Components of a Virtual Network
A virtual network has the following components:
-
Virtual Network Interface Card (VNIC)
-
Virtual switch
-
Etherstub
-
Zone
Virtual Network Interface Card (VNIC)
A VNIC is an L2 entity or virtual network device that behaves just like a physical NIC when configured. You configure a VNIC over an underlying datalink to share it between multiple zones or VMs. In addition, the system's resources treat VNICs as if they were physical NICs. All physical Ethernet interfaces support the creation of VNICs. For more information about how to configure a VNIC, see How to Configure VNICs and Etherstubs.
A VNIC has an automatically generated MAC address. Depending on the network interface in use, you can assign a MAC address to a VNIC other than the automatically generated MAC address. For more information, see Modifying VNIC MAC Addresses.
Virtual Switch
A virtual switch is an entity that facilitates communication between virtual machines (VMs). The virtual switch loops traffic between virtual machines (inter-VM traffic) within the physical machine and does not send this traffic out on the wire. A virtual switch is implicitly created whenever you create a VNIC on top of an underlying datalink. The VNICs configured with the VMs need to be on the same VLAN or VXLAN for inter-VM communication. Virtual switches can be managed by EVS. For information about EVS, see Chapter 5, About Elastic Virtual Switches.
As per Ethernet design, if a switch port receives an outgoing packet from the host connected to that port, that packet cannot go to a destination on the same port. This Ethernet design is a limitation for systems that are configured with virtual networks because the virtual networks share the same NIC. This Ethernet design limitation is overcome by using the virtual switches, which enable VMs to communicate with one another.
In certain cases, communication between VMs in a system might require the use of a switch. For example, communication between VMs might need to be subjected to access control lists (ACLs) that are configured on the switch. By default, a switch cannot send packets on the same port where the packets are received. Therefore, reflective relay is enabled on the switch for communication between VMs that use a switch. Reflective relay enables the switch to forward the packets on the same port where the packets are received. For more information, see Reflective Relay.
Etherstub
An etherstub is a pseudo Ethernet NIC that is configured at the datalink layer (L2) of the Oracle Solaris network stack. You can create VNICs over an etherstub instead of over a physical NIC. With etherstubs, you can construct a private virtual network that is isolated both from the other virtual networks on the system and from the external network. For example, etherstubs can be used to create a network environment whose access is limited only to your developers and not to the entire network.
The following figure shows a private virtual network based on the etherstub.
Figure 1-1 Private Virtual Network
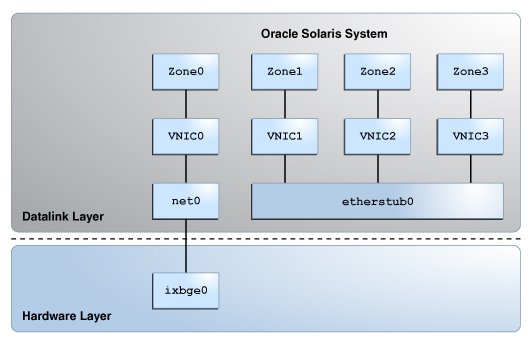
This figure shows etherstub0 over which VNIC1, VNIC2, and VNIC3 are configured. Each VNIC is assigned to a zone. The private virtual network based on the etherstub cannot be accessed by external networks. For more information, see How to Configure a Private Virtual Network.
Zone
A zone is a virtualized operating system environment created within a single instance of the Oracle Solaris operating system. Zones provide an isolated and protected environment for running applications. Etherstubs and VNICs are only a part of the virtualization features of Oracle Solaris. By assigning VNICs or etherstubs for use by Oracle Solaris zones, you can create a network within a single system. For more information about zones, see Introduction to Oracle Solaris Zones .