1 About Oracle Solaris Security
Oracle Solaris is a robust, premier enterprise operating system that offers proven security features. With a sophisticated network-wide security system that controls the way users access files, protect system databases, and use system resources, Oracle Solaris 11.4 addresses security requirements at every layer. While traditional operating systems can contain inherent security weaknesses, the flexibility of Oracle Solaris 11.4 enables it to satisfy a variety of security objectives from enterprise servers to desktop clients. Oracle Solaris is fully tested and supported on a variety of SPARC and x86-based systems from Oracle and on other hardware platforms from third-party vendors.
This chapter covers the following topics:
What's New in Security Features in Oracle Solaris 11.4
This section highlights information for existing customers about important new security features in this release.
Compliance Security Features
Compliance enables you to define a security policy for a system and run regular assessments to verify the continued compliance of the system.
-
You can run assessments remotely over authenticated RAD connections. To run remote assessments, you must configure Secure Shell so that it does not prompt the user for authentication. See Configuring Administrators to Run Remote Compliance Commands in Oracle Solaris 11.4 Compliance Guide.
-
You can store assessments immediately in a remote common store or move them to the common store later. See Using a Common Store for Compliance Assessments in Oracle Solaris 11.4 Compliance Guide.
-
Tags on assessments enable you to locate and manage reports based on the tags. Oracle Solaris provides tags and you can create your own tags. See Using Metadata to Manage Assessments in Oracle Solaris 11.4 Compliance Guide.
-
Assessments that you start from a script called a roster run asynchronously on multiple systems from a local system. See How to Run Asynchronous Remote Assessments in Oracle Solaris 11.4 Compliance Guide and the compliance(8) and compliance roster(8) man pages.
-
The
compliance explaincommand lists the rules of the current or specified benchmark or profile. See the compliance(8) man page.
Cryptography Security Features
Oracle Solaris provides the Cryptographic Framework, a central store for cryptographic functions. It closely conforms to recent U.S. government cryptographic requirements. Cryptography is available from other sources that are bundled with Oracle Solaris, such as SASL and OpenSSL.
-
The Cryptographic Framework is based on the latest PKCS #11 Cryptographic Token Interface Standard, PKCS #11 v2.40. Several new cryptographic algorithms and security standards are included in this upgrade. See Chapter 1, About Cryptographic Providers in Oracle Solaris in Managing Encryption and Certificates in Oracle Solaris 11.4.
-
PKCS #11 token labels are configurable. You can simultaneously create a new token, set its PIN, and assign it a label with the
pktool inittokencommand. You can also use this command to change the labels of existing tokens. However, to change the PINs of existing tokens, you continue to use thepktool setpincommand. See How to Create a PKCS #11 Keystore in Managing Encryption and Certificates in Oracle Solaris 11.4. -
Administrators can use the
ucryptoprovider to directly access user-level cryptographic primitives. This faster access can significantly improve the performance of applications. For more information, see Simple and Fast ucrypto Provider in Managing Encryption and Certificates in Oracle Solaris 11.4 and thelibucrypto*(3LIB) man pages. -
To prevent POODLE (Padding Oracle On Downgraded Legacy Encryption) attacks, the
libcrypto.soandlibssl.soOpenSSL libraries do not support the SSLv2 and SSLv3 protocols. -
Weak ciphers in OpenSSL are either removed or deprecated. MD2 is removed. MD4, MD5, RC2, RC4, and DES are deprecated.
-
Enhancements to
elfsignfunctionality add more protection of data from attackers. Also,elfsignseparates the signature cryptographic algorithm calculation from the data range algorithm which simplifies adding and maintaining new algorithms. See Elfsign Enhancements in Managing Encryption and Certificates in Oracle Solaris 11.4.
Kernel and System Security Features
Security extensions, verified boot, and file labeling are added and upgraded.
-
Enforced verified boot on some SPARC platforms requires a firmware upgrade. For details, see Firmware Upgrade for Verified Boot in Securing Systems and Attached Devices in Oracle Solaris 11.4.
-
Verified Boot on x86 systems conforms with the UEFI v2.3.1 Errata B specification. Oracle Solaris uses a first-stage boot loader called "shim" to validate the GRUB2 boot loader. GRUB2 Verified Boot then validates the elfsign signature on the initial Oracle Solaris kernel module "
unix". After Oracle Solaris starts executing from GRUB2, Oracle Solaris validates all other kernel modules. -
The ‐P and ‐H options to the recursive
chmod -Rcommand limit file permission changes across symbolic links. See How to Change File Permissions Across Symbolic Links in Securing Files and Verifying File Integrity in Oracle Solaris 11.4 and the chmod(1)man page. -
Security extensions have several additions.
-
You can enable or disable the inheritance of a security extension's configuration by using the ‐i option with the
sxadm execcommand. For more information, see Preventing Intentional Misuse of System Resources in Securing Systems and Attached Devices in Oracle Solaris 11.4 and thesxadm(8) man page. -
You can add security extensions per object. See Specifying Per-Object Security Extensions in Securing Systems and Attached Devices in Oracle Solaris 11.4.
-
The adiheap security extension enables the malloc family of functions in the
libumemandlibclibraries to support ADI, so provides a reliable defense against linear buffer overflows and mitigates against use-after-free issues. adiheap can uncover subtle bugs that are triggered by an otherwise innocuous code change. See Preventing Process Heap Corruption Using adiheap in Securing Systems and Attached Devices in Oracle Solaris 11.4. -
The adistack security extension is available on SPARC platforms that support Application Data Integrity (ADI). adistack reports stack buffer overflows detected by ADI. For more information, see ADI-Based Stack Protection Using adistack in Securing Systems and Attached Devices in Oracle Solaris 11.4.
-
-
rsyslogreplacessyslogas the default system log daemon implementation.rsyslogis modular, and when system logs are sent to a remote system, additional options include plain TCP, Reliable Event Logging Protocol (RELP), and GSS-API. For more information, see New Feature – Logging Audit Records With rsyslog in Managing Auditing in Oracle solaris 11.4. -
Oracle Solaris provides fault management reports about unresolved faults at login. For more information, see the rsyslogd(8)man page.
File and File System Security Features
ZFS adds the following security features to its existing security.
-
Labeling sensitive data and access to the data to prevent data loss enables you to comply with isolation requirements from corporate security, legislation, and standards bodies. In Oracle Solaris you can identify sensitive files and file systems by applying labels to them. For more information, see Labeling Files for Data Loss Protection in Securing Files and Verifying File Integrity in Oracle Solaris 11.4.
-
Only users who have the clearance to handle those sensitive files can view or modify them. Even privileged users and roles can be prevented from accessing the contents of labeled files. For more information, see Labeling Processes for Data Loss Protection in Securing Users and Processes in Oracle Solaris 11.4.
-
You can encrypt your file systems at boot time. For more information, see Using ZFS Root Pool Encryption in Automatically Installing Oracle Solaris 11.4 Systems.
User and Process Rights Features
For process labeling, see Kernel and System Security Features.
Note:
Rights protect new features, such as the analytics dashboard for viewing the Oracle Solaris StatsStore. For the new authorizations and rights profiles that protect the StatsStore, see Statistics Store Authorizations and Administrative Profiles in Using Oracle Solaris 11.4 StatsStore and System Web Interface.Additional security attributes are available for users and systems.
-
The Service Management Facility (SMF) is the repository for system-wide security settings which were previously in the following files:
/etc/security/policy.conf /etc/default/login /etc/default/passwd /etc/default/su
The values are set in an SMF stencil when the
svc:/system/account-policy:defaultservice is enabled. The service is disabled by default, so as not to interrupt your legacy practices. When the service is enabled, the following modification to the Oracle Solaris 11.3policy.conffile is replaced by asetpropcommand in Oracle Solaris 11.4:example-11u3$ ## /etc/security/policy.conf file PRIV_DEFAULT=basic,!file_link_any PRIV_DEFAULT=basic,!file_link_anyexample-11u4-sys$ pfbash svccfg -s account-policy \ setprop config/etc_security_policyconf/disabled = boolean: false example-11u4-sys$ pfbash svccfg -s account-policy \ setprop rbac/default_privileges astring: = "basic,!file_link_any"
Similar modifications to the properties of the
account-policyservice can affect logins and the security settings of thesucommand. For more information, see account-policy(8S). -
The
unlock_afteruser attribute has been added to theuser_attrdatabase. Administrators can use this new attribute to specify the time after which a successful authentication automatically unlocks a locked account. The time may be specified as a number of minutes, hours, days, or weeks. For further information, see What’s New in Rights in Oracle Solaris 11.4 in Securing Users and Processes in Oracle Solaris 11.4 and the user_attr(5) man page. -
The
annotationuser attribute has been added to theuser_attrdatabase. Administrators can use this new attribute to require users to annotate their logins. For further information, see What's New in Rights in Oracle Solaris 11.4 in Securing Users and Processes in Oracle Solaris 11.4 and the user_attr(5) man page. -
In Oracle Solaris you can limit labeled file access to processes and users who have the clearance to handle those labeled files. Even privileged users and roles can be prevented from accessing the contents of labeled files. For more information, see Labeling Processes for Data Loss Protection in Securing Users and Processes in Oracle Solaris 11.4.
Passwords and Authentication Security Features
Password defaults are strengthened, Simple Authentication and Security Layer (SASL) is based on Cyrus SASL, and OpenSSH is the basis for Secure Shell. For information about features that interact with authentication, see Cryptography Security Features and Auditing Security Features.
-
Password constraints are stronger. Passwords must have at least
PASSLENGTHcharacters as defined in the/etc/default/passwdfile. The default length is eight characters. Three additional variables can constrain password duration: MAXDAYS, MINDAYS, and WARNDAYS. For more information, see Password Parameters in Securing Systems and Attached Devices in Oracle Solaris 11.4 and the passwd(1) man page. -
The Simple Authentication and Security Layer (SASL) in Oracle Solaris is based on the open source Cyrus SASL with a few changes. For details of the implementation, see Using Simple Authentication and Security Layer in Managing Authentication in Oracle Solaris 11.4 and the SASL man pages, such as saslauthd(8).
-
The sole Secure Shell implementation in Oracle Solaris is OpenSSH. For the release number, type
pkg info sshin a terminal window. OpenSSH replaces SunSSH. See OpenSSH Implementation of Secure Shell in Managing Secure Shell Access in Oracle Solaris 11.4.For keywords that enable OpenSSH and legacy Oracle Solaris 11 SunSSH systems to interoperate, see Ignore Keywords in Secure Shell in Managing Secure Shell Access in Oracle Solaris 11.4.
-
Secure Shell can store and retrieve Secure Shell public keys from an LDAP directory server. See Secure Shell and Remote Public Keys in Managing Secure Shell Access in Oracle Solaris 11.4 and the
ssh-ldap-pubkey(8)man page.
Networking Security Features
Security is added to ports, IKEv2 optimizes the handling of large encrypted messages, and the Packet Filter firewall has additional features.
-
Oracle Solaris Packet Filter (PF) adds the
ftp-proxyservice and firewall interface groups to PF. For more information, see Oracle Solaris Firewall in Securing the Network in Oracle Solaris 11.4 and theftp-proxy(8)man page. -
IKEv2 can prevent most IP layer fragmentation of its messages by replacing large encrypted messages with a series of smaller encrypted messages. See What’s New in Network Security in Oracle Solaris 11.4 in Securing the Network in Oracle Solaris 11.4and IKEv2 Service in Securing the Network in Oracle Solaris 11.4.
-
To enhance the security of ports, see Protecting Networks With IEEE 802.1X Certificates in Securing the Network in Oracle Solaris 11.4.
Auditing Security Features
Auditing adds many new features, including per-object auditing, annotated login
records, and analytics. Interfaces such as the admhist command and the
Oracle Solaris StatsStore can present audit records and information in an easy-to-understand
format.
-
The
sstoremeta-class replaces theloclass as the default set of audit flags. In additionlo, thesstoremeta-class includes thess,as,xa, andpeaudit classes. See Viewing Audit Data in the Statistics Store in Managing Auditing in Oracle Solaris 11.4. -
Audit information is available to the Oracle Solaris StatsStore and the Oracle Solaris Analytics BUI. For more information about how audit information is captured in the StatsStore and can be viewed in the Analytics BUI, see Analytics’ Auditing Sheet in Managing Auditing in Oracle Solaris 11.4 and Using Oracle Solaris 11.4 StatsStore and System Web Interface.
-
The audit service supports per-object auditing. Administrators with the appropriate privileges can set ACL entries to audit access attempts for specific files or specific directories. For more information, see New Feature - Per-Object Logging of Audit Events in Managing Auditing in Oracle Solaris 11.4.
-
Oracle Solaris enables administrators to require users to annotate their sessions at login. The annotation is written to the audit record. See New Feature – Annotating Reason for Access in the Audit Record in Managing Auditing in Oracle Solaris 11.4 and several man pages, including profiles(1), auditrecord(8), and pam_unix_cred(7).
-
The
admhistcommand provides a summary of privileged execution audit records in a helpful, easy-to-understand format. This command extracts only audit events that successfully used privilege from the audit trail, so the output more accurately displays events that were likely to have modified the system. For more information, see New Feature - Viewing a Summary of Audit Records in Managing Auditing in Oracle Solaris 11.4 and the admhist(8) man page. -
The
auditstatcommand replaces the‐getstatand‐setstatoptions to theauditconfigcommand. See the auditstat(8) man page. -
The
peaudit class enables the audit service to automatically track the use of privileges that allowed a process to change the system's configuration. For more information, see New Feature - Per-Privilege Logging of Audit Events in Managing Auditing in Oracle Solaris 11.4. -
Auditing tracks whether Verified Boot is enabled and working on your system. See New Feature - Auditing Verified Boot in Managing Auditing in Oracle Solaris 11.4.
-
You must refresh the audit service after changing an audit configuration file. See New Feature - Refreshing the audistet SMF Service After Changing Event-Class Mappings in Managing Auditing in Oracle Solaris 11.4.
-
You can filter audit records by functional areas such as
cpuandnetwith theauditreduce -tcommand. Theaudit_tagsdatabase stores these functional areas as audit tags. For more information, see New Feature - Filtering Audit Records by Functional Area in Managing Auditing in Oracle Solaris 11.4 and the audit_tags(5) and auditreduce(8) man pages. -
Administrators can now view configured audit classes by using the
‐lsclassoption to theauditconfigcommand. For more information, see the auditconfig(8) man page. -
Administrators can display audit event information per audit class by using the
auditconfig -lsevent audit_flagscommand. See New Feature - Listing Audit Events by Audit Class in Managing Auditing in Oracle Solaris 11.4 and the auditconfig(8) and audit_flags(7) man pages. -
All audit plugins can now specify which audit classes from the classes that are configured system-wide are to be written to their plugin. In addition, the Audit Remote Server (ARS) now supports specifying a set of audit flags on a per-connection group basis. For more information, see New Feature - Flexible Per-Plugin Configuration of Audit Classes in Managing Auditing in Oracle Solaris 11.4 and the auditconfig(8) man page.
Oracle Solaris 11.4 Security After Installation
Oracle Solaris is installed "secure by default" (SBD). This security posture protects the system from intrusion and monitors login attempts, among other security features.
System Access Is Limited and Monitored
Initial user and root role accounts – The initial user account can log in from the console. This account is assigned the root role. The password for the initial user and the root accounts is identical at installation.
-
After logging in, the initial user can assume the
rootrole to further configure the system. Upon assuming the role, the user is prompted to change therootpassword. Note that no role can log in directly, including therootrole. -
The initial user is assigned defaults from the
/etc/security/policy.conffile. The defaults include the Basic Solaris User rights profile and the Console User rights profile. These rights profiles enable users to read and write to a CD or DVD, run any command on the system without privilege, and stop and restart their system when sitting at the console. -
The initial user account is also assigned the System Administrator rights profile. Therefore, without assuming the
rootrole, the initial user has some administrative rights, such as the right to install software and manage the naming service.
Password requirements
– User passwords must be at least eight characters
long, and have at least two alphabetic characters and one non-alphabetic
character. Passwords are hashed by using the SHA256
algorithm.
Limited network access
– After installation, the system is protected from
intrusion over the network. Remote login by the initial user is allowed
over an authenticated, encrypted connection with the Secure Shell protocol.
This is the only network protocol that accepts incoming packets. The
Secure Shell key is wrapped by the AES128 algorithm. With
encryption and authentication in place, the user can reach the remote
system without interception, modification, or spoofing.
Recorded login attempts – The audit
service is enabled for all login/logout events (login, logout, switching
user, starting and stopping a Secure Shell session, and screen locking) and for
all non-attributable (failed) logins. Because the root role cannot log
in, the name of the user who is acting as root is recorded in the audit
trail. The initial user can review the audit logs by a right granted through the System
Administrator rights profile.
Kernel and File Protections Are in Place
After the initial user is logged in, the kernel, file systems, and system files are protected by file permissions, privileges, and user rights. User rights are also known as role-based access control (RBAC).
Kernel protections
– Many daemons and administrative commands are assigned
just the privileges that enable them to succeed. Many daemons are run
from special administrative accounts that do not have
root (UID=0) privileges, so they
cannot be hijacked to perform other tasks. These special administrative
accounts cannot log in. Security extensions protect
kernel processes. Devices are protected by privileges.
File systems – By
default, all file systems are ZFS file systems. The user's
umask is 022, so when a user
creates a new file or directory, only the user is allowed to modify it.
Members of the user's group are allowed to read and search the
directory, and read the file. Logins that are outside the user's group
can list the directory and read the file. The default directory
permissions are drwxr-xr-x (755).
The file permissions are -rw-r--r--
(644).
System files – System
configuration files are protected by file permissions. Only the
root role or a user who is assigned the right to edit
a specific system file can modify a system file. The audit service calls
system files public objects.
Oracle Hardware Management Package
The Oracle Hardware Management Package provides a set of utilities for configuring, managing, and monitoring Oracle servers. This value-add set of tools for Oracle hardware is always available. It can automatically deliver certain hardware-related information to ILOM to complete the view that it has of system hardware. For information about the utilities and security, see Systems Management and Diagnostics Documentation Library (https://docs.oracle.com/cd/F24624_01/index.html#hwmgmt).
Oracle Solaris Configurable Security
In addition to the solid foundation that Oracle Solaris security defaults provide, the security posture of a Oracle Solaris system is highly configurable to satisfy a range of security requirements.
The following sections provide a short introduction to the security features of Oracle Solaris. The descriptions include references to more detailed explanations and to procedures that show how to configure these features.
Protecting Data
Oracle Solaris protects data from booting through installation, use, and archiving. This section covers files, file systems, and cryptographic protections. Additional data protection features are described in Protecting and Isolating Applications and Labeled Security.
File Permissions and Access Control Entries
The first line of defense for protecting objects in a file system are the default UNIX permissions that are assigned to every file system object. UNIX permissions support assigning unique access rights to the owner of the object, to a group assigned to the object, as well as to anyone else. Additionally, the default file system, ZFS, supports access control lists (ACLs), which more finely control access to individual or groups of file system objects.
For more information, see the following:
-
For a description of security-relevant ZFS file attributes, see Using File Attributes to Add Security to ZFS Files in Securing Files and Verifying File Integrity in Oracle Solaris 11.4 and the man pages.
-
For an overview of file permissions, see Setting ACLs on ZFS Files in Securing Files and Verifying File Integrity in Oracle Solaris 11.4.
-
For an overview and examples of protecting ZFS files, see Setting ACLs on ZFS Files in Securing Files and Verifying File Integrity in Oracle Solaris 11.4 and the ZFS and chmod(1) man pages.
Cryptographic Services
The Cryptographic Framework feature of Oracle Solaris and the Key Management Framework (KMF) feature of Oracle Solaris provide central repositories for cryptographic services and key management. Hardware, software, and end users have seamless access to optimized algorithms. KMF provides a unified interface for otherwise different storage mechanisms, administrative utilities, and programming interfaces for various public key infrastructures (PKIs).
The Cryptographic Framework provides a common store of algorithms and PKCS #11 libraries to handle cryptographic requirements. The PKCS #11 libraries are implemented according to the RSA Security Inc. PKCS #11 Cryptographic Token Interface (Cryptoki) standard. Cryptographic services, such as encryption and decryption for files, are available to regular users. The Cryptographic Framework is evaluated to run in FIPS 140-2 mode. See How to Create a Boot Environment With FIPS 140-2 Enabled in Managing Encryption and Certificates in Oracle Solaris 11.4.
KMF provides tools and programming interfaces for centrally managing public key objects, such as X.509 certificates and public/private key pairs. The formats for storing these objects can vary. KMF also provides a tool for managing policies that define the use of X.509 certificates by applications. KMF supports third-party plugins.
For more information, see the following:
-
Selected man pages include cryptoadm(8), digest(1), encrypt(1), mac(1), pktool(1), and kmfcfg(1).
-
Managing Encryption and Certificates in Oracle Solaris 11.4.
Identity Service
The svc:/system/identity SMF service configures the basic network identity
(names) of the Oracle Solaris instance. The identity includes its node name, RPC domain name, and
the default set of X.509 certificates to use for the Remote Administration Daemon (RAD) and WebUI.
The service is composed of the following instances:
-
svc:/system/identity:node– Specifies the host name or node name -
svc:/system/identity:domain– Specifies the RPC domain name -
svc:/system/identity:cert– Deploys or creates the X.509 certificates for WebUI and RAD connections that use the TLS transport -
svc:/system/identity:cert-expiry– Certificate expiry check -
svc:/system/identity:version– Updates the value that is used inuname -voutput
The identity:cert-expiry instance periodically checks the expiry status of a identity:cert-created certificate. When it finds an expired certificate, the identity:cert-expiry instance has the identity:cert instance re-issue the certificate, if possible.
In addition, the identity:cert-expiry instance monitors the certificates in /etc/certs/CA that are distributed by the ca-certificate package. If any of those certificates are expired, the identity:cert-expiry instance enters degraded mode. When in degraded mode, identity:cert-expiry appears in svcs -x output and an FMA alert is posted. This situation generally occurs if you are not updating the system on a regular basis.
Oracle Solaris ZFS File System
ZFS is the default file system for Oracle Solaris. ZFS is robust, scalable, and easy to administer. Because file system creation in ZFS is lightweight, you can easily establish quotas and reserved space. UNIX permissions and ACLs protect files, and you can encrypt the entire dataset at creation. Oracle Solaris rights management supports the delegated administration of ZFS datasets, that is, users who are assigned a limited set of privileges can administer ZFS datasets.
For more information, see the following:
Protecting Users and Assigning Additional Rights
Users are assigned a basic set of privileges, rights profiles, and authorizations from the
/etc/security/policy.conf file, similar to the initial user as
described in System Access Is Limited and Monitored.
These rights are configurable. You can deny basic rights and increase the rights for a user.
Oracle Solaris protects users with flexible complexity requirements for passwords, authentication that is configurable for different site requirements, and user rights management. User rights management limits and distributes administrative rights by assigning privileges, authorizations, and rights profiles to trusted users. Additionally, special shared accounts called roles assign the user just those administrative rights when the user assumes the role. The ARMOR package provides predefined roles. For more information, see Using ARMOR Roles in Securing Users and Processes in Oracle Solaris 11.4.
Passwords and Password Policy
Your password change policy should follow industry standards. System administration
logins, such as root, must be carefully controlled. Administration should
be through roles, users with rights profiles, or sudo. These
administrative methods use least privilege and write administrative events to the audit trail.
Note:
The passwords for users who can assume roles must not be subject to any password aging constraints.For more information, see the following:
-
Controlling Logins in Securing Systems and Attached Devices in Oracle Solaris 11.4
-
Troubleshooting Passwords in Securing Users and Processes in Oracle Solaris 11.4
-
Securing Logins and Passwords in Securing Systems and Attached Devices in Oracle Solaris 11.4
-
Selected man pages include account-policy(8S), passwd(1), and crypt.conf(5).
Pluggable Authentication Modules
The Pluggable Authentication Module (PAM) framework enables administrators to coordinate and configure user authentication requirements for accounts, credentials, sessions, and passwords without modifying the services that require authentication.
The PAM framework enables organizations to customize the user authentication experience as well as account, session, and password management functionality. System entry services such as login and ssh use the PAM framework to secure all entry points for the freshly installed system. PAM enables the replacement or modification of authentication modules in the field to secure the system against any newly found weaknesses without requiring changes to any system services that use the PAM framework.
Oracle Solaris delivers a broad set of PAM modules and configurations to meet most site policies. For more information, see the following:
User Rights Management
User rights in Oracle Solaris are governed by the security principle of least privilege. Organizations can selectively grant administrative rights to users or roles according to the unique needs and requirements of the organization. They can also deny rights to users when required. Rights are implemented as privileges on processes and authorizations on users or SMF methods. Rights profiles provide a convenient way to collect privileges and authorizations into a bundle of related rights.
For more information, see the following:
-
Selected man pages include auths(1), privileges(7), profiles(1), rbac(7), roleadd(8), roles(1), and user-attr(5).
Protecting and Isolating Applications
Applications can be entry points for malware and malicious users. In Oracle Solaris, these threats are mitigated by the use of privileges and the containment of applications within zones. Applications can run with just the privileges that the application needs, so a malicious user does not have root privileges to access the rest of the system. Zones can limit the extent of an attack. Attacks on applications in a non-global zone can affect processes in that zone only, not the zone's host system. For more information, see Oracle Solaris Zones.
Security extensions, such as address space layout randomization (ASLR), nxheap, nxstack, adiheap, and adistack make it difficult for intruders to benefit from a stack overflow or to compromise an executable or the heap. For more information, see Kernel and System Security Features.
The Service Management Facility (SMF) also protects applications by enabling administrators to restrict starting, stopping, and using an application. For more information, see Service Management Facility.
Privileges in Oracle Solaris
Privileges are fine-grained, discrete rights on processes that are enforced in the kernel. Oracle Solaris defines over 80 privileges, ranging from basic privileges like file_read to more specialized privileges like proc_clock_highres. Privileges can be granted to a process, a user, or a role. Many Oracle Solaris commands and daemons run with just the privileges that are required to perform their task. Privilege-aware programs can prevent intruders from gaining more privileges than the program itself uses.
The use of privileges is also called process rights management. Privileges enable organizations to specify, hence limit, which privileges are granted to services and processes that run on their systems.
For more information, see the following:
Oracle Solaris Zones
The Oracle Solaris Zones software partitioning technology enables you to maintain the one-application-per-server deployment model while simultaneously sharing hardware resources. Figure 1-1 illustrates two zones sharing the same hardware. The Data Zone connection to the private LAN is read-write, while the Web Zone connection to the Internet is read-only.
Figure 1-1 Zone Sharing Hardware
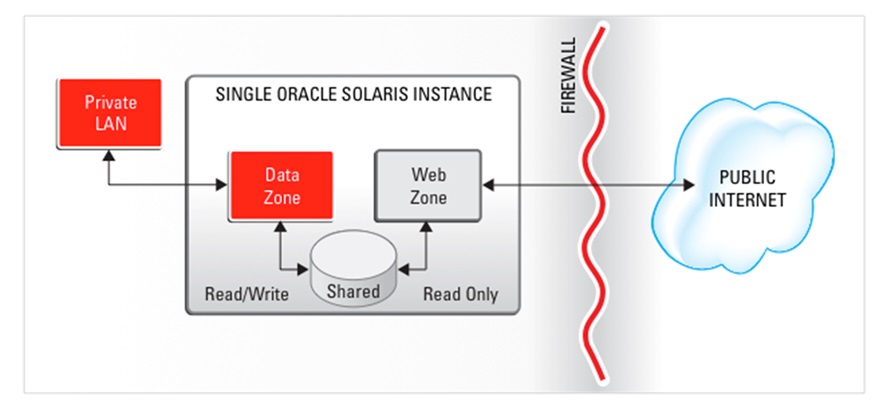
Zones are virtualized operating environments that enable multiple applications to run in isolation from each other on the same physical hardware. This isolation prevents processes that run within a zone from monitoring or affecting processes that run in other zones, viewing each other's data, or manipulating the underlying hardware. Zones also provide an abstraction layer that separates applications from physical attributes of the system on which they are deployed, such as physical device paths and network interface names.
For added protection, physical global zones, called Immutable Global Zones, and virtual global zones, called Oracle Solaris Kernel Zones, can be read-only. Immutable global zones are slightly more powerful than Kernel Zones, but neither can permanently change the hardware or configuration of the system. Read-only zones boot faster and are more secure than zones that allow writes.
For maintenance, immutable global zones define a special set of processes, called the Trusted Path Domain (TPD) that can be configured to limit administrative logins. For more information, see Configuring and Administering Immutable Zones in Creating and Using Oracle Solaris Zones and the tpd(7) man page. For information about zone configuration resources, see Introduction to Oracle Solaris Zones. See also the mwac(7) and tpd(7).
Oracle Solaris Kernel Zones are useful for deploying a compliant system. For example, you can configure a compliant system, create a Unified Archive, then deploy the image as a kernel zone. For more information, see the solaris-kz(7) man page, Creating and Using Oracle Solaris Kernel Zones, “Oracle Solaris Zones Overview” in Introduction to Oracle Solaris 11.4 Virtual Environments, and Using Unified Archives for System Recovery and Cloning in Oracle Solaris 11.4.
For more information, see the following:
-
Configuring Immutable Zones in Creating and Using Oracle Solaris Zones
-
Selected man pages include brands(7), zoneadm(8), and zonecfg(8)
Security Extensions
Oracle Solaris security extensions are flags at the kernel level that protect applications from compromise. For more information, see the following:
-
For administrator information, see Preventing Intentional Misuse of System Resources in Securing Systems and Attached Devices in Oracle Solaris 11.4
-
For developer information, follow the links in Writing Applications That Run Securely
Service Management Facility
Services are persistently running applications. A service can represent a running application, the software state of a device, or a set of other services. The Service Management Facility (SMF) feature of the Oracle Solaris is used to add, remove, configure, and manage services. SMF uses rights management to control access to service management functions on the system. In particular, authorizations determine who can manage a service and what functions that person can perform.
SMF enables organizations to control access to services, as well as to control how those services are started, stopped, and refreshed.
For more information, see the following:
Java Cryptography Extension
Java provides the Java Cryptography Extension (JCE) for developers of Java applications. JCE provides a framework for implementing encryption, key generation and key agreement, and message authentication code (MAC) algorithms. For more information, see Java SE Security (https://www.oracle.com/java/technologies/javase/javase-tech-security.html).
Securing Network Communications
Network communications can be protected by features such as firewalls, TCP wrappers on networked applications, and encrypted and authenticated remote connections.
Packet Filtering
Packet filtering provides basic protection against network-based attacks. Oracle Solaris includes the OpenBSD Packet Filter firewall and TCP wrappers.
OpenBSD Packet Filter Firewall
The OpenBSD Packet Filter (PF) replaces the IP Filter feature in Oracle Solaris. PF is a network firewall that captures inbound packets and evaluates them for entry to and exit from the system. PF provides stateful packet inspection. It can match packets by IP address and port number as well as by the receiving network interface.
PF is based on OpenBSD Packet Filter version 5.6, which is enhanced to work with Oracle Solaris components, such as zones with exclusive IP instances.
For more information, see the following:
-
For an overview, see Oracle Solaris Firewall in Securing the Network in Oracle Solaris 11.4
-
For examples of using PF, see Configuring the Firewall in Oracle Solaris in Securing the Network in Oracle Solaris 11.4, and the man pages.
-
Selected man pages include pf.conf(7), pfctl(8), and pf.os(7).
TCP Wrappers
TCP wrappers provide access control for internet services. When various internet
(inetd) services are enabled, the tcpd daemon
checks the address of a host requesting a particular network service against an ACL.
Requests are granted or denied accordingly. TCP wrappers also log host requests for
network services in syslog, which is a useful monitoring function.
The sendmail feature of Oracle Solaris is configured to use TCP wrappers. Network services that have a one-to-one mapping to executable files, such as proftpd and rpcbind, are candidates for TCP wrappers.
TCP wrappers support a rich configuration policy language that enables organizations to specify security policy not only globally but on a per-service basis. Further access to services can be permitted or restricted based upon host name, IPv4 or IPv6 address, netgroup name, network, and even DNS domain.
For information about TCP wrappers, see the following:
-
For information and examples of the syntax of the access control language for TCP wrappers, see the
hosts-access(4)man page. -
Selected man pages include
tcpd(8)and inetd(8).
Remote Access
Remote access attacks can damage a system and a network. Oracle Solaris provides defense in depth for network transmissions. Defense features include encryption and authentication checks for data transmission, login authentication, and the disabling of unnecessary remote services.
IPsec and IKE
IP security (IPsec) protects network transmissions by authenticating the IP packets, by encrypting them, or by doing both. Because IPsec is implemented well below the application layer, Internet applications can take advantage of IPsec without requiring modifications to their code.
IPsec and its automatic key exchange protocol, IKE, use algorithms from the Cryptographic Framework. Additionally, the Cryptographic Framework provides a central keystore. When IKE is configured to use the metaslot, organizations have the option of storing the keys on disk or in a software keystore called softtoken. Oracle Solaris supports both the IKE Version 2 (IKEv2) protocol and the IKEv1 protocol.
IPsec and IKE require configuration, so are installed but not enabled by default. When properly administered, IPsec is an effective tool in securing network traffic.
For more information, see the following:
-
About IP Security Architecture in Securing the Network in Oracle Solaris 11.4
-
Configuring IPsec in Securing the Network in Oracle Solaris 11.4
-
IPsec and FIPS 140-2 in Securing the Network in Oracle Solaris 11.4
-
About Internet Key Exchange in Securing the Network in Oracle Solaris 11.4
-
Configuring IKEv2 in Securing the Network in Oracle Solaris 11.4
-
Selected man pages include ipsecconf(8) and in.iked(8).
OpenSSH Secure Shell
By default, OpenSSH (Secure Shell) is the only active remote access mechanism on a newly installed system. All other network services are either disabled or in listen-only mode.
Secure Shell creates an encrypted communications channel between systems. Secure Shell can also be used as an on-demand virtual private network (VPN) that can forward X Window system traffic or can connect individual port numbers between a local system and remote systems over an authenticated and encrypted network link.
Thus, Secure Shell prevents a would-be intruder from being able to read an intercepted communication and prevents an adversary from spoofing the system.
The openssh implementation of Secure Shell can run in FIPS 140-2 mode.
OpenSSH sets FIPS 140-2 mode dynamically.
For more information, see the following:
-
Using Secure Shell in Managing Secure Shell Access in Oracle Solaris 11.4
-
Secure Shell and FIPS 140-2 in Managing Secure Shell Access in Oracle Solaris 11.4
-
Selected man pages are available on the command line and include
ssh(1), ssh(8),sshd(8),sshd_config(5), andssh_config(5).
Kerberos Service
The Kerberos feature of the Oracle Solaris enables single sign-on and secure transactions, even over heterogeneous networks where systems run different operating systems and run the Kerberos service. You can install Kerberos clients by using AI, so that the client is a Kerberized system at first boot.
Kerberos is based on the Kerberos V5 network authentication protocol from MIT. The Kerberos service offers strong user authentication, as well as integrity and privacy. Using the Kerberos service, you can log in once and access other systems, execute commands, exchange data, and transfer files securely. Additionally, the service enables administrators to restrict access to services and systems.
For more information, see the following:
-
How to Configure Kerberos Clients Using AI in Automatically Installing Oracle Solaris 11.4 Systems
-
Kerberos and FIPS 140-2 Mode; in Managing Kerberos in Oracle Solaris 11.4
-
Selected man pages include
kadmin(8),kdcmgr(8),kerberos(5),kinit(1), andkrb5.conf(5).
Labeled Security
Oracle Solaris now supports file and process labeling using the same labeling APIs and CLIs as
Trusted Extensions. The label syntax described in the applies to
both environments. Similarly, the new labelcfg command can configure labels
in both environments.
The labeling scenario for the Oracle Solaris environment is distinct from the Trusted Extensions environment.
-
Labeling for privacy – In this scenario, labels are applied to files, directories and System V IPC objects that contain sensitive data. Access to labeled data is restricted to the few users who are assigned the clearance to access it. Hosts and zones are not labeled. Users who have access to labeled data can share the data at their discretion. Users also can choose to lower the clearance of processes that they execute by running them in sandboxes. This is the default behavior for Oracle Solaris.
-
Mandatory Access Control – In this scenario, zones and hosts are assigned a label and all the data that can be modified within a zone is automatically labeled with the zone’s label. Users are assigned a clearance which determines which zones they can see or log in to. When executing in a labeled zone, users are only permitted to share data with processes and network endpoints at the same label. Administrative users can be given permission to share read-only data with higher level zones or hosts. This scenario is handled by Trusted Extensions.
Labeling for Privacy
In Oracle Solaris, you can protect data from unwarranted access by applying labels to datasets, user processes, and SMF processes at administrative discretion. Most users and processes are not visibly labeled. File systems can contain multiple labels below the declared upper bound of the file system.
In this labeled environment, trusted users can also be assigned or create sandboxes, that is, protected areas for work at a specified label and for processes at that label.
For more information, see the following:
Mandatory Access Control
The Trusted Extensions feature of Oracle Solaris is an optionally enabled layer of secure labeling technology that enables data security policies to be separated from data ownership on disk and over the wire. Trusted Extensions supports both traditional discretionary access control (DAC) policies based on ownership, as well as label-based mandatory access control (MAC) policies. When the Trusted Extensions layer is enabled, all data flows are restricted based on a comparison of the labels associated with the processes (subjects) requesting access and the objects containing the data.
Trusted Extensions features include:
-
All file systems are labeled – By default, Trusted Extensions file systems are assigned a single label in a zone at that same label. You can create a multilevel ZFS dataset, mount it on a Trusted Extensions system, and with appropriate permissions, upgrade and downgrade the files in that dataset. For more information, see Multilevel Datasets for Relabeling Files in Trusted Extensions Configuration and Administration.
-
All network communications are labeled – Trusted Extensions labels network communications. Data flows are restricted based on a comparison of the labels associated with the originating network endpoint and the receiving network endpoint. Gateways and in-between hops must also be labeled to allow the passage of information at the label of the communication. NFS and multilevel ZFS datasets provide additional features on a network.
The Trusted Extensions implementation is unique in its ability to provide high assurance, while maximizing compatibility and minimizing overhead.
Trusted Extensions is part of the Oracle Solaris 12 Common Criteria EAL4+ Certification. Trusted Extensions meets the requirements of the Common Criteria Labeled Security Package (LSP).
For more information, see the following:
-
Selected man pages include trusted_extensions(7), labeladm(8), and labeld(8).
Writing Applications That Run Securely
Developers should write and compile applications to run securely on Oracle Solaris. For general information, see the following:
For specific suggestions, see the following:
-
ld(1) man page – Security extension flags as arguments to the ‐z sx= option
-
Secure Coding Guidelines for Developers in Developer’s Guide to Oracle Solaris 11.4 Security
-
Security Considerations When Using C Functions in Developer’s Guide to Oracle Solaris 11.4 Security
-
Runtime Security in Oracle Solaris 11.4 Linkers and Libraries Guide
Site Security Policy and Practice
For a secure system or network of systems, your site must have a security policy in place with security practices that support the policy. If you are developing programs or installing third-party programs, you must develop and install those programs securely. For more information, see Site Security Policy and Enforcement.