to any of the other compute instances and login should work without any issues.
[oracle@*-wls-1 ~]$ ssh oracle@*-wls-2
WebCenter WebLogic Server Lifecycle Operations
This section describes managing the lifecycle of WebLogic Servers for the WebCenter Stack.
Prerequisites
You’ll need to complete either of the following prerequisites to setup the required scripts.
-
Provision a stack with the latest version of WebCenter stack (25.5.1 or higher).
-
For an existing WebCenter stack, you will need to patch the WebCenter environment to the latest version (25.5.1 or higher) using the Patch Tool. See About the Patch Tool.
How to manage WebLogic Servers
CLI Script Usage
Usage: sh webcenter_server_manager.sh -a <action> -s <all | comma_separated_server_prefix_indexed-vm_list>
Parameters:
-a (required) action to perform
Valid values: start, shutdown, force_shutdown, status, restart, rolling_restart
-s (required) all or
comma separated list of server(s) or prefix(s) or indexed VM(s) to perform the action on
Quote the value provided if the list supplied has spaces
Valid values: all: All Servers
vm1, vm2, vm3 and so on: All Servers on provided indexed VMs in the format - vm<host_index>
AdminServer: Admin Server
UCM_server, capture_server, IPM_server, IBR_server, WCCADF_server: Prefixes for WCC
WC_Portal_server, WC_Portlet_server: Prefixes for WCP
wcsites_server: Prefix for WCS
satellite_server: Prefix for WCSSAT
UCM_server1, capture_server4, WC_Portal_server1, wcsites_server2, satellite_server1 and so on: Specific Individual Servers
-h To print Usage of this script
Note:
-----
1. When 'all' is specified, action will be performed on all the servers across all VMs.
Any other specified value will be ignored.
'all' will always have the highest precedence.
2. When indexed VM(s) are specified, action will be performed on all the servers across
the specified VMs.
3. When prefixes are specified, action will be performed on all the servers of that type
across all VMs.
4. For rolling_restart, action will be performed on all the servers across all VMs in a
rolling manner.
Within each rolling batch, action on all the servers on a VM will happen in parallel.
5. For start, restart and rolling_restart - action on Admin Server will happen upfront.
For shutdown and force_shutdown, action on Admin Server will happen in the last.
6. All the actions happen via the Admin Server, so the process automatically takes care
of bringing up Admin Server, if its down.
CLI Script Execution and Examples
-
Connect to the bastion instance as the opc user. Users using a private service can skip this as we do not provision bastion for a private service.
ssh -i path_to_private_key opc@bastion_public_ip -
Connect to any of the weblogic server compute instance.
ssh -i path_to_private_key opc@compute_wls_private_ip -
Change to 'oracle' user.
sudo su - oracle -
Navigate to the scripts directory.
cd /u01/scripts/lcm/sh -
Execute the script in the following format:
sh webcenter_server_manager.sh -a <action> -s <all | comma_separated_server_prefix_indexed-vm_list>
Examples:
For all these actions: start, shutdown, force_shutdown, status, restart, rolling_restart
in the examples given, replace the value for the options:
'-a' with the desired action and
'-s' with the desired servers/prefixes/indexed_vms or all
# all the servers along with Admin Server
nohup sh webcenter_server_manager.sh -a <action_name> -s 'all' &> wc_svr_mgr.log &
# all the servers on VMs: 1 and 2
nohup sh webcenter_server_manager.sh -a <action_name> -s 'vm1,vm2' &> wc_svr_mgr.log &
# all the WCC UCM and IPM servers
nohup sh webcenter_server_manager.sh -a <action_name> -s 'UCM_server,IPM_server' &> wc_svr_mgr.log &
# all the WCC UCM and specific capture servers along with Admin Server
nohup sh webcenter_server_manager.sh -a <action_name> -s 'AdminServer,UCM_server,capture_server1,capture_server3' &> wc_svr_mgr.log &
# specific WCC servers
nohup sh webcenter_server_manager.sh -a <action_name> -s 'UCM_server1,capture_server2,capture_server3,IBR_server1,WCCADF_server2' &> wc_svr_mgr.log &
# all the WCP servers
nohup sh webcenter_server_manager.sh -a <action_name> -s 'WC_Portal_server,WC_Portlet_server' &> wc_svr_mgr.log &
# specific WCP servers
nohup sh webcenter_server_manager.sh -a <action_name> -s 'WC_Portal_server1,WC_Portlet_server1' &> wc_svr_mgr.log &
# all the WCS servers
nohup sh webcenter_server_manager.sh -a <action_name> -s 'wcsites_server' &> wc_svr_mgr.log &
# specific WCS servers along with Admin Server
nohup sh webcenter_server_manager.sh -a <action_name> -s 'AdminServer,wcsites_server1,wcsites_server2' &> wc_svr_mgr.log &
# specific WCSSAT servers along with Admin Server
nohup sh webcenter_server_manager.sh -a <action_name> -s 'AdminServer,satellite_server1' &> wc_svr_mgr.log &
How to update an existing WebCenter Marketplace Content stack using basedb to switch over to EXAData database
This section covers steps for switching from a source database to a new target EXAData database.
Prerequisites
- Please ensure that the source database is backed up and recovered on the target EXAData database.
- You should make note of below information that will be needed going forth.
| Information | Option | Note |
|---|---|---|
| EXAData Database compartment name | --compartment-name |
The name of the compartment that has the target EXAData database. |
| EXAData VM Cluster name | --exa-vmcuster-name |
The name of the EXAData VM Cluster thats has target EXAData database system. |
| EXAData Database name | --exa-db-name |
The name of the target EXAData database system. |
| EXAData Pluggable Database name | --exa-pluggable-db-name |
The name of the target EXAData pluggable database. |
| EXAData sys account password | --read-sys-pw-stdin |
The target EXAData pluggable database’s sys account password. This is optional, however, if not provided then you will be prompted for the sys account password during execution. |
| EXAData Database Sys account password secret name | --secret |
The name of secret that has sys account password for the target EXAData pluggable database. Please note this will be updated if the password provided via --read-sys-pw-stdin is different from the current version. |
| Vault name | --vault |
The name of the vault that hosts secret as mentioned via --secret for the target EXAData database. |
| Vault compartment name | --vault-compartment |
The name of the compartment that has vault mentioned by --vault. |
| Disable health check. | --disable-healthcheck |
Disable health check during switch over check. If we wish to force switch over without performing sanity check then provide this option. Please note that this is optional. |
Proceed with following steps:
- SSH to WebCenter admin (wls-1) instance as opc user.
- Switch to oracle user.
sudo su - oracle - Update the scripts to the latest version using Update the Current Node with Scripts from the Latest Release Version.
-
Navigate to the scripts directory.
cd /u01/scripts/lcm/sh - Execute below:
Command line help example
usage: db_manager.sh UPDATE-EXADB [-h] [--disable-healthcheck]
--compartment-name COMPARTMENT_NAME
[--read-sys-pw-stdin] --vault-compartment
VAULT_COMPARTMENT --vault VAULT --secret
SECRET [--no-wls-bounce] --exa-vmcuster-name
EXADB_VMCLUSTER_NAME --exa-db-name
EXADB_DB_NAME --exa-pluggable-db-name
EXA_PLUGGABLE_DB_NAME
options:
-h, --help show this help message and exit
--disable-healthcheck
Disable healthcheck. (default: False)
--compartment-name COMPARTMENT_NAME
Please specify DB Comparment name.
--read-sys-pw-stdin Read sys password from stdin. (default: False)
--vault-compartment VAULT_COMPARTMENT
Specify vault compartment to be used.
--vault VAULT Specify vault to be used.
--secret SECRET Specify secret to be used for sys/admin password.
--no-wls-bounce Do not restart WLS Servers.
--exa-vmcuster-name EXADB_VMCLUSTER_NAME
Please specify EXAData VM Cluster Name.
--exa-db-name EXADB_DB_NAME
Please specify EXAData Database Name.
--exa-pluggable-db-name EXA_PLUGGABLE_DB_NAME
Please specify Pluggin DB Name.
Sample command example
For example for an environment as below:
| Information | Option | Note |
|---|---|---|
| EXAData Database compartment name | --compartment-name |
devcomp |
| EXAData VM Cluster name | --exa-vmcuster-name |
devexavmcluster |
| EXAData Database name | --exa-db-name |
devexadb |
| EXAData Pluggable Database name | --exa-pluggable-db-name |
devexapdb |
| EXAData Database Sys account password secret name | --secret |
exasyspw |
| Vault name | --vault |
devvault |
| Vault compartment name | --vault-compartment |
devcomp |
The command would be:
[oracle@dev-wls-1 sh]$ echo 'dummyPass#123' | sh db_manager.sh UPDATE-EXADB --compartment-name devcomp --exa-vmcuster-name devexavmcluster --exa-db-name devexadb --exa-pluggable-db-name devexapdb --vault-compartment devcomp --vault devvault --secret exasyspw --read-sys-pw-stdin
<Mar 22, 2025 08:49:58 AM GMT> <INFO> <loadProperties> <Loading /u01/scripts/props/webcenter.properties ...>
<Mar 22, 2025 08:50:00 AM GMT> <INFO> <databag> <(host:dev-wls-1) - Getting host fqdn using socket call... >
<Mar 22, 2025 08:50:00 AM GMT> <INFO> <db_manager> <(host:dev-wls-1) - Getting number of total nodes ...>
<Mar 22, 2025 08:50:18 AM GMT> <INFO> <db_manager> <(host:dev-wls-1) - Node Count: 2>
...
...
<Mar 22, 2025 08:57:03 AM GMT> <INFO> <db_manager> <(host:dev-wls-1) - Completed operation: [UPDATE-EXADB] with RC Code 0. Time taken: 7m 2s>
Success scenario
The operation can be considered if the RC Code as mentioned above is 0. Else a suitable error message would be printed.
Failure scneario
In case the datasource reconfiguration fails, please execute the same command, but instead provide the original/source database details.
Appendix
Convert a Passphrase-Based Private Key to Empty Passphrase Private Key
Convert a Passphrase-Based Private Key to Empty Passphrase Private Key on Linux
-
Make a copy of the original SSH key with the desired private key file name.
cp <private-ssh-key-path> <new-private-ssh-key-path>For example :
cp /home/user/.ssh/wcmpstack_id_rsa /home/user/.ssh/wcmpstack_id_rsa_nopass -
Run the below command to update the copied private key file’s passphrase.
ssh-keygen -p -f <new-private-ssh-key-path> Enter old passphrase: ******* Enter new passphrase (empty for no passphrase): <HIT ENTER> Enter same passphrase again: <HIT ENTER> Your identification has been saved with the new passphrase.
Convert a Passphrase-Based Private Key to Empty Passphrase Private Key on Windows
- Find puttygen.exe in the PuTTY folder on your computer and double-click it.
- Click Load and locate your private key with passphrase in ppk or OpenSSH format.
- Enter the passphrase for the key so PuttyKeyGen can load it.
- Remove the contents from the Key passphrase and Confirm fields.
- To save the private key in OpenSSH format, in the Putty Key Generator, click Conversions, and then click Export OpenSSH Key.

- Click Yes to save without a passphrase dialog.

- Save your file with a name such as
<webcenter-marketplace-stack-name>_id_rsaand save as type ‘All Files (*.*)’.
Enable Data Guard for Base Database
Learn how to enable Data Guard on Base Database from your primary to standby region. Ensure all requirements are met in the Base Database documentation before you proceed.
Before enabling Data Guard to your DB System, you will need to create a remote peering connection from your VCN in the primary region to a VCN in the standby region. Then, you will need to configure the DB System’s subnets to allow traffic between the VCNs. See Remote VCN Peering using a Legacy DRG for more information.
Task A: Create VCN in Standby Region
Create a VCN in your standby region. The standby region’s VCN must not have overlapping CIDRs with the VCN of your DB system in the primary region. See Create VCN for detailed steps.
Task B: Create a Dynamic Routing Gateway (DRG) in Primary and Standby Regions
- In your primary region, navigate to Networking, Customer connectivity, and then Dynamic routing gateways.
- Select Create dynamic routing gateway. Enter a name for the DRG and select the compartment of your DB system.
- After DRG is created, navigate to the DRG and create the VCN attachment. Enter a name for the VCN attachment and select the VCN of your DB system.
- Repeat steps 1 to 3 in the standby region to create the DRG in the same compartment.
Task C: Create a Remote Peering Connection (RPC) in Primary and Standby Regions
- Navigate to the Dynamic Routing Gateway created in Task B.
- Under Resources, navigate to Remote peering connection attachments and create the remote peering connection. Enter a name for the RPC and select the compartment of your DB system.
- Repeat steps 1 and 2 in the standby region to create the RPC in the same compartment.
- After creating the RPC in the standby region, select the RPC under the Remote peering connection column and record the OCID.
Task D: Establish the Remote Peering Connection from Primary Region
- In the primary region, navigate to the Dynamic Routing Gateway and select the Remote peering connection attachments under Resources.
- Select the RPC under the Remote peering connection column and select Establish Connection.
- Under Region, select the standby region and enter the OCID of the RPC created in the standby region.
- Establish the connection and confirm Peering status is Peered.
Task E: Configure the Route Table in Primary and Standby Regions
- In the primary region, navigate to Networking, Virtual Cloud Networks, and then select the VCN of your DB system.
- Select the subnet of your DB system.
- Navigate to the subnet route table and add a route rule with the following configuration:
- Target Type: DRG
- Destination: Standby region’s VCN CIDR block
- Target Dynamic Routing Gateway: DRG attached to in primary region’s VCN
- In the standby region, navigate to Networking, Virtual Cloud Networks, and then select the VCN created in Task A. Create or select an existing subnet where the peer DB system will be created.
- Navigate to the subnets route table and add a route rule with the following configuration:
- Target Type: DRG
- Destination: Primary region’s VCN CIDR block
- Target Dynamic Routing Gateway: DRG attached to in standby region’s VCN
Task F: Configure the Security List in Primary and Standby Regions
- In the primary region, navigate to the subnet of your DB system and select its security list.
-
Add a new ingress rule with the following configuration:
- Source Type: CIDR
- Source CIDR: Standby region’s subnet CIDR
- IP Protocol: TCP
- Source Port Range: All
- Destination Port Range: 1521
-
If the security list’s egress rules do not have traffic enabled on all outgoing points (0.0.0.0/0), add the following egress rule:
- Destination Type: CIDR
- Destination CIDR: Standby region’s subnet CIDR
- IP Protocol: TCP
- Source Port Range: All
- Destination Port Range: 1521
- In the standby region, navigate to the subnet where the peer DB system will be created and select its security list.
- Repeat steps 2 and 3 with the Destination CIDR being the primary region’s subnet CIDR.
Task G: Enable Data Guard for Base Database in Primary Region
- Navigate to Oracle Database, Oracle Base Database Service in primary region, and then select your DB System.
- Select the Database to view details and under Resources, select Data Guard Associations.
- Select Enable Data Guard and enter the following configuration:
- Display name: Same display name as your DB system
- Region: Standby region
- AD: Any available AD in the standby region
- License Type: Same license type as your DB system
- VCN: VCN created in Task A
- Client Subnet: Subnet created for peer DB system
- Hostname prefix: Same as display name
- After selecting required from Enable Oracle Data Guard on a DB System and clicking Next, enter the same database password as the current administrator password for your Base Database.
- Enable the Data Guard. The Data Guard will be enabled after the peer DB system is created and updated successfully in your standby region.
Update the Current Node with Scripts from the Latest Release Version
To update the scripts on the current node with latest release version, just run the patch tool with help option (-h) as oracle user as shown below:
# Switch to oracle user if current user is opc
sudo su - oracle
cd /u01/scripts/patch
sh patch_tool.sh -h
Patch Troubleshooting
Object Storage BucketNotFound or Not Authorized
If you see any of the below error messages during apply_patch -
Object storage bucket [***] not found
'message': "Either the bucket named '***' does not exist in the namespace '***' or you are not authorized to access it"
- Check if the storage bucket exists
- Check bucket name
<stackname>-webcenter-bucketexits in stack compartment. List object storage buckets. - If bucket
<stackname>-webcenter-bucketis not found in stack compartment then create bucket.
- Check bucket name
- If storage bucket exists then check policies granted for the storage bucket
SSH connection failed
If you see any of the below error messages during apply_patch -
SSH connection failed
subprocess.CalledProcessError: Command '['ssh', '-i', '***', '-o', 'UserKnownHostsFile=/dev/null', '-o', 'BatchMode=yes', '-o', 'StrictHostKeyChecking=no', 'opc@localhost', 'echo "Connected successfully!"']' returned non-zero exit status 255.
Check and remove passphrase from ssh private key.
For generating a private key without any passphrase using passphrase-based key, see Convert a Passphrase-Based Private Key to Empty Passphrase Private Key
Post Switchover Steps for WebCenter Sites Cross Region Disaster Recovery
After switchover and switchback of WebCenter Sites stack, we need to reconfigure the Sites cluster with current primary’s host details.
- Log in to WebCenter Sites (https://<sites-host>:7103/sites). Navigate to Admin, System Tools, and then Cluster Node Management.
- You will need to update the cluster settings to align with the current primary hosts. Under Choose Option drop-down, select Edit. The Choose Node drop-down will display the current servers (nodes) configured for WebCenter Sites.
- If there are no existing nodes configured in Choose Node drop-down, choose the Add option from the Choose Option drop-down menu and enter the node details as described in the next step.
- If the node is shown in the drop-down, select the node and enter the node details as described in the next step. You will need to update the node with the current primary’s host IP. For example, for wcsites_server1, you will need to update the Host Name and Batch Host name with host IP.
- If the drop-down displays any additional nodes that are not configured for the current primary stack, select Delete under Choose Option and delete the node configuration.
- Enter the following details for the node:
- Node name: Enter the server name. For example: wcsites_server1.
- Host name: The host IP address of the compute instance where the server is running. For example, the host IP address of wcsites_server1 is the private IP of the host *-wls-1.
- Port number: 7103
- Batch Host name: The IP address of the admin host *-wls-1.
- Batch Port number: 7103
- Are you installing over a secure connection?: Select No and then Add.
- If the WebCenter Sites stack has scaled out to more than one node, you will also need to complete Step 2 and Step 3 for all remaining nodes in the cluster.
Using Oracle WebCenter 14c (14.1.2) on Marketplace, 14c (14.1.2.0.0)
G27079-10