The software described in this documentation is either in Extended Support or Sustaining Support. See https://www.oracle.com/us/support/library/enterprise-linux-support-policies-069172.pdf for more information.
Oracle recommends that you upgrade the software described by this documentation as soon as possible.
The iptables and
system-config-firewall packages provide the
components of the packet-filtering firewall and the accompanying
utilities.
A packet filtering firewall filters incoming and outgoing network packets based on the packet header information. You can create packet filter rules that determine whether packets are accepted or rejected. For example, if you create a rule to block a port, any request is made to that port that is blocked by the firewall, and the request is ignored. Any service that is listening on a blocked port is effectively disabled.
The Oracle Linux kernel uses the Netfilter feature to provide packet filtering functionality for IPv4 and IPv6 packets respectively.
Netfilter consists of two components:
A
netfilterkernel component consisting of a set of tables in memory for the rules that the kernel uses to control network packet filtering.The iptables and ip6tables utilities to create, maintain, and display the rules that
netfilterstores.
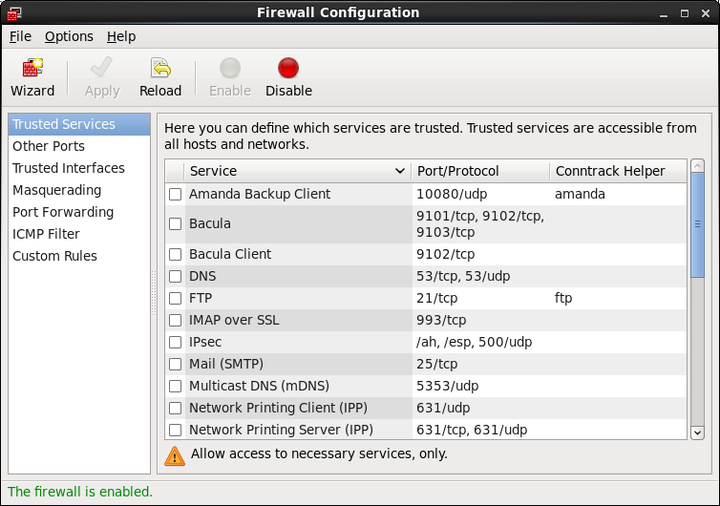
To implement a simple, general-purpose firewall, you can use the Firewall Configuration GUI (system-config-firewall) to create basic Netfilter rules.
Figure 25.1 shows the Firewall Configuration GUI.
To create a more complex firewall configuration, use the iptables and ip6tables utilities to configure the packet filtering rules.
Netfilter records the packet filtering rules in the
/etc/sysconfig/iptables and
/etc/sysconfig/ip6tables files, which
netfilter reads when it is initialized.
The netfilter tables include:
-
Filter The default table, which is mainly used to drop or accept packets based on their content.
-
Mangle This table is used to alter certain fields in a packet.
-
NAT The Network Address Translation table is used to route packets that create new connections.
The kernel uses the rules stored in these tables to make decisions about network packet filtering. Each rule consists of one or more criteria and a single action. If a criterion in a rule matches the information in a network packet header, the kernel applies the action to the packet. Examples of actions include:
-
ACCEPT Continue processing the packet.
-
DROP End the packet’s life without notice.
-
REJECT As
DROP, and additionally notify the sending system that the packet was blocked.
Rules are stored in chains, where each chain is composed of a default policy plus zero or more rules. The kernel applies each rule in a chain to a packet until a match is found. If there is no matching rule, the kernel applies the chain’s default action (policy) to the packet.
Each netfilter table has several predefined
chains. The filter table contains the following
chains:
-
FORWARD Packets that are not addressed to the local system pass through this chain.
-
INPUT Inbound packets to the local system pass through this chain.
-
OUTPUT Locally created packets pass through this chain.
The chains are permanent and you cannot delete them. However, you can create additional chains in the filter table.
For more information, see the iptables(8) and
ip6tables(8) manual pages.