Configuring an EVS Controller
You must configure only one compute node as an EVS controller in your network and then set the EVS controller on each EVS node so that the EVS nodes can communicate with the EVS controller. However, you need to set the properties for the EVS controller only once from any node that can communicate with the EVS controller. You use the evsadm set-controlprop command to set the properties for the EVS controller. For more information, see How to Configure an EVS Controller.
You can also reset the properties for an EVS controller. Example 51, Resetting Properties for an EVS Controller shows how to reset a property for an EVS controller. For information about the EVS controller and its properties, see EVS Controller.
To simplify the configuration of an elastic virtual switch, you need to connect as evsuser. When you install the mandatory EVS package (service/network/evs), a special user, evsuser, is created and assigned with the Elastic Virtual Switch Administration rights profile. This profile contains all the authorizations and privileges to perform the EVS operations. To use evsuser, you need to set the controller property as follows:
# evsadm set-prop -p controller=ssh://evsuser@evs-controller-hostname-or-IP-address
In addition, you must set up the SSH authentication by using the preshared public key between the host where you run the evsadm command and the EVS controller.
Note - To perform the EVS operations, you need to be superuser or a user that has the Elastic Virtual Switch Administration rights profile. For more information, see Security Requirements for Using EVS.
Setting Up SSH Authentication
You need SSH authentication with the preshared public key for the evsadm command to communicate with the EVS controller non-interactively and securely. You need to set up the SSH authentication with the preshared public key for evsuser between the following components in the EVS setup:
-
EVS manager and EVS controller – Append the public key of the administrator or the user running the evsadm command on the EVS manager in the /var/user/evsuser/.ssh/authorized_keys file on the EVS controller.
-
EVS nodes and EVS controller – Append the public key of the root user on each EVS node in the /var/user/evsuser/.ssh/authorized_keys file on the EVS controller. You need to append these public keys because the zoneadmd daemon runs as root. This daemon connects to the EVS controller and retrieves configuration information for the VNIC anet resource. For more information, see the zoneadmd(1M) man page.
-
EVS controller and EVS nodes – Append the public key of evsuser on the EVS controller in the /var/user/evsuser/.ssh/authorized_keys file on each EVS node as the EVS controller communicates with each of the EVS node for setting VPort properties.
If the EVS components are in a single host, you can use the unix RAD connection to set up authentication. The command syntax is:
# evsadm set-prop -p controller=unix://
For more information, see Per-EVS Node Connection.
The following figure shows the setting up of SSH authentication between the EVS components.
Figure 19 SSH Authentication in the EVS Setup
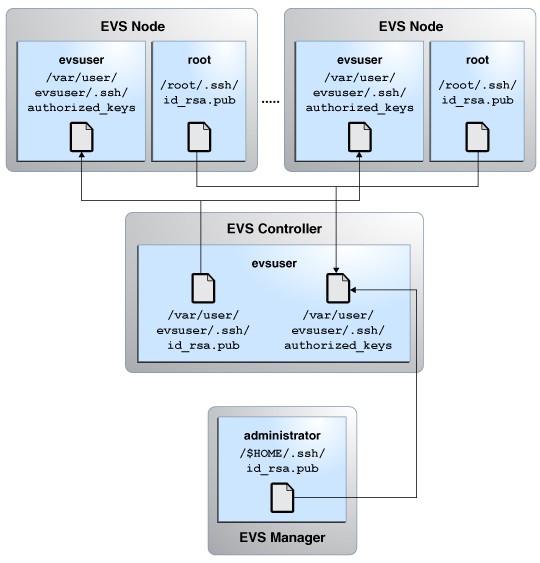
After you set up the SSH authentication, you need to specify the EVS controller. The assumption is that the controller property is set to ssh://evsuser@evs-controller.example.com on the EVS nodes, EVS manager, and EVS controller.
The following procedures show how to set up the SSH authentication.
How to Set Up SSH Authentication Between an EVS Node and the EVS Controller
-
Become an administrator.
For more information, see Using Your Assigned Administrative Rights in Securing Users and Processes in Oracle Solaris 11.3.
-
Generate a RSA key pair in the EVS node.
evs-node# ssh-keygen -t rsa Generating public/private rsa key pair. Enter file in which to save the key (/root/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /root/.ssh/id_rsa. Your public key has been saved in /root/.ssh/id_rsa.pub. The key fingerprint is: a0:64:de:3d:c8:26:59:cb:4a:46:b9:1d:17:04:7d:bf root@evs-node
- Copy the public key from the /root/.ssh/id_rsa.pub file in the EVS node to the /var/user/evsuser/.ssh/authorized_keys file in the EVS controller.
-
Log in to the EVS controller as evsuser from
the EVS node to verify whether the SSH authentication is set
up.
evs-node# ssh evsuser@evs-controller The authenticity of host 'evs-controller (192.0.2.10)' can't be established. RSA key fingerprint is 73:66:81:15:0d:49:46:e0:1d:73:32:77:4f:7c:24:a5. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added 'evs-controller' (RSA) to the list of known hosts. Last login: Wed Jun 11 14:36:28 2014 from evs-controller Oracle Corporation SunOS 5.11 11.2 April 2014 evsuser@evs-controller$
The output shows that you can log in to the EVS controller as evsuser without a password from the EVS node.
How to Set Up SSH Authentication Between the EVS Manager and the EVS Controller
-
Become an administrator.
For more information, see Using Your Assigned Administrative Rights in Securing Users and Processes in Oracle Solaris 11.3.
-
Generate a RSA key pair in the EVS manager.
evs-manager# ssh-keygen -t rsa Generating public/private rsa key pair. Enter file in which to save the key (/root/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /root/.ssh/id_rsa. Your public key has been saved in /root/.ssh/id_rsa.pub. The key fingerprint is: a0:64:de:3d:c8:26:59:cb:4a:46:b9:1d:17:04:7e:bf root@evs-manager
- Copy the public key from the /root/.ssh/id_rsa.pub file in the EVS manager to the /var/user/evsuser/.ssh/authorized_keys file in the EVS controller.
-
Log in to the EVS controller as evsuser from
the EVS manager to verify whether the SSH authentication is set
up.
evs-manager# ssh evsuser@evs-controller The authenticity of host 'evs-controller (192.0.2.10)' can't be established. RSA key fingerprint is 73:66:81:15:0d:49:46:e0:1d:73:32:77:4f:7c:24:a5. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added 'evs-controller' (RSA) to the list of known hosts. Last login: Wed Jun 11 14:38:28 2014 from evs-controller Oracle Corporation SunOS 5.11 11.2 April 2014 evsuser@evs-controller$
The output shows that you can log in to the EVS controller as evsuser without a password from the EVS manager.
How to Set Up SSH Authentication Between the EVS Controller and an EVS Node
-
Become an administrator.
For more information, see Using Your Assigned Administrative Rights in Securing Users and Processes in Oracle Solaris 11.3.
-
Become the user, evsuser, in the EVS
controller.
evs-controller# su - evsuser
For more information, see Using Your Assigned Administrative Rights in Securing Users and Processes in Oracle Solaris 11.3.
-
Generate a RSA key pair in the EVS controller for
evsuser.
evsuser@evs-controller$ ssh-keygen -t rsa Generating public/private rsa key pair. Enter file in which to save the key (/var/user/evsuser/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /var/user/evsuser/.ssh/id_rsa. Your public key has been saved in /var/user/evsuser/.ssh/id_rsa.pub. The key fingerprint is: a0:64:de:3d:c8:26:59:cb:4a:46:b9:1e:17:04:7d:bf evsuser@evs-controller
- Copy the public key from the /var/user/evsuser/.ssh/id_rsa.pub file in the EVS controller to the /var/user/evsuser/.ssh/authorized_keys file in the EVS node.
-
Log in to the EVS node as evsuser from the EVS
controller to verify whether the SSH authentication is set
up.
evsuser@evs-controller$ ssh evsuser@evs-node The authenticity of host 'evs-node (192.0.2.20)' can't be established. RSA key fingerprint is 73:66:89:15:0d:49:46:e0:1d:73:32:77:4f:7c:24:a5. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added 'evs-node' (RSA) to the list of known hosts. Last login: Wed Jun 11 14:40:28 2014 from evs-node Oracle Corporation SunOS 5.11 11.2 April 2014 evsuser@evs-node$
The output shows that you can log in to the EVS node as evsuser without a password from the EVS controller.

Caution - If you do not set up the SSH authentication in the EVS setup, the evsadm command cannot communicate with the EVS controller non-interactively and securely.
Per-EVS Node Connection
You can configure node RAD connection by using the uri-template controller property. You can specify either ssh://[username@] or unix://[username@] values for the uri-template property. The default value of this property is ssh://. The RAD URI that is used to connect to an EVS node is derived from the uri-template property by the EVS controller.
Example 49 Connecting to an EVS NodeThe following example displays the value for the uri-template property.
# evsadm show-controlprop -p uri-template PROPERTY PERM VALUE DEFAULT HOST uri-template rw ssh:// ssh:// --
The output shows that all the EVS controller uses the RAD SSH to connect to all of the EVS nodes. The SSH user is the user connected to the EVS controller.
The following example shows how to connect to an EVS node as evsuser by using the uri-template property.
# evsadm set-controlprop -p uri-template=ssh://evsuser@ # evsadm show-controlprop -p uri PROPERTY PERM VALUE DEFAULT HOST uri-template rw ssh://evsuser@ ssh:// --
The output shows that all the per-EVS node RAD connections must use SSH. However, the SSH user must use evsuser instead of the SSH user connected to the EVS controller. For example, consider that an EVS client connects to the EVS controller as ssh://user1@controller.example.com. If uri-template is set to ssh://evsuser@, then instead of using user1 as the SSH user the EVS controller uses evsuser as the SSH user.
The following example shows how to set up authentication on a single system that contains all the EVS components by using the uri-template property.
# evsadm set-controlprop -p uri-template=unix:// # evsadm show-controlprop -p uri-template PROPERTY PERM VALUE DEFAULT HOST uri-template rw unix:// unix:// --
If the EVS Controller is set up on one of the EVS nodes, then you can use AF_UNIX for the EVS node instead of SSH as shown in the following example.
# evsadm set-controlprop -h evs-controller.example.com -p uri-template=unix:// # evsadm show-controlprop -p uri-template PROPERTY PERM VALUE DEFAULT HOST uri-template rw ssh:// ssh:// -- uri-template rw unix:// unix:// evs-controller.example.com
The output shows that all the per-EVS node RAD connection must use the default SSH except for the host evs-controller.example.com where you need to use AF_UNIX.
How to Configure an EVS Controller
Before You Begin
Set up the SSH authentication with the preshared keys between the host where you run the evsadm command and the EVS controller.
-
Become an administrator or user with the Elastic Virtual Switch
Administration rights profile.
For more information, see Using Your Assigned Administrative Rights in Securing Users and Processes in Oracle Solaris 11.3.
-
Set the EVS controller.
# evsadm set-prop -p controller=[value[...,]]
This command sets the values of a property for the host where the command is executed. The only supported property is controller, which can be of the format ssh://[user@]evs-controller-host-name, ssh://[user@]evs-controller-IP-address, or unix://.
- (Optional)
Display the configured EVS controller.
# evsadm show-prop [[-c] -o field[,...]] [-p controller[,...]]
For more information, see Displaying the EVS Controller.
-
Set the properties for the EVS controller.
# evsadm set-controlprop [-h host] -p prop=[value[...,]]
For more information, see Setting Properties for an EVS Controller.
- (Optional)
Display the properties of an EVS controller.
# evsadm show-controlprop [[-c] -o field[,...]] [-p prop[,...]]
For more information, see Displaying Properties of an EVS Controller.
The following example shows how to configure the host s11-server as the EVS controller, whose L2 segments are created by using a VXLAN.
# evsadm set-prop -p controller=ssh://evsuser@s11-server # evsadm show-prop PROPERTY PERM VALUE DEFAULT controller rw ssh://evsuser@s11-server -- # evsadm set-controlprop -p l2-type=vxlan # evsadm set-controlprop -p vxlan-range=10000-20000 # evsadm set-controlprop -p vxlan-addr=192.0.2.0/24 # evsadm set-controlprop -h s11-server -p uplink-port=net3 # evsadm set-controlprop -h s11-client -p uplink-port=net4 # evsadm show-controlprop PROPERTY PERM VALUE DEFAULT HOST l2-type rw vxlan vlan -- uplink-port rw -- -- -- uplink-port rw net3 -- s11-server uplink-port rw net4 -- s11-client uri-template rw ssh:// ssh:// -- uuid r- b3fda654-c14c-11e4-ae16-5f67bed8a8e9 -- -- vlan-range rw -- -- -- vlan-range-avail r- -- -- -- vxlan-addr rw 192.0.2.0/24 0.0.0.0 -- vxlan-ipvers rw v4 v4 -- vxlan-mgroup rw 0.0.0.0 0.0.0.0 -- vxlan-range rw 10000-20000 -- -- vxlan-range-avail r- 10000-20000 -- -- # evsadm show-controlprop -o property,value,vlan_range,vxlan_range, \ flat,host -p uplink-port PROPERTY VALUE VLAN_RANGE VXLAN_RANGE FLAT HOST uplink-port -- -- -- no -- uplink-port net3 -- 10000-20000 yes s11-server uplink-port net4 -- 10000-20000 yes s11-client
In this example, the vxlan-range-avail property displays the VXLAN IDs (10000-20000) that are available for implementing elastic virtual switches. An IP interface that is part of the subnet 192.0.2.0/27 is used to create the VXLAN links on the EVS nodes.
The following example shows how to configure a host with the IP address 192.0.2.1 as the EVS controller, whose L2 segments are created by using a VLAN.
# evsadm set-prop -p controller=ssh://evsuser@192.0.2.1 # evsadm set-controlprop -p l2-type=vlan # evsadm set-controlprop -p vlan-range=200-300,400-500 # evsadm set-controlprop -p uplink-port=net2 # evsadm set-controlprop -h host2.example.com -p uplink-port=net3 # evsadm set-controlprop -h host3.example.com -p uplink-port=net4
The output shows that the VLAN IDs 200-300 and 400-500 are set aside for elastic virtual switches. The datalink net2 is uplink-port on all the hosts except for host2.example.com and host3.example.com. On host2, the datalink net3 is used as uplink-port and on host3, the datalink net4 is used as uplink-port.
You can optionally specify the vlan-range or vxlan-range properties with the uplink-port property. See Example 47, Setting Uplink Port with VLAN and VXLAN Ranges for the EVS Controller.
Example 51 Resetting Properties for an EVS ControllerThe following example shows how to reset the controller property uplink-port.
# evsadm show-controlprop -p uplink-port PROPERTY PERM VALUE DEFAULT HOST uplink-port rw net2 -- -- # evsadm set-controlprop -p uplink-port= # evsadm show-controlprop -p uplink-port PROPERTY PERM VALUE DEFAULT HOST uplink-port rw -- -- --