Contents
A Relative Path binds policies to a specific relative path location
(for example /test/path). When the API Gateway receives a request on the specified
Relative Path, it invokes the specified policy or policy chain. This topic explains how to
configure Relative Path resolvers. For details on how to configure policies, see Part 4, “Policy Governance”.
You can use a Static Content Provider or Static File Provider to serve static HTTP content or files from a particular directory. In this case, the API Gateway instance acts as a Web server. The API Gateway instance can also act as a Servlet Application container, which enables you to drop servlets into the HTTP Services configuration. This should only be used by developers with specific requirements under strict advice from the Oracle Support team.
Relative Paths can have nested child resolvers of the following type:
-
Relative Path
-
Static Content Provider
-
Static File Provider
-
Servlet Application
This topic explains how to use the Policy Studio to configure each of these Relative Path resolver types. For details on configuring HTTP Services Groups and HTTP Interfaces, see Configuring HTTP Services.
To configure a Relative Path for a specific HTTP Service Group (for example, Default Services), perform the following steps:
-
In the Policy Studio tree, select Listeners -> API Gateway -> Default Services -> Paths.
-
Right-click Paths, and select Add -> Relative Path. You can also click the Add button in the screen on the right.
-
In the Configure Relative Path dialog, specify whether to enable listening on the specified path using the Enable this path resolver setting, which is set by default.
Alternatively, when editing a policy, you can click the Add Relative Path button at the bottom of the policy canvas beside the Context drop-down list.
The next four sections explain how to configure the settings on the Configure Relative Path dialog.
Use the Policies tab to specify the Relative Path and the policies that are called. The API Gateway invokes the selected policies when it receives a request on the specified path. You can specify a single policy or a chain of policies. Policies are called in the order displayed on this tab. Complete the following fields:
| When a request arrives that matches the path: |
Enter a Relative Path (for example, /test/path) for the selected
HTTP Services Group. Requests received on this Relative Path are processed
by the policies selected on this tab.
|
| Global Request Policy | If a global request policy is configured, when you select this setting, the global request policy is called first in the policy chain. For more details, see Configuring Global Policies. |
| Path Specific Policy | To configure a path-specific policy, select this setting, and browse to select a policy from the dialog. You can search for a specific policy by entering its name in the text box, and the policy tree is filtered automatically. The Path Specific Policy field is auto-populated with the currently selected policy when the dialog is launched using the Add Relative Path button at the bottom of the policy canvas. |
| Global Response Policy | If a global response policy is configured, when you select this setting, the global response policy is called last in the policy chain. For more details, see Configuring Global Policies. |
When you select multiple policies to form a policy chain, the behavior is the same as for a policy shortcut chain filter. Policies are only evaluated when selected, and when the policy can be reached. If any reachable policy fails, the chain fails, and no more policies are evaluated.
The Audit Settings tab enables you to configure the logging level for all filters executed on the Relative Path, and to configure when message payloads are logged.
Logging Level
You can configure the following settings on all filters executed on the specified Relative Path:
| Logging Level | Description |
| Fatal | Logs Fatal log points that occur on all filters executed. |
| Failure | Logs Failure log points that occur on all filters executed. This is the default logging level. |
| Success | Logs Success log points that occur on all filters executed. |
For more details on logging levels, and on how to configure logging for a specific filter, see the Transaction Log Level and Message topic.
Payload Level
You can configure the following settings on the specified Relative Path:
| Payload Logging | Description |
| On receive request from client | Log the message payload when a request arrives from the client. |
| On send response to client | Log the message payload before the response is sent back to the client. |
| On send request to remote server | Log the message payload before the request is sent using any Connection or Connect to URL filters deployed in any policies executed. |
| On receive response from remote server | Log the message payload when the response is received using any Connection or Connect to URL filters deployed in any policies executed. |
For details on how to log message payloads at any point in a specific policy, see the Log Message Payload topic.
Access Log
Select the Include in server access log records setting if you wish to add this Relative Path to the API Gateway Access Log. This enables the Access Log at the service level. This setting is not selected by default. For more details, see the topic on Access Log Settings.
The HTTP Method tab enables you to configure an accepted HTTP Method
(for example, POST). The default is *, which means that all
HTTP Methods are accepted. You can override the default behavior, and select an
appropriate HTTP method for the Relative Path from the list.
You can also configure multiple HTTP methods on paths of the same name. This enables you to call different policies for different HTTP methods, as shown in the following example:
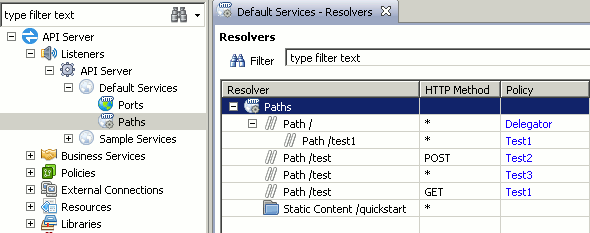
In this example, the /test path is configured three times, each using a
different HTTP Method as follows:
-
If a
GETrequest is sent to the API Gateway on the/testpath, theTest1policy is executed. -
If a
POSTrequest is sent, theTest2policy is executed. -
If any other type of request is sent (for example,
DELETE,PUT, and so on), theTest3policy is executed.
For details on the subpath shown in this example (Path/Test1),
see the section called “Nested Relative Paths”.
On the Advanced tab, select whether to resolve this Relative Path using
an Exact path match. The default behavior is to use a longest path match
(explained in the next section). This setting enables you to further restrict the match to
an exact path match (for example, test1/helloService). This setting is not
selected by default.
Using the example shown in the section called “HTTP Method Settings”, when you
have a path / that has a child subpath (in this case /test1),
the following occurs when a request arrives at the API Gateway:
-
Incoming request with path
/test1is received. -
Request is resolved against
/(using the longest path match algorithm). -
API Gateway checks if there are any children (in this case, there is
/test1). -
API Gateway checks if any children can process the request (
/test1is a match). -
Path resolution is successful.
From a policy execution point of view, when the request is being processed, each policy associated
with a matching path is executed. In the above example, both / and /test1
make up the match. This means that the policy associated with / is executed first, and
if that passes, the policy associated with /test1 is executed. The parent policy uses
the Call Internal Service filter, which enables child resolvers to be invoked.
Nested paths are generally used as a protection mechanism. For example, a system might be configured
with / as the only root path, with a number of children. / could have a
Role-Based Access Control (RBAC) policy associated with it protecting all children. If the RBAC
policy succeeds, access is granted, and the child policy is executed. If it fails, access is denied.
This mechanism is implemented in the Admin Node Manager. You can view this in Policy Studio by opening the
Admin Node Manager configuration.
![[Note]](../common_oracle/images/admon/note.png) |
Note |
|---|---|
|
The difference between |
Adding a Nested Relative Path
To add a child node to a Relative Path, right-click the appropriate Relative Path node in the Resolvers screen, and select the node type (for example, Add -> Relative Path). You can add child resolver nodes of the following type:
-
Relative Path
-
Static Content Provider
-
Servlet Application
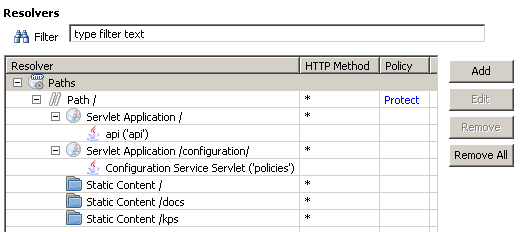
In the following example, there is one main Relative Path configured to /,
which calls the Protect policy. Content is served by the underlying
Servlet Application and Static Content resolvers only when the Protect
policy succeeds:
![[Important]](../common_oracle/images/admon/important.png) |
Important |
|---|---|
|
The parent policy (in this case, Protect) must use the Call Internal Service filter. This acts as a loopback and enables child resolvers to be invoked. When this prerequisite is met, you can add nested Relative Paths as required. |
Order of Resolution
The order of resolution for nested Relative Paths is to first resolve at the parent level. If resolution is successful, and there are children present, then attempt to resolve at the child level. There is no precedence between resolver node types (Relative Path, Static Content Provider, and Servlet Application). Path resolution is performed using the longest path match algorithm by default, regardless of whether nested subpaths are used. For details on configuring an exact path match, see the section called “Advanced Settings”.
Example Nested Path Resolution
Using the example Relative Path in the screen above, consider the following inbound requests to the Node Manager:
https://testpc:8090/api/deployment/domain/deployments https://testpc:8090/common/themes/blue/images/server_icon.png
The /api/deployment/domain/deployments request is resolved as follows:
-
Matches the root relative path
/as a longest path match -
Matches Servlet Application
/as a longest path match (1 char) -
Matches Servlet
/apias a longest path match (4 char) -
Matches Static Content
/as a longest path match (1 char) -
Does not match Servlet Application
/configuration -
Does not match Static Content
/docs -
Does not match Static Content
/kps
In this example, there are two matches, the api Servlet under the Servlet Application
on /, and the Static Content on /. Because the API Gateway uses the longest
path match, the api Servlet wins, and the request is routed to that resolver. There is
no precedence between resolvers, all resolvers are queried for a match.
The /common/themes/blue/images/server_icon.png request is resolved as follows:
-
Matches the root relative path
/as a longest path match -
Matches Servlet Application
/as a longest path match (1 char) -
Does not match Servlet
/api -
Matches Static Content
/as a longest path match (1 char) -
Does not match Servlet Application
/configuration -
Does not match Static Content
/docs -
Does not match Static Content
/kps
In this example, there is only one match, the Static Content on /. In this case,
the Servlet Application on / is not considered because none of its children can
resolve the request path.
![[Note]](../common_oracle/images/admon/note.png) |
Note |
|---|---|
|
If there are two resolver matches, and each matches on the same path length, the last resolver visited during path resolution is used, in the order in which the resolver was read and loaded from the configuration. |
A Static Content Provider can be used with an HTTP Interface to serve
static content from a specified directory. A Relative Path is associated with each Static
Content Provider so that requests received on this path are dispatched directly to the
provider and are not mapped to a policy in the usual way. For example, you can configure a
Static Content Provider to serve content from the c:\docs folder on
Windows when it receives requests on the Relative Path /docs.
Adding a Static Content Provider
To add a Static Content Provider to an HTTP Services group (for example, Default Services), perform the following steps:
-
Select Listeners -> API Gateway -> Default Services -> Paths.
-
Right-click Paths, and select Add -> Static Content Provider.
-
Complete the following fields on the General tab:
Relative Path:
Enter the path that you want to receive requests for static content on.
Content Directory:
Enter or browse to the location of the directory that you want to serve static content from.
Index File:
Enter the name of the file that you want to use as the index file for
content retrieved from the directory specified in the field above. This
file is retrieved by default if no resource is explicitly specified in the
request URI. For example, if the client requests
http://[HOST]:8080/docs (with only a relative path specified
instead of a specific resource), the file specified here will be retrieved.
This file must exist in the directory specified in the previous field.
Allow Directory Listings:
If this option is selected, the Static Content Provider returns
full directory listings for requests specifying a Relative Path only.
For example, if this is selected, and if a request is received for
http://[HOST]:8080/docs/samples, the list of directories
under this directory is returned, assuming that this directory exists on
the file system. You can turn this off to prevent attacks where a hacker
can send up different request URIs in the hope that the server returns
some information about the directory structure of the server.
HTTP Method:
The HTTP Method tab enables you to configure an accepted
HTTP Method (for example, POST). The default is *,
which means that all HTTP Methods are accepted. You can override the default
behavior, and select an appropriate HTTP method for this resolver from the list.
For more details, see the section called “HTTP Method Settings”.
A Static File Provider can be used with an HTTP Interface to serve
a static file from a specified directory. A Relative Path is associated with each Static
File Provider so that requests received on this path are dispatched directly to the file
provider and are not mapped to a policy in the usual way. For example, you can configure
a Static File Provider to serve c:\my_brand\favicon.ico on Windows
when it receives requests on the /favicon.ico Relative Path.
Adding a Static File Provider
To add a Static File Provider to an HTTP Services group (for example, Default Services), perform the following steps:
-
Select Listeners -> API Gateway -> Default Services -> Paths.
-
Right-click Paths, and select Add -> Static File Provider.
-
Complete the following fields on the General tab:
Relative Path:
Enter the path that you want to receive requests for the static file on
(for example, /favicon.ico).
File:
Enter or browse to the location of static file that you want to serve (for example,
$VDISTDIR/webapps/emc/favicon.ico, where $VDISTDIR specifies
the directory in which the API Gateway is installed).
HTTP Method:
The HTTP Method tab enables you to configure an accepted
HTTP Method for the static file. The default is GET, which means
that only HTTP GET calls are accepted. You can override the default behavior,
and select a different HTTP method for this resolver from the list. For more
details, see the section called “HTTP Method Settings”.
Developers may wish to write their own Java servlets and deploy them under the API Gateway to serve HTTP traffic. Conversely, they may wish to remove some of the default servlets from the out-of-the-box configuration (for example, to remove the ability to view logging remotely). This pairing down of unwanted functionality may be required to further lock down the machine on which the API Gateway is running.
![[Note]](../common_oracle/images/admon/note.png) |
Note |
|---|---|
|
Adding and removing Servlet Applications should be performed only by developers with very specific requirements and under strict guidance from the Oracle Support team. These instructions simply outline how to configure the fields on the dialogs used to set up Servlet Applications. For more detailed instructions, please contact the Oracle Support Team. |
When editing Admin Node Manager or API Gateway Analytics configuration, there are some default
Servlet Applications available under the Management Services
group. By default, this HTTP Services Group is not displayed, but can be displayed
using the Preferences dialog in the Policy Studio. For example,
the /configuration/ Servlet Application updates configuration
information for the API Gateway.
![[Warning]](../common_oracle/images/admon/warning.png) |
Warning |
|---|---|
|
Deleting any of the default Servlet Applications may prevent the API Gateway from functioning correctly. You should only delete default Servlet Applications under strict supervision of the Oracle Support team. |
Adding a Servlet Application
To add a Servlet Application to an HTTP Services Group (for example, Default Services), perform the following steps:
-
Select Listeners -> API Gateway -> Default Services -> Paths.
-
Right-click Paths, and select Add -> Servlet Application.
-
Complete the following fields on the General tab:
Relative Path:
Enter the servlet context in this field. You can add multiple servlets under this context, where each servlet is mapped to a unique URI.
Session Timeout:
Enter the timeout in seconds after which an inactive session is closed. Click OK.
HTTP Method:
The HTTP Method tab enables you to configure an accepted
HTTP Method (for example, POST). The default is *,
which means that all HTTP Methods are accepted. You can override the default
behavior, and select an appropriate HTTP method for this resolver from the list.
For more details, see the section called “HTTP Method Settings”.
Adding a Servlet
The new Servlet Application now appears in the Resolvers screen. To add a new servlet, right-click the new Servlet Application, and select Add Servlet. Configure the following fields on the Servlet dialog:
URI:
The path entered here maps incoming requests on a particular request URI to the Java servlet class entered in the field below. This path must be unique across all Servlets that are added under this Servlet Application (servlet context).
Class:
Enter the fully qualified class name of the servlet class. You can add this
class to the server runtime by adding the JAR, class file, or package hierarchy
to the [VDISTDIR]/ext/lib folder. VDISTDIR
is your API Gateway distribution directory, which is the location where the API Gateway
is installed.
Read Timeout:
Specify the time in seconds that the servlet should wait before closing an idle connection.
Servlet Properties:
You can configure properties for each servlet by clicking the Add button, and entering a name and value in the fields provided on the Properties dialog.
A Web Service Resolver is used to identify messages destined for a Web Service, and to map them to the Service Handler (Web Service Filter) for that Web Service. When you import a WSDL file in the Web Service Repository, a new Web Service Resolver node is created for each imported Web Service under the Paths for the relevant HTTP Services group (for example, Default Services). You can edit the Web Service Resolver settings by right-clicking its tree node, and selecting Edit.
The following settings are available in the Web Service Resolver dialog:
Enable this web service resolver:
Specify whether to enable this Web Service resolver. This is enabled by default.
Name:
You can edit the name of the Web Service Resolver.
Web Service:
Click the browse button to select a Web Service to resolve to. Defaults to the Web Service imported into the Web Services Repository when this resolver was created.
Policies:
On the Policies tab, select the path and the policies to use for the Web Service. You can specify a single policy or a chain of policies. Policies are called in the order displayed on this tab. The global request policy, the policy automatically generated when the WSDL file is imported, and the global response policy are all selected in a chain by default. Complete the following fields:
| Matches the paths in the WSDL: | Select this option if you want the resolver to use the paths specified in the WSDL file. This is the default. |
| Matches this path: | Select this option if you want to specify a different path from the WSDL file, and enter the path. |
| Global Request Policy | If a global request policy is configured, when you select this setting, the global request policy is called first in the policy chain. For more details, see Configuring Global Policies. |
| Path Specific Policy | To configure a path-specific policy, select this setting, and browse to select a policy from the dialog. |
| Global Response Policy | If a global response policy is configured, when you select this setting, the global response policy is called last in the policy chain. For more details, see Configuring Global Policies. |
Policies are only evaluated when selected, and when the policy can be reached. If any selected policy fails, the chain fails, and no more policies are evaluated.
Audit Settings:
The Audit Settings tab enables you to configure the logging level for all
filters executed on the Web Service, and to configure when message payloads are logged. The
default logging level for all filters on the Web Service is Failure. These logging
settings are the same as those already described for the Relative Path. For more details, see
the section called “Audit Settings”.
HTTP Method:
The HTTP Method tab enables you to configure an accepted HTTP Method (for
example, POST). The default is *, which means that all HTTP Methods
are accepted. You can override the default behavior, and select an appropriate HTTP method from
the list. The HTTP Method settings are the same as those already described
for the Relative Path. For more details, see the section called “HTTP Method Settings”.
Editing Service Handler Options
You also edit options for the Service Handler for the Web Service. Right-click the Web Service Resolver node, and select Quick-Edit Policy to display a dialog that enables you to configure the following options:
| Validation | If you wish to use a dedicated validation policy for all messages sent to the Web Service, select this checkbox, and click the browse button to configure a policy in the dialog. For example, this enables you to delegate to a custom validation policy used by multiple Web Services. |
| Routing | If you wish to use a dedicated routing policy to send all messages on to the Web Service, select this checkbox, and click the browse button to configure a policy in the dialog. For example, this enables you to delegate to a custom routing policy used by multiple Web Services. |
| WSDL Access Options | Select whether to make the WSDL for this Web Service available to clients. The Allow the API Gateway to publish WSDL to clients checkbox is selected by default. The published WSDL represents a virtualized view of the Web Service. Clients can retrieve the WSDL from the API Gateway, generate SOAP requests, and send them to the API Gateway, which routes them on to the Web Service. |
These options enable you to configure the underlying auto-generated Service Handler (Web Service Filter) without navigating to it in the Policies tree. These are the most commonly modified Web Service Filter options after importing a WSDL file. Changes made in this dialog are visible in the underlying Web Service Filter. For more details, see the Web Service Filter topic.