The Certificate Manager can publish certificates (ones that it issues) to an LDAP-compliant directory and a flat file. Sections that follow explain each of these in detail.
Publishing of Certificates to a Directory
Large corporations typically use Lightweight Directory Access Protocol (LDAP) directories, such as Netscape Directory Server, to store and manage corporatewide data, including user and group information and network resource data. If you have deployed an LDAP-compliant directory, you can configure the Certificate Manager to automatically publish your CA and end-entity certificate-related information to that directory. For example, if you have configured the Certificate Management System to employ directory-based authentication, you should consider publishing the CA and end-entity certificates to the same directory. This way, you can keep your users' security credentials with the rest of the user information (see Figure 20.1).
Figure 20.1 Publishing certificates to a directory for distribution
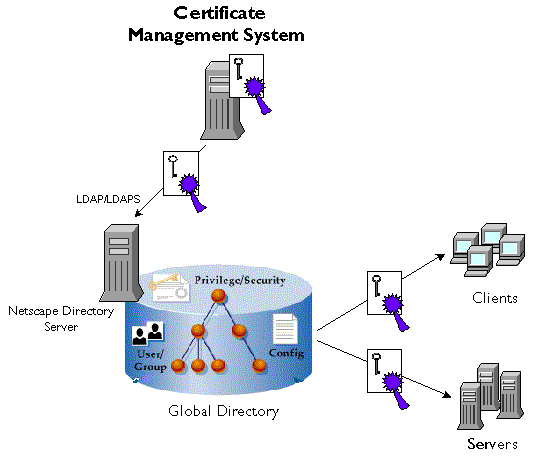
The ability of a Certificate Manager to publish certificates, CRLs, and other certificate-related objects to a directory using the LDAP or LDAPS protocol is called LDAP publishing and the directory to which it publishes is called the publishing directory. Note that configuring the Certificate Manager for LDAP publishing is optional--you can turn this feature off without affecting any of the certificate issuance, renewal, and revocation operations handled by the server.
You can configure the Certificate Manager to automatically publish certificates to the directory every time a certificate is issued and at a predetermined interval--for example, every day or once every week. Privileged users (administrators and agents) can also manually initiate the LDAP publishing process.
Figure 20.2 illustrates LDAP publishing by the Certificate Manager when a certificate requested via the manual-enrollment process is issued.
Figure 20.2 Publishing by a Certificate Manager
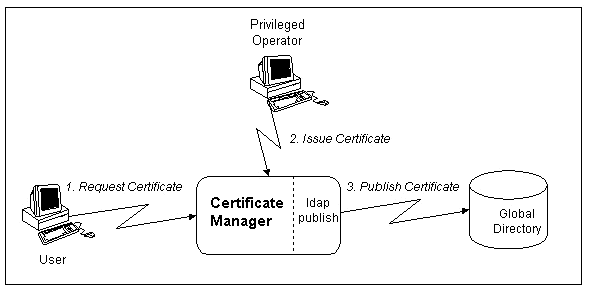
Figure 20.3 illustrates how certificates requested via a Registration Manager get published to the directory.
Figure 20.3 Publishing of certificates requested via a Registration Manager

Timing of Directory Updates
If the LDAP directory is properly configured to work with the Certificate Manager (and vice versa), any changes to the certificate information in the Certificate Manager are automatically made also in the publishing directory.
The publishing directory is updated at these times:
Table 20.1 summarizes the above-listed actions of the Certificate Manager. The table also indicates how the Certificate Manager populates an LDAP directory, if configured for publishing. Note that certificates (and CRLs) are published as DER-encoded binary blobs.
The Certificate Manager cannot update the directory in the following cases:
Note that the Certificate Manager's LDAP publishing action happens as a separate transaction from any certificate operation (such as issuance); the operation of a certificate is not affected by whether it was successfully published or not.
Directory Update Process
As indicated in Table 20.1, when a Certificate Manager is requested to issue a certificate, update certificate information, or publish a CRL, it automatically updates the corresponding entry in the configured directory with relevant information. To locate the correct directory entry, the Certificate Manager relies on object-mapping rules, which can be defined using the mapper modules; for details, see "Mapper Modules". Once an entry is located, to publish the object to the correct attribute, the server relies on object-publishing rules, which can be defined with the help of publisher modules; for details, "Publisher Modules".
Similarly, when you revoke a certificate, the Certificate Manager uses the object mapping and publishing rule to locate and delete the corresponding certificate from the directory.
For instruction on how to configure the Certificate Manager to publish to a directory, see "Publishing Certificates and CRLs to a Directory".
Directory Synchronization
The Certificate Manager and the publishing directory can become out of sync if certificates are issued or revoked while Directory Server is down. Certificates that were issued or revoked need to be published or unpublished manually when Directory Server comes back up.
To help find certificates that are out of sync with the directory--that is, valid certificates that are not in the directory and revoked or expired certificates that are still in the directory--the Certificate Manager keeps a record of whether a certificate in its internal database has been published to the directory. If the Certificate Manager and the publishing directory become out of sync, you can use the Update Directory option in the Certificate Manager Agent Services interface to synchronize the publishing directory with the internal database.
The following choices are available for synchronizing the directory with the internal database:
For instructions, see "Manually Updating Certificates in the Directory".
Publishing of Certificates to a Flat File
In addition to publishing to a directory, the Certificate Manager can publish the certificate to a file. The certificate is published as a DER-encoded binary blob and applications that are capable of reading such data may read the file for certificate information. For example, you can customize the sample code for Flat File CRL and certificate publisher can be customized to store certificates and CRLs in a relational database management system.
For instructions on how to configure a Certificate Manager to publish certificates to a flat file, see "Publishing Certificates and CRLs to Flat Files".