Secure HTTPS Outbound Communication and SSL Certificates
For secure (HTTPS) outbound communication with the NetSuite application, you should purchase SSL certificates from a Certificate Authority (CA) that is included in the Mozilla Included CA Certificate List.
-
Any CA in this list is trusted by the NetSuite application.
-
Certificates obtained from CAs that are not included in this list are not trusted by the NetSuite application for HTTPS communication.
Secure HTTPS outbound communication includes, for example, traffic that is using the SuiteScript N/https Module. For example, if the SSL certificate in use was not obtained from a trusted CA, a SuiteScript call such as https.get or https.post will return an SSS_INVALID_HOST_CERT error.
The SSL Certificate Chain
The following information is presented to provide a deeper understanding of the SSL certificate chain. Oracle NetSuite requires that the endpoints you're connecting to from NetSuite provide a full certificate chain. A full certificate chain lets us build the certificate path from the leaf certificate (the certificate created for the target endpoint) to the root certificate, which is stored in the NetSuite application.
These two certificates (the leaf and the root) are usually connected by one or more intermediate certificates. The intermediate certificate signs the leaf certificate and is signed by the root certificate, completing the path by following the signature chain from leaf to intermediate to root.
Intermediate certificates are not stored in the NetSuite application. So, we require the endpoint to send the intermediate certificate along with the leaf certificate, because we don't store them. Modern browsers and tools like Postman are able to work without the intermediate certificate. Browsers or tools like Postman can download the intermediate certificate based on a field in the leaf certificate. The field specifies where to find the intermediate certificate. The ability to determine the location of the intermediate certificate has not been implemented in the NetSuite application. This means that you must provide all intermediate certificates along with the leaf certificate.
Verifying Your Certificate Chain
Your browser or a tool like Postman might say your certificate is fine. However, you're able to verify whether your endpoint is serving the complete certificate chain using one of two methods. You can check the output of an OpenSSL command or analyze the chain at SSL Labs to see what's happening.
If your outbound HTTPS communication is served by a third party, ensure that the third party is aware of the necessity to include all intermediate certificates with the leaf certificate.
To verify your certificate chain using OpenSSL:
-
Open a command window.
-
The following is an example of the command format. Replace the variable in this command with the appropriate value for your certificate chain:
openssl s_client -showcerts -connect <example-test.example.com:443> -
View the output of the command to verify all intermediate certificates are included in the chain.
To verify your certificate chain at SSL Labs:
-
Go to www.ssllabs.com/ssltest.
-
Enter your domain in the Hostname field.
-
Click Submit.
-
Scroll down to the Additional Certificates section of the report.
If intermediate certificates are missing from the chain, the output may look like this example:
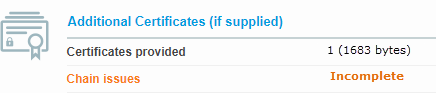
If all intermediate certificates are present in the chain, the output may look like this example:
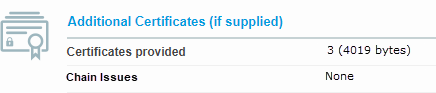
For information about SSL certificates for Commerce websites, see Automatic and Manual Certificates and Select Type of SSL Certificate.