Contents
This topic explains some of the main components and concepts used in Oracle API Gateway management, and shows examples of how they are displayed in the API Gateway management tools such as Policy Studio and API Gateway Explorer. For example, these include concepts such as filters, policies, message attributes, and listeners. For details on the core API Gateway architecture, see the API Gateway Concepts Guide. For example, this includes concepts such as API Gateway instances, groups, Node Manager, Admin Node Manager, and so on.
A filter is an executable rule that performs a specific type of processing on a message. For example, the Message Size filter rejects messages that are greater or less than a specified size. There are many categories of message filters available with the API Gateway, including authentication, authorization, content filtering, signing, and conversion. In the Policy Studio, a filter is displayed as a block of business logic that forms part of an execution flow known as a policy. The next section shows some example filters.
A policy is a network of message filters in which each filter is a modular unit that processes a message. A message can traverse different paths through the policy, depending on which filters succeed or fail. For example, this enables you to configure policies that route messages that pass a Schema Validation filter to a back-end system, and route messages that pass a different Schema Validation filter to a different system. A policy can also contain other policies, which enables you to build modular reusable policies.
In the Policy Studio, the policy is displayed as a path through a set of filters. Each filter can have only one Success Path and one Failure Path. You can use these success and failure paths to create sophisticated rules. For example, if the incoming data matches schema A, scan for attachments and route to service A, otherwise route to service B. You can configure the colors used to display success paths and failure paths in the Policy Studio Preferences menu. You can also specify to Show Link Labels (S or F).
The following screen shot shows an example policy:
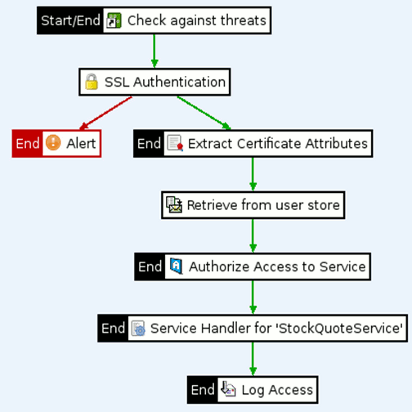 |
A policy must have a Start filter (in this example, Check against threats). Filters labeled End stop the execution of the policy (for example, the filter execution fails). A filter labeled Start/End indicates that the policy execution starts there, and that the policy stops executing if this filter fails. A policy with a single filter labeled Start/End is also valid.
Each filter requires input data and produces output data. This data is stored in message attributes,
and you can access their values in API Gateway configuration using a selector syntax (for example,
${attribute.name}). You can also use specific filters to create your own message attributes,
and to set their values. The full list of message attributes flowing through a policy is displayed when
you right-click the Policy Studio canvas, and select Show All Attributes. You can also hover
your mouse over a filter to see its inputs and outputs. The Trace filter enables you to
trace message attribute values at execution time.
The following example screen shot shows the attributes displayed when hovering over an HTTP Basic authentication filter:
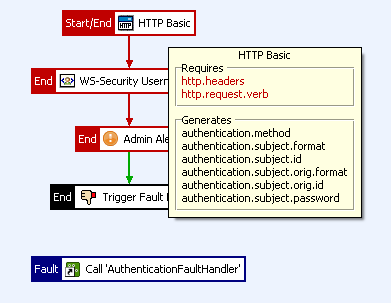 |
If a filter requires an attribute as input that has not been generated in the previous execution steps, the filter is displayed in a different color in the Policy Studio (default is red). You can configure the color used to display missing attributes in the Policy Studio Preferences menu. Alternatively, you can also view all required attributes by right-clicking the canvas, and selecting Show All Attributes.
A missing attribute may indicate a problem that you need to investigate (for example, in the chaining of filters or policies, or that the policy can not run on its own). This is often the case for reusable filters, such as those displayed in the previous example.
At the policy level, you also can click the horizontal bar at the top of the Policy Studio canvas to show the list of all attributes required as input to the entire policy. If any attributes are generated by the policy, you can click a corresponding bar at the bottom to see a list of generated attributes. The following example screen shot shows the attributes required by an Authenticate policy:
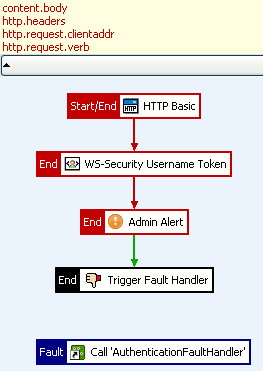 |
A selector is a special syntax that enables API Gateway configuration settings to be evaluated and expanded at runtime based on metadata (for example, in message attributes, a Key Property Store (KPS), or environment variables). For example, the following selector returns the value of a message attribute:
${http.request.clientaddr}
Selectors are powerful a feature for System Integrators (SIs) and Independent Software Vendors (ISVs) when extending the API Gateway to integrate with other systems. For more details on selectors, see Selecting Configuration Values at Runtime.
When a SOAP transaction fails, you can use a SOAP fault to return error information to the SOAP client. By default, the API Gateway returns a basic SOAP fault to the client when a message filter fails. You can add a SOAP Fault filter to a policy to return more detailed error information to the client. For example, the previous example screen shot shows an AuthenticationFaultHandler, which is a policy shortcut to the following fault handler policy:
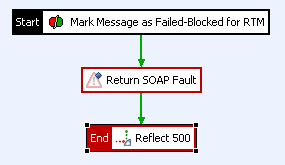 |
A policy shortcut enables you to create a link from one policy to another policy. For example, you could create a policy that inserts security tokens into a message, and another that adds HTTP headers. You can then create a third policy that calls the other two policies using Policy Shortcut filters.
A policy shortcut chain enables you to run a series of policies in sequence without needing to create a policy containing policy shortcuts. In this way, you can create modular policies to perform certain specific tasks, such as authentication, content filtering, returning faults, or logging, and then link these policies together in a sequence using a policy shortcut chain. You can also use API Service Manager to automate the creation of a policy shortcut chain simply by dragging and dropping existing policies into a composite policy.
The API Gateway can send alert messages for specified events to various alerting destinations. System alerts are usually sent when a filter fails, but they can also be used for notification purposes. For example, the API Gateway can send system alerts to the following destinations:
-
Email Recipient
-
Check Point Firewall-1 (OPSEC)
-
Local Sylsog
-
Remote Sylsog
-
SNMP Network Management System
-
Twitter
-
Windows Event Log
You can configure alert destinations, and then add an Alert filter to a policy, specifying the appropriate alert destination.
A policy container is used to group similar policies together (for example, all authentication or logging policies), or policies that relate to a particular service. A number of useful policies are provided in the Policy Library container (for example, policies that return faults, and policies that block threatening content). You can add your own policies to this container, and add your own policy containers to suit your requirements.
Policies can execute in a specified context. For example, you can set a context by associating a relative execution path or listener with a policy. When a policy is called from another policy, the context is set to the calling policy name (for example, Authenticate). In the Policy Studio, you can select a context from the Context drop-down list at the bottom of the policy canvas. The Policy Studio then displays whether the attributes required for execution are available in that context. The Context list includes all connected relative paths, listeners, Web Services, SMTP services, and policy shortcuts that use the selected policy. Click the View navigator node button to display the selected context.
API Gateway Instance
An API Gateway instance is an API Gateway capable of running on a host. You can use Policy Studio to configure and deploy API Gateway instances. You can configure various features at the instance level (for example, HTTP(S) interfaces, file transfer services, JMS services, and Remote Hosts).
You can define different types of listeners and associate them with specific policies. For example, listeners include the following types:
-
HTTP/HTTPS
-
Directory Scanner
-
POP mail server connection
-
JMS connection
-
TIBCO RV/EMS connection
The API Gateway can be used to provide protocol mediation (for example, receiving a SOAP request over JMS, and transforming it into a SOAP/HTTP request to a back-end service). For HTTP/HTTPS listeners, policies are linked to a relative path. Otherwise, policies are linked to the listener itself. You can associate a single policy with multiple listeners.
You can define a remote host when you need more control of the connection settings to a particular server. The available connection settings include the following:
-
HTTP version
-
IP addresses
-
Timeouts
-
Buffers
-
Caches
For example, by default, the API Gateway uses HTTP 1.1. You can force it to use HTTP 1.0 using Remote Host settings. You must also define a Remote Host if you want to track real-time metrics for a particular host.
The API Gateway provides a Web server and servlet application server that can be used to host static content (for example, documentation for your project), or servlets providing internal services. Static content or servlets can be accessed from a policy using the Call Internal Service filter. This feature is not meant to replace an enterprise J2EE server, but rather to enable you to write functionality using technology such as servlets.
When you register an API service or Web Service, and deploy it to the API Gateway, the API Gateway virtualizes the service. Instead of connecting to the service directly, clients connect through the API Gateway. The API Gateway can then apply policies to messages sent to the destination service (for example, to enable security, monitoring, and acceleration).