Overview of Network Virtualization
Network virtualization is an OS-provisioned mechanism that enables you to programmatically create and configure virtual networks that are decoupled from the underlying physical network. A virtual network is therefore a pseudo network that uses the physical network only as a packet forwarding backbone. You can virtualize entire network topologies of servers, routers, switches, and firewalls all running on a single platform and requiring no additional investment in networking hardware.
In virtual networks, virtual machines (VMs) are provisioned that run instances of the operating system. The VMs are isolated from one another but communicate with each other within the network.
Note - IP addresses that are used in Oracle Solaris 11 documentation conform to RFC 5737, IPv4 Address Blocks Reserved for Documentation (https://tools.ietf.org/html/rfc5737) and RFC 3849, IPv6 Address Prefix Reserved for Documentation (https://tools.ietf.org/html/rfc3849). IPv4 addresses used in this documentation are blocks 192.0.2.0/24, 198.51.100.0/24, and 203.0.113.0/24. IPv6 addresses have prefix 2001:DB8::/32.
To show a subnet, the block is divided into multiple subnets by borrowing enough bits from the host to create the required subnet. For example, host address 192.0.2.0 might have subnets 192.0.2.32/27 and 192.0.2.64/27.
Network Virtualization Technologies That Are Supported by Oracle Solaris
Oracle Solaris supports the following network virtualization technologies:
-
Edge Virtual Bridging (EVB) – Enables a host to exchange information related to virtual links on a system with an external switch. EVB is used to exchange information about all the virtual links behind a port whereas data center bridging (DCB) is used to exchange information about the port. See Using Edge Virtual Bridging.
-
Virtual Extensible Local Area Network (VXLAN) – VXLAN addresses the 4K limitation of virtual local area network (VLAN) and also reduces the demand of virtualization on physical infrastructure such as switches. It uses physical server resources effectively in a data center that spans multiple L2 networks and provides scalability and network isolation for virtual networks. See Configuring Virtual Extensible Local Area Networks.
-
Single Root I/O Virtualization (SR-IOV) – Enables the creation of a virtual function (VF) based VNIC on a network device that supports SR-IOV. See Using Single Root I/O Virtualization With VNICs.
-
Private Virtual Local Area Network (PVLAN) VNICs – Enables you to configure PVLAN VNICs that are used for dividing a VLAN into sub-VLANs to isolate the network traffic thereby providing better usage of the limited number of available VLANs.
Network Virtualization Components
This section describes the components of network virtualization.
Virtual Network Interface Card (VNIC)
A VNIC is an L2 entity or virtual network device that is configured over a physical datalink. VNICs are created either by an administrator or by the system. The VNICs are then assigned to zones to enable the zones to exchange network traffic.
A VNIC has an automatically generated MAC address. However, you can also assign a different MAC address to a VNIC if preferred.
Virtual Switch
A virtual switch is an entity that facilitates communication between virtual machines (VMs) that share the same datalink. The virtual switch loops traffic between virtual machines (inter-VM traffic) within the physical machine and does not send this traffic out on the wire. A virtual switch is implicitly created whenever you create a VNIC on top of an underlying datalink. The VNICs configured with the VMs need to be on the same VLAN or VXLAN for inter-VM communication.
In certain cases, communication between VMs in a system might require the use of a switch. For example, communication between VMs might need to be subjected to access control lists (ACLs) that are configured on the switch. By default, a switch cannot send packets on the same port where the packets are received. Therefore, reflective relay is enabled on the switch for communication between VMs that use a switch. Reflective relay enables the switch to forward the packets on the same port where the packets are received.
Etherstub Virtual NIC
An etherstub is a pseudo Ethernet NIC that is configured at the datalink layer (L2) of the Oracle Solaris network stack. You can create VNICs over an etherstub instead of over a physical NIC. With etherstubs, you can construct a private virtual network that is isolated both from the other virtual networks on the system and from the external network. For example, you can use etherstubs to create a network environment without the external connectivity or resources.
Elastic Virtual Switch
The Oracle Solaris Elastic Virtual Switch (EVS) feature provides virtual networking infrastructure that interconnects virtual machines that reside on multiple systems. EVS enables centralized management of virtual switches on multiple hosts and VNICs connected to the elastic virtual switch. Virtual machines connected to the same elastic virtual switch can communicate with each other.
Types of VMs for Network Virtualization in Oracle Solaris
Although you can assign VNICs to resources in a single instance of the Oracle Solaris, you can extend their use in network virtualization by using them in virtualized environments such as Oracle Solaris Zones, Oracle Solaris Kernel Zones, or Oracle VM Server for SPARC.
Oracle Solaris Zones
A zone is a virtualized operating system environment created within a single instance of Oracle Solaris. Etherstubs and VNICs are only a part of the virtualization features of Oracle Solaris. By assigning VNICs or etherstubs for use by Oracle Solaris zones, you can create a network within a single system.
An Oracle Solaris Kernel Zone, also called a solaris-kz branded zone, uses the branded zones framework to run a zone with a separate kernel and operating system (OS) installation from the global zone. The separate kernel and OS installation provide for greater independence and enhanced security of operating system instances and applications.
For information about zones, refer to the zone documentation on the Creating and Using Oracle Solaris Virtual Environments shelf of the Oracle Solaris 11.4 Information Library.
Oracle VM Server for SPARC
Oracle VM Server for SPARC provides highly efficient, enterprise-class virtualization capabilities for SPARC T-Series, SPARC M5, Fujitsu SPARC M12, and Fujitsu M10 platforms. You can create virtual servers called "logical domains" that can run an instance of an operating system to enable multiple operating systems on the same computer. For more information, see the appropriate administration guide in the Oracle VM Server for SPARC (https://docs.oracle.com/en/virtualization/oracle-vm-server-sparc/) documentation library.
How a Virtual Network Works
The following figure shows the working of a virtual network and its components in a system.
Figure 1 Working of a Virtual Network
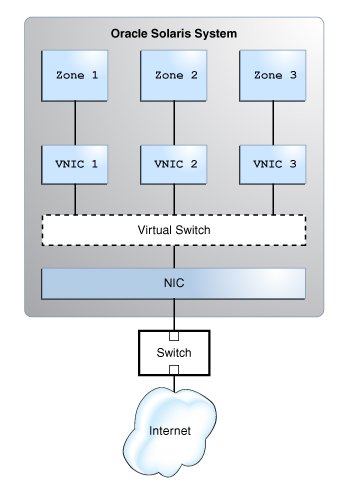
The figure shows a single system with one NIC. The NIC is configured with three VNICs. Each VNIC is assigned to a zone. The zones communicate with each other and with the external network by using their respective VNICs. The three VNICs connect to the underlying physical NIC through the virtual switch. The function of a virtual switch is equivalent to the function of a physical switch, which is to provide connectivity to the systems.
When a virtual network is configured, a zone sends traffic to an external host as usual. Traffic flows from the zone, through the VNIC to the virtual switch, and then to the physical interface, which sends the data to the network.
The zones can also exchange traffic with one another inside the system if all the VNICs configured to the zones are part of the same VLAN. The traffic is managed by the virtual switch. In this case, the traffic never leaves the system, and therefore never violates the Ethernet restrictions.
You can also create a virtual network based on the etherstub. Etherstubs are entirely software based and do not require a network interface as the basis for the virtual network. See the following figure:
Figure 2 Private Virtual Network
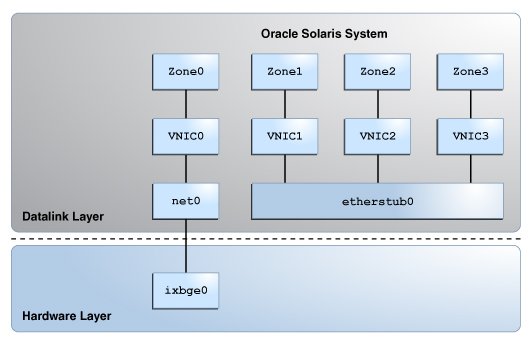
This figure shows etherstub0 over which VNIC1, VNIC2, and VNIC3 are configured. Each VNIC is assigned to a zone. The private virtual network based on the etherstub cannot be accessed by external networks. For more information, see Use Case: Configuring a Private Virtual Network.
You can use Oracle Enterprise Manager to manage some aspects of network virtualization, for example, the ability to create virtual networks inside a virtual data center. For more information about Oracle Enterprise Manager, see https://www.oracle.com/enterprise-manager/technologies/.
With the release of Oracle Virtual Networking Drivers for Oracle Solaris, Oracle Virtual Networking now supports Oracle Solaris on x86 and SPARC servers. For more information about Oracle Virtual Networking, see Oracle Virtual Networking Documentation (https://docs.oracle.com/cd/E38500_01/).