| Skip Navigation Links | |
| Exit Print View | |
|
Oracle® ZFS Storage Appliance Administration Guide |
Chapter 1 Oracle ZFS Storage Appliance Overview
Chapter 3 Initial Configuration
Chapter 4 Network Configuration
Chapter 5 Storage Configuration
Chapter 6 Storage Area Network Configuration
Chapter 8 Setting ZFSSA Preferences
Chapter 10 Cluster Configuration
Configuring Services Using the BUI
Viewing a Specific Service Screen
Viewing a Specific Service Screen
Configuring Services Using the CLI
iSCSI Service Targets and Initiators
SMB Microsoft Stand-alone DFS Namespace Management Tools Support Matrix
Example: Manipulating DFS Namespaces
Adding a User to an SMB Local Group
Active Directory Configuration
Project and Share Configuration
SMB Data Service Configuration
Allowing FTP Access to a share
HTTP Authentication and Access Control
Allowing HTTP access to a share
NDMP Local vs. Remote Configurations
Allowing SFTP access to a share
Configuring SFTP Services for Remote Access
Allowing TFTP access to a share
Configuring virus scanning for a share
Adding an appliance administrator from NIS
Adding an appliance administrator
Active Directory Join Workgroup
Active Directory Domains and Workgroups
Active Directory Windows Server 2012 Support
Active Directory Windows Server 2008 Support
Active Directory Windows Server 2008 Support Section A: Kerberos issue (KB951191)
Active Directory Windows Server 2008 Support Section B: NTLMv2 issue (KB957441)
Active Directory Windows Server 2008 Support Section C: Note on NTLMv2
Configuring Active Directory Using the BUI
Configuring Active Directory Using the CLI
Example - Configuring Active Directory Using the CLI
Identity Mapping Rule-based Mapping
Identity Mapping Directory-based Mapping
Mapping Rule Directional Symbols
Identity Mapping Best Practices
Identity Mapping Case Sensitivity
Identity Mapping Domain-Wide Rules
RIP and RIPng Dynamic Routing Protocols
Registering the Appliance Using the BUI
Registering the Appliance Using the CLI
Configuring SNMP to Serve Appliance Status
Configuring SNMP to Send Traps
Receiver Configuration Examples
Configuring a Solaris Receiver
Chapter 12 Shares, Projects, and Schema
The Microsoft Management Console (MMC) is an extensible framework of registered components, known as snap-ins, that provide comprehensive management features for both the local system and remote systems on the network. Computer Management is a collection of Microsoft Management Console tools, that may be used to configure, monitor and manage local and remote services and resources.
In order to use the MMC functionality on the Sun ZFS Storage 7000 appliances in workgroup mode, be sure to add the Windows administrator who will use the management console to the Administrators local group on the appliance. Otherwise you may receive an Access is denied or similar error on the administration client when attempting to connect to the appliance using the MMC.
The Sun ZFS Storage 7000 appliances support the following Computer Management facilities:
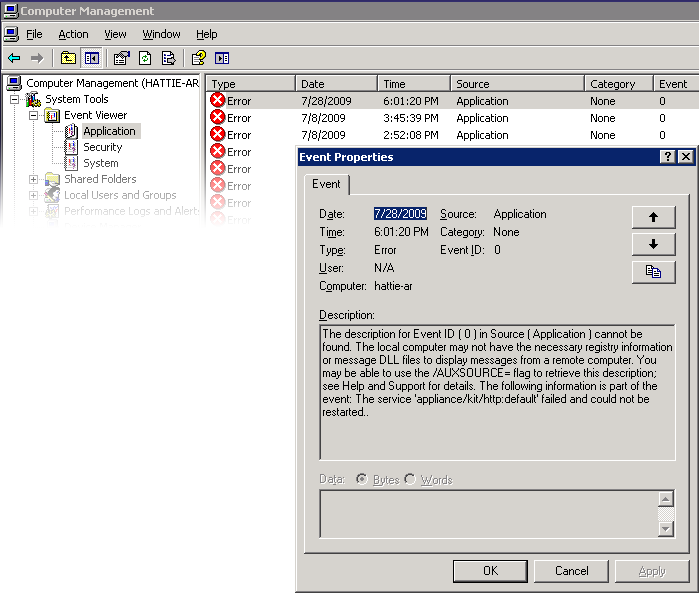
Display of the Application log, Security log, and System log are supported using the Event Viewer MMC snap-in. These logs show the contents of the alert, audit, and system logs of the Sun ZFS Storage 7000 system. Following is a screen capture that illustrates the Application log and the properties dialog for an error event.
Figure 11-3 SMB Event Viewer
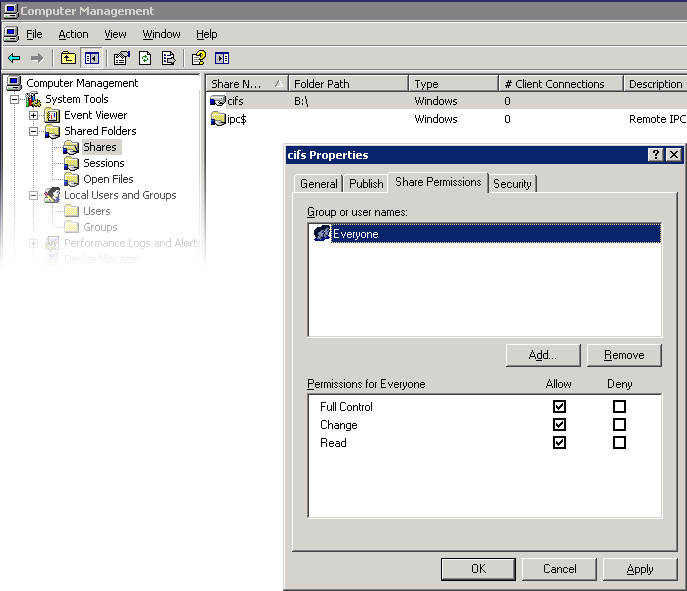
Support for share management includes the following:
Listing shares
Setting ACLs on shares
Changing share permissions
Setting the description of a share
Features not currently supported via MMC include the following:
Adding or Deleting a share
Setting client side caching property
Setting maximum allowed or number of users property
Figure 11-4 SMB Share Permission Properties
The following features are supported:
Viewing local SMB users and groups
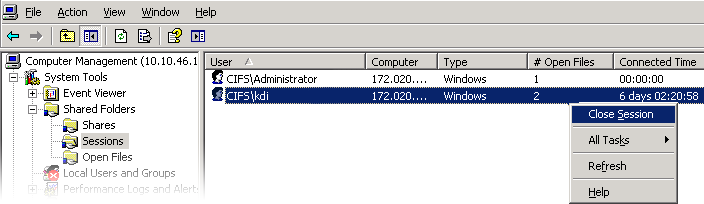
Listing user connections, including listing the number of open files per connection
Closing user connections
Listing open files, including listing the number of locks on the file and file open mode
Closing open files
Figure 11-5 Open Files per Connection
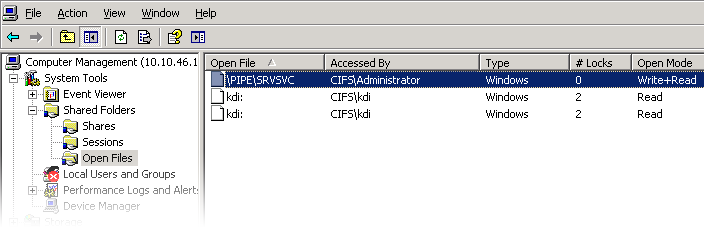
Figure 11-6 Open Sessions
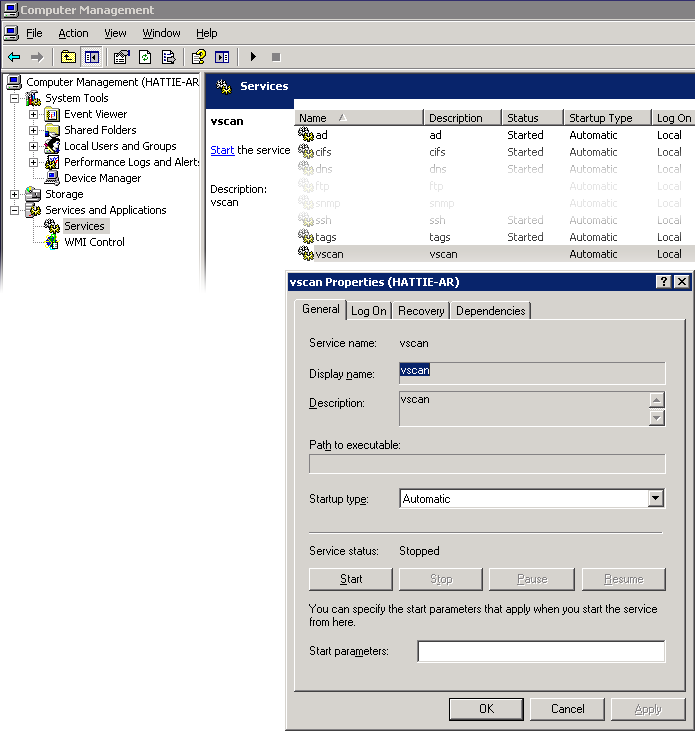
Support includes listing of ZFSSA services. Services cannot be enabled or disabled using the Computer Management MMC application. Following is a screen capture that illustrates General properties for the vscan Service.
Figure 11-7 vscan Properties
To ensure that only the appropriate users have access to administrative operations there are some access restrictions on the operations performed remotely using MMC.
|