Data Protection
For cloud providers, data protection is at the heart of their security strategy. Given the importance of privacy and compliance mandates, organizations considering multitenant architectures should strongly consider the use of cryptography to protect information flowing to and from their databases. The use of cryptographic services for data protection is systemically applied to ensure the confidentiality and integrity of information as it flows across the network and when it resides on disk.
The SPARC M8 and M7 processors in SuperCluster facilitate hardware-assisted, high-performance encryption for the data protection needs of security-sensitive IT environments. The processor also features Silicon Secured Memory technology that ensures the prevention of malicious application-level attacks such as memory scraping, silent memory corruption, buffer overruns, and related attacks.
Figure 4 Data Protection Provided by the Hardware-Assisted Cryptographic Acceleration and Memory Intrusion Protection
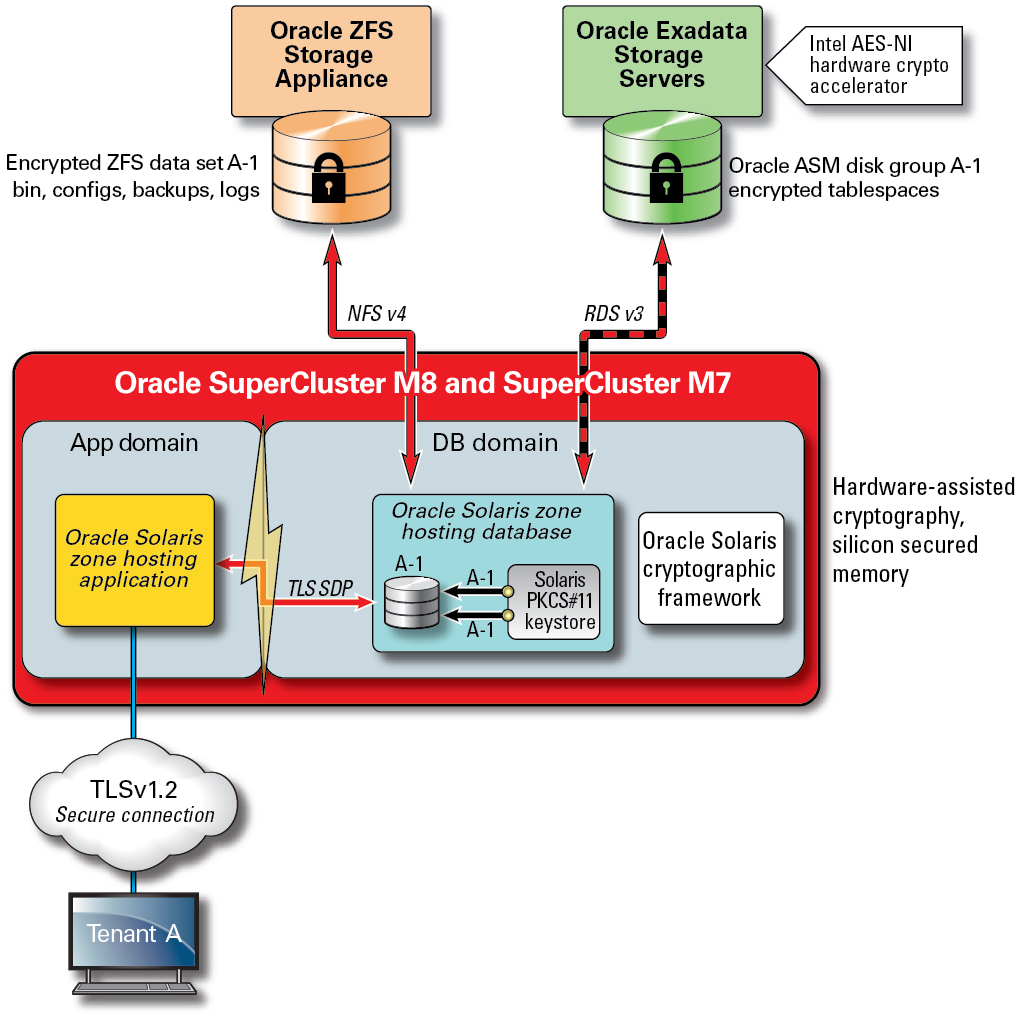
For secure multitenant architectures, where data protection figures into nearly every aspect of the architecture, SuperCluster and its supporting software enables organizations to meet their security and compliance objectives without having to sacrifice performance. SuperCluster leverages on-core based cryptographic instructions and Silicon Secured Memory capabilities, which are designed into its SPARC M8 or M7 processor for accelerating cryptographic operations and ensuring memory intrusion protection without a performance impact. These capabilities yield improved cryptographic performance and provide memory intrusion checking, and they also improve overall performance, because more compute resources can be dedicated to servicing tenant workloads.
The SPARC processor enables hardware-assisted cryptographic acceleration support for over 16 industry-standard cryptographic algorithms. Together, these algorithms support most modern cryptographic needs including public-key encryption, symmetric-key encryption, random number generation, and the calculation and verification of digital signatures and message digests. In addition, at the OS level, cryptographic hardware acceleration is enabled by default for most core services including Secure Shell, IPSec/IKE, and encrypted ZFS data sets.
Oracle Database and Oracle Fusion Middleware automatically identify the Oracle Solaris OS and the SPARC processor used by SuperCluster. This enables the database and middleware to automatically use the hardware cryptographic acceleration capabilities of the platform for TLS, WS-Security, tablespace encryption operations. It also allows them to use the Silicon Secured Memory feature for ensuring memory protection, and it ensures application data integrity without the need for end-user configuration. To protect the confidentiality and integrity of tenant-specific, interzone, IP-based communications flowing over the IB network use IPSec (IP Security) and IKE (Internet Key Exchange).
Any discussion of cryptography would be incomplete without discussing how encryption keys are managed. Generating and managing encryption keys, especially for large collections of services, has traditionally been a major challenge for organizations, and the challenges grow even more significant in the case of a cloud-based multitenant environment. On SuperCluster, ZFS data set encryption and Oracle Database Transparent Data Encryption can leverage an Oracle Solaris PKCS#11 keystore to securely protect the master key. Using the Oracle Solaris PKCS#11 keystore automatically engages the SPARC hardware-assisted cryptographic acceleration for any master key operations. This allows SuperCluster to significantly improve the performance of the encryption and decryption operations associated with encryption of ZFS data sets, Oracle Database tablespace encryption, encrypted database backups (using Oracle Recovery Manager [Oracle RMAN]), encrypted database exports (using the Data Pump feature of Oracle Database), and redo logs (using Oracle Active Data Guard).
Tenants using a shared-wallet approach can leverage ZFS storage appliance to create a directory that can be shared across all the nodes in a cluster. Using a shared, centralized keystore can help tenants better manage, maintain, and rotate the keys in clustered database architectures such as Oracle Real Application Clusters (Oracle RAC), because the keys will be synchronized across each of the nodes in the cluster.
Figure 5 Data Protection Through a Multitenant Key-Management Scenario Using Oracle Key Manager
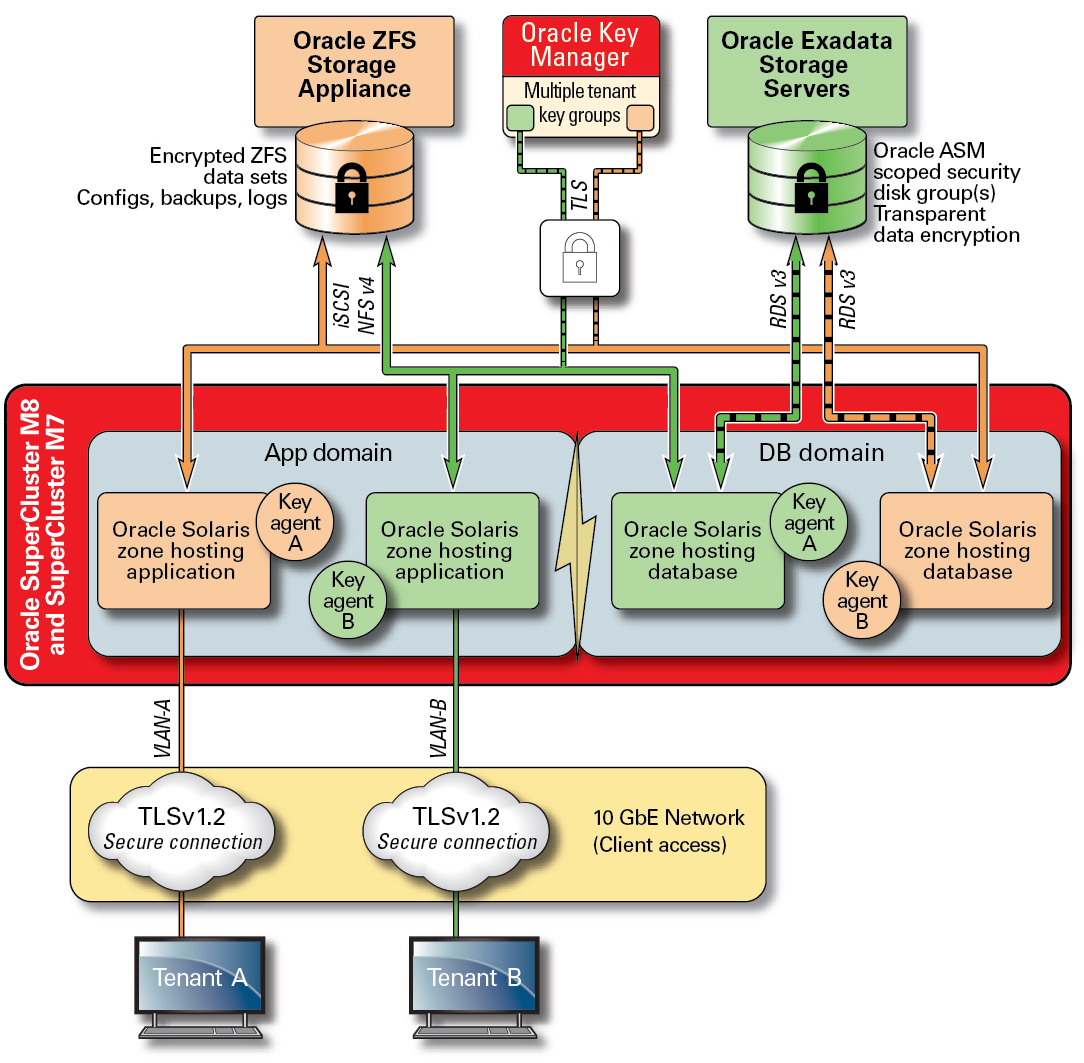
To address key management complexities and issues associated with multiple hosts and applications in a cloud-based multitenant environment, use the optional Oracle Key Manager as an appliance integrated into the management network. Oracle Key Manager centrally authorizes, secures, and manages access to encryption keys used by Oracle Database, Oracle Fusion applications, Oracle Solaris, and the ZFS storage appliance. Oracle Key Manager also supports Oracle’s StorageTek encrypting tape drives. Having the encryption policy and key management at the ZFS data set (file system) level delivers assured deletion of tenant file systems through key destruction.
Oracle Key Manager is a complete key management appliance that supports life-cycle key management operations and trusted key storage. When configured with an additional Sun Crypto Accelerator 6000 PCIe Card from Oracle, Oracle Key Manager offers FIPS 140-2 Level 3 certified key storage of AES 256-bit encryption keys as well as FIPS 186-2–compliant random number generation. Within SuperCluster, all database and application domains, including their global zones and non-global zones, can be configured to use Oracle Key Manager for managing keys associated with applications, databases, and encrypted ZFS data sets. In fact, Oracle Key Manager is able to support key management operations associated with individual or multiple database instances, Oracle RAC, Oracle Active Data Guard, Oracle RMAN, and the Data Pump feature of Oracle Database.
Finally, separation of duties, enforced by Oracle Key Manager, enables each tenant to maintain complete control over its encryption keys with consistent visibility into any key management operations. Given how important keys are for the protection of information, it is critical that tenants implement the necessary levels of role-based access control and auditing to ensure that keys are properly safeguarded throughout their lifetime.