| Skip Navigation Links | |
| Exit Print View | |
|
Oracle Java CAPS Worklist Manager Service Engine User's Guide Java CAPS Documentation |
| Skip Navigation Links | |
| Exit Print View | |
|
Oracle Java CAPS Worklist Manager Service Engine User's Guide Java CAPS Documentation |
Using the Worklist Manager Service Engine
Worklist Manager Service Engine Overview
Worklist Manager Service Engine Features
Worklist Manager Service Engine Architecture
About the Worklist Manager Console
The Composite Application Project
XPath Expressions in Task Definitions
Worklist Manager Task Validation
Steps to Implement a Worklist Manager Task
Defining Worklist Manager Tasks
(Optional) Connecting to the LDAP Server
(Optional) Installing the Sample Worklist Manager Console Projects
To Install the Sample Worklist Manager Console
Creating the Worklist Module Project
Creating the XML Schema Definition (XSD)
To Create the XML Schema Definition
Creating the Worklist Manager Task Definition
To Create the Worklist Manager Task Definition
Assigning Users and User Groups to a Task
To Assign File Realm Users and Groups to a Task
To Assign LDAP Users and Groups to a Task
Configuring Advanced Task Options
Defining Time Limits and Deadlines for a Task
Defining Automatic Task Escalations
To Define Automatic Escalations
Defining Automatic Task Notifications
To Define Automatic Notifications
To Associate a Notification With a Task Status Change or Escalation
To Configure the Email BC for Task Notification
To Define a Custom Notification
Defining Trigger Actions Using the Mapper
To Define Trigger Actions Using the Mapper
Initializing Variables Using the Mapper
To Initialize Variables Using the Mapper
Creating the Worklist Manager Database
Creating the Worklist Manager Database
Creating the Database for JavaDB (Derby)
Creating the Database for MySQL
Creating the Database for Oracle
Setting the GlassFish JVM Classpath to the Database Drivers
To set the GlassFish JVM Classpath settings
Creating the JDBC Connection Pool and JDBC Resource
To Create the JDBC Connection Pool
Configuring the Service Engine to Use the Worklist Manager Database
To Configure the Service Engine for the Database
Configuring Worklist Manager Service Engine Runtime Properties
To Configure WLM SE Runtime Properties
Worklist Manager Service Engine Runtime Property Descriptions
Defining Worklist Manager Console Security
Defining Worklist Manager Console Security Using a File Realm
To Create a User Login Profile in the File Realm
To Define Security Roles for the Worklist Manager Console
To Map Groups to Security Roles for the Worklist Manager Console
Defining Worklist Manager Console Security Using LDAP
To Create an LDAP Realm in the GlassFish Server
To Update web.xml for the Worklist Manager Console (for LDAP)
To Map User Groups to Security Roles for the Worklist Manager Console (for LDAP)
Including the Worklist Manager Task in a BPEL Process
To Include the Worklist Manager Task in a BPEL Process
Creating and Deploying the Composite Application
To Create and Deploy the Composite Application
Testing the Worklist Manager Composite Application
To Run All Test Cases in a Project
Using the Default Worklist Manager Console
Installing and Deploying the Worklist Manager Console Sample
To Install and Deploy the Worklist Manager Console Sample
Logging In to the Worklist Manager Console
To Launch the Worklist Manager Console From a Browser
To Launch the Worklist Manager Console From the GlassFish Admin Console
Using XPath Expressions and Functions in Task Definitions
wlmfn:get-task-owner as xs:string
wlmfn:get-email() as xs:string
wlmfn:get-email($arg as xs:string) as xs:string
wlmfn:get-manager-email() as xs:string
wlmfn:get-manager-email($arg as xs:string) as xs:string
wlmfn:get-manager-uid() as xs:string
wlmfn:get-manager-uid($arg as xs:string) as xs:string
Entering XPath Variables in Design View
Creating Worklist Manager Task Mappings
To Create a Mapping Without Using any Functions
To Use a Function in a Mapping
To Delete a Link or Function From a Mapping
Customizing the Worklist Manager Console
About the Worklist Manager Console
Functionality and UI Semantics Specification
Customizing the Worklist Manager Console
Correcting the Task Input Data Display
Correcting the Task Output Data Display
Creating a Custom Worklist Manager Console
Creating the Web Application and Composite Application
To Configure the Web Application
The Worklist Manager Console can use either Java EE security or LDAP security for authentication. Java EE security is defined through the GlassFish server file realm security feature.
Perform one of the following procedures to define security for the Worklist Manager Console:
When you install the WLM SE, sample users and groups are defined for you in the GlassFish file realm. The users include staff1, staff2, and manager1. The password for each is the same as the username. The user groups (or roles) are staff and manager.
Perform the following steps to define file-realm security:
The default URL for the Admin Console is http://localhost:4848, if GlassFish is installed on the computer from which you launched the web browser.
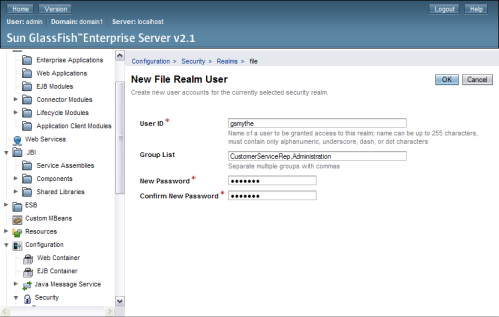
The New File Realm User page appears.
User ID: The login user name for the user.
Group List: One or more user groups to which the user is assigned.
Note - These user groups need to be added to the Worklist Manager Console's web.xml file. This is described in the following task.
New Password: The login password for the user.
Confirm New Password: The same password as above.
This procedure describes how to define abstract security roles to the default Worklist Manager Console. These roles can then be mapped to user groups.
The XML Editor appears.
The Add Security Role dialog box appears.
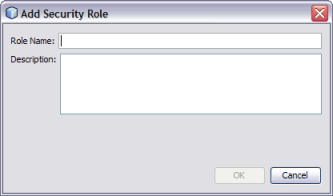
The new user role appears in the Security Roles list.
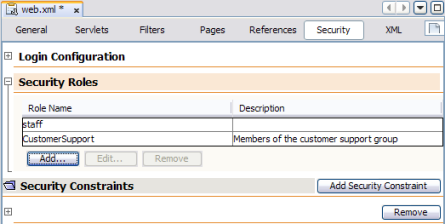
This procedure describes how to map user groups to the security roles you defined above for the default Worklist Manager Console.
The XML Editor appears.
The user roles you created above appear in the list.
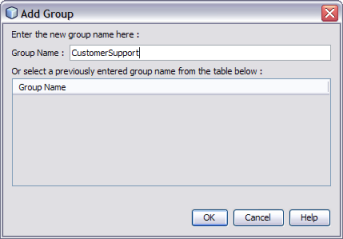
The Add Group dialog box appears.
LDAP can be used for authentication, authorization, and user management. This section provides general instructions for working with LDAP security in the GlassFish server. For more information, see the Sun GlassFish Enterprise Server v2.1.1 Administration Guide.
Perform the following steps to configure the WLM SE and Console for LDAP:
To Update web.xml for the Worklist Manager Console (for LDAP)
To Map User Groups to Security Roles for the Worklist Manager Console (for LDAP)
The default URL for the console is http://localhost:4848.
The New Realm page appears.
JAAS context: The type of login to use for this realm. For LDAP, it must be ldapRealm.
Directory: The URL of the directory server. For example, ldap://190.111.0.111:389.
Base DN: The base Distinguished Name (dn) for the user data.
You can specify additional optional properties for the realm.
.
The roles defined in web.xml are abstract roles are not used to match groups in the LDAP directory. The groups that are mapped to the roles in sun-web.xml are used to match LDAP groups.
The XML Editor appears.
<login-config>
<auth-method>FORM</auth-method>
<realm-name id="LDAPRealm"/>
<form-login-config>
<form-login-page>/login.jsp</form-login-page>
<form-error-page>/login-failed.jsp</form-error-page>
</form-login-config>
</login-config>A new constraint appears and is named Constraint with a number appended to the end.
The Add Web Resource window appears.
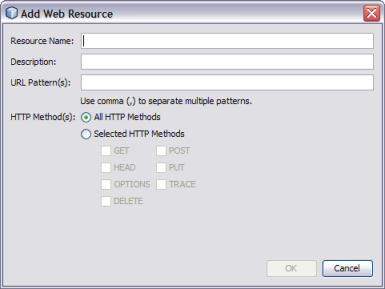
|
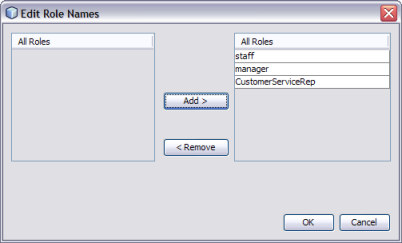
The Edit Role Names dialog box appears.
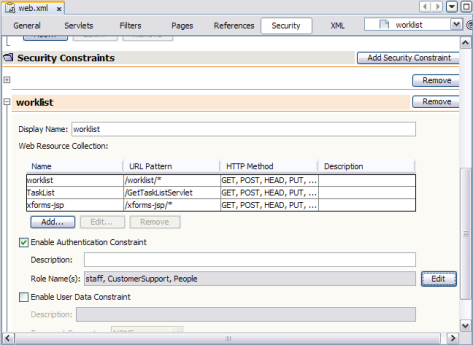
The image below illustrates a defined security constraint.
The XML Editor appears.
The Properties Editor appears.