The software described in this documentation is either in Extended Support or Sustaining Support. See https://www.oracle.com/us/support/library/enterprise-linux-support-policies-069172.pdf for more information.
Oracle recommends that you upgrade the software described by this documentation as soon as possible.
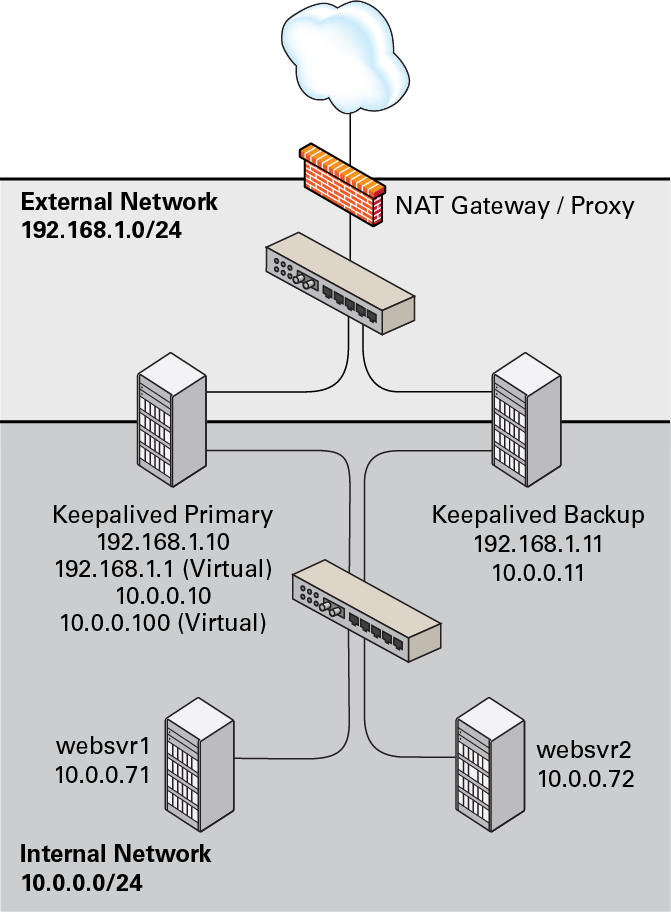
The following example uses Keepalived in NAT mode to implement a
simple failover and load balancing configuration on two servers.
One server acts as the primary, the other acts as a backup, and
the primary server has a higher priority than the backup server.
Each of the servers has two network interfaces, where one
interface is connected to the side facing an external network
(192.168.1.0/24) and the other interface is
connected to an internal network (10.0.0.0/24)
on which two web servers are accessible.
Figure 17.3
shows that the Keepalived primary server has network addresses
192.168.1.10, 192.168.1.1
(virtual), and 10.0.0.10, and
10.0.0.100 (virtual). The Keepalived backup
server has network addresses 192.168.1.11 and
10.0.0.11. The web servers
websvr1 and websvr2 have
network addresses 10.0.0.71 and
10.0.0.72 respectively.
You might the following
/etc/keepalived/keepalived.conf configuration
on the primary server:
global_defs {
notification_email {
root@mydomain.com
}
notification_email_from svr1@mydomain.com
smtp_server localhost
smtp_connect_timeout 30
}
vrrp_sync_group VRRP1 {
# Group the external and internal VRRP instances so they fail over together
group {
external
internal
}
}
vrrp_instance external {
state MASTER
interface eth0
virtual_router_id 91
priority 200
advert_int 1
authentication {
auth_type PASS
auth_pass 1215
}
# Define the virtual IP address for the external network interface
virtual_ipaddress {
192.168.1.1/24
}
}
vrrp_instance internal {
state MASTER
interface eth1
virtual_router_id 92
priority 200
advert_int 1
authentication {
auth_type PASS
auth_pass 1215
}
# Define the virtual IP address for the internal network interface
virtual_ipaddress {
10.0.0.100/24
}
}
# Define a virtual HTTP server on the virtual IP address 192.168.1.1
virtual_server 192.168.1.1 80 {
delay_loop 10
protocol TCP
# Use round-robin scheduling in this example
lb_algo rr
# Use NAT to hide the back-end servers
lb_kind NAT
# Persistence of client sessions times out after 2 hours
persistence_timeout 7200
real_server 10.0.0.71 80 {
weight 1
TCP_CHECK {
connect_timeout 5
connect_port 80
}
}
real_server 10.0.0.72 80 {
weight 1
TCP_CHECK {
connect_timeout 5
connect_port 80
}
}
}
This configuration is similar to that given in
Section 17.6, “Configuring Simple Virtual IP Address Failover Using Keepalived” with the additional
definition of a vrrp_sync_group section so that
the network interfaces are assigned together on failover, and a
virtual_server section to define the real
back-end servers that Keepalived uses for load balancing. The
value of lb_kind is set to
NAT (Network Address Translation), which means
that the Keepalived server handles both inbound and outbound
network traffic from and to the client on behalf of the back-end
servers.
The configuration of the backup server is the same except for the
values of notification_email_from,
state, priority, and
possibly interface if the system hardware
configuration is different:
global_defs {
notification_email {
root@mydomain.com
}
notification_email_from svr2@mydomain.com
smtp_server localhost
smtp_connect_timeout 30
}
vrrp_sync_group VRRP1 {
# Group the external and internal VRRP instances so they fail over together
group {
external
internal
}
}
vrrp_instance external {
state BACKUP
interface eth0
virtual_router_id 91
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass 1215
}
# Define the virtual IP address for the external network interface
virtual_ipaddress {
192.168.1.1/24
}
}
vrrp_instance internal {
state BACKUP
interface eth1
virtual_router_id 92
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass 1215
}
# Define the virtual IP address for the internal network interface
virtual_ipaddress {
10.0.0.100/24
}
}
# Define a virtual HTTP server on the virtual IP address 192.168.1.1
virtual_server 192.168.1.1 80 {
delay_loop 10
protocol TCP
# Use round-robin scheduling in this example
lb_algo rr
# Use NAT to hide the back-end servers
lb_kind NAT
# Persistence of client sessions times out after 2 hours
persistence_timeout 7200
real_server 10.0.0.71 80 {
weight 1
TCP_CHECK {
connect_timeout 5
connect_port 80
}
}
real_server 10.0.0.72 80 {
weight 1
TCP_CHECK {
connect_timeout 5
connect_port 80
}
}
}Two further configuration changes are required:
Configure firewall rules on each Keepalived server (primary and backup) that you configure as a load balancer as described in Section 17.7.1, “Configuring Firewall Rules for Keepalived NAT-Mode Load Balancing”.
Configure a default route for the virtual IP address of the load balancer's internal network interface on each back-end server that you intend to use with the Keepalived load balancer as described in Section 17.7.2, “Configuring Back-End Server Routing for Keepalived NAT-Mode Load Balancing”.
See Section 17.5, “Installing and Configuring Keepalived” for details of how to install and configure Keepalived.