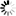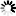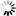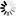Corente Cloud Services Exchange provides two DMZ configurations:
Typical DMZ Configuration
In the most typical DMZ configuration, servers residing in the DMZ each use a single Ethernet interface that is configured on a private subnet. All traffic to and from the DMZ, between the DMZ and both the LAN and the Internet/WAN, is managed by the Corente Services Gateway.
Alternate DMZ Configurations
There are two other possible DMZ configurations, both of which require two Ethernet interfaces on each server in the DMZ: one interface is on the same private subnet as the Corente Services Gateway’s DMZ interface, and the other interface is on either the LAN side of the DMZ or the Internet/WAN side of the DMZ.
When the additional interface is on the LAN side of the DMZ, the gateway will handle security only for traffic between the Internet/WAN and the DMZ.
The DMZ to Internet Access partner is used. You should not configure the LAN to DMZ Access partner.
When the additional interface is on the Internet/WAN side of the DMZ, the Corente Services Gateway will handle security only for traffic between the LAN and the DMZ.
The LAN to DMZ Access partner is used. You should not configure the DMZ to Internet Access partner.
This means that, for both alternate configurations, you must supply your own security measures for the side that is not being protected by the gateway.