16 Complete Conditional Common Post-Installation Tasks
After successfully completing the mandatory post-installation tasks, review and perform the following conditional tasks. Some components in the Oracle Fusion Applications environment are dependent on one another. Therefore, it is important to start and stop components in the proper order. In the course of normal Information Technology (IT) operations, common operations include shutting down computers and starting them back up. Therefore, it is crucial to start and stop Oracle Fusion Applications in a sequential manner.
-
Configure Oracle User Productivity Kit In-Application Support
-
Review and Configuring Diagnostic Logging Settings and Diagnostic Testing Features
-
Set up Oracle Enterprise Manager Cloud Control to Monitor and Manage Oracle Fusion Applications
-
Complete Conditional Oracle Identity Management Post-Installation Tasks
-
Install and Configuring Oracle Business Intelligence Applications
-
Configure Oracle HTTP Server for Privileged Port (UNIX Only with No Load Balancer)
16.1 Set Up Global Search
Oracle Fusion Applications Search provides the search framework to manage enterprise-wide searches. Each product family within Oracle Fusion Applications such as Oracle Fusion Customer Relationship Management, Oracle Fusion Human Capital Management, and Oracle Fusion Supply Chain Management has its own set of seeded searchable objects that are packaged into its corresponding search application. For example, the seeded searchable objects for Oracle Fusion Customer Relationship Management such as leads, opportunities, and contacts are packaged in the Oracle Fusion Customer Relationship Management search application. To support the lifecycle management of searchable objects for a particular product family, provision the Oracle Fusion Applications environment.
This task is not applicable to Oracle Cloud implementations.
16.1.1 Oracle Fusion Applications Environment
Provisioning the Oracle Fusion Applications environment is mandatory before you can manage the searchable objects of any product family. See Provision a New Oracle Fusion Applications Environment.
16.1.2 Oracle Enterprise Crawl and Search Framework
Oracle Fusion Applications Search functionality is fundamentally made possible by the integration of three systems, each playing a role in forming the complete search platform:
-
Oracle Fusion Applications Search leverages the Oracle Enterprise Crawl and Search Framework (ECSF) to enable search on transactional business objects. Therefore, validating the environment for Enterprise Crawl and Search Framework involves the recommended checks for establishing Oracle Fusion Applications Search. See Validate the Oracle Enterprise Crawl and Search Framework Environment.
-
Managing search involves making seeded searchable objects available for search, maintaining search categories, and so on.
-
To make the Oracle Fusion Applications search components appear on the user interface, enable the relevant profile option.
ECSF is an Oracle Fusion Middleware search framework that enables the exposure of application context information on various business objects to enable full-text transactional search. Benefits of ECSF include:
-
Transparent integration of applications with search engines, which minimizes development time and maximizes the user experience with search
-
Code reuse, through use of a well designed set of abstract classes, to reduce long design cycles
-
Basic platform for developing search, which helps new developers to grasp the conceptual flow of work easily
-
Centralized process and control mechanism, which enhances search functionality
-
Wide range of optimizations that offer better control to leverage search results
16.1.2.1 Oracle Enterprise Crawl and Search Framework Management Features
ECSF management features include:
-
Runtime server, a metadata-driven runtime engine that serves as an integration framework between enterprise data sources and Oracle Secure Enterprise Search (Oracle SES). It enables crawling, indexing, and the security service. It also serves as the semantic engine that provides "smart" search features, such as faceted navigation, actionable results, and related search.
-
Oracle Enterprise Manager Fusion Applications Control (Fusion Applications Control), an administration user interface for configuring and administering the ECSF runtime server, managing the searchable object lifecycle, and synchronizing with Oracle SES. Support for a command line administration option is also provided. See ECSF Command Line Administration Utility in the Oracle Fusion Applications Developer's Guide.
16.1.2.2 Key Oracle Enterprise Crawl and Search Framework Features
Key ECSF features that are built on top of Oracle SES and enhance the Oracle Fusion Applications user experience with search include:
-
Basic search, which allows query based on keyword and search category
-
Advanced search, which allows query based on keyword, search category, and up to 100 attribute filters
-
Faceted navigation, which allows the filtering of search results based on attributes of the business objects. Users can navigate a search result set based on a set of predefined facets, or dimensions. This feature returns a list of facets and their associated set of available values with the search result. Users can select a value for each facet, which is then submitted with the search query to narrow down the result set
-
Actionable results, which are search results with action links associated with the searchable objects. From the search results users can either go straight to the page displaying the record they selected, or they can invoke a specific task on a search result
-
Saved searches, which allows saved search criteria for later use. Users can create new saved search entries, edit and delete existing saved search entries, and retrieve user-specified or public saved search entries
-
File attachments, which allow the crawling of attachments that are associated with Oracle Fusion Applications transactional objects or records
-
Crawling Oracle WebCenter Portal tags, which supports crawling searchable objects that contain Oracle WebCenter Portal tags
-
Crawling tree structures, which supports search functionality on source systems containing data that is organized in a tree structure (for example, Oracle Business Intelligence Catalog)
-
Search support for external data sources, which allows querying against search groups that contain external data sources, which are non-ECSF related data sources, such as wiki pages and blogs, that are directly crawled by Oracle SES
16.1.3 Validate the Oracle Enterprise Crawl and Search Framework Environment
Before beginning to manage search with ECSF, make sure that the environment is set up properly for using ECSF.
To validate the ECSF setup, follow the procedures in the following sections.
- Task 1 Make Sure That Oracle Fusion Applications Includes Search Functionality
-
Oracle Fusion Applications Search should be embedded within Oracle Fusion Applications, but it must be enabled in the user interface by setting the profile option
FUSION_APPS_SEARCH_ENABLEDtoY.To make sure that Oracle Fusion Applications includes search functionality:
-
Log in to Oracle Fusion Applications. In case of any problems to log in to Oracle Fusion Applications, contact the installation team.
-
Verify that the Enterprise Search box is available at the top of every Oracle Fusion Applications page.
-
View the Search Categories dropdown list. There should be no search categories listed.
-
Log out.
-
- Task 2 Make Sure That Oracle SES Is Installed and Configured Properly
-
Oracle SES provides the fundamental search capability that includes crawling, indexing, and querying. For more information about Oracle SES, see Introduction to Oracle Secure Enterprise Search in the Oracle Secure Enterprise Search Administrator's Guide.
To make sure that Oracle SES is installed and configured properly:
-
Check the administration endpoint by logging in to the Oracle SES Administration GUI with the administration username and password at the following URL.
http: host_name:7777/search/admin/index.jspThe default port number is 7777. Make sure to use the correct port number for the installation. In case of any issues to access the Oracle SES search engine, contact the installation team.
-
Make sure that the Oracle SES identity plug-in has been registered.
-
Make sure that the federated trusted entities are created. Depending on what product families are installed, it should possible to see one to three proxy users listed. The valid values are:
-
FUSION_APPS_CRM_ECSF_SEARCH_APPID -
FUSION_APPS_FSCM_ECSF_SEARCH_APPID -
FUSION_APPS_HCM_ECSF_SEARCH_APPID
-
-
- Task 3 Make Sure That Fusion Applications Control Is Available
-
Fusion Applications Control must be available for configuring and administering the ECSF runtime server, managing the searchable object lifecycle, and synchronizing with Oracle SES.
To make sure that Fusion Applications Control is available:
-
Log in to Oracle Enterprise Manager.
-
From the navigation pane, expand the farm and then the Enterprise Crawl and Search Framework folder.
-
Select the application engine instance that contains the searchable objects that are managed to open the Enterprise Crawl and Search Framework Configuration Settings page.
The search engine types (Oracle SES) should be listed.
-
Click the Oracle SES search engine type name link in the Search Engine Types table to open the Search Engine Instance administration page, and validate the Oracle SES search engine instance parameters.
-
From the table of search engine instances, select a search engine instance record, and then select the Searchable Objects tab to view the table of searchable objects, and validate the list of searchable objects for the application. For a list of seeded searchable objects.
-
Select the Search Categories tab to view the table of search categories, and validate the list of search categories and objects associated with the search categories for the application. For a list of seeded search categories.
-
From the navigation pane, re-select the application to open the Enterprise Crawl and Search Framework Configuration Settings page, then click the Search Application Service Component link to open the Search Application Service Component administration page, and validate that the search applications for the product families are installed.
-
- Task 4 Provide Access to ECSF Pages in Fusion Applications Control
-
To access the ECSF pages in Fusion Applications Control, users must have Operator privileges in Oracle WebLogic Server. Add the users to the Operator group and above on Oracle WebLogic Server.
- Task 5 Validate the Application Identities
-
Oracle Fusion Applications include seven search-related application identities that are seeded and are stored in the identity store:
-
FUSION_APPS_CRM_SES_CRAWL_APPID -
FUSION_APPS_CRM_ECSF_SEARCH_APPID -
FUSION_APPS_FSCM_SES_CRAWL_APPID -
FUSION_APPS_FSCM_ECSF_SEARCH_APPID -
FUSION_APPS_HCM_SES_CRAWL_APPID -
FUSION_APPS_HCM_ECSF_SEARCH_APPID -
FUSION_APPS_ECSF_SES_ADMIN_APPID
ECSF is powered by Oracle SES. To integrate with Oracle SES, several integration identities known as application identities are used. For each Oracle Fusion Applications application, there are a pair of application identities, for example,
FUSION_APPS_HCM_SES_CRAWL_APPIDandFUSION_APPS_HCM_ECSF_SEARCH_APPID. TheCRAWLapplication identities are used by Oracle SES to interact with ECSF for crawling and security requests, while theSEARCHapplication identities are used by Oracle SES to query Oracle SES as proxy users.FUSION_APPS_ECSF_SES_ADMIN_APPIDis the application identity used by ECSF to integrate with Oracle SES for administration tasks, such as deployment, scheduling, and so on.Application identities are provisioned as users in the Oracle Fusion Applications identity store. They often have high level privileges, and their credentials are generated and stored in the credential store. These users are used mainly for machine to machine (application to application) integration.
The Lightweight Directory Access Protocol (LDAP) credential store stores the passwords for the identities that Oracle Fusion Applications and ECSF uses to retrieve passwords for Oracle SES integration.
View the LDAP credential store to make sure the application identities exist.
-
16.1.4 Configure Help Search: Highlights
It is possible to include Help in the list of search categories for the search in the global area of Oracle Fusion Applications. This search is of type Oracle Fusion Applications Search, and administering this search involves tasks in Oracle Enterprise Crawl and Search Framework.
This task is not applicable to Oracle Cloud implementations.
The search in Oracle Fusion Applications Help and the navigators, for example Search by Business Process, are based on other search functionality and do not require configuration.
Oracle Enterprise Crawl and Search Framework administration is described fully in Understand Key Oracle Enterprise Crawl and Search Framework Features in the Oracle Fusion Applications Administrator's Guide. While reading content from that guide, keep in mind that Oracle Fusion Applications Search is not used only for Oracle Fusion Applications Help; therefore, the content is not specific to help.
16.1.5 Searchable Objects
-
Deploy and activate the TopicSearchPVO searchable object, associate it with the Help category and deploy the category, and deploy and start index schedules. Each crawl picks up customizations and patches for help, so the frequency depends on how often you help is added, managed or patched.
-
Do not modify the TopicSearchPVO searchable object itself.
16.1.6 Configure External Search Categories for Oracle Business Intelligence and Oracle WebCenter Portal: Procedures
To perform global search within Oracle Business Intelligence and Oracle WebCenter Portal, create the appropriate external search categories in Oracle Fusion Applications. For general instructions on making external search categories available for search, see Make External Search Categories Available for Federated Search in the Oracle Fusion Applications Administrator's Guide.
However, before proceeding with the configuration of external search categories for Oracle Business Intelligence and Oracle WebCenter Portal, create manually the Business Intelligence data source.
Perform the search-related configuration tasks using Oracle Enterprise Crawl and Search Framework. To configure external search categories for Oracle Business Intelligence and Oracle WebCenter Portal, follow these instructions.
-
Log in to Oracle Enterprise Manager Fusion Applications Control.
-
From the navigation pane, open Farm - Enterprise Crawl and Search Framework folder.
-
Select the application engine instance SES 11.2.1. It contains the searchable objects that are managed to open the Enterprise Crawl and Search Framework Configuration Settings page.
-
From the Search Engine Types table, click Oracle Fusion Application Search engine SES 11.2.1 to open the Search Engine Instance administration page.
-
On the External Search Categories tab, click Import.
-
In the Available Categories column, select the checkbox of the external search categories to be imported, and click Move to shuttle the selection to the Selected Categories column.
-
To import Oracle Business Intelligence, select bi_search
-
To import Oracle WebCenter Portal, select Collaboration
-
-
Click OK to import the selected external search categories.
-
Associate the Application ID with the imported external categories:
-
To associate with Oracle Business Intelligence, in the Application ID column corresponding to the imported external search category (bi_search), enter BI.
-
To associate with Oracle WebCenter Portal, in the Application ID column corresponding to the imported external search category (Collaboration), enter WC.
-
-
Click Save External Search Category to save the selected record.
-
Associate the Application ID with the Search Service component:
-
From the navigation pane on the left side, select Enterprise Crawl and Search Framework folder. The Enterprise Crawl and Search Framework Settings page appears.
-
From the context menu of Enterprise Crawl and Search Framework, select Home.
-
Select the first active service component and note down the search engine instance that is associated with the active service component.
-
In the
ECSF_QUERY_SERVICE_APP_IDSfield, enter the Application ID in comma separated string format:
-
To configure external search category for Business Intelligence, enter BI.
-
To configure external search category for Oracle WebCenter Portal, enter WC
-
-
Save the changes.
-
Restart the Search application from the WebLogic Server Console.
16.1.7 Make a Search Application Highly Available
Each installation of Oracle Fusion Applications can provision one or more offerings such as Oracle Fusion Customer Relationship Management (Oracle Fusion CRM), Oracle Fusion Human Capital Management (Oracle Fusion HCM), and so on. Each offering has its own search application such as CRM Search Application, HCM Search Application and so on. However, the application architecture restricts running only one search application at a time and only that search application is registered as the identity plug-in end point of Oracle Secure Enterprise Search (Oracle SES). The identity plug-in end point of Oracle SES is a critical part of Oracle Fusion Search and is used in authenticating all users using the search functionality. Therefore, to mitigate the risk of any down time, it is necessary to identify and make the registered search application highly available by adding more managed WebLogic servers to the cluster.
Depending on the provisioned offerings, the actual search application registered as the identity plug-in endpoint varies. The following instructions help identify the search application and add more managed WebLogic servers to the existing cluster.
16.2 Set Up Privacy Statement
The Privacy Statement link is disabled by default.
Enable the Privacy Statement link in the About this Page dialog available from the Settings and Actions menu and configure it to link to a customer-defined page by setting the PRIVACY_PAGE profile option value to a full URL. See About Setting and Accessing Profile Values in the Oracle Fusion Applications Developer's Guide.
16.3 Configure Oracle User Productivity Kit In-Application Support
This section describes the procedures for setting up the Oracle User Productivity Kit In-Application Support.
Users may need to access and take advantage of the Oracle User Productivity Kit (UPK) content while working with Oracle Fusion Applications. To make the Oracle UPK content available for users, enable and configure the UPK link under the Settings and Actions menu of Oracle Fusion Applications, using the Oracle UPK In-Application Support functionality.
To perform this task, have the role of a System Administrator and have relevant privileges on the environment where the UPK link is enabled and configured.
Configuring the Oracle UPK In-Application Support involves the following activities:
- Registering Oracle UPK as an Enterprise Application.
- Deploying the Oracle UPK package on a HTTP server.
16.3.1 Register Oracle UPK as an Enterprise Application
The system administrator must have security access to use Oracle Fusion Functional Setup Manager to complete the steps that follow.
To complete the configuration:
-
From the Oracle Fusion Applications home page, navigate to Navigator, Tools, Setup and Maintenance to access the Setup and Maintenance work area.
-
In the Tasks list, select Topology Registration, Register Enterprise Applications to access the Register Enterprise Applications work area.
-
In the Register Enterprise Applications work area, do one of the following:
-
To modify an existing configuration, click the Name link of the registered application.
For example: Oracle User Productivity Kit
-
If this is a new configuration, click Add (+) to register Oracle UPK as a new application in Oracle Fusion Applications.
-
-
In the Add Enterprise Application work area, in the Basic Information section, do the following:
-
In the Enterprise Environment drop-down list, select the environment.
For example: Oracle
-
In the Enterprise Application drop-down list, select the enterprise application.
For example: Oracle User Productivity Kit
-
In the Name field, enter the name of the enterprise application to be registered.
For example: Oracle User Productivity Kit
-
-
In the Server Details section, do the following:
-
In the Server Protocol drop-down list, select the appropriate protocol for the server that is planned to be used to launch UPK content.
The UPK Player supports both HTTP and HTTPS.
-
In the External Server Host field, enter the full DNS name of the server host.
For example: content.mycompany.com
-
In the External Server Port field, enter the appropriate port for either HTTP or HTTPS. It could be either the default value 80/443 or customer configured port location.
The Context Root name is the name of the virtual directory used in the URL that launches the UPK content.
-
Click Save and Close when the process is done.
-
-
Click Regenerate Domain Connections.
-
Log out of Oracle Fusion Applications and log in again.
-
Click the Settings and Actions menu on the Oracle Fusion Applications Home page to verify if the Oracle User Productivity Kit is now available as a menu item.
16.3.2 Deploy the Oracle UPK Player Package
Deploy the Oracle UPK Player Package to any server that uses the HTTP or HTTPS protocols.
The content root directory must be configured to the location of the Oracle UPK Player on the web server.
For example: http(s)://<server>:<port>/<directory>
Test access to the content.
If the Oracle UPK Player launches with all topics, continue to Oracle Fusion Applications for In-Application Support.
16.4 Review and Configure Diagnostic Logging Settings and Diagnostic Testing Features
The infrastructure for health checking and troubleshooting Oracle Fusion Applications is provided along with provisioning. However, before beginning any production activity on Oracle Fusion Applications, perform the following configuration tasks.
This task is not applicable to Oracle Cloud implementations.
16.4.1 Configure Settings for Log Files During Normal Operation
Although critical business logic sections of Oracle Fusion Applications may write more information to log files than less critical areas of the application code, the amount of information that Oracle Fusion Applications log depends primarily on how the environment is configured. Oracle supplies default values for log settings, but different setting values can be specified to adjust the amount of information to be logged. Most Oracle Fusion Applications components use a standard set of log configuration settings.
In busy computing environments, the amount of disk space used by log files can become a concern. Large log files can also affect system performance. Oracle Fusion applications that are written in PL/SQL address this concern using automatic log file rotation.
16.4.1.1 Manage Rotating Log File Space Usage for PL/SQL Applications
For Oracle Fusion Applications modules that are implemented using PL/SQL, when a diagnostic.log file reaches a specific size, the diagnostic.log file is automatically renamed, and a new diagnostic.log file is created. If the AFLOG_PLSQL_FILENAME profile option is set so that the logging framework uses a log file name other than diagnostic.log, then the file name that the profile option specifies is used, instead of diagnostic.log.
Use the following profile options settings to specify the maximum log file size:
(KSQ: revisit this section: is ordered list procedure needed? Looks like FAC for profile option changing, yes?)
-
AFLOG_MAX_FILE_SIZE:This setting specifies the size in megabytes beyond which a PL/SQL log file name is automatically renamed and a new log file is started. The default value is 10 megabytes.If the
AFLOG_BUFFER_MODEprofile option is set to a value larger than 0, enabling asynchronous buffering of PL/SQL log entries, then the actual maximum size of any single PL/SQL log file is the value ofAFLOG_MAX_FILE_SIZEplus the number of megabytes that are flushed from the buffer. This value is approximate, because the amount of information that can accumulate in the buffer is set using theAFLOG_BUFFER_SIZEsetting, which specifies a specific number of log records, rather than a specific number of megabytes. -
AFLOG_NUMBER_OF_LOG_FILES:This setting specifies the maximum number of PL/SQL log files the system keeps at any one time. The default value is 10 files.
PL/SQL log rotation is currently done only on the basis of file size, not on the basis of the passage of a specified amount of time.
When a PL/SQL log file is renamed, the new name depends on whether the AFLOG_PLSQL_FILENAME profile option is set:
-
If the profile option is set, then the new log file name is of the format
AFLOG_PLSQL_FILENAME_value-n.log,wherenis a positive integer. -
If the profile option is not set, then the new log file name is of the format
diagnostic-n.log,wherenis a positive integer.
The value of n depends on the names of the log files that are already present in the directory. If the directory contains no previously renamed log files, then the first renamed log file is called diagnostic-1.log or AFLOG_PLSQL_FILENAME_value-1.log. If other log files exist, then n is set to the next higher integer after the highest integer that is already in use. For example, if the directory contains diagnostic-1.log through diagnostic-8.log at the time when the diagnostic.log file surpasses the size limit set in the AFLOG_MAX_FILE_SIZE profile option, then the diagnostic.log file is renamed to diagnostic-9.log.
When the number of log files reaches the value specified using the AFLOG_NUMBER_OF_LOG_FILES profile option, then older log files are deleted automatically, to prevent the disk space usage of the log file directory from getting too large.
Over time, the value of n in diagnostic-n.log or AFLOG_PLSQL_FILENAME_value-n.log can become large enough to cause usability challenges or exceed the number of characters that the operating system allows in a file name. To have the value of n start over at 1, move all existing log files except the currently active diagnostic.log file or AFLOG_PLSQL_FILENAME_value.log file into another directory. When the active file surpasses the size limit and the log rotation code finds no previously renamed log files in the directory, the active file is renamed using a value of 1 for n.
If the Oracle Fusion Applications environment includes multiple database nodes such as Oracle Real Application Clusters (RAC), then each database node corresponds to a server instance that has its own location for log files.
If an incident is created, then the server instance that creates the incident handles all subsequent jobs related to that incident. Identifiers for incidents are unique within a specific instance, but not across instances. For more information about working with incidents, see Prepare to Troubleshoot Using Incidents, Logs, QuickTrace, and Diagnostic Tests in the Oracle Fusion Applications Administrator's Guide.
(KSQ: consider moving this info to the troubleshooting chapter, since it seems more useful for troubleshooting than normal operation?)
16.4.1.2 Manage Log File Space Usage for C Applications
Oracle Fusion Applications modules that are implemented in C currently produce log files that continually increase in size.
Writer note: PM says it's very important to include this section, despite not seeing a corresponding section in the FMW Admin Guide that Thomas K. designated as a model for this book, because Oracle Fusion Applications that are implemented in C do not have a log management facility.
To manage log file space usage for log files created by Oracle Fusion Applications modules that are written in C:
-
Navigate to the directory that contains the log files:
-
If the
AFLOG_FILENAMEprofile option is set, then navigate to the location designated by the profile option value. -
If the
AFLOG_FILENAMEprofile option is not set, then navigate to the location set by Oracle Enterprise Scheduler Service.Use Fusion Applications Control to determine the location of Oracle Enterprise Scheduler log files, as follows:
-
In the navigation pane, expand the farm part of the navigational tree, then expand Scheduling Services, and then select an Oracle Enterprise Scheduler server as the target.
-
In the context pane, from the Scheduling Service dropdown menu, choose Logs, View Log Messages.
-
Click Target Log Files to view a list of log files associated with the selected server.
For example, a typical path and file name might be the following, where
APPLICATIONS_CONFIG/domain/<domain_name>is the domain home directory,SERVER_HOMEis the server home directory, andserverNameis the name of the Oracle Enterprise Scheduler server:APPLICATIONS_CONFIG/domain/<domain_name>/servers/SERVER_HOME/logs/serverName-diagnostic.log
(REVIEWER: Correct? On the PRC system where I saw this on 02/10/11,
http://example.country.oracle.com:8201/em,whereexample.countrywasadcdbc13.us,there were also ESS log file names in the formatserverName.logandserverName.log0000n,but the downloaded files withdiagnosticin the file name were the ones that referred to the product such as PRC or PRJ.)
-
-
-
Rename the log file that is currently in use.
For example, if the current log file is called
Cdiagnostic.log,it might be renamed toCdiagnostic_MMDDYYYY.log,whereMMDDYYYYis the current date. -
Delete any previously renamed log files that are no longer need.
16.4.2 Understand Oracle Fusion Applications Diagnostic Tests and the Diagnostic Framework
Incidents are collections of information about error conditions. It is strongly recommended to follow Information Technology Infrastructure Library (ITIL) best practices by establishing a help desk or service desk within the organization to support Oracle Fusion Applications, and have the help desk personnel use incidents to track the troubleshooting and resolution of all problems. Some incidents are created and gather information automatically when problems occur. For example, the information associated with an automatically created incident may include detailed operational information collected by the QuickTrace (in-memory logging) feature for Oracle Fusion Applications. For problems that do not automatically create incidents, administrators or help desk personnel can manually create incidents and manually gather and add related system information.
Log files contain information about both normal and problematic events. Log files can help both to monitor normal operations and to diagnose and address some problems. For example, log messages that state that a service cannot be reached might indicate a hardware failure. If r a more complex issue is discovered, then Oracle Support personnel may use log files to trace the execution code paths of relevant requests, as part of diagnosing the problem. Log files are particularly helpful if the Oracle implementation contains custom code that needs debugging, especially when using a debugger is not feasible, such as on a production system.
The QuickTrace (in-memory logging) feature continuously records a specified level of log detail in an area of memory. The memory is recycled on an ongoing basis, with the oldest information being deleted or overwritten first. Because QuickTrace writes to memory instead of to a log file, it can gather operational information continuously without significantly affecting system performance. The information that QuickTrace stores in memory is written to disk only when an incident occurs or when an administrator manually dumps the contents of a QuickTrace buffer.
Diagnostic tests are executables that are designed to exercise particular aspects of Oracle Fusion applications, to determine whether they are operating correctly and to help identify and resolve any problems. The Oracle Fusion Applications Diagnostic Testing Framework (Diagnostic Testing Framework) lets execute diagnostic tests and collects the results into detailed diagnostic reports. Oracle provides diagnostics tests that are installed along with Oracle Fusion Applications releases and patches.
Use diagnostic tests along with information from log files and the collections of error condition information that are called incidents.
In Cloud Control, Support Workbench helps investigate, report, and resolve problems (critical errors). Use Support Workbench to perform the following kinds of operations:
-
View summary information about recent problems and incidents
-
View detailed diagnostic data that was gathered automatically
-
Manually trigger additional dumps of diagnostic data
-
Connect to the Oracle Fusion Applications Diagnostic Dashboard (Diagnostic Dashboard), which provides additional diagnostic tests that can be run
-
Create or update service requests with Oracle Support, including uploading diagnostic data to Oracle
16.4.2.1 Relationships Between Diagnostic Tests, Incidents, and Log Messages
Oracle developers create diagnostic tests that can be used to help diagnose and resolve Oracle Fusion application problems.
Oracle developers use mechanisms such as application programming interface (API) calls in Oracle Fusion Applications code to record application operations in log files and to provide error messages as appropriate. A diagnostic test may or may not be associated with a particular error message.
If an Oracle Fusion application handles a particular error in a way that triggers the creation of an incident, then any diagnostic tests that are associated with the error message for the incident run automatically. Oracle developers accomplish this by setting the value of each diagnostic test's APPS_MSG_ID tag to match the identifier of any error message that should trigger the automatic execution of that test. There is no configuration setting for disabling this automatic execution of diagnostic tests.
The results of any automatically run diagnostic test are automatically associated with the related incident, and the identity of the user who received the error message is recorded.
For more information about using diagnostic tests and log files to help diagnose a problem, see Prepare to Troubleshoot Using Incidents, Logs, QuickTrace, and Diagnostic Tests in the Oracle Fusion Applications Administrator's Guide.
It is important to be familiar with the following additional concept that Seed data is information that Oracle provides in the form of database records. Diagnostic tests are included in seed data.
16.4.2.2 Standard Diagnostic Testing Administration Tasks and Tools
Under normal circumstances, the following administrative tasks are associated with Oracle Fusion Applications diagnostic tests:
-
Configuring security to provide appropriate access to diagnostic tests. Job roles can be assigned to particular users to grant those users the ability to perform various diagnostic operations.
In the current release, a job role for diagnostic operations grants the user the ability to perform the specified operations for all diagnostic tests that are provided with Oracle Fusion Applications. When choosing whether to grant a diagnostic job role to specific users, be aware that some diagnostic tests may include sensitive information in their results.
(Writer note: this information is current as of early December 2010. Depending on technical and scheduling constraints, future releases may or may not add the ability to control access to individual diagnostic tests.
-
Running diagnostic tests. Diagnostic tests can be used for the following purposes:
-
Routinely checking the health of the Oracle Fusion applications
-
Troubleshooting a problem with an Oracle Fusion application
-
Collecting detailed data that may help Oracle Support to resolve a problem
-
Some diagnostic tests require a specific Oracle Fusion application to be running while the test is performed—these diagnostic tests are called internal diagnostic tests. Other diagnostic tests can perform their functions even if the Oracle Fusion application to be tested is not running—these tests are called external diagnostic tests.
(Writer note: PM says customer administrators do not need to know the technical differences between what internal means for Java tests and what it means for PL/SQL tests. I.e., a Java internal diagnostic test reuses or refers to code modules, entity objects, or view objects from a Fusion application, but a PL/SQL internal diagnostic test runs using the data security context of the Fusion application.)
The distinction between internal and external tests is important because it affects both when the tests can be run and which interfaces can be used to run the tests. The Diagnostic Testing Framework provides two interfaces:
-
The Oracle Fusion Applications Diagnostic Dashboard application (Diagnostic Dashboard) provides a graphical user interface that allows to perform the following tasks:
-
Execute and monitor both internal and external diagnostic tests for Oracle Fusion applications
-
Purge diagnostic test results
-
Register any special-purpose diagnostic tests that Oracle Support may provide
-
Work with categorization tags to keep the diagnostic tests organized
(Writer note: references to custom tags hidden for v1 per PM request, as we do not yet have a supported migration path for custom tags.)
-
-
The
diagctlcommand-line interface allows to perform the following tasks:-
Execute external diagnostic tests (tests that do not require a specific Oracle Fusion application to be running)
Technical constraints prevent the
diagctlcommand-line interface from returning useful results for internal diagnostic tests (tests that require a specific Oracle Fusion application to be running when the test is performed). Use Diagnostic Dashboard to run any internal diagnostic tests.Use also Diagnostic Dashboard to determine whether a particular test is an internal or an external test.
-
View diagnostic test results
-
Register any special-purpose diagnostic tests that Oracle Support may provide
-
16.4.3 Configure the Diagnostic Testing Framework for Normal Operation
Diagnostic tests can be used to check normal system health and to troubleshoot system problems. The Oracle Fusion Applications environment can be configured to run all Oracle Fusion Applications diagnostic tests using the Diagnostic Dashboard application, and to run external diagnostic tests using the diagctl command-line interface.
Technical constraints prevent the diagctl command-line interface from returning useful results for internal diagnostic tests (tests that require a specific Oracle Fusion application to be running when the test is performed). Use Diagnostic Dashboard to run any internal diagnostic tests.
Use also Diagnostic Dashboard to determine whether a particular test is an internal or an external test.
Both the Diagnostic Dashboard application and the diagctl command-line interface are automatically installed as part of the Oracle Fusion Applications installation. However, assign appropriate job roles to specific users to give them the ability to display and perform operations using the Diagnostic Dashboard application. Access to the diagctl command-line interface is controlled at the level of the server operating system.
For proper operation of the diagctl command-line interface, set also certain environment variables.
To help to locate diagnostic tests for specific purposes, the diagnostic tests that are received with Oracle Fusion applications are all assigned to predefined categories.
(Writer note: references to custom tags hidden for v1 per PM request, as we do not yet have a supported migration path for custom tags.)
If preferred, define also custom categories and use categorization tags to assign tests to the custom categories.
The custom categories to which the diagnostic tests are assigned can be changed, and the custom categorization tags and tag values from the database can be removed.
The tag name and tag value assignments that Oracle uses to categorize diagnostic tests cannot be changed, and those tag names or tag values from the database cannot be removed. The following related links in the Task pane of the Diagnostic Dashboard application are intended for use by Oracle personnel only:
-
Add New Tag
-
Add New Tag Value
-
Assign Tags to Tests
-
Unassign Tags from Tests
-
Remove Tag
-
Remove Tag Value
WARNING: Do not attempt to modify the diagnostic test seed data provided by Oracle. Unauthorized modification of this seed data may prevent diagnostic tests from functioning correctly, lengthening the amount of time required to resolve both current and future problems.
16.4.3.1 Control Access to Diagnostic Testing Functionality
Access to diagnostic testing functionality is controlled separately for Diagnostic Dashboard and the diagctl command-line interface.
For the diagctl command-line interface, access is controlled at the level of the server operating system. If a user can log in to the server where diagctl is stored, and if that user has operating system permissions to read and execute diagctl, then that user can use diagctl to perform all diagnostic operations that the command-line interface supports.
For Diagnostic Dashboard, Oracle Identity Manager can be used to assign specific users to any of the four preconfigured job roles that grant users access to Diagnostic Dashboard. Each of these four job roles provides access to a different amount of the functionality of the dashboard.
Oracle Fusion Applications display the Troubleshooting, Run Diagnostic Tests command in the Settings and Actions menu only for users who are associated with the preconfigured job roles that grant access to Diagnostic Dashboard operations.
-
The
Diagnostic Viewerjob role can view and analyze diagnostic test results for Oracle Fusion applications. -
The
Diagnostic Regular Userjob role can execute diagnostic test runs and view diagnostic test results for Oracle Fusion applications, and cancel diagnostic test runs that were started by the current user. -
The
Diagnostic Advanced Userjob role can schedule and execute diagnostic test runs, view diagnostic test results, attach test results to application incidents for Oracle Fusion applications, and cancel diagnostic test runs that were started by the current user. In general, this job role is recommended for running Oracle Fusion Applications diagnostic tests, because its added capabilities allow users to work with administrators more flexibly during troubleshooting. -
The
Diagnostic Administratorjob role can use all of the diagnostic testing functionality provided for Oracle Fusion applications, including purging test results from the database and canceling test runs started by other users.
In the current release, any job role for diagnostic operations grants the user the ability to perform the role's specified operations for all diagnostic tests that are provided with Oracle Fusion applications. When choosing whether to grant any diagnostic job role to specific users, be aware that some diagnostic tests may include sensitive information in their results.
To grant specific users permission to use Diagnostic Dashboard:
- Decide which users need the capabilities of each of the four preconfigured job roles for diagnostic operations.
- Use Oracle Identity Manager to assign the appropriate job role to each user.
- For each external role that was created or found in Step 2, use Oracle Authorization Policy Manager to map the external role to the specific diagnostic duty role that allows the needed operations.
16.4.3.2 Navigate to the Diagnostic Dashboard Application
The Diagnostic Dashboard application for Oracle Fusion Applications provides a graphical user interface that lets execute and monitor diagnostic tests, display and purge test results, and register any special-purpose diagnostic tests that Oracle Support may provide. Each product family within Oracle Fusion Applications has its own instance of Diagnostic Dashboard. Provided that an appropriate job role is assigned, navigate to Diagnostic Dashboard from any Oracle Fusion application or from Oracle Enterprise Manager Cloud Control (Cloud Control).
(Writer note: paragraph above also referred to the dashboard letting the customer "work with categorization tags to keep the diagnostic tests organized," but this text is currently hidden as it implies custom tag capability, which is not planned to be supported in v1).
16.4.3.2.1 Navigate to the Diagnostic Dashboard Application from an Oracle Fusion Application
To use Diagnostic Dashboard to execute or monitor diagnostic tests or display or purge test results while using an Oracle Fusion application, navigate to Diagnostic Dashboard directly from the application.
To display the Diagnostic Dashboard application from an Oracle Fusion application:
16.4.3.2.2 Navigate to the Diagnostic Dashboard Application from Cloud Control
To use the Diagnostic Dashboard application to execute or monitor diagnostic tests or display or purge test results while using Cloud Control, such as while using Support Workbench to gather additional information about an existing incident, navigate to Diagnostic Dashboard directly from Cloud Control.
To display to Diagnostic Dashboard from Cloud Control:
16.4.3.2.3 Configure Required Variables for the diagctl Command Line Interface
To operate properly, the diagctl command-line interface requires to set certain environment variables.
Set the required environment variables for each session that plans to use the diagctl command-line interface. For more convenience, the commands that define these variables may be added to the .profile or .bashrc files of all users who will run diagctl.
To set environment variables for a user of the diagctl command-line interface:
16.4.4 Health Checking and Diagnostic Tasks
Only after ensuring the completeness of the following configuration, perform health checking and troubleshooting for Oracle Fusion applications using log files, incidents, diagnostic tests and so on. See Perform System Maintenance Tasks and Prepare to Troubleshoot Using Incidents, Logs, QuickTrace, and Diagnostic Tests in the Oracle Fusion Applications Administrator's Guide.
16.4.5 Configuration Tasks
The following configuration tasks can be performed:
-
Enable viewing of logs generated by C and PL/SQL. See Configuring Access to Logs for Fusion Applications Control in the Oracle Fusion Applications Administrator's Guide.
-
Configure log file rotation. See Configuring Log File Rotation in the Oracle Fusion Middleware Administrator's Guide.
-
Review default logging profile options and adjust values for specific requirements. See Default System Log Settings and Configure Standard Fusion Applications Log Settings for Troubleshooting in the Oracle Fusion Applications Administrator's Guide.
-
Review and adjust the QuickTrace settings. See Default System Settings for Incident Creation in the Oracle Fusion Applications Administrator's Guide.
-
Configure user access to diagnostic testing functionality. See Configure Access to the Diagnostic Dashboard in the Oracle Fusion Applications Administrator's Guide.
-
Configure a job role for future user access to troubleshooting options. See Assist Users in Gathering Data Using Troubleshooting Options in the Oracle Fusion Applications Administrator's Guide.
-
To benefit from the health checking, patching recommendations, and configuration services offered by My Oracle Support, install and configure Oracle Configuration Manager. See Install Configuration Manager on My Oracle Support.
-
To use the latest troubleshooting features, including a purpose built Oracle Fusion Applications module, provided by Remote Diagnostic Agent (RDA), install and configure RDA. See the RDA Documentation on My Oracle Support.
16.5 Configure Oracle HTTP Server with Custom Certificates
If Simple topology is implemented, SSLterminates at OHS. Provisioning configures OHS with a default dummy certificate. As the dummy certificate is not trusted by browsers, certificate warning messages are displayed when accessing any external URL.
To avoid this, configure OHS to use certificate(s) signed by a trusted certificate authority (CA). It can be an external certificate authority such as Verisign, or an internal certificate authority whose root certificate is trusted by the browser.
Generate a certificate signing request and obtain signed certificate(s) and import these certificate(s) into wallet(s). There are two options for choosing certificate(s) and the OHS configuration is different based on the chosen option.
16.5.1 Option 1
Obtain a wildcard or Subject Alternative Name (SAN) certificate. A single wildcard certificate can protect all sub-domains at the same level (for example, *.mycompany.com can be used for both fin.mycompany.com and prj.mycompany.com). A SAN certificate can protect various domains mentioned in the Subject Alternative Name field.
-
Import a single certificate (SAN or wildcard) into the wallet. Wallet location is specified using SSLWallet directive in
${ORACLE_INSTANCE}/config/${COMPONENT_TYPE}/${COMPONENT_NAME}/FusionSSL.confand by default points to the directory containing the default wallet. -
To specify the wallet containing the signed certificate, comment the existing SSLWallet directive and add a new line which points to the directory containing the wallet you have created, for example: SSLWallet "${ORACLE_INSTANCE}/config/${COMPONENT_TYPE}/${COMPONENT_NAME}/keystores/myWallet
16.5.2 Option 2
Obtain a separate server certificate for all external URLs. Procure up to 10 certificates, one for each external URL. This number varies depending on the selected offerings to provision.
After making all the necessary changes, restart OHS.
For more information about generating wallets, see Managing Keystores, Wallets, and Certificates in the Oracle Fusion Middleware Administering Oracle Fusion Middleware guide.
16.6 Set Up Backup for Oracle Fusion Applications
If there is an Enterprise Manager Cloud Control and it is intended to be used for backing up and restoring Oracle Fusion Applications, set it up before performing the initial backup. Follow the instructions detailed in Prerequisites for Using Cloud Control to Back Up or Restore the Environment in the Oracle Fusion Applications Administrator's Guide.
If Enterprise Manager Cloud Control is not intended to be used, perform backup and restore using operating system commands or third party tools to back up the Oracle Fusion Applications and Oracle Identity Management file systems, as well as database tools to back up the databases.
Ensure to perform a full backup either immediately or when the remaining post-installation tasks have been completed. See Perform a Backup in the Oracle Fusion Applications Administrator's Guide for instructions on how to perform a backup using Enterprise Manager Cloud Control or command line.
16.7 Set up Oracle Enterprise Manager Cloud Control to Monitor and Manage Oracle Fusion Applications
Oracle Enterprise Manager Cloud Control (Cloud Control) is a system management software that delivers centralized monitoring, administration, and life cycle management functionality for the complete Oracle Fusion Applications IT infrastructure from one single console. For example, monitor all the Oracle WebLogic Server domains for all the product families from one console.
For information about how to install Cloud Control, see Overview of Enterprise Manager Cloud Control in the Oracle Enterprise Manager Cloud Control Basic Installation Guide and Understanding the Basics of Enterprise Manager Cloud Control Installation in the Oracle Enterprise Manager Cloud Control Advanced Installation and Configuration Guide .
16.8 Complete Conditional Oracle Identity Management Post-Installation Tasks
Review and complete the conditional Oracle Identity Management Post-Installation tasks described in this section.
16.8.1 Post-Provisioning Steps for Oracle Access Manager
Perform the tasks in the following sections:
The Oracle Identity Management Console URLs are provided in About Oracle Identity Management Console URLs.
16.8.1.1 Update Existing WebGate Agents
Update the OAM Security Model of all WebGate profiles, with the exception of Webgate_IDM and Webgate_IDM_11g, which should already be set
To do this, perform the following steps:
16.8.2 Configure Oracle Identity Federation
This section is not applicable for the Single Host topology or when all Oracle Identity Management products are installed on the same host.
The Oracle Identity Management provisioning tools create, but do not start, Oracle Identity Federation. This section explains how to enable Oracle Identity Federation after provisioning has completed.Oracle Identity Federation is an optional component. If Oracle Identity Federation is not intended to be used, skip this section. This section describes how to extend the Oracle Identity Management domain to include Oracle Identity Federation in an enterprise deployment.
This section contains the following topics:
16.8.2.1 Start Oracle Identity Federation Managed Servers
Do the following to start the managed servers wls_oif1 and wls_oif2:
16.8.2.2 Validate Oracle Identity Federation
Validate the configuration of Oracle Identity Federation on IDMHOST1 and IDMHOST2 by accessing the Service Provider (SP) metadata on each host.
If the configuration is correct, access the following URL from a web browser:
https://SSO.mycompany.com/oamfed/sp/metadata
Metadata should be shown.
16.8.2.3 Configure the Enterprise Manager Agents
All the Oracle Fusion Middleware components deployed in this enterprise deployment are managed by using Oracle Enterprise Manager Fusion Middleware Control. To manage Oracle Identity Federation with this tool, configure the EM agents with the correct monitoring credentials. Update the credentials for the EM agents associated with IDMHOST1 and IDMHOST2. Follow these steps to complete this task:
-
Use a web browser to access Oracle Enterprise Manager Fusion Middleware Control at
http://ADMINVHN.mycompany.com:7001/em. Log in as the WebLogic user. -
From the Domain Home Page, navigate to the Agent-Monitored Targets page using the menu under Farm, then Agent-Monitored Targets.
-
Click the Configure link for the Target Type Identity Federation Server to go to the Configure Target Page.
-
On the Configure Target Page, click Change Agent and choose the correct agent for the host.
When unsure about which agent to update, execute the command:
OAM_ORACLE_INSTANCE/EMAGENT/EMAGENT/bin/emctl status agent -
Update the WebLogic monitoring user name and the WebLogic monitoring password. Enter
weblogic_idmas the WebLogic monitoring user name and the password for the weblogic user as the WebLogic monitoring password. -
Click OK to save changes.
-
16.8.2.4 Enable and Disable Oracle Identity Federation
In Service Provider (SP) mode, Oracle Access Manager delegates user authentication to Oracle Identity Federation, which uses the Federation Oracle Single Sign-On protocol with a remote Identity Provider. Once the Federation Oracle Single Sign-On flow is performed, Oracle Identity Federation will create a local session and then propagates the authentication state to Oracle Access Manager, which maintains the session information.
This section provides the steps to integrate Oracle Identity Federation with Oracle Identity Manager in authentication mode and SP mode.
MANDATORY: Federation Trust must be established prior to enabling Oracle Identity Federation.
This section contains the following topics:
16.8.2.4.1 Enable Oracle Identity Federation
This section describes how to switch the authentication of the Oracle Access Manager security domain from local authentication to Federation SSO.
Perform the following operations to switch from local authentication to Federation SSO for Browser Based Schemes:
16.8.3 Configure Identity Integration with Active Directory
This section describes how to add support for Active Directory to the enterprise deployment.
This section contains the following topics:
16.8.3.1 Create Adapters in Oracle Virtual Directory
Oracle Virtual Directory communicates with other directories through adapters.
The procedure is slightly different, depending on the directory to be connected to. The following sections show how to create and validate adapters for supported directories:
16.8.3.1.1 Remove Existing Adapters
The provisioning process created Oracle Virtual Directory adapters to Oracle Internet Directory. When switching the identity store to Active Directory, remove these adapters.
- Log in to Oracle Directory Services Manager (ODSM) at:
http://admin.mycompany.com/odsm - If this has not been done already , create connections to each of the Oracle Virtual Directory instances.
- Select one of the Oracle Virtual Directory instances and connect to it.
- Click the Adapter tab.
- Click the adapter User ID.
- Click Delete Selected Adapter.
- Repeat for the adapter CHANGELOG_OID.
- Repeat Steps 1- 7 for each Oracle Virtual Directory instance.
16.8.3.1.2 Create an Oracle Virtual Directory Adapter for Active Directory
idmConfigTool can be used to create the Oracle Virtual Directory User and Changelog adapters for Oracle Internet Directory and Active Directory. Oracle Identity Manager requires adapters. It is highly recommended, though not mandatory, to use Oracle Virtual Directory to connect to Oracle Internet Directory.
Perform the following tasks on IDMHOST1:
Run this command for each Oracle Virtual Directory instance in the topology, with the appropriate value for ovd.host in the property file.
16.8.3.1.3 Validate the Oracle Virtual Directory Adapters
Perform the following tasks by using ODSM:
-
Access ODSM through the load balancer at:
http://ADMIN.mycompany.com/odsm -
Connect to Oracle Virtual Directory.
-
Go the Data Browser tab.
-
Expand Client View to see each of the user adapter root DNs listed.
-
Expand the user adapter root DN, if there are objects already in the back end LDAP server, see those objects here. ODSM does not support changelog query, so the
cn=changelogsubtree cannot be expanded. -
Perform the following tasks by using the command-line:
-
Validate the user adapters by typing:
ldapsearch -h directory_host -p ldap_port -D "cn=orcladmin" -q -b <user_search_base> -s sub "objectclass=inetorgperson" dn
For example:
ldapsearch -h LDAPHOST1.mycompany.com -p 6501 -D "cn=orcladmin" -q -b "cn=Users,dc=mycompany,dc=com" -s sub "objectclass=inetorgperson" dn
Supply the password when prompted.
See the user entries that already exist in the back end LDAP server.
-
Validate changelog adapters by typing:
ldapsearch -h directory_host -p ldap_port -D "cn=orcladmin" -q -b "cn=changelog" -s one "changenumber>=0"
For example:
ldapsearch -h LDAPHOST1 -p 6501 -D "cn=orcladmin" -q -b "cn=changelog" -s one "changenumber>=0"
The command returns logs of data, such as creation of all the users. It returns without error if the changelog adapters are valid.
-
Validate lastchangenumber query by typing:
ldapsearch -h directory_host -p ldap_port -D "cn=orcladmin" -q -b "cn=changelog" -s base 'objectclass=*' lastchangenumber
For example:
ldapsearch -h LDAPHOST1 -p 6501 -D "cn=orcladmin" -q -b "cn=changelog" -s base 'objectclass=*' lastchangenumber
The command returns the latest change number generated in the back end LDAP server.
-
16.8.3.2 Prepare Active Directory
Prepare Active Directory as described in the following sections:
16.8.3.2.1 Configure Active Directory for Use with Oracle Access Manager and Oracle Identity Manager
16.8.3.2.2 Create Users and Groups
Create users and groups as described in the following sections.
16.8.3.2.2.1 Create Users and Groups by Using the idmConfigTool
Configure the Identity Store by using the command idmConfigTool, which is located at:
IDM_BASE/products/app/iam/idmtools/bin
When the idmConfigToolis run, it creates or appends to the file idmDomainConfig.param. This file is generated in the same directory in which the idmConfigTool is run. To ensure that the same file is appended to every time the tool is run, always run the idmConfigTool from the directory:
IDM_BASE/products/app/iam/idmtools/bin
The syntax of the command on Linux is:
idmConfigTool.sh -prepareIDStore mode=all input_file=configfile
For example:
idmConfigTool.sh -prepareIDStore mode=all input_file=idstore.props
When the command runs, it prompts to enter the password of the account to be connected to and passwords for the accounts that are being created.
The password must conform to the following rules:
This invocation of idmConfigTool creates the group orclFAOAMUserWritePrivilegeGroup.
16.8.3.2.2.2 Create the Configuration File
Create a property file, idstore.props, to use when preparing the Identity Store. The file has the following structure:
# Common IDSTORE_HOST: LDAPHOST1.mycompany.com IDSTORE_PORT: 389 IDSTORE_BINDDN: cn=orcladmin IDSTORE_GROUPSEARCHBASE: cn=Groups,dc=mycompany,dc=com IDSTORE_SEARCHBASE: dc=mycompany,dc=com IDSTORE_USERNAMEATTRIBUTE: cn IDSTORE_LOGINATTRIBUTE: uid IDSTORE_USERSEARCHBASE: cn=Users, dc=mycompany,dc=com POLICYSTORE_SHARES_IDSTORE: true # OAM IDSTORE_OAMADMINUSER:oamadmin IDSTORE_OAMSOFTWAREUSER:oamLDAP OAM11G_IDSTORE_ROLE_SECURITY_ADMIN:OAMAdministrators # OAM and OIM IDSTORE_SYSTEMIDBASE: cn=systemids,dc=mycompany,dc=com # OIM IDSTORE_OIMADMINGROUP: OIMAdministrators IDSTORE_OIMADMINUSER: oimLDAP # Required due to bug IDSTORE_OAAMADMINUSER : oaamadmin # Fusion Applications IDSTORE_READONLYUSER: IDROUser IDSTORE_READWRITEUSER: IDRWUser IDSTORE_SUPERUSER: weblogic_fa # Weblogic IDSTORE_WLSADMINUSER : weblogic_idm
Where:
-
IDSTORE_BINDDNis an administrative user in the Identity Store Directory -
IDSTORE_GROUPSEARCHBASEis the location in the directory where Groups are Stored. -
IDSTORE_HOSTandIDSTORE_PORTare, respectively, the host and port of the Identity Store directory. Specify the back end directory here, rather than Oracle Virtual Directory, Active Directory:LDAPHOST1and389. -
IDSTORE_LOGINATTRIBUTEis the LDAP attribute which contains the users Login name. -
IDSTORE_OAMADMINUSERis the name of the user to be created as the Oracle Access Manager Administrator. -
IDSTORE_OAMSOFTWAREUSERis a user that gets created in LDAP that is used when Oracle Access Manager is running to connect to the LDAP server. -
IDSTORE_OIMADMINGROUPIs the name of the group to be created to hold the Oracle Identity Manager administrative users. -
IDSTORE_OIMADMINUSERis the user that Oracle Identity Manager uses to connect to the Identity store. -
IDSTORE_READONLYUSERis the name of a user to be created, which has Read Only permissions on the Identity Store. -
IDSTORE_READWRITEUSERis the name of a user to be created, which has Read/Write permissions on the Identity Store. -
IDSTORE_SUPERUSERis the name of the administration user to be used to log in to the WebLogic Administration Console in the Oracle Fusion Applications domain. -
IDSTORE_SEARCHBASEis the location in the directory where Users and Groups are stored. -
IDSTORE_SYSTEMIDBASEis the location of a container in the directory where users can be placed when they are not wanted in the main user container. This happens rarely but one example is the Oracle Identity Manager reconciliation user which is also used for the bind DN user in Oracle Virtual Directory adapters. -
IDSTORE_USERSEARCHBASEis the location in the directory where Users are Stored. -
OAM11G_IDSTORE_ROLE_SECURITY_ADMINis the name of the group which is used to allow access to the OAM console. -
POLICYSTORE_SHARES_IDSTOREis set totruefor IDM 11g. -
IDSTORE_OAAMADMINUSERis required because of a bug inidmConfigTool.
16.8.3.2.3 Create Access Control Lists in Non-Oracle Internet Directory Directories
In the preceding sections, the Identity Store was seeded with users and artifacts for the Oracle components. If the Identity Store is hosted in a non-Oracle Internet Directory directory, such as Microsoft Active Directory, set up the access control lists (ACLs) to provide appropriate privileges to the entities created. This section lists the artifacts created and the privileges required for the artifacts.
-
Users and groups. ACLs to the users and groups container are provided in Oracle Internet Directory. Set them manually for other directories. The Oracle Identity Manager/Oracle Access Manager integration and Oracle Fusion Applications require the following artifacts to be created in the Identity store.
-
Group with read privileges to the users container (
orclFAUserReadPrivilegeGroup). Configure the local directory ACLs so that this group has privileges to read all the attributes of the users in the Identity Store. -
Group with read/write privileges to the users container (
orclFAUserWritePrivilegeGroup) -
Group with read privileges to the groups container (
orclFAGroupReadPrivilegeGroup) -
Group with read privileges to the groups container (
orclFAGroupWritePrivilegeGroup) -
Group with write privileges to a partial set of attributes (
orclFAUserWritePrefsPrivilegeGroup)
-
-
The user specified by the
IDSTORE_READONLYUSERparameter. When running thepreconfigIDstorecommand, this user is assigned to the groupsorclFAUserReadPrivilegeGroup,orclFAWritePrefsPrivilegeGroup, andorclFAGroupReadPrivilegeGroup. The user also needs compare privileges to theuserpasswordattribute of the user entry. -
The user specified by the
IDSTORE_READWRITEUSERparameter. It is assigned to the groupsorclFAUserWritePrivilegeGroupandorclFAGroupWritePrivilegeGroup. -
System IDs. The System ID container is created for storing all the system identifiers. If there is another container in which the users are to be created, that is specified as part of the admin.
-
Oracle Access Manager Admin User. This user is added to the OAM Administrator group, which provides permission for the administration of the Oracle Access Manager Console. No LDAP schema level privileges are required, since this is just an application user.
-
Oracle Access Manager Software User. This user is added to the groups where the user gets read privileges to the container. This is also provided with schema admin privileges.
-
Oracle Identity Manager user
oimLDAPunder System ID container. Password policies are set accordingly in the container. The passwords for the users in the System ID container must be set up so that they do not expire. -
Oracle Identity Manager administration group. The Oracle Identity Manager user is added as its member. The Oracle Identity Manager admin group is given complete read/write privileges to all the user and group entities in the directory.
-
WebLogic Administrator. This is the administrator of the IDM domain for Oracle Virtual Directory
-
WebLogic Administrator Group. The WebLogic administrator is added as a member. This is the administrator group of the IDM domain for Oracle Virtual Directory.
-
Reserve container. Permissions are provided to the Oracle Identity Manager admin group to perform read/write operations.
16.8.3.3 Modify Oracle Identity Manager to Support Active Directory
When first installed, Oracle Identity Manager has a set of default system properties for its operation.
If the Identity Store is in Active Directory, change the System property XL.DefaultUserNamePolicyImpl to oracle.iam.identity.usermgmt.impl.plugins.FirstNameLastNamePolicyForAD or oracle.iam.identity.usermgmt.impl.plugins.LastNameFirstNamePolicyForAD.
See Managing System Properties in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Manager.
16.8.3.4 Update the Username Generation Policy for Active Directory
If the back-end directory is Active Directory, update Oracle Identity Manager so that it only allows user names with a maximum of 20 characters. This is a limitation of Active Directory. Update the username generation policy from DefaultComboPolicy to FirstnameLastnamepolicyforAD as follows.
- Log in to the OIM Console at the URL listed in About Oracle Identity Management Console URLs.
- Click Advanced on the top of the right pane.
- Click Search System properties.
- On the navigation bar in the left pane, search on Username Generation.
- Click Default Policy for Username Generation.
- In the Value field, update the entry from
oracle.iam.identity.usermgmt.impl.plugins.DefaultComboPolicytooracle.iam.identity.usermgmt.impl.plugins.FirstNameLastNamePolicyForAD. - Click Save.
16.8.4 Set up LDAP Split Profile and Enable Active Directory Users in Oracle Fusion Applications
A split profile, or split directory configuration, is one where identity data is stored in multiple directories, possibly in different locations. A split profile is used to store custom attributes required for Oracle Fusion Applications deployment. Use this kind of deployment when to avoid modifying the existing Identity Store by extending the schema.
Oracle Virtual Directory unifies Active Directory and Oracle Internet Directory to provide a single consolidated abstract view. This is a very generic implementation scenario but is very important when setting up Oracle Identity Management for Oracle Fusion Applications to use the existing Enterprise Repository for the user base but do not want to modify the existing Enterprise Repository Schema.
For example: To provision users out of the existing Active Directory without replicating the user base to some other repository, use split profile with Active Directory and Oracle Internet Directory. In this scenario, Oracle Virtual Directory provides the consolidated view.
Figure 16-1 LDAP Split Profile Configuration
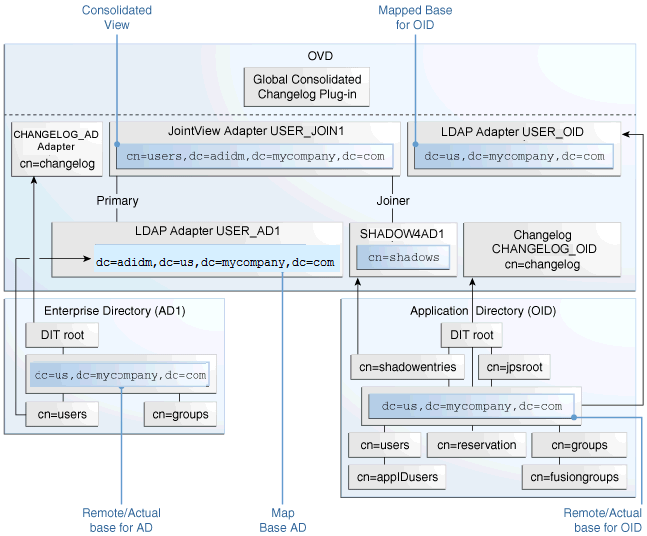
Figure 16-1 illustrates the scenario of split profile configuration where the existing Enterprise Repository is not extended and represents the view from the Oracle Virtual Directory level (adapter plug-in view/unified view).
In the image, although the actual base for both Oracle Internet Directory and Active Directory repositories are the same dc=mycompany,dc=com, the Oracle Virtual Directory Adapters are configured to map uniquely and to consolidate to a unified view of dc=adidm,dc=mycompany,dc=com.
The following sections describe how to set up split profile to enable Active Directory Users.
16.8.4.1 Create Adapters in Oracle Virtual Directory for consolidating Active Directory and Oracle Internet Directory
This section details the steps required to create Adapters in Oracle Virtual Directory for consolidating the two directory servers Active Directory and Oracle Internet Directory:
16.8.4.1.1 Set Up Oracle Internet Directory as a Shadow Directory
As Active Directory is not being extended, Oracle Internet Directory is used as a shadow directory. Use Oracle Virtual Directory to merge the entities from the directories by creating a container in Oracle Internet Directory to store Fusion Applications specific attributes.
-
Create a shadowentries container in Oracle Internet Directory.
Create a
ShadowADContainer.ldiffile with the following details and run it against Oracle Internet Directory using theldapaddcommand.Contents of ShadowADContainer.ldif:
dn: cn=shadowentries cn: shadowentries objectclass: top objectclass: orclContainer
Command:
ldapadd -h idmhost1.mycompany.com -p 3060 -D "cn=orcladmin" -q -c -v -f /tmp/ShadowADContainer.ldifEnsure that the following environment variables are set before using ldapadd:
-
ORACLE_HOME (set to
IDM_BASE/products/dir/oid) -
PATH - The following directory locations should be in the PATH:
ORACLE_HOME/binORACLE_HOME/ldap/binORACLE_HOME/ldap/admin
Output:
add cn: shadowentries add objectclass: top orclContainer adding new entry cn=shadowentries modify complete -
-
Verify if the container is successfully created by accessing ODSM using the URL:
<sso-address>/odsm.If Oracle Internet Directory/Oracle Virtual Directory servers are not listed in the ODSM client, configure them before proceeding to the next step. See Creating ODSM Connections to Oracle Virtual Directory.
-
Grant access to the shadowentries container by creating a
Grant.ldiffile as follows:Contents of
Grant.ldif:dn: cn=shadowentries changetype: modify add: orclaci orclaci: access to entry by group="cn=RealmAdministrators,cn=groups,cn=OracleContext,dc=mycompany,dc=com" (browse,add,delete) orclaci: access to attr=(*) by group="cn=RealmAdministrators,cn=groups,cn=OracleContext,dc=mycompany,dc=com" (read,write,search,compare) orclaci: access to entry by group="cn=OIMAdministrators,cn=Groups,dc=mycompany,dc=com" (browse,add,delete)orclaci: access to attr=(*) by group="cn=OIMAdministrators,cn=Groups,dc=mycompany,dc=com" (search,read,compare,write) - changetype: modify add: orclentrylevelaci orclentrylevelaci: access to entry by * (browse,noadd,nodelete) orclentrylevelaci: access to attr=(*) by * (read,search,nowrite,nocompare)
Command:
ldapadd -h idmhost1.mycompany.com -p 3060 -D "cn=orcladmin" -q -c -v -f /tmp/Grant.ldifOutput:
add orclaci: access to entry by group="cn=RealmAdministrators,cn=groups,cn=OracleContext,dc=mycompany,dc=com" (browse,add,delete) access to attr=(*) by group="cn=RealmAdministrators,cn=groups,cn=OracleContext,dc=mycompany,dc=com" (read,write,search,compare) access to entry by group="cn=OIMAdministrators,cn=Groups,dc=mycompany,dc=com" (browse,add,delete) access to attr=(*) by group="cn=OIMAdministrators,cn=Groups,dc=mycompany,dc=com" (search,read,compare,write)add orclentrylevelaci: access to entry by * (browse,noadd,nodelete) access to attr=(*) by * (read,search,nowrite,nocompare)modifying entry cn=shadowentriesmodify complete
-
Verify the access permissions in Oracle Internet Directory with ODSM using the URL:
<sso-address>/odsm. To verify the settings select the containercn=shadowentriesin the Data Browser and open the Subtree Access tab. The table Content Access Control should display the entries that were created.
16.8.4.1.2 Create a Shadow Joiner Adapter
WARNING: All the ODSM steps should be performed by connecting to Oracle Virtual Directory.
To create a shadow joiner adapter, select the Adapter tab, and then click the Create adapter icon in the left pane.
-
In the New Adapter Wizard window, select the Type tab:
-
In the Adapter drop-down list, select
LDAP. -
In the Adapter Name field, specify
SHADOW4AD1. -
In the Adapter Template drop-down list, select template
User_OID. -
Click Next.
-
-
In the New LDAP Adapter Wizard window:
Connection tab:
-
Click Add Host and specify the Host and Port values. It is recommended to use the same value used for the USER_OID adapter.
-
In the Server Proxy Bind DN field, specify the required value. It is recommended to use the same value used for the USER_OID adapter.
-
In the Proxy Password field, specify the password.
-
Click Next.
Connection Test tab:
-
Verify if the connection is successful and click Next.
Namespace tab:
-
In the Remote Base field, specify
cn=shadowentries. -
In the Mapped Namespace field, specify
cn=shadows. -
Click Next.
Summary tab:
-
Verify the summary details and click Next.
-
-
Verify the created adapter on the left pane, and select it.
-
Review the details of the General tab, and then click the Routing tab.
-
On the Routing tab, from the Visibility drop-down list, select
Internaland click Apply. -
On the
Pluginstab, select User management and click Edit (select User Management and click the pencil icon).-
oamEnabled should be changed from 'false' to 'true'.
-
oimLanguages must be added and set to = 'en'.
-
-
Click Apply.
16.8.4.1.3 Verify Oracle Internet Directory User Adapter and Changelog Adapter
-
Select USER_OID and verify default settings on the General tab.
-
If any changes are required, select the Plug-ins tab and edit User Management (select User Management and click the pencil icon).
-
Select CHANGELOG_OID adapter and verify default settings on the General tab.
-
Select the Plug-ins tab and edit the changelog plugin.
-
In addition to default values, add the following:
-
targetDNFilter=cn=shadowentries -
virtualDITAdapterName=USER_JOIN1;SHADOW4AD1 -
virtualDITAdapterName=USER_OID(if this value is already present, do not make any changes)
-
-
Click OK and Apply.
16.8.4.1.4 Create Active Directory User Adapter
In the Directory Manager, on the Adapter tab, click New Adapter.
-
In the New Adapter Wizard window, on the Type tab:
-
In the Adapter Type drop-down list, select
LDAP. -
In the Adapter Name field, specify
USER_AD. -
In the Adapter Template drop-down list, select
User_ActiveDirectory.
-
-
Click Next.
-
In the New LDAP Adapter Wizard window:
Connection tab:
-
In the DNS Settings area, for the Use DNS for Auto Discovery option, select the No radio button.
-
Click Add Host and specify the Host and Port values. Ensure that the Is Read Only checkbox is selected to ensure no write attempts against the Active Directory.
-
Do not select the Use SSL/TLS checkbox.
-
The SSL Authentication Mode will be read-only and set to No Authentication.
-
In the Server Proxy Bind DN field, specify the required value.
-
In the Proxy Password field, specify the password.
-
Click Next.
Connection Test tab:
-
Verify if the connection is successful and click Next.
Namespace tab:
-
In the Remote Base field, specify
dc=us,dc=mycompany,dc=com. -
In the Mapped Namespace field, specify
dc=adidm,dc=us,dc=mycompany,dc=com. -
Click Next.
Summary tab:
-
Verify the summary details and click Finish.
-
-
Verify and review the details on the General tab.
-
On the Routing tab, from the Visibility drop-down list, select Internal, and click Apply.
-
On the Plug-ins tab, edit User Management and set the following parameter values:
-
oamEnabled=true -
Add
filterObjectClass = oblixOrgPerson,oblixPersonPwdPolicy,OIMPersonPwdPolicy
-
-
Click OK and Apply.
16.8.4.1.5 Create Active Directory Changelog adapter
In the Directory Manager, on the Adapter tab, click New Adapter.
-
In the New Adapter Wizard window, on the Type tab:
-
In the Adapter Type drop-down list, select
LDAP. -
In the Adapter Name field, specify
CHANGELOG_AD. -
In the Adapter Template drop-down list, select
Changelog_ActiveDirectory.
-
-
Click Next.
-
In the New LDAP Adapter Wizard window:
Connection tab:
-
In the DNS Settings area, for the Use DNS for Auto Discovery option, select the No radio button.
-
Click Add Host and specify the Host and Port values. Ensure that the Is Read Only checkbox is selected to ensure no write attempts against the Active Directory.
-
Do not select the Use SSL/TLS checkbox.
-
The SSL Authentication Mode will be read-only and set to No Authentication.
-
In the Server Proxy Bind DN field, specify the required value. It is recommended to use the same value used for the USER_AD adapter.
-
In the Proxy Password field, specify the password.
-
Click Next.
Connection Test tab:
-
Verify if the connection is successful and click Next.
Namespace tab:
-
In the Remote Base field, do not specify any value.
-
In the Mapped Namespace field, specify
cn=changelog. -
Click Next.
Summary tab:
-
Verify the summary details and click Finish.
-
-
Verify and review the details on the General tab.
-
On the Plug-ins tab, edit User Management and set the following parameter values:
-
mapUserState=true -
oamEnabled=true -
targetDNFilter=dc=mycompany,dc=com -
virtualDITAdapterName=USER_JOIN1;USER_AD -
sizeLimit=1000
-
-
Click OK and Apply.
16.8.4.1.6 Create Join Adapter
In the Directory Manager, on the Adapter tab, click New Adapter.
-
In the New Adapter Wizard window, on the Type tab:
-
In the Adapter Type drop-down list, select
Join. -
In the Adapter Name field, specify
USER_JOIN1. -
In the Adapter Template drop-down list, select
Default.
-
-
Click Next.
-
In the New Join Adapter Wizard window:
Settings tab:
-
In the Adapter Suffix/Namespace field, specify
cn=users,dc=adidm,dc=mycompany,dc=com. -
In the Primary Adapter drop-down list, select
USER_AD. -
In the Bind Adapters field, specify
USER_AD. -
Click Next.
Summary tab:
-
Verify the summary details and click Finish.
-
-
Verify and review the details on the General tab. Select the
USER_JOIN1adapter and add join rule. In the Join Rule window:-
In the Joined Adapter drop-down list, select
SHADOW4AD1. -
In the Type drop-down list, select
ShadowJoiner. -
In the Condition field, specify
cn. -
Click OK.
-
-
Click Apply and verify the details.
Before proceeding, review all adapter details on the Home tab.
16.8.4.1.7 Create Global Plugin for virtualmemberof Functionality
-
In ODSM connected to Oracle Virtual Directory, select the Advanced tab, then select global plugins and click Create.
-
In the Plug-in window, specify values as follows:
-
In the Name field, specify
global_virtmember1. -
In the Class field, click Select and select
VirtualMemberOfPluginfrom the list. -
In the Parameters field, add the following values:
-
Name = searchBase, Value = cn=groups,dc=mycompany,dc=com -
Name = adapterName, Value = USER_OID -
Name = explicitrequestonly, Value = false
-
-
In the Namespace field, add
dc=mycompany,dc=com. -
Click Apply. An Internal Server Error may be displayed due to time out.
-
Click OK.
-
16.8.4.1.8 Create Global Plugin for Changelog
-
In ODSM connected to Oracle Virtual Directory, select the Advanced tab, then select global plugins and click Create.
-
In the Plug-in window, specify values as follows:
-
In the Name field, specify
GlobalChangeLogPlugin. -
In the Class field, click Select and select
com.octetstring.vde.chain.plugins.changelog.ConsolidatedChglogPlugin. -
Click Apply. An Internal Server Error is displayed due to timeout.
-
Click OK. Reconnect to Oracle Virtual Directory and then browse the adbase tree.
-
Verify changelog functionality using the following command:
ldapsearch -h idmhost1.mycompany.com -p 6501 -D "cn=orcladmin" -q -b "cn=changelog" -s base "objectclass=*" lastchangenumberThe command should return the following output:
cn=ChangeLoglastChangeNumber=CHANGELOG_AD:1234;CHANGELOG_OID:17890
-
16.8.4.2 Configure the Storable Attributes
Configure the storable attributes to ensure that the Oracle Virtual Directory can correctly route attributes against Active Directory and Oracle Internet Directory and does not store attributes in Active Directory.
-
In ODSM connected to Oracle Virtual Directory, select the Adapter tab, then select SHADOW4AD and click the Routing tab.
-
In the Storable Attributes field, click Add and paste the following attribute values.
orclMTUid orclTimeZone orclDisplayNameLanguagePreference orcldateFormat orclFontSize orclnumberFormat orclPwdExpirationDate orclGenerationQualifier middleName c orclHireDate orclImpersonationGrantee orclAdminPrivilege orclIsEnabled orclFAPartyID orclembeddedHelp orclFATerritory orclAccessibilityMode orclImpersonationGranter orclPwdChangeRequired orclColorContrast orclActiveEndDate orclFAUserID orclMTTenantUName orcltimeFormat orclcurrency orclFAPersonID employeeNumber orclActiveStartDate orclMTTenantGUID orclFALanguage manager
-
Select USER_AD and click the Routing tab.
-
In the Unstorable Attributes field, click Add and paste the attribute values specified in Step 2.
-
Click Apply.
16.8.4.3 Configure Oracle Access Manager and Oracle Identity Manager for Split Profile
This section details the steps required to configure Oracle Access Manager and Oracle Identity Manager for Split Profile.
-
Configure Oracle Identity Management Domain with new settings
-
Verify and Configure OAM to use third-party users as OAM Administrators
-
Update Username Generation Policy to Accommodate Active Directory
-
Change User and Group Search Base for all Oracle Fusion Applications Domains
-
Add Users from Active Directory into Oracle Identity Manager
16.8.4.3.1 Configure Oracle Identity Management Domain with new settings
-
Log in to the Oracle WebLogic Server console as
weblogic_idmand go to Security Realms, and then click myrealm, Providers. -
Click OVDAuthenticator, then select the Provider Specific tab, and then click Lock & Edit.
-
Click Save and then click Activate Changes.
-
Restart Oracle Identity Management, log in to the Oracle WebLogic Server console, and go to Security Realms, myrealm.
-
On the Users tab and Groups tab, verify that the users from Active Directory are also displayed in addition to Oracle Internet Directory.
16.8.4.3.2 Verify and Configure OAM to use third-party users as OAM Administrators
-
Log in to the OAM console, and go to system configuration, common configuration, datasources, user identity stores, OIMIDStore.
-
On the OIMIDStore tab, in the Users and Groups area, delete "
cn=users" and "cn=groups" from the User Search Base and Group Search Base fields. -
Click Apply.
-
In the Access System Administrators area, click the green + to add an OAM Administrator.
-
In the Add System Administrator Roles window, search for and select an Active Directory user.
-
Click Add Selected.
-
Click Apply.
-
On the Oracle Identity Management server, do an ldapsearch for the same user to retrieve DN.
-
Log into ODSM with Oracle Internet Directory, and browse to cn=OAMadministrators under dc=com,dc=mycompany,dc=groups. Click the green + and add the DN.
-
Click Apply.
-
Log in to the OAM console again with the Active Directory user credentials.
16.8.4.3.3 Verify Oracle Identity Manager
-
Log in to the Oracle Identity Manager as xelsysadm (example
https://sso.mycompany.com/oim). -
Click Advanced, Configuration, Resource Management, Manage IT Resource. Ensure that pop-ups are allowed.
-
In the Manage IT Resource window, from the IT Resource Type drop-down list, select
Directory Server. -
Click Search.
-
Ensure that the Search Base and User Reservation Container fields contain the existing Oracle Identity Manager values.
16.8.4.3.4 Update Container Rules in MDS for Split Profile
-
Navigate to the Oracle Identity Manager home's
binfolder. -
In the
weblogic.propertiesfile, set the following three values:wls_servername=wls_oim1 application_name=OIMMetadata metadata_from_loc=/tmp/oimtemp
-
Create the following directory structure: /
tmp/oimtemp/file/and create a file calledLDAPContainerRules.xmlwith following content:<?xml version='1.0' encoding='UTF-8'?> <container-rules> <user> <rule> <expression>Default</expression> <container>cn=Users,dc=mycompany,dc=com</container> <description>UserContainer</description> </rule> </user> <role> <rule> <expression>Default</expression> <container>cn=Groups,dc=mycompany,dc=com</container> <description>RoleContainer</description> </rule> </role> </container-rules>
-
Run the
weblogicImportMetadata.shcommand to import content from the xml file.
16.8.4.3.5 Update Username Generation Policy to Accommodate Active Directory
-
Log in to Oracle Identity Manager, typically
https://sso.mycompany.com/oimas xelsysadm and go to Advanced, Search System Properties, Advanced Search. -
Search for "
Username Generation" and then click on Default policy for username generation. -
In the Value field, update the value from
oracle.iam.identity.usermgmt.impl.plugins.DefaultComboPolicytooracle.iam.identity.usermgmt.impl.plugins.FirstNameLastNamePolicyForAD. -
Click Save.
16.8.4.3.6 Change User and Group Search Base for all Oracle Fusion Applications Domains
-
Ensure all Oracle Fusion Applications components are shut down on the Oracle Fusion Applications node.
-
Do a backup of the Fusion domains structure.
-
Change
user-base-dnandgroup-base-dnin xml files for all domains using the following commands:The
sedcommand does the actual change, the preceding commands are used for verification.cd $APPLICATIONS_CONFIG/domains/<hostname> grep -i "user-base-dn" */config/config.xml grep -i "group-base-dn" */config/config.xml ls -l */config/config.xml sed -i 's/<wls:group-base-dn>cn=Groups,dc=mycompany/<wls:group-base-dn>dc=mycompany/g' */config/config.xml sed -i 's/<wls:user-base-dn>cn=Users,dc=mycompany/<wls:user-base-dn>dc=mycompany/g' */config/config.xml
-
Restart all Oracle Fusion Applications components.
16.8.4.3.7 Add Users from Active Directory into Oracle Identity Manager
-
Log in to Oracle Identity Manager, typically
https://sso.mycompany.com/oim, and go to Advanced, Search Scheduled Jobs, Advanced Search. -
Search for "
LDAP user create" and select LDAP User Create and Update Full Reconciliation to run the job. -
Click Refresh and verify that the job status changes from running to stopped, and execution status is success.
-
Repeat Step 1 to Step 3 for LDAP Role Create and Update Full Reconciliation job.
16.8.4.3.8 Grant Privileges to Active Directory User
-
In Oracle Identity Manager, click Administration, Advanced Search: Users, and search for an Active Directory user.
-
In the displayed search result, select the user and click the Roles tab to review the current roles.
-
Click Assign and select a new role.
-
Verify if the user has the new role assigned. Log in to the Oracle Fusion Applications home page and verify the dashboard.
16.8.5 Set Up Oracle Identity Management Node Manager for SSL
Follow the instructions detailed in this section ONLY for EDG topology and only if the Configure Second application instances option is selected on the Node Topology Configuration Page.
This section contains the following topics:
16.8.5.1 Overview of the Node Manager
Node Manager enables to start and stop the Administration Server and the Managed Servers.
Process
The topologies and hosts are shown in Table 16-1.
Table 16-1 Hosts in Each Topology
| Topology | Hosts |
|---|---|
|
OAM11g/OIM11g |
IDMHOST1 IDMHOST2 |
|
OIF11g |
IDMHOST1 IDMHOST2 |
Note that the procedures in this section must be performed multiple times for each VIP-and-IP pair using the information provided in the component-specific sections.
Recommendations
Oracle provides two main recommendations for Node Manager configuration in enterprise deployment topologies:
-
Oracle recommends placing the Node Manager log file in a location different from the default one (which is inside the Middleware Home where Node Manager resides).
-
Oracle also recommends using host name verification for the communication between Node Manager and the servers in the domain. This requires the use of certificates for the different addresses used in the domain. This section explains the steps for configuring certificates in the hosts for host name verification. See Enable Host Name Verification Certificates for Node Manager.
The passwords used in this guide are used only as examples. Use secure passwords in a production environment. For example, use passwords that consist of random sequences of both uppercase and lowercase characters as well as numbers.
16.8.5.2 Configure Node Manager to Use SSL
By default, provisioning does not configure Node Manager in SSL mode. Configure each node manager in the topology to use SSL.
For each node manager that has its configuration in IDM_CONFIG/nodemanager/hostname, perform the following steps:
Repeat these steps for each node manager.
16.8.5.3 Update Domain to Access Node Manager Using SSL
- Log in to the WebLogic Administration console as the user
weblogic_idm. Console URLs are provided in About Oracle Identity Management Console URLs. - Select IDMDomain, Environment, Machines from the Domain Structure menu.
- Click on Lock and Edit.
- Click on one of the machines, for example idmhost1.mycompany.com.
- Click on the Node Manager tab.
- Change Type from Plain to SSL.
- Click Save.
- Repeat Steps 4-7 for each machine.
- Click Activate Changes.
16.8.5.4 Update Start and Stop Scripts to Use SSL
Update the following files, which are generated by the provisioning tool. Each of these files is located in the directory IDM_CONFIG/scripts/basescripts:
-
stop_nodemanager_template.py -
stop_adminserver_template.py -
start_adminserver_template.py
Do the following for each of the files:
16.8.5.5 Enable Host Name Verification Certificates for Node Manager
This section describes how to set up host name verification certificates for communication between Node Manager and the Administration Server. It consists of the following steps:
16.8.5.5.1 Generate Self-Signed Certificates Using the utils.CertGen Utility
The certificates added in this section (as an example) address a configuration where Node Manager listens on a physical host name (HOST.mycompany.com) and a WebLogic Managed Server listens on a virtual host name (VIP.mycompany.com). Whenever a server is using a virtual host name, it is implied that the server can be migrated from one node to another. Consequently, the directory where keystores and trust keystores are maintained ideally must reside on a shared storage that is accessible from the failover. If additional host names are used in the same or different nodes, the steps in this example must be extended to:
-
Add the required host names to the certificate stores (if they are different from HOST.mycompany.com and VIP.mycompany.com).
-
Change the identity and trust store location information for Node Manager (if the additional host names are used by Node Manager) or for the servers (if the additional host names are used by Managed Servers).
Follow these steps to create self-signed certificates on HOST. These certificates should be created using the network name or alias. The following examples configure certificates for HOST.mycompany.com and VIP.mycompany.com; that is, it is assumed that both a physical host name (HOST) and a virtual host name (VIP) are used in HOST. It is also assumed that HOST.mycompany.com is the address used by Node Manager and VIP.mycompany.com is the address used by a Managed Server or the Administration Server. This is the common situation for nodes hosting an Administration Server and a Fusion Middleware component, or for nodes where two Managed Servers coexist with one server listening on the physical host name and one server using a virtual host name (which is the case for servers that use migration servers).
16.8.5.5.2 Create an Identity Keystore Using the utils.ImportPrivateKey Utility
Follow these steps to create an identity keystore on IDMHOST1:
16.8.5.5.3 Create a Trust Keystore Using the Keytool Utility
Follow these steps to create the trust keystore on each host, for example IDMHOST1 and IDMHOST2:
16.8.5.5.4 Configure Node Manager to Use the Custom Keystores
To configure Node Manager to use the custom keystores, add the following lines to the end of the nodemanager.properties file located in the IDM_CONFIG/nodemanager/hostname directory, where hostname is the name of the host where nodemanager runs:
KeyStores=CustomIdentityAndCustomTrust CustomIdentityKeyStoreFileName=Identity_Keystore CustomIdentityKeyStorePassPhrase=Identity_Keystore_Password CustomIdentityAlias=Identity_Keystore_Alias CustomIdentityPrivateKeyPassPhrase=Private_Key_Used_When_Creating_Certificate
For example:
KeyStores=CustomIdentityAndCustomTrust CustomIdentityKeyStoreFileName=IDM_CONFIG/domains/IDMDomain/keystores/appIdentityKeyStore.jks CustomIdentityKeyStorePassPhrase=Key_Passphrase CustomIdentityAlias=appIdentityIDMHOST1 CustomIdentityPrivateKeyPassPhrase=Key_Passphrase
The passphrase entries in the nodemanager.properties file get encrypted when Node Manager is started, as described in Start and Stop Components. For security reasons, minimize the time the entries in the nodemanager.properties file are left unencrypted. After editing the file, start Node Manager as soon as possible so that the entries get encrypted.
16.8.5.5.5 Configure Managed Oracle WebLogic Servers to Use the Custom Keystores
Follow these steps to configure the identity and trust keystores for WLS_SERVER:
16.8.5.5.6 Change the Host Name Verification Setting for the Managed Servers
Once the previous steps have been performed, set host name verification for the affected Managed Servers to Bea Hostname Verifier. To do this, perform the following steps:
- Log in to Oracle WebLogic Server Administration Console. Console URLs are provided in About Oracle Identity Management Console URLs.
- Select Lock and Edit from the change center.
- Expand the Environment node in the Domain Structure window.
- Click Servers. The Summary of Servers page is displayed.
- Select the Managed Server in the Names column of the table. The settings page for the server is displayed.
- Open the SSL tab.
- Expand the Advanced section of the page.
- Set host name verification to
Bea Hostname Verifier. - Click Save.
- Click Activate Changes.
16.8.5.6 Update boot.properties Files
Each managed server has a boot.properties file which is created as part of the process described in previous sections. In order to start managed servers using the provisioning start script, update each of these files and comment out following line:
TrustKeyStore=DemoTrust
After finishing updating the file, the line should look like this:
#TrustKeyStore=DemoTrust
The files that must be updated are:
IDM_CONFIG/domains/IDMDomain/servers/AdminServer/security/boot.properties
and each Managed Server boot.properties file. These have path names of the form:
IDM_CONFIG/domains/IDMDomain/servers/servername/security/boot.properties
and
IDM_CONFIG/domains/IDMDomain/servers/AdminServer/data/nodemanager/boot.properties
16.8.5.7 Start Node Manager
Verify that Node Manager is using the appropriate stores and alias from the Node Manager output. The following should be seen when Node Manager starts.:
<Loading identity key store:
FileName=IDM_CONFIG/domains/IDMDomain/keystores/appIdentityKeyStore.jks, Type=jks, PassPhraseUsed=true>
Host name verification works if a test configuration change is applied to the servers and it succeeds without Node Manager reporting any SSL errors.
16.9 Install and Configure Oracle Business Intelligence Applications
Oracle Business Intelligence Applications consists of pre-built metadata, dashboards, analyses, and ETL tools that provide insight into the organization's historical data. The Oracle Business Intelligence Applications software binaries are installed during Oracle Fusion Applications installation and provisioning in the Oracle Home for Business Intelligence. Set up the Oracle Business Intelligence Applications components before using them. See Installing and Setting Up Oracle BI Applications in the Oracle Business Intelligence Applications Installation Guide.
16.10 Configure Oracle Transactional Business Intelligence
After installing Oracle Fusion Transactional Business Intelligence, configure it to obtain real-time analysis of the organization's day-to-day operational data. For information on setting up accounting segment, modeling Essbase cubes, and setting up Descriptive Flexfields see the Oracle Fusion Transactional Business Intelligence Administrator's Guide.
16.11 Set Up Report Delivery Servers
Oracle Business Intelligence Publisher is the report generation and delivery engine for Oracle Fusion Applications. Oracle BI Publisher receives report requests from Oracle Fusion Applications in the following ways:
-
Through Oracle Enterprise Scheduler
-
Through the Reports and Analytics pane
-
From an application page
Requests submitted through Oracle Enterprise Scheduler are processed by the Oracle BI Publisher scheduler. Requests submitted through the Reports and Analytics pane can be either real-time online requests or scheduled requests. Requests submitted through an application may invoke Oracle Enterprise Scheduler or may return report request results directly back to the application page.
After installing Oracle Fusion Applications, Oracle BI Publisher is configured to accept requests from Oracle Fusion Applications. However, before delivering report documents to their destinations, define the delivery servers in Oracle BI Publisher. Use the Oracle BI Publisher Administration page to define the delivery servers.
After setup, configure the number of report processor and delivery threads to best handle the processing and delivery requirements. In addition, configure report properties for the system or at the report level to tune performance of the reports. To diagnose report processing issues, BI Publisher provides a set of scheduler diagnostics.
16.11.1 Navigate to the Oracle BI Publisher Administration Page
Use the Oracle BI Publisher Administration page to:
-
Configure delivery servers
-
Manage report and delivery processors
-
View scheduler diagnostics
-
Set system properties and report runtime configuration properties
The BIAdministrator role is necessary to access the BI Publisher Administration page.
To navigate to the Oracle BI Publisher Administration page:
-
From the Oracle Fusion Applications Navigator, under Tools, click Reports and Analytics. In the Reports and Analytics pane, click Catalog to display the Oracle Business Intelligence presentation catalog page. From here, click Administration and then click Manage BI Publisher.
-
Alternatively, log in to Oracle Business Intelligence directly (example:
http://example.com:port/analytics). Click Administration and then click Manage BI Publisher.
Figure 16-2 shows the BI Publisher Administration page:
Figure 16-2 BI Publisher Administration Page
16.11.2 Configure Report Delivery Servers
To configure delivery servers:
The following table lists the report delivery channels supported by Oracle BI Publisher. See Setting Up Delivery Destinations in the Oracle Fusion Middleware Administrator's Guide for Oracle Business Intelligence Publisher (Oracle Fusion Applications Edition) for configuration information.
| Delivery Type | Section |
|---|---|
|
Printer and Fax |
|
|
|
|
|
WebDAV |
|
|
HTTP |
|
|
FTP |
Note that printing is supported through Internet Printing Protocol (IPP). If Oracle BI Publisher is operating in a UNIX environment, set up the Common UNIX Printing Service (CUPS) and then define the CUPS server to Oracle BI Publisher. For information on setting up CUPS and Windows IPP, see Setting Up a Printer in the Oracle Fusion Middleware Administrator's Guide for Oracle Business Intelligence Publisher (Oracle Fusion Applications Edition).
16.12 Configure Oracle Data Integrator Studio
Configuring Oracle Data Integrator Studio for external authentication is necessary to prevent any unauthorized access. The access credentials are stored in a configuration file. To make the external configuration work, the jps configuration file (jps-config.xml) must be configured and placed in the prescribed directory where the application is installed.
Prerequisites
-
Select the Developer Installation options on the Select Installation Type page:
-
ODI Studio (with local agent)
-
ODI SDK
-
-
Skip Repository Configuration on the Repository Configuration page
MANDATORY: Oracle Data Integrator Studio must be installed in a separate Oracle home other than Oracle Fusion Middleware Oracle homes and Oracle Fusion Applications Oracle home.
For more information about installing Oracle Data Integrator, see Preparing to Install and Configure Oracle Data Integrator in the Fusion Middleware Installing and Configuring Oracle Data Integrator.
16.13 Set Up the Oracle Business Intelligence Administration Tool
Oracle Business Intelligence Administration Tool is a part of the Oracle Business Intelligence Client Tools and is packaged along with the Oracle Business Intelligence Applications. It enables to manage the metadata repository and is required for certain steps in the Oracle Business Intelligence Applications setup process. For more information about setting up the Oracle Business Intelligence Administration Tool, see Installing and Setting Up Oracle BI Applications in the Oracle Business Intelligence Applications Installation Guide
16.14 Perform Optional Language Installations
This section describes how to install a language other than US English, using Language Pack Installer. See Select Languages for a list of available languages.
A language pack for a given language and release contains artifacts at the specific release level that are translated to the specific language. Translated artifacts include Oracle Fusion Applications seed data that is uploaded into Oracle Fusion Applications database, SOA resource bundles, JEE resource bundles, LDAP data, Diagnostics Test Framework, and BI Presentation Catalog data. Install language packs with Language Pack Installer.
This section includes the following topics:
16.14.1 Pre-Installation Steps - Before Down Time
This section describes the preparation steps for installing a language pack, all of which can be performed before the scheduled down time.
16.14.1.1 Before Beginning
Follow the steps in this section before beginning the language pack installation.
- Ensure there is access to the Oracle Fusion Applications NLS release notes from the current release.
- Ensure that the steps in Download Language Pack Software have been followed.
16.14.1.2 Confirm the Oracle Fusion Applications Installation is Complete
Ensure that all tasks described in Complete Mandatory Common Post-Installation Tasks have been followed.
If a language pack is being installed on an upgraded environment, ensure to complete that all tasks described in Run Post-Upgrade Tasks in the Oracle Fusion Applications Upgrade Guide.
In either case, perform also the steps in Post-Installation in the Technical Known Issues, Oracle Fusion Applications Release 12 document.
16.14.1.3 Maintain Versions of Customized BI Publisher Reports
If a language pack is installed immediately after the Oracle Fusion Applications installation, skip this step.
If a language pack is installed at a later stage, ensure to have the versions of any customized BI Publisher reports. If a language pack includes an update to a catalog object that was delivered with an Oracle Fusion application, the update overwrites any customizations applied to the original report.
16.14.1.4 Run Health Checker for Pre-Down Time Checks
Run Health Checker directly from APPLICATIONS_BASE and from the primordial host. Run these checks any number of times prior to the down time. For information about the checks that Health Checker runs, see Language Pack Readiness Health Checks in the Oracle Fusion Applications Upgrade Guide.
Perform the following steps to run Health Checker:
If any health checks fail, refer to the Health Checker log files and reports to find the corrective actions to resolve the issue. The suggested corrective actions must be run manually to fix the issue before proceeding with the upgrade. Then rerun Health Checker to ensure all checks are successful. Optionally, use the -checkpoint true option when Health Checker is restarted, so that only the failed plug-ins or the plug-ins that did not run are executed.
Review the Health Checker log file or the HTML summary report to see if any errors occurred that require corrective action. The log file and the HTML summary are located in APPLICATIONS_CONFIG/lcm/logs/release_version/healthchecker.
16.14.2 Pre-Installation Steps - During Down Time
This section describes the mandatory preparation steps for installing a language pack, all of which must be performed during the system down time. Language Pack Installer does not require any servers to be shut down. However, no users should be online, so it is still considered to be down time.
16.14.2.1 Run Health Checker for General System Health Checks
Run Health Checker directly from APPLICATIONS_BASE and from the primordial host. For information about the checks that Health Checker runs, see General System Health Checks in the Oracle Fusion Applications Upgrade Guide.
Perform the following steps to run Health Checker:
If any health checks fail, refer to the Health Checker log files and reports to find the corrective actions to resolve the issue. The suggested corrective actions must be run manually to fix the issue before proceeding with the upgrade. Then rerun Health Checker to ensure all checks are successful. Optionally, use the -checkpoint true option when Health Checker is restarted, so that only the failed plug-ins or the plug-ins that did not run are executed.
Review the Health Checker log file or the HTML summary report to see if any errors occurred that require corrective action. The log file and the HTML summary are located in APPLICATIONS_CONFIG/lcm/logs/release_version/healthchecker.
16.14.2.2 Back Up Oracle Fusion Applications
Back up the entire Oracle Fusion Applications environment by following the steps in Back Up and Recover Oracle Fusion Applications in the Oracle Fusion Applications Administrator's Guide. You should also back up your central inventory.
16.14.2.3 Apply Mandatory Prerequisite Patches
Apply any patches listed in Post-Installation in the Oracle Fusion Applications release notes that might have been downloaded in Download Language Pack Software.
16.14.3 Install a Language
Language Pack Installer does not require any servers to be shut down. However, no users should be online, so it is still considered to be down time. Oracle recommends that language packs be installed from a machine that is co-located in the same subnetwork as the database server to maximize performance. Language Pack Installer must be run on the primordial host.
Ensure that the steps in Pre-Installation Steps - Before Down Time and Pre-Installation Steps - During Down Time are successfully completed before starting Language Pack Installer.
The policy store can maintain attributes in only one language. To override the base English strings in the policy store, set the -DupdateJAZNPolicyStore option to true when the Language Pack is installed. The Description and Displayname are the two attributes which are translatable and are loaded in JAZN files in the Language Pack.
Language Pack Installer supports silent mode and GUI mode. In silent mode, Language Pack Installer reports the progress of the installation as console output. In GUI mode, navigate through screens that display the progress of the installation, including log file locations and status messages.
16.14.3.1 Run Language Pack Installer in Silent Mode
Perform the following steps to start Language Pack Installer in silent mode from the command line, using specific options to further define the necessary actions. Language Pack Installer must be run from the primordial host.
16.14.3.2 Run Language Pack Installer in GUI Mode
Perform the following steps to run Language Pack Installer in GUI mode from the command line, using specific options to further define the necessary actions. Language Pack Installer must be run from the primordial host.
If Language Pack Installer encounters errors, refer to Troubleshoot Language Pack Installer Sessions before clicking any buttons in the Language Pack Installer user interface.
Example 16-1 Language Pack Installation with no policy store translation
UNIX: $REPOSITORY_LOCATION/installers/fusionapps/Disk1/runInstaller -addLangs -jreLoc APPLICATIONS_BASE/fusionapps/jdk -invPtrLoc FA_ORACLE_HOME/oraInst.loc -noCheckForUpdates OR -updatesDir installer_patch_directory
Example 16-2 Language Pack Installation with policy store translation
UNIX: $REPOSITORY_LOCATION/installers/fusionapps/Disk1/runInstaller -addLangs -jreLoc APPLICATIONS_BASE/fusionapps/jdk -invPtrLoc FA_ORACLE_HOME/oraInst.loc -DupdateJAZNPolicyStore=true -noCheckForUpdates OR -updatesDir installer_patch_directory
Example 16-3 Language Pack installation when FA_ORACLE_HOME is registered with a /net path
UNIX: $REPOSITORY_LOCATION/installers/fusionapps/Disk1/runInstaller -addLangs -jreLoc APPLICATIONS_BASE/fusionapps/jdk -invPtrLoc /net/APPLICATIONS_BASE/fusionapps/applications/oraInst.loc -noCheckForUpdates OR -updatesDir installer_patch_directory
16.14.3.2.1 Installer User Interface
Language Pack Installer provides a graphical user interface which allows to control the behavior of the installer by the use of buttons, in cases where it encounters a failure. Note that the behavior of these buttons may vary, depending on whether it is a configuration assistant, or a step within a configuration assistant, that fails. The behavior also depends on whether a configuration assistant is mandatory. All mandatory configuration assistants must complete successfully before proceeding to the next configuration assistant. For information about which configuration assistants are mandatory, see Language Pack Installer Configuration Assistants.
Exit out of the installer in the event of a failure and restart from the point of failure. If a non-mandatory configuration assistant fails, and the next configuration assistant continues, restart the installer after it finishes the last configuration assistant. When restarting, the installer retries all failed configuration assistants and steps.
An explanation of the usage of each button follows. Note that the buttons are available only in GUI mode, not in silent mode.
-
Abort Button
The Abort button allows to skip a failed configuration assistant or step within a configuration assistant, and records the failure so it can be rerun when the installation is restarted. For mandatory configuration assistants, after aborting the configuration assistant, the installer does not proceed and only the Cancel button is enabled. Resolve the cause of the failure and start the installer from this failure point. For non-mandatory configuration assistants, the installer proceeds to the next configuration assistant after aborting the configuration assistant. This button is enabled only after a failure.
-
Cancel Button
The Cancel button allows to stop an installer session after the failure of a mandatory action. This button is enabled only after a failure.
-
Close Button
The Windows Close button allows to stop an installer session after a failure. This is enabled only after a failure.
-
Continue Button
The Continue button allows to skip a failed non-mandatory step within any configuration assistant. The installer records the failure and then proceeds with the next step within the configuration assistant. When this installer session is rerun, the failed steps within the configuration assistant are attempted again.
Note that this button is enabled only for non-mandatory steps within a configuration assistant.
-
Next Button
The Next button allows to proceed to the next screen. This button is enabled only when all configuration assistants complete successfully in the current screen.
-
Retry Button
The Retry button allows to attempt to rerun a failed configuration assistant, or a step within a configuration assistant. Use Retry when the cause of the failure is identified the issue can be resolved during the current Language Pack Installer session.
16.14.4 Complete the Post-Installation Tasks
Perform the following required manual steps after Language Pack Installer completes successfully:
16.14.4.1 Confirm Database Artifact Deployments Were Successful
Confirm that all database artifact deployments were successful by reviewing the Diagnostics report and log files. See Diagnostics Report in the Oracle Fusion Applications Patching Guide.
16.14.4.2 Review Log Files for Errors or Exceptions
Confirm there are no unresolved errors or exceptions in the log files. For information about resolving errors, see Troubleshoot Language Pack Installer Sessions.
16.14.4.3 Run Health Checker for Post Installation Checks
Run Health Checker to perform post installation checks directly from APPLICATIONS_BASE and from the primordial host by performing the following steps. For information about the checks that Health Checker runs, see Post-Upgrade Tasks Performed by Health Checker in the Oracle Fusion Applications Upgrade Guide.
If any health checks fail, refer to the Health Checker log files and reports to find the corrective actions to resolve the issue. The suggested corrective actions must be run manually to fix the issue before proceeding with the upgrade. Then rerun Health Checker to ensure all checks are successful. Optionally, use the -checkpoint true option when Health Checker is restarted, so that only the failed plug-ins or the plug-ins that did not run are executed.
Review the Health Checker log file or the HTML summary report to see if any errors occurred that require corrective action. The log file and the HTML summary are located in APPLICATIONS_CONFIG/lcm/logs/release_version/healthchecker.
If the JAZN Conflicts check fails, refer to Resolve JAZN Conflicts Found by Health Checker.
16.14.4.5 Reload Custom Templates for BI Publisher Reports
Follow this step if you have customized BI Publisher reports.
Reload custom templates for BI Publisher reports on Oracle-delivered BI Publisher reports.
16.14.5 Troubleshoot Language Pack Installer Sessions
This section the following topics related to troubleshooting Language Pack Installer sessions.
16.14.5.1 Log Directories for Language Pack Installer Tasks
The following table provides a list of log directories for Language Pack Installer tasks.
Table 16-5 Log Directories for Language Pack Installer Activities
| Log directory name | Description |
|---|---|
|
|
Installation phase logs |
|
APPLICATIONS_CONFIG/lcm/logs/11.1.11.x.0/LanguagePack/language |
Top level directory for Language Pack Installer logs |
|
APPLICATIONS_CONFIG/lcm/logs/11.1.11.x.0/LanguagePack/language/configlogs |
Top level log directory for configuration assistants. A log file exists for each configuration assistant. |
|
APPLICATIONS_CONFIG/lcm/logs/11.1.11.x.0/LanguagePack/language/PatchManager_DBPatch |
Log directory for the Loading Database Components configuration assistant |
|
APPLICATIONS_CONFIG/lcm/logs/11.1.11.x.0/LanguagePack/language/PatchManager_ActivateLanguage |
Log directory for the Activate Language configuration assistant |
|
APPLICATIONS_CONFIG/lcm/logs/11.1.11.x.0/LanguagePack/language/soalogs |
Log files from SOA Composite activities Note that SOA server logs are located under respective domains. For example, the SOA server logs for Common Domain are under |
16.14.5.2 Troubleshoot Failures During the Installation Phase
For information regarding troubleshooting failures during the language pack installation phase, see Troubleshoot Other Potential Issues During the Upgrade in the Oracle Fusion Applications Upgrade Guide.
16.14.5.3 Language Pack Installer Configuration Assistants
During the installation phase, Language Pack Installer copies all files from the language pack to the appropriate locations, such as Oracle Fusion Middleware home and Oracle Fusion Applications Oracle home. After the file copy is completed, Language Pack Installer calls configuration assistants to perform the remaining tasks required to update and deploy the artifacts included in the language pack. Language Pack Installer supports parallel processing of certain configuration assistants to improve performance. Parallel configuration assistants are organized by groups and all configuration assistants in a group start running at the same time. The installer proceeds to the next configuration assistant outside of the group, only after all parallel tasks in a group complete successfully.
All mandatory configuration assistants must complete successfully before proceeding to the next configuration assistant. See General Troubleshooting During the Configuration Phase in Silent Mode and General Troubleshooting During the Configuration Phase in GUI Mode.
The following table provides a list of possible configuration assistants, including steps within the configuration assistants. The Retry Behavior and Troubleshooting column describes what Language Pack Installer does after a configuration assistant fails and the Retry button is selected or Language Pack Installer is restarted in silent mode. If available, links are provided to relevant troubleshooting sections.
Table 16-6 Configuration Assistants Run by Language Pack Installer
| Name | Mandatory | Description | Retry Behavior and Troubleshooting |
|---|---|---|---|
|
Activate Language |
Yes |
Activates the language in the database. |
Runs Activate Language again. |
|
Preverification |
Yes |
Performs the following validation checks:
|
Runs failed steps. |
|
Synchronize Multilingual Tables |
Yes |
Runs the Maintain Multilingual Tables utility to maintain the tables related to the newly activated language. See Maintaining Multi-lingual Tables in the Oracle Fusion Applications Patching Guide. |
Restart from failure. |
|
Apply Middleware Language Patches |
Yes |
|
Applies the failed patches. See Troubleshoot Applying Middleware Patches in the Oracle Fusion Applications Upgrade Guide. |
|
Load Database Components |
Yes |
Uploads the database content packaged in the language pack to the database. |
Runs failed database commands. See Troubleshoot Loading Database Components in the Oracle Fusion Applications Upgrade Guide. |
|
Update Language Release Information |
Yes |
Updates the language release information in the |
Starts from the beginning of the task. |
|
Deploy Applications Policies (jazn-data.xml) |
Yes |
Performs the deployment of the updated applications policies, based on the selections during the Policy Store Analysis task. This task runs only in case of choosing to override the base English strings in the policy store by using the |
Deploys the failed stripes. See Troubleshooting Deployment of Applications Policies in the Oracle Fusion Applications Upgrade Guide. |
|
Deploy BI Publisher Artifacts |
Yes |
Using Catalog Manager, deploys BI Publisher artifacts.: |
Starts from the beginning of the task. See Troubleshooting Deployment of BI Publisher Artifacts. |
|
Deploy Flexfields |
No |
Deploys flexfields to the domain that hosts the |
Starts from the beginning of the task. |
|
Deploy LDAP Data (LDIF) |
Yes |
Uploads LDIF XLIFF translations to the identity store |
Retries failed XLIFF files. |
|
Deploy SOA Resource Bundles |
Yes |
Deploys SOA Resource Bundles to the corresponding SOA servers. |
Deploys failed SOA resource bundles. |
|
Activate SOA Language |
Yes |
Runs the SOA Human Workflow configuration script to activate the language of the language pack. |
Starts from the beginning of the task. |
16.14.5.4 General Troubleshooting During the Configuration Phase in Silent Mode
The installer can be restarted to rerun all failed configuration tasks as well as those tasks that were not started from the previous session. When a mandatory configuration task or step fails in silent mode, the installer exits. After resolving the issue that caused the failure, restart the installer using the same command used to start it. When the installer restarts, it restarts from the first failed task.
If any non-mandatory tasks fail in silent mode, the installer continues with the next configuration task and does not exit. Review the logs to find any non-mandatory tasks that failed and then rerun the installer until all tasks complete successfully.
If the installer is run in GUI mode, start it from the REPOSITORY_LOCATION/installers/fusionapps/Disk1 directory.
16.14.5.5 General Troubleshooting During the Configuration Phase in GUI Mode
This section describes the following troubleshooting scenarios:
16.14.5.5.1 Restart a Failed Installer Session
The installer can be restarted to rerun all failed configuration assistants as well as those configuration assistants that were not started from the previous session. When a configuration assistant or step fails, the Configuration Progress screen displays the location of the log file and the exception that caused the failure. View the content of the log files that appear at the bottom of the screen to obtain detailed information to assist in diagnosing the cause of the failure.
If one or more failures occur during the configuration phase, after the final configuration assistant is complete, the following message displays:
Configuration is completed with errors, exit the installer by clicking the 'Cancel' button and retry the failed configurations.
Perform the following steps to rerun the installer and retry the failed configuration assistants:
- Click Cancel to exit the installer.
- Resolve the issues that caused the failure.
- Start the installer using the same command syntax used for the previous incomplete installation.
- A pop up dialog displays, asking to continue or not the previous incomplete installation. Select Yes to continue running the previous session. If No is selected, the installer starts from the beginning and it fails, indicating that a release cannot be installed again in the same environment. Restore then from the backup and restart the installer.
- The Configuration Progress screen displays only the failed and remaining configuration assistants, and then runs these configuration assistants.
- Assuming all configuration assistants complete successfully, click Next to go to the Installation Complete screen and then click Finish to end the session. If a configuration assistant fails again and to attempt to run the session again, click Cancel to save the session. If all configuration assistants completed successfully, click Finish to end the session.
16.14.5.5.2 Troubleshoot Failures While Parallel Tasks Are Running
If one or more tasks in a group fail, select the failed tasks in any combination, and the Abort, Retry, and Continue buttons are enabled as appropriate for the selected tasks. For example, if two tasks in a group fail, and the first task allows to select Continue, but the other task does not, then the Continue button is not enabled if both tasks are selected.
Process one or more failed tasks at a time. For example, if three tasks fail, retry one of them, and abort the second task while it is running. Then, retry the third task. When the first and third tasks finish processing, the next step depends on whether the second task is mandatory. If it is a mandatory task, the installer stops, and if it is non-mandatory the installer continues with the next task after the group. It is also possible to pick two out of three or all three tasks and select Retry, Abort, or Continue, based on which buttons are enabled.
Note that all tasks in a group must either fail or complete successfully before the Cancel button is enabled.
16.14.5.5.3 The Next Button Is Not Enabled During Configuration Assistants
Problem
On the Configuration Progress page of the installer, the Next button is enabled only when all configuration assistants are successful.
If all the configuration assistants are complete, and the Next button is not enabled, then a configuration failure has been encountered and continued to the next configuration assistant.
Solution
In this case, retry the failed configuration assistants by following these steps:
- On the Configuration Progress page of the installer, click Cancel.
- Restart the installer. All failed configuration assistants or steps rerun upon restart. See Restart a Failed Installer Session.
As long as a configuration assistant is not successful, the Next button remains disabled. It may be necessary to repeat the cancel and retry procedure until all configuration assistants are successful.
16.14.5.5.4 The OPSS Security Store Goes Down While the Installer is Running
Problem
The OPSS Security Store goes down while the installer is running.
Solution
Configuration tasks that are related to the OPSS Security Store fail if the store goes down. Perform the following steps to recover:
- Abort the failed configuration task.
- Select Cancel to end the installer session.
- Start the OPSS Security Store. See Start Oracle Internet Directory in the Oracle Fusion Applications Upgrade Guide.
- Start a new installer session. The installer resumes with the remaining tasks because Cancel is selected, which saves the session.
16.14.5.5.5 Failure During Opening of Wallet Based Credential Store
Problem
The following error occurs during the configuration phase.
Reason:oracle.security.jps.service.credstore.CredStoreException: JPS-01050: Opening of wallet based credential store failed. Reason java.io.IO Exception: PKI-02002: Unable to open the wallet. Check password.
Solution
After resolving the cause of the failure, cancel the installation and then restart the installer.
16.14.5.5.6 Error While Loading Database Components in GUI Mode
Problem
Language Pack Installer reports that one or more database workers failed during the Loading Database Components configuration assistant.
Solution
Use AD Controller to manage the failed workers. After resolving the issue that caused the workers to fail and restarting the failed worker, click OK in the dialog box and Language Pack Installer continues processing. See Troubleshoot Patching Sessions for Database Content in the Oracle Fusion Applications Patching Guide.
16.14.5.6 Recover From a Language Pack Installer Session That Was Shut Down
Problem
A Language Pack Installer session was shut down during the upgrade.
Solution
If tasks spawned by Language Pack Installer are killed in the middle of any process, the system may not be in a recoverable state and the state should be carefully reviewed by Oracle Support before proceeding.To recover from this situation, restore the backup of APPLICATIONS_BASE and start from the beginning of the language pack installation.
16.14.5.7 Troubleshoot Applying Middleware Patches
For information about troubleshooting a failure that occurs during the Applying Middleware Patches configuration assistant, see Troubleshoot Applying Middleware Patches in the Oracle Fusion Applications Upgrade Guide.
16.14.5.8 Troubleshoot Loading Database Components
For information about troubleshooting a failure that occurs during the Loading Database Components configuration assistant, see Troubleshoot Loading Database Components in the Oracle Fusion Applications Upgrade Guide.
16.14.5.9 Troubleshoot Deployment of Applications Policies
For information about troubleshooting failures during the Deployment of Applications Policies configuration assistant, see Troubleshooting Deployment of Applications Policies in the Oracle Fusion Applications Upgrade Guide.
16.14.5.10 Troubleshoot Deployment of BI Publisher Artifacts
Problem
The following error occurs if the BI Presentation servers are running during the deployment of BI Publisher artifacts:
java.lang.RuntimeException: Webcat patch file creation failed!
Solution
If the language pack contains BI Publisher artifacts, the BI Presentation servers must not be running. To resolve this issue, shut down the BI Presentation servers to release locks on the Oracle BI Presentation Catalog. See fastartstop Syntax in the Oracle Fusion Applications Administrator's Guide.
16.14.5.11 Resolve JAZN Conflicts Found by Health Checker
This step is performed by Health Checker only if the -DupdateJAZNPolicyStore option is set to true.
Health Checker checks the JAZN Analysis reports for potential conflicts and deletions that are not patched automatically by Language Pack Installer.
16.14.5.12 Installer Requirement Checks Fail
Problem
The installer fails with the following type of errors:
Starting Oracle Universal Installer... Checking if CPU speed is above 300 MHz. Checking Temp space: must be greater than 4096 MB. Actual 9177 MB Passed Checking swap space: 3915 MB available, 4000 MB required. Failed <<<< Some requirement checks failed. You must fulfill these requirements before continuing with the installation,
Solution
Manually increase the requirement check that failed, in this example, the swap space. Then restart Language Pack Installer.
16.14.5.13 Language Pack Installer Fails Due To Thread Calls
Problem
Language Installer fails due to thread calls and reports errors similar to the following example:
"Thread-11" id=29 idx=0x98 tid=25751 prio=5 alive, native_blocked
at java/io/UnixFileSystem.getBooleanAttributes0(Ljava/io/File;)I(Native
Method)
at java/io/UnixFileSystem.getBooleanAttributes(UnixFileSystem.java:228)
at java/io/File.exists(File.java:733)
Solution
Restart Language Pack Installer.
16.15 Set Up Segregation of Duties
When a role assignment is requested through Oracle Identity Management, it needs to check with the Application Access Controls Governor to see if there are any segregation of duties (SOD) violations. If Application Access Controls Governor reports any SOD violations, depending on the violation or access issues, Oracle Identity Manager needs to send the request for an approval to specific roles, automatically approve the request, or reject the request.
16.15.1 Set Up SOD
To set up SOD, complete the following procedures.
-
Ensure that the following configuration requirements are met:
-
Set up an Application Access Controls Governor server
-
Set up the Oracle Fusion connector
-
Define a data source
-
Update the Application Access Controls Governor server details in Identity Manager
Perform all the setup tasks only from the Identity Manager domain.
-
-
To manually switch from Oracle Identity Management to Lightweight Directory Access Protocol (LDAP) as the source of user roles for Service-Oriented Architecture (SOA) server deployed with Identity Manager, perform the following configuration steps.
This step is applicable only to the environments set up with Oracle Identity Management and Oracle Access Management integration, and LDAP synchronization of users and roles enabled in Oracle Identity Manager.
-
Log in to the Enterprise Manager Console as a Weblogic_Administrator user.
-
Access the Weblogic Domain in which Identity Manager is configured.
-
Open the Security - Realms page.
-
On the Providers tab of the Security - Realms page, open OIDAuthenticator.
-
In the provider specific parameters for
OIDAuthenticator, update the Oracle Virtual Directory port with the Oracle Internet Directory port by changing the value of the port from Oracle Virtual Directory port to Oracle Internet Directory port. -
On the Providers tab of the security realm settings page, create a new authentication provider with the name OIMSignatureAuthenticationProvider and the type OIMSignatureAuthenticationProvider.
-
Configure
OIMSignatureAuthenticationProviderwith the following parameters:DBDriver: oracle.jdbc.OracleDriveDBUrl: jdbc:oracle:thin:@<db_hostname>:<db_port>:<db_sid>.For example, jdbc:oracle:thin:@localhost:5521:iam4.PKIKeystore Provider: sun.security.rsa.SunRsaSignSymmetric Key Keystore Provider: com.sun.crypto.provider.SunJCEDBUser: the Identity Manager database schema user nameDBPassword: the Identity Manager database schema user passwordThese parameters as same as in
OIMAuthenticationProvider. -
Delete the existing
OIMSignatureAuthenticator. -
Reorder authentication providers into the following sequence:
OAMIDAsserter
OIMSignatureAuthenticationProvider
OIMAuthenticationProvider
OIDAuthenticator
DefaultAuthenticator
DefaultIdentityAsserter
IDMDomainAgent
-
Disable the Weblogic user profile in Identity Manager.
This user profile must be disabled to avoid the authentication errors at Identity Manager Authenticator level, as Identity Manager Authenticator is now placed ahead of the Default Authenticator in authentication provider ordering. However, the user profile cannot be disabled from Identity Manager Administration page. Instead, run the following SQL scripts on the OIM database.
update usr set usr_status='Disabled' where usr_login='WEBLOGIC';update usr set usr_disabled=1 where usr_login='WEBLOGIC'; -
Create the Weblogic user profile in LDAP and add it to the Administrators role. If the Administrators role does not exist in LDAP, create it first and then add the Weblogic user profile to it.
A user can be created in LDAP by creating an LDAP Data Interchange Format (LDIF) file and using the ldapadd command.
-
In the jps-config.xml file, locate the element group
<jpsContext name="default">. -
Under
<jpsContext name="default">, locate the identity store element<serviceInstanceRef ref="idstore.oim"/>, replace its value withidstore.ldapand save the file. -
Restart all servers in the domain, including the Administration Server.
-
-
Administer role memberships using the Delegated Administration tasks in Oracle Identity Manager. To apply SOD checks on these administrative actions, configure the following Identity Manager system properties.
-
Set
XL.RM_REQUEST_ENABLEDtoTRUE -
Set
XL.RM_ROLE_ASSIGN_TEMPLATEtoASSIGN ROLES WITH CALLBACK POLICY
-
16.15.2 Turn Off SOD Checks
To turn off the SOD checks, do the following.
-
Log in as an Administrator to the Enterprise Manager application for Oracle Identity Manager server.
-
Navigate to the system MBean browser for the Identity Manager server.
-
Locate
OAACGConfig MBeanoption. -
Set the property
SODEnabledtoFalseand save. -
Log in to the Identity Manager's advanced console and set the system property
XL.RM_REQUEST_ENABLEDtoFalse. -
Restart the Identity Manager server.
To turn on the SOD checks, set the properties SODEnabled and XL.RM_REQUEST_ENABLED to True.
16.15.3 Modify the Segregation of Duties Routing Policies for Approving Role Provisioning: Procedures
When an access control necessitates an approval, the predefined routing rules determine the approver for a role provisioning request. These rules are defined in the OAACGRoleAssignSODCheck composite because of Approval Management Extensions (AMX) functionality such as Supervisory List.
The following rules are used to route the request to the suitable role.
-
If the requested role assignment is of Chief Financial Officer, SOD remediation task is assigned to the IT Security Manager role.
-
If SOD violation occurs because of a policy where the SOD control perspective is Business Process - Information Technology Management and the control priority is 1, SOD remediation task is assigned to the Application Administrator role.
-
If SOD violation occurs for any other reason (Catch All rule), SOD remediation task is assigned to the Controller role.
To modify these routing rules, do it in two ways:
-
Using Oracle SOA Composer
-
Using JDeveloper
16.15.4 Modify Rules Using Oracle SOA Composer
Use the Oracle SOA Composer associated with the SOA server used by Oracle Identity Management, and change the RemediationRules ruleset associated with OAACGRoleAssignSODCheck composite. For instance, to shift the task assignment in the Catch All rule from the Controller role to a different role.
-
Log in to the Oracle SOA Composer.
-
Click Open - Open Task.
-
Select OAACGRoleAssignSODCheck and click Open.
-
On the ApprovalTaskRules.rules tab, click Edit.
-
Expand Catch All and in the THEN statement, replace
GL_CONTROLLER_JOBwith the new role. -
Save the changes.
16.15.5 Modify Rules Using JDeveloper
Modifications can be made directly to the configuration file available within OAACGRoleAssignSODCheck.zip.
To perform this task, administrative privileges or the role of an Administrator are necessary.
-
Go to IDM_BASE/products/app/oim
/server/workflows/composites/and extract the contents of OAACGRoleAssignSODCheck.zip to a directory. -
Open the application in JDeveloper. See the routing rules in the ruleset
RemeditationRulesof theApprovalTaskRules.rulesfile, where the following SOD related information is available for configuring the rules as part of the task payload elementoaacgResponse.-
hasIssues: Acceptable values are:
-
TRUE: Authorization issues exist but can be remedied
-
FALSE: No authorization issues
-
REJECT: Authorization issues exist but cannot be remedied; request has to be rejected
-
-
dimensions: List of dimensions and tags that are defined on the controls related to the authorization issues
-
requestedRoles: List of roles that are requested as part of this request
-
existingRoles: List of existing role memberships for the user
-
authIssues: List of Oracle Governance, Risk and Compliance Controls Incident IDs and the following additional details. This information is subsequently required to notify the approval decision.
-
ctrlPriority: Priority of the Oracle Applications Access Control Governor control that resulted in the authorization issue
-
ctrlName: Name of the SOD policy
-
userName: User profile to which the authorization issue belongs
-
roleName: Role associated with the authorization issue
-
sodStatus: Approval status of the request indicating whether the request is approved by Governance, Risk and Compliance Controls, or approved with conditions, or rejected
-
issuePath: Information about the entity on which the SOD policy is defined
-
-
After the rule modifications, update the following values in the OAACGRoleAssignSODCheck_cfgplan.xml configuration plan file.
| Value | Description |
|---|---|
|
|
The OIM server t3 URL |
|
|
The OIM server host name |
|
|
The OIM server port number |
Thereafter, deploy the modified composite with this updated configuration plan file.
16.15.6 Troubleshoot Segregation of Duties for Role Provisioning: Procedures
The following scenarios may require troubleshooting measures to ensure successful completion of segregation of duties (SOD) checks and approval of role provisioning requests.
16.15.7 Failure of Role Assignment Request
The role assignment request fails and the request gets the Request Failed status. To troubleshoot this, do the following:
-
Log in to the Oracle Identity Management domain in Enterprise Manager.
-
On the home page, under (Service Oriented Architecture), click OAACGRoleAssignSODCheck composite.
-
Under Recent Instances, click the latest instance and look for any error message or description of failure of request.
-
Check if the Application Access Controls Governor server information provided in Oracle Identity Manager is correct.
-
On the left pane, click IDM domain and from the context menu select System Mbean Browser.
-
Under Application Defined Mbeans, navigate to
oracle.iamand select the OIM server and Application OIM. -
Expand XML Config - Config - XMLConfig.OAACGConfig and select OAACGCOnfig.
-
Ensure that the attribute values used in Host, Port, DataSourceName, Service URL, and UserName are correct. To modify any incorrect information, on the Operations tab, click
updateOAACGConfigInformationmethod, and provide the following parameters.Parameter Description host
Application Access Controls Governor host name or IP address
port
Application Access Control Governor port
username
Admin username
password
Admin password
serviceURL
Application Access Control Governor service URL
Note
Ensure that there is a forward slash at the end of the URL. The URL must be in the format /grcc/services/GrccService/.
DatasourceName
Data source name of the Oracle Fusion connector that is configured in Application Access Control Governor
-
After saving the modifications, restart the Oracle Identity Management server.
16.15.8 Task Details Missing
If the task details of the assigned task are not found, perform the following checks to troubleshoot.
-
Ensure that the taskflow is deployed on the SOA server.
-
Log in to the Weblogic console.
-
On the left side, under the menu, click Deployments.
-
Ensure that TaskDetails application is deployed to SOA server and its state is Active.
-
-
Ensure that the predefined Admin user in Oracle Identity Management (OIM) is available in the Oracle Credential Store Framework (CSF), do the following:
-
Log in to Oracle Identity Management domain in Enterprise Manager.
-
On the left pane, click Identity Management domain and from the context menu, select Security - Credentials.
-
Expand OIM and check for the key entry
sysadmin. -
Select the entry and click Edit to view the details.
-
Ensure that the user name is set to
xelsysadm.
-
If these steps do not help, refer to the generic troubleshooting tips associated with Oracle Identity Manager.
For generic information about troubleshooting OIM, see Troubleshoot Oracle Identity Management in the Oracle Fusion Applications Administrator's Guide.
16.15.9 Configure Oracle Data Integrator Studio for External Authentication: Explained
Configuring Oracle Data Integrator Studio for external authentication is necessary to prevent any unauthorized access. The access credentials are stored in a configuration file. To make the external configuration work, the jps configuration file (jps-config.xml) must be configured and placed in the prescribed directory where the application is installed.
16.15.10 Prerequisites
To configure Oracle Data Integrator Studio, ensure that the following selections were made in the Oracle Data Integrator installation wizard:
-
Developer Installation options on the Select Installation Type page:
-
ODI Studio (with local agent)
-
ODI SDK
-
-
Skip Repository Configuration on the Repository Configuration page
Oracle Data Integrator Studio must be installed in a separate Oracle home other than Oracle Fusion Middleware Oracle homes and Oracle Fusion Applications Oracle home.
16.16 Configure Presence Servers
For an on-premise installation of Oracle Fusion Applications, Microsoft Office Communication Server (OCS) 2007 or Microsoft Live Communication Server (LCS) can be optionally used as the presence server. The setup involves creating external application connections, and instant messaging and presence connections, to OCS or LCS for each Oracle Fusion application.
Prerequisites for OCS or LCS need also to be set up.
This table lists the Java EE applications that can be configured with OCS or LCS.
| Product Family or Product | Java EE Application Name |
|---|---|
|
Oracle Fusion Application Customer Relationship Management |
|
|
Oracle Fusion Applications Human Capital Management |
|
|
Oracle Fusion Applications Projects |
ProjectFinancialsApp |
|
Oracle Fusion Application Toolkit |
HomePageApp |
For each application, execute the following commands against the appropriate domain:
-
createExtAppConnection -
addExtAppField -
createIMPConnection
Replace placeholder values enclosed within brackets (< >) with real values, for the appName, url, poolName, userDomain, and server fields.
-
For the appName field, enter the Java EE application name, for example HcmBenefitsApp.
-
The userDomain field is required only for the OCS connection and refers to the user domain associated with the OCS installation.
-
For the server field, enter the managed server name on which the Java EE application is deployed. This field is optional if there is only one managed server for the application.
16.16.1 createExtAppConnection
Execute this command:
createExtAppConnection(appName='<JavaEEApp>', name='IMP_EXT_APP', displayName='Presence Server Login Credentials')
The appName field is environment specific and requires to enter a value.
16.16.2 addExtAppField
Execute this command:
addExtAppField(appName='<JavaEEApp>', name='IMP_EXT_APP', fieldName='Account', fieldValue='', displayToUser=1)
The appName field is environment specific and requires to enter a value.
16.16.3 createIMPConnection
If Oracle Fusion Applications is deployed in a high availability configuration, there may be multiple managed servers targeted for each Java EE application. The createIMPConnection command must be run for each application on each server, and specify the server in the server field.
If the LCS adapter is used, then execute this command:
createIMPConnection(appName='<JavaEEApp>', name='presence', adapter='LCS', url='<http://host:port/contextPath>', appId='IMP_EXT_APP', poolName='<poolNameHere>', timeout=60, default=1, server='<managedServerName>')
If the OCS adapter is used, then execute this command:
createIMPConnection(appName='<JavaEEApp>', name='presence', adapter='OCS2007', url='<http://host:port/contextPath>', appId='IMP_EXT_APP', userDomain='<example.com>', poolName='<poolNameHere>', timeout=60, default=1, server='<managedServerName>')
These fields are environment specific and require to enter a value:
-
appName
-
adapter (OCS2007 or LCS)
-
url
-
poolName
-
default (1 or 0)
The connection is not used unless this field is set to 1. If 0 is used, then essentially disable the connection.
-
server
16.17 Configure Audit Trails for Oracle Fusion Middleware
The Oracle Fusion Middleware Audit Framework is a new service in Oracle Fusion Middleware 11g, designed to provide a centralized audit framework for the middleware family of products. The framework provides audit service for platform components such as Oracle Platform Security Services (OPSS) and Oracle Web Services. It also provides a framework for JavaEE applications, starting with Oracle's own JavaEE components. JavaEE applications will be able to create application-specific audit events. For non-JavaEE Oracle components in the middleware, such as C or JavaSE components, the audit framework also provides an end-to-end structure similar to that for JavaEE applications. For Oracle Fusion Applications, several Oracle Fusion Middleware products such as Oracle Data Integrator (ODI), Business Intelligence Publisher (BIP), Oracle Platform Security Services (OPSS), Oracle Web Service Management (OWSM), Oracle Business Intelligence Enterprise Edition (OBIEE), and Meta Data Services (MDS) leverage audit trails capability.
Figure 16-4 is a high-level architectural diagram of the Oracle Fusion Middleware Audit Framework.
Figure 16-4 Audit Event Flow
The Oracle Fusion Middleware Audit Framework consists of the following key components:
-
Audit APIs: These are APIs provided by the audit framework for any audit-aware components integrating with the Oracle Fusion Middleware Audit Framework. During run time, applications may call these APIs, where appropriate, to audit the necessary information about a particular event happening in the application code. The interface allows applications to specify event details such as user name and other attributes needed to provide the context of the event being audited.
-
Audit Events and Configuration: The Oracle Fusion Middleware Audit Framework provides a set of generic events for convenient mapping to application audit events. Some of these include common events such as authentication. The framework also allows applications to define application-specific events.
These event definitions and configurations are implemented as part of the audit service in Oracle Platform Security Services. Configurations can be updated through Enterprise Manager (UI) and WebLogic Scripting Tool (WLST) command-line tool.
-
Audit Bus-stop: Bus-stops are local files containing audit data before they are pushed to the audit repository. In the event where no database repository is configured, these bus-stop files can be used as a file-based audit repository. The bus-stop files are simple text files that can be queried easily to look up specific audit events. When a DB-based repository is in place, the bus-stop acts as an intermediary between the component and the audit repository. The local files are periodically uploaded to the audit repository based on a configurable time interval.
-
Audit Loader: As the name implies, the audit loader loads the files from the audit bus-stop into the audit repository. In the case of platform and JavaEE application audit, the audit loader is started as part of the JavaEE container start-up. In the case of system components, the audit loader is a periodically spawned process.
-
Audit Repository: The audit repository contains a predefined Oracle Fusion Middleware Audit Framework schema, created by Repository Creation Utility (RCU). When configured, all the audit loaders are aware of the repository and upload data to it periodically. The audit data in the audit repository is expected to be cumulative and will grow over time. Ideally, this should not be an operational database used by any other applications; rather, it should be a standalone RDBMS used for audit purposes only. In a highly available configuration, Oracle recommends to use an Oracle Real Application Clusters (RAC) database as the audit data store.
-
Oracle Business Intelligence Publisher: The data in the audit repository is exposed through predefined reports in Oracle Business Intelligence Publisher. The reports allow users to drill down the audit data based on various criteria. For example:
-
User name
-
Time range
-
Application type
-
Execution context identifier (ECID)
-
The enterprise deployment topology does not include Oracle Fusion Middleware Audit Framework configuration. The ability to generate audit data to the bus-stop files and the configuration of the audit loader will be available after the products are installed. The main consideration is the audit database repository where the audit data is stored. Because of the volume and the historical nature of the audit data, it is strongly recommended that customers use a separate database from the operational store or stores being used for other middleware components.
16.18 Install Print Servers
Print servers must be installed for external applications as part the implementation activity in Oracle Fusion Applications.
This task is not applicable to Oracle Cloud implementations.
16.18.1 External Applications
Several external applications require specialized print servers. See the related product documentation for installing print servers for these applications.
-
Oracle Business Intelligence Financial Reporting Studio and Financial Reporting Print Server.
-
Primavera P6 Enterprise Project Portfolio Management.
16.19 Configure Oracle HTTP Server for Privileged Port (UNIX Only with No Load Balancer)
A secondary Oracle HTTP server needs to be added to the Oracle Fusion Applications environment to effectively handle the load and improve the application performance.
Before proceeding with the installation of the secondary HTTP server, ensure that the following prerequisites are met.
-
Availability of a free slot to install the secondary HTTP server.
Usually, the secondary HTTP server is installed on the same slot as the primary HTTP server. In such cases, the webgate used by the primary HTTP server can be used by the secondary HTTP server. However, if the secondary HTTP server is not installed on the same slot as the primary HTTP server, the webgate used by the primary HTTP server is not accessible by the secondary HTTP server. In that case, a separate webgate needs to be installed for the secondary HTTP server.
-
Set up a directory structure similar to the directory structure of the primary HTTP server. The directory structure of the primary HTTP server is as follows.
First OHS mw home: /slot/ems5905/appmgr/APPLICATIONS_BASE/webtier_mwhome First OHS OH: webtier First OHS instance dir: /slot/ems5905/appmgr/APPLICATIONS_BASE/instance/CommonDomain_webtier/ First OHS component name: ohs1 First OHS bin dir: /slot/ems5905/appmgr/APPLICATIONS_BASE/instance/CommonDomain_webtier/bin First OHS config dir: /slot/ems5905/appmgr/APPLICATIONS_BASE/instance/CommonDomain_webtier/config/OHS/ohs1/moduleconf
On the same lines, a directory structure can be defined for the secondary HTTP server as shown here:
Second OHS mw home: /slot/ems5905/appmgr/APPLICATIONS_BASE/webtier_mwhome2 Second OHS OH: webtier2 Second OHS instance dir: /slot/ems5905/appmgr/APPLICATIONS_BASE/instance/CommonDomain_webtier2 Second OHS component name: ohs2
16.20 Use Default Oracle Database Vault Schemas
This is an optional step. If Oracle Database Vault is intended to be used, use only the default Oracle Database Vault Owner (DVOWNER) and Oracle Database Vault Account (DVACCTMGR) schemas. Custom schemas are not allowed for using Oracle Database Vault. This ensures future smooth migration to Oracle Software As A Service.
16.21 Next Steps
For more information about scale out and server migration for Oracle Fusion Applications, go to Complete Conditional Common High Availability Post-Installation Tasks for Oracle Identity Management. Otherwise, go to the section that corresponds to the product offering that is installed.