The software described in this documentation is either in Extended Support or Sustaining Support. See https://www.oracle.com/us/support/library/enterprise-linux-support-policies-069172.pdf for more information.
Oracle recommends that you upgrade the software described by this documentation as soon as possible.
To be able to use Kerberos authentication with an LDAP or NIS
client, use yum to install the
krb5-libs and
krb5-workstation packages.
If you use the Authentication Configuration GUI (system-config-authentication) and select LDAP or NIS as the user account database, select Kerberos password as the authentication method and enter values for:
- Realm
The name of the Kerberos realm.
- KDCs
A comma-separated list of Key Distribution Center (KDC) servers that can issue Kerberos ticket granting tickets and service tickets.
- Admin Servers
A comma-separated list of Kerberos administration servers.
Alternatively, you can use DNS to configure these settings:
Select the Use DNS to resolve hosts to realms check box to look up the name of the realm defined as a
TXTrecord in DNS, for example:_kerberos.mydom.com IN TXT "MYDOM.COM"
Select the Use DNS to locate KDCs for realms check box to look up the KDCs and administration servers defined as
SVRrecords in DNS, for example:_kerberos._tcp.mydom.com IN SVR 1 0 88 krbsvr.mydom.com _kerberos._udp.mydom.com IN SVR 1 0 88 krbsvr.mydom.com _kpasswd._udp.mydom.com IN SVR 1 0 464 krbsvr.mydom.com _kerberos-adm._tcp.mydom.com IN SVR 1 0 749 krbsvr.mydom.com
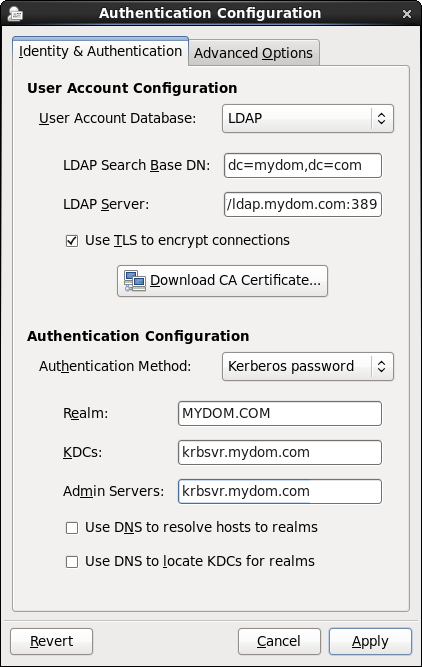
Figure 23.6 shows the Authentication Configuration GUI with LDAP selected as the user account database and Kerberos selected for authentication.
Alternatively, you can use the authconfig command to configure Kerberos authentication with LDAP, for example:
#authconfig --enableldap\--ldapbasedn="dc=mydom,dc=com" --ldapserver=ldap://ldap.mydom.com:389\ [--enableldaptls --ldaploadcacert=https://ca-server.mydom.com/CAcert.pem] \--enablekrb5\--krb5realm=MYDOM.COM|--enablekrb5realmdns\--krb5kdc=krbsvr.mydom.com --krb5adminserver=krbsvr.mydom.com|--enablekrb5kdcdns\--update
or with NIS:
#authconfig --enablenis\--enablekrb5\--krb5realm=MYDOM.COM|--enablekrb5realmdns\--krb5kdc=krbsvr.mydom.com --krb5adminserver=krbsvr.mydom.com|--enablekrb5kdcdns\--update
The --enablekrb5 option enables Kerberos
authentication by modifying the PAM configuration files in
/etc/pam.d to use the
pam_krb5.so module. The
--enableldap and
--enablenis options configure
/etc/nsswitch.conf to enable the system to
use LDAP or NIS for information services.
For more information, see the authconfig(8),
nsswitch.conf(5), and
pam_krb5(5) manual pages.