After physically setting up the DMZ subnet and assigning IP addresses to the servers, personality file configuration for the Corente Services Gateway that is supporting the DMZ begins on the Network tab of the gateway’s Location form in App Net Manager. Use this tab to register the Ethernet interface of the gateway that will connect to the DMZ.
To access this tab, right-click the gateway’s name and select Edit. The Location form will be displayed. Click Network from the tabs across the top of this form. In the Network Interfaces section of this tab, you must click the Add button to register the DMZ interface.
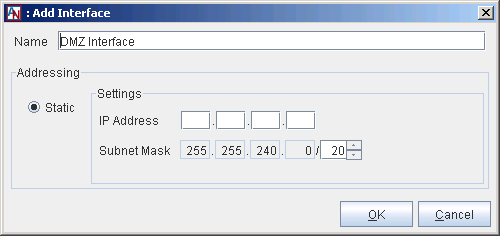
On the window that is displayed, select DMZ Interface and click OK. The Add Interface window will be displayed.
Supply an IP address and subnet mask for the gateway’s DMZ interface. Remember that this address must be on the same private subnet as the servers in the DMZ. Click OK. When you select OK, a series of dialog boxes will be displayed that allow you to perform several automatic personality configurations.
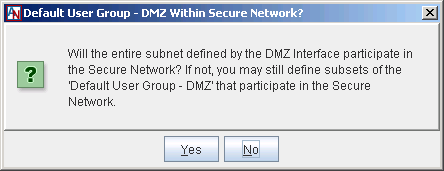
In the first dialog box, if you select Yes, by default, the entire DMZ subnet will be available to share across the secure Corente Services network with the Corente Services Gateway partners. Computers at partner Locations can be permitted to access servers on the DMZ in the same way that computers on the LAN access them.
If you select No, by default, the entire DMZ subnet will not be shared over the Corente Services network. Computers at partner Locations must connect to servers on the DMZ like machines from the Internet/WAN. If you select No, you can later define subsets of the subnet that will be included in the secure network on the User Groups tab of the Location form.
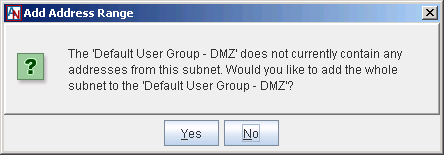
When adding the DMZ interface, a new User Group is created on the User Groups tab of the Location form: the Default User Group – DMZ. The creation of this default User Group informs the Corente Services Gateway what particular sets of addresses are participating in the DMZ. If you select Yes in this dialog box, you will populate the Default User Group – DMZ with the entire subnet in which the DMZ exists. If you select No, the User Group will be created, but will be empty, and you must populate the group manually on the User Groups tab.
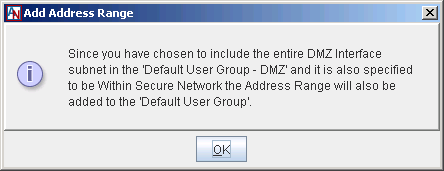
If you selected Yes for the both of the previous dialog boxes, a third dialog box will be displayed to inform you that the DMZ subnet will be added to the main Default User Group for the gateway. The Default User Group contains all addresses on the LAN that are permitted to participate in the secure Corente Services network.
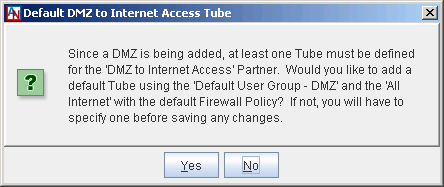
The next dialog box enables you to automatically create a tube on the Partners tab for the DMZ to Internet Access partner that allows all machines on the Internet to connect to the Default User Group – DMZ using the default DMZ to Internet Firewall Policy for your domain. By default, this firewall policy denies all inbound and outbound traffic. You will be able to modify this tube and add new tubes for the DMZ to Internet Access partner at any time. If you select No, no tube will be created, so you must manually create this tube on the Partners tab.
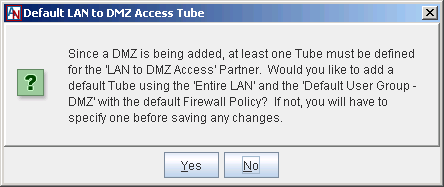
The final dialog box enables you to automatically create a tube on the Partners tab for the LAN to DMZ Access partner that allows any machine on the LAN to connect to the Default User Group – DMZ using the default LAN to DMZ Firewall Policy for your domain. By default, this firewall policy denies all inbound and outbound traffic between the LAN and the DMZ. You will be able to modify this tube and add new tubes for the LAN to DMZ Access partner at any time. If you select No, no tube will be created, so you must manually create this tube on the Partners tab.