You can manage both constraints and extensions policy rules in two ways:
The recommended method is to use the CMS window.
Policy Management From the CMS Window
The CMS window (as shown in Figure 19.1) provides the appropriate user interface to support policy management for each subsystem, the Certificate Manager, Registration Manager, and Data Recovery Manager.
Figure 19.1 Policy information in the CMS window
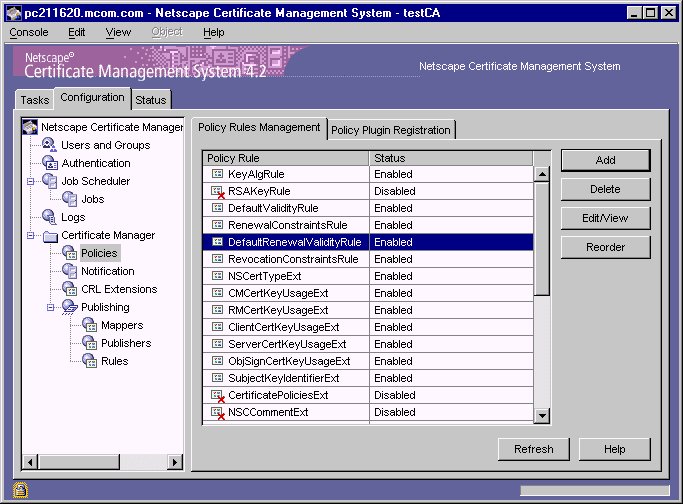
Under each subsystem tree node in the CMS window, you will find a Policies object. This object represents the policy configuration of that subsystem, enabling you to accomplish the following operations:
The sections that follow describe the parts of the window from which you carry out these operations.
Policy Rules Management Tab
The Policy Rules Management tab displays the current policy configuration for the selected subsystem. The tab lists the currently configured policy instances (or rules) for a subsystem, enabling you to manage them at a single place. From this tab you can add, modify, or delete rules, enable or disable individual rules, and change the order in which the rules get applied to an end-entity request.
Add.
The add operation shows a list of registered policy modules from which you can select the one you want to configure. When you save the changes, the subsystem creates the rule and displays it in the list of policy rules. For instructions, see "Step 4. Add New Policy Rules".
Delete.
The delete operation allows you to remove unwanted policy rules from the CMS configuration. For instructions, see "Step 3. Delete Unwanted Policy Rules".
Edit/View.
The edit operation allows you to view and modify configuration parameter values associated with the currently configured policy rules. For instructions, see "Step 2. Modify Existing Policy Rules".
Reorder.
The reorder operation allows you to change the order of the policy rules a subsystem applies to an end-entity request. Enabled rules are applied in the order in which they appear; disabled rules are ignored. For instructions, see "Step 5. Reorder Policy Rules".
Policy Plugin Registration Tab
The Policy Plugin Registration tab lists the currently registered policy plug-in modules for the selected subsystem and gives you access to the window from which you can register new modules. On this tab you will find the names of registered modules listed on the left and the path to the Java class that implements the module listed on the right.
You can perform the following operations from this tab:
Register.
This operation allows you to register a new policy module. For instructions, see "Registering a Policy Module".
Delete.
This operation allows you to remove unwanted policy modules from the CMS framework. For instructions, see "Deleting a Policy Module".
Policy Parameters in the Configuration File
The sample configuration file shown on page 89 illustrates how policy-specific information appears in the configuration file. Keep the following points in mind:
To change the configuration by editing the configuration file, follow the instructions in "Changing the Configuration by Editing the Configuration File".