Obtaining a Credential for the Ticket-Granting Service
-
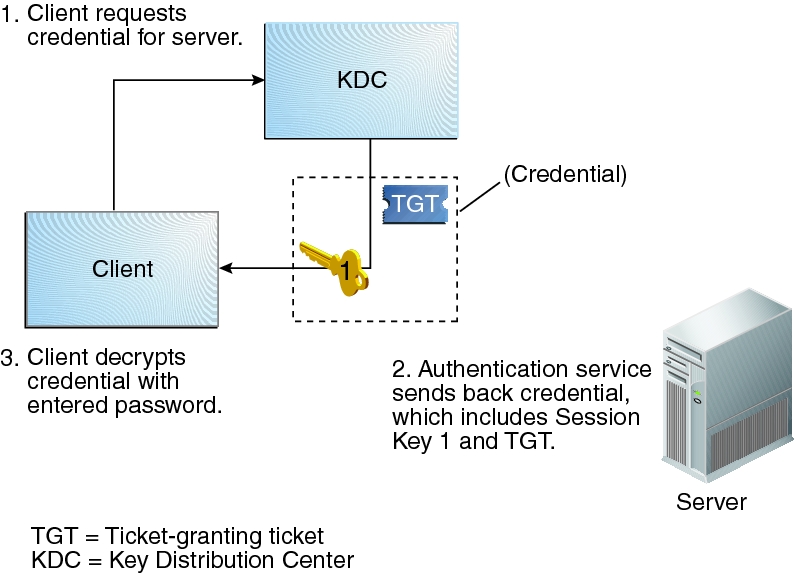
To start the authentication process, the client sends a request to the authentication server for a specific user principal. This request is sent without encryption. No secure information is included in the request, so using encryption is not necessary.
-
When the request is received by the authentication service, the principal name of the user is looked up in the KDC database. If a principal matches the entry in the database, the authentication service obtains the private key for that principal. The authentication service then generates a session key to be used by the client and the ticket-granting service (call it Session Key 1) and a ticket for the ticket-granting service (Ticket 1). This ticket is also known as the ticket-granting ticket (TGT). Both the session key and the ticket are encrypted by using the user's private key, and the information is sent back to the client.
-
The client uses this information to decrypt Session Key 1 and Ticket 1 by using the private key for the user principal. Because the private key should be known only by the user and the KDC database, the information in the packet should be safe. The client stores the information in the credentials cache.
During this process, a user is normally prompted for a password. If the password the user specifies is the same as the password that was used to build the private key stored in the KDC database, then the client can successfully decrypt the information that is sent by the authentication service. The client then has a credential to be used with the ticket-granting service and is ready to request a credential for a server.
Figure 2-5 Obtaining a Credential for the Ticket-Granting Service