The software described in this documentation is either in Extended Support or Sustaining Support. See https://www.oracle.com/us/support/library/enterprise-linux-support-policies-069172.pdf for more information.
Oracle recommends that you upgrade the software described by this documentation as soon as possible.
Authentication is the verification of the identity of an entity, such as a user, to a system. A user logs in by providing a user name and a password, and the operating system authenticates the user's identity by comparing this information to data stored on the system. If the login credentials match and the user account is active, the user is authenticated and can successfully access the system.
The information that verifies a user's identity can either be
located on the local system in the /etc/passwd
and /etc/shadow files, or on remote systems
using Identity Policy Audit (IPA), the Lightweight Directory
Access Protocol (LDAP), the Network Information Service (NIS), or
Winbind. In addition, IPSv2, LDAP, and NIS data files can use the
Kerberos authentication protocol, which allows nodes communicating
over a non-secure network to prove their identity to one another
in a secure manner.
You can use the Authentication Configuration GUI
(system-config-authentication) to select the
authentication mechanism and to configure any associated
authentication options. Alternatively, you can use the
authconfig command. Both the Authentication
Configuration GUI and authconfig adjust
settings in the PAM configuration files that are located in the
/etc/pam.d directory.
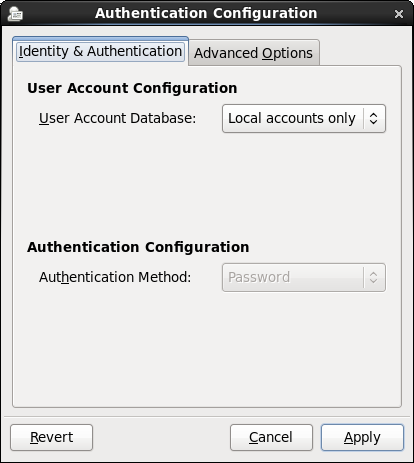
Figure 23.1 shows the Authentication Configuration GUI with Local accounts only selected.