|
You can configure a Certificate Manager to publish certificates to a directory or flat file, and to publish CRLs to a directory, online validation authority, or flat file. If you configure the Certificate Manager to publish to a directory, whenever the server issues a certificate or updates a certificate or CRL, it needs to locate the entry in the directory in order to update it. For example, to find the correct directory entry to update, the Certificate Manager needs to present Directory Server with search criteria (so that it can initiate an LDAP search operation); the Certificate Manager considers the search successful only if Directory Server returns a single LDAP entry that exactly matches the search criteria.
The Certificate Manager uses object-mapping rules to find the directory entry that needs to be updated. When configuring a Certificate Manager for publishing certificates and CRLs, you define mapping rules that help the server to construct appropriate search criteria that find the entry that needs to be updated.
Mapper modules help you configure the Certificate Manager to use specific rules to map or locate a specific entry, such as a CA's entry or an end-entity's entry, in a specified directory; once the correct entry is located, the server publishes the certificate or CRL to the correct attribute in the entry using a publisher rule, as explained in "Publisher Modules".
Overview of Mapper Modules
By default, the Certificate Manager provides a set of mapper plug-in modules for mapping the CA certificate, end-entity certificates, and CRLs to appropriate entries in an LDAP directory; because it's not required to map entries in a flat file and online validation authority, no mapper modules are provided for mapping objects in a flat file or an online validation authority. Plug-in modules are implemented as Java classes and are registered in the CMS publishing framework. The Mapper Plugin Registration tab of the CMS window (Figure 21.1) lists all the modules and the corresponding classes that are registered by default with a Certificate Manager.
Figure 21.1 Default mapper modules registered with a Certificate Manager 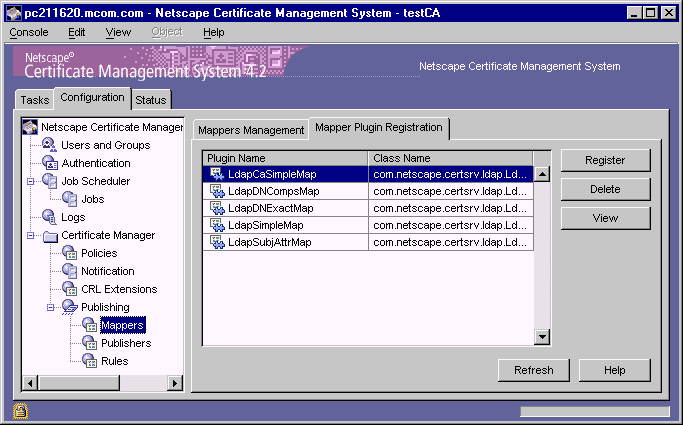
Table 21.1 lists the mapper modules provided for the Certificate Manager.
After you take a look at the default mapper modules, if you determine that they do not meet your requirements entirely, you can develop a custom mapper module by implementing the following Java interface:
com.netscape.certsrv.ldappublish.ILdapMapper
For more information on this interface, check the CMS software development kit (SDK) installed at this location: <server_root>/cms_sdk/sdkdocs
Be sure to take a look at the samples available at this location: <server_root>/cms_sdk/samples/publishing/mappers
When developing a custom mapper module, you may want to intercept LDAP error 52 and reword it so that the correct error message gets logged. To give you an example, if the publishing directory has been stopped, the server logs the following message in its error and system logs:
Error publishing CRL MasterCRL: Cannot find a match in the LDAP server for certificate. netscape.ldap.LDAPException: unable to establish connection (52); DSA is unavailable.
Notice that the error message incorrectly says DSA is unavailable instead of Directory Server is unavailable.
For instructions on how to configure a Certificate Manager to use a mapper module, see "Step 3. Configure the Certificate Manager to Publish Certificates".
CA Certificate Mapper
The LdapCaSimpleMap plug-in module implements the CA certificate mapper.
This mapper enables you to configure a Certificate Manager to automatically
create an entry for the CA in an LDAP directory and then map the CA's
certificate to the directory entry by formulating the entry's DN from
components specified in the certificate's subject name and attribute variable
assertion (AVA) constants. For more information on AVAs, check the directory
documentation.
The CA certificate mapper allows you to specify whether to create an entry for
the CA or to just map the certificate to an existing entry, or to do both; for
example, you can choose to manually create an entry for the CA in the
directory and then configure the CA certificate mapper to just locate the entry
by using attributes from the issuer name in the CA's signing certificate and AVA
constants.
During installation, the Certificate Manager automatically creates two instances (called mappers) of the CA certificate mapper module (see Figure 21.2). The mappers are named as follows:
It is important that you review and customize these mappers. For instructions on modifying mappers or creating new mappers, see "Step 3. Configure the Certificate Manager to Publish Certificates".
LdapCaSimpleMap Module
The Java class that implements the CA certificate mapper is as follows:
com.netscape.certsrv.ldap.LdapCaSimpleMap
Figure 21.3 shows how the configurable parameters for the LdapCaSimpleMap module are displayed in the CMS window.
Figure 21.3 Parameters defined in the LdapCaSimpleMap module 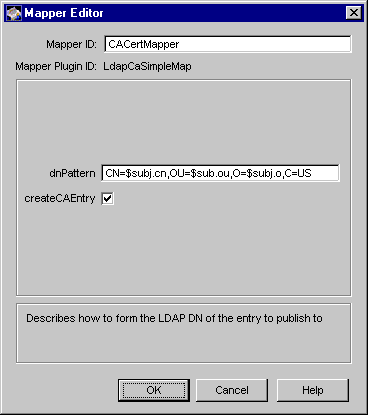
Table 21.2 describes these parameters.
Table 21.2 Description of parameters defined in the LdapCaSimpleMap module
Parameter
| Description
|
|---|
dnPattern
| Specifies the DN pattern the Certificate Manager should use to construct the DN in order to search for the CA's entry in the publishing directory. The value of dnPattern can be a list of AVA s separated by commas. An AVA can be a variable, such as CN=$subj.cn, that the Certificate Manager can derive from the certificate subject name, or a constant, such as O=Siroe Corporation.
Permissible values: A valid pattern that will enable the Certificate Manager to construct the DN for the CA's entry.
Example: CN=$subj.cn,OU=$subj.ou,O=$subj.o,C=US
|
createCAEntry
| Specifies whether the Certificate Manager should create an entry for the CA in the publishing directory. Check the box if you want the server to create a CA's entry (default). Uncheck the box if you don't want the server to create an entry.
If you check the box, the Certificate Manager first attempts to create an entry for the CA in the directory. If the Certificate Manager succeeds in creating the entry, it then attempts to publish the CA's certificate to the entry. Note that the CA's entry DN in the directory will match the pattern you specify in the dnPattern field. For example, if the issuer DN (specified in the CA's signing certificate) is CN=testCA, OU=Research Dept, O=Siroe Corporation, C=US, and the dnPattern is set to CN=$subj.cn,OU=$subj.ou,O=$subj.o,C=US, the Certificate Manager creates an entry with CN=testCA, OU=Research Dept, O=Siroe Corporation, C=US as its DN.
|
LdapCaCertMap Mapper
The mapper named LdapCaCertMap is an instance of the LdapCaSimpleMap module. The Certificate Manager automatically creates this mapper during installation.
You can use this mapper for creating an entry for the CA in the directory and for mapping the CA certificate to the CA's entry in the directory.
By default, the mapper is configured to create an entry for the CA in the directory and the default DN pattern for locating the CA's entry is as follows:
UID=$subj.cn,OU=people,O=$subj.o
LdapCrlMap Mapper
The mapper named LdapCrlMap is an instance of the LdapSimpleMap module. The Certificate Manager automatically creates this mapper during installation.
You can use this mapper for creating an entry for the CA in the directory and for mapping the CRL to the CA's entry in the directory.
By default, the mapper is configured to create an entry for the CA in the directory and the default DN pattern for locating the CA's entry is as follows:
UID=$subj.cn,OU=people,O=$subj.o
DN Components Mapper
The LdapDNCompsMap plug-in module implements the DN components mapper. This mapper enables you to configure a Certificate Manager to map a certificate to an LDAP directory entry by constructing the entry's distinguished name from components (such as CN, OU, O, and C) specified in the certificate subject name, and then using it as the search DN to locate the entry in the directory. You can use this mapper to locate the following:
The mapper requires you to specify values for three parameters, filterComps, dnComps, and baseDN, which are explained in Table 21.3. In general, the mapper takes DN components to build the search DN. The mapper also takes an optional root search DN. The server uses the DN components to form an LDAP entry to begin a subtree search and the filter components to form a search filter for the subtree. If none of the DN components are configured, the server uses the base DN for the subtree. If the base DN is null and none of the DN components match, an error is returned. If none of the DN components and filter components match, an error is returned. If the filter components are null, a base search is performed.
Note that both DNComps and filterComps parameters accept valid DN components or attributes separated by commas. The parameters don't accept multiple entries of an attribute; for example, you can set filterComps to CN,OU, but not to CN,OU2,OU1. If there's a need for you to support such a filter, for example, if your directory entries contain multiple OUs and you want to use multiple OUs in your filterComps for filtering entries, you can modify the source code for the LdapDNCompsMap module. The java class for the module is in this directory:
<server_root>/cms_sdk/samples/publishing/mappers
The discussion below explains how mapping by DN components works. It is recommended that you read this before configuring a Certificate Manager to use this mapper.
Subject names in certificates are in distinguished-name format. A distinguished name (DN) uniquely identifies an entry in an LDAP directory. The DN consists of components that help identify the entry; for details, see Appendix A, "Distinguished Names."
The following components are commonly used in DNs:
For example, the following DN represents the user named Jane Doe who works for the Sales department at Siroe Corporation, which is located in Mountain View in the state of California, United States:
CN=Jane Doe, E=jdoe@siroe.com, OU=Sales, O=Siroe Corporation, L=Mountain View, ST=California, C=US
The Certificate Manager uses the components in subject names to construct a DN that it can use as the base for searching specific directory entries in order to publish the corresponding certificate information.
For example, suppose the subject name in the certificate is in this form:
CN=Jane Doe, OU=Sales, O=Siroe Corporation, L=Mountain View, ST=California, C=US
The Certificate Manager can use some or all of these components (CN, OU, O, L, ST, and C) to build a DN for searching the directory. When creating a mapper rule, you can specify the components the server should use to build a DN (that is, components to match attributes in the directory). You do this by configuring the dnComps parameter; for details, see Table 21.3.
For example, assume you entered components CN, E, OU, O, and C as values for the dnComps parameter. For locating Jane Doe's entry in the directory, the Certificate Manager constructs the following DN by reading the DN attribute values from the certificate, and uses the DN as the base for searching the directory:
CN=Jane Doe, OU=Sales, O=Siroe Corporation, C=US
Note the following:
In general, for the dnComps parameter, you should enter those DN components that the Certificate Manager can use to form the LDAP DN exactly. In certain situations, however, the subject name in a certificate may match more than one entry in the directory. Then, the Certificate Manager might not get a single, distinct matching entry from the DN. For example, the subject name
CN=Jane Doe, OU=Sales, O=Siroe Corporation, C=US
might match two users with the name Jane Doe in the directory. If that occurred, the Certificate Manager would need additional criteria to determine which entry corresponds to the subject of the certificate.
To specify the components the Certificate Manager must use to distinguish between different entries in the directory, use the filterComps parameter; for details, see Table 21.3.
For example, if you entered CN, OU, O, and C as values for the dnComps parameter, enter L for the filterComps parameter only if the L attribute can be used to distinguish between entries with identical CN, OU, O, and C values.
Consider another example that shows how two directory entries with similar DNs can be differentiated by the value of the UID attribute: Assume that the two Jane Doe entries are distinguished by the value of the UID attribute. One entry's UID value is janedoe1 and the other entry's UID value is janedoe2. Because the UID attribute corresponds to the UID component in a DN, you can set up the subject names of certificates to include the UID component.
Generally, the E, L, and ST components are not included in the standard set of
certificate request forms provided for end entities. You can add these
components to the forms, or you can have the issuing agents insert these
components when editing the subject name in the certificate issuance forms.
LdapDNCompsMap Module
The Java class that implements the DN components mapper is identified as follows:
com.netscape.certsrv.ldap.LdapCertCompsMap
Figure 21.4 shows how the configurable parameters for the LdapDNCompsMap module are displayed in the CMS window.
Figure 21.4 Parameters defined in the LdapDNCompsMap module 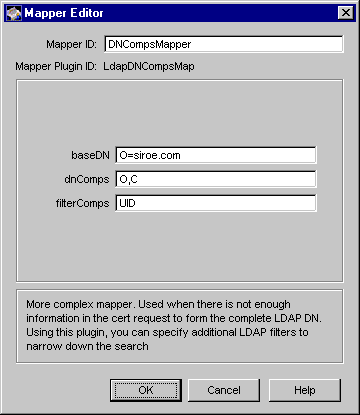
With this configuration, a Certificate Manager maps its certificates with the ones in the LDAP directory by using the dnComps values to form a DN and the filterComps values to form a search filter for the subtree.
Table 21.3 describes these parameters.
Subject Name Mapper
The LdapDNExactMap plug-in module implements the subject name mapper. This mapper enables you to configure a Certificate Manager to map a certificate to an LDAP directory entry by searching for the LDAP entry DN that matches the certificate subject name. Note that to be able to use this mapper, each certificate subject name must exactly match a DN in a directory entry. For example, assume the certificate subject name is this:
UID=jdoe, O=Siroe Corporation, C=US
When searching the directory for the entry, the Certificate Manager only searches for an entry whose DN is this:
UID=jdoe, O=Siroe Corporation, C=US
If no matching entries are found, the server returns an error and does not publish the certificate.
This mapper does not require you to specify any values for any parameters because it obtains all values from the certificate (see Figure 21.5).
LdapDNExactMap Module
The Java class that implements the subject name mapper is identified as follows:
com.netscape.certsrv.ldap.LdapCertExactMap
Figure 21.5 shows how the LdapDNExactMap module looks when viewed in the CMS window.
Figure 21.5 The LdapDNExactMap module 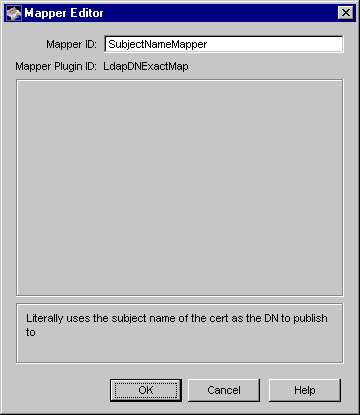
Simple Mapper
The LdapSimpleMap plug-in module implements the simple mapper. This
mapper enables you to configure a Certificate Manager to map a certificate to
an LDAP directory entry by formulating the entry's DN from components
specified in the certificate's subject name and attribute variable assertion (AVA)
constants. For more information on AVAs, see the directory documentation.
The simple mapper requires you to specify just one parameter, which is named
dnPattern. The value of dnPattern can be a list of AVA s separated by
commas. An AVA can be a variable, such as UID=$subj.UID, or a constant,
such as O=Siroe Corporation. By default, the Certificate Manager uses
mapper rules that are based on the simple mapper.
During installation, the Certificate Manager automatically creates an instance (called a mapper) of the simple mapper module. The mapper is named LdapUserCertMap (see Figure 21.2). You can use the default mapper to map various types of end-entity certificates the server will issue to their corresponding directory entries. For details, see "LdapUserCertMap Mapper".
It is important that you review and customize this mapper. For instructions on modifying mappers or creating new mappers, see "Step 3. Configure the Certificate Manager to Publish Certificates".
LdapSimpleMap Module
The Java class that implements the simple mapper is as follows:
com.netscape.certsrv.ldap.LdapSimpleMap
Figure 21.6 shows how configurable parameters for the LdapSimpleMap module are displayed in the CMS window.
Figure 21.6 Parameters defined in the LdapSimpleMap module 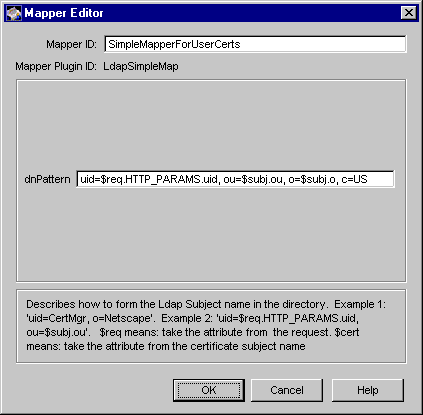
LdapUserCertMap Mapper
The rule named LdapUserCertMap is an instance of the LdapSimpleMap module. The Certificate Manager automatically creates this mapper during installation.
You can use this mapper for mapping end-user certificates to users' directory entries. The default DN pattern for locating end-user entries is as follows:
UID=$subj.UID, OU=people, O=$subj.o
The default pattern indicates that the Certificate Manager should use the UID and O values from the certificate subject name and a constant OU=people to construct the DN pattern in order to search for an entry.
For example, if the certificate subject name is
CN=Jane Doe, UID=jdoe, OU=people, O=Siroe Corporation, C=US
the Certificate Manager will construct the following DN to search the directory for the entry:
UID=jdoe, OU=people, O=Siroe Corporation
Subject Attribute Mapper
The LdapSubjAttrMap plug-in module implements the subject attribute mapper. This mapper enables you to configure a Certificate Manager to map a certificate to an LDAP directory entry by using the LDAP attribute named certSubjectDN. Note that for you to be able to use this mapper, your directory entries must include the certSubjectDN attribute.
This mapper requires you to specify the exact pattern of the subject DN because the Certificate Manager searches the directory for the certSubjectDN attribute whose value exactly matches the entire subject DN specified in the mapper configuration. For example, assume the certificate subject name is this:
UID=jdoe, O=Siroe Corporation, C=US
When searching the directory for the entry, the Certificate Manager first searches for entries that have these attributes in common
certSubjectDN=UID=jdoe, O=Siroe Corporation, C=US
and then narrows down the search to an entry that has only this:
certSubjectDN=UID=jdoe, O=Siroe Corporation, C=US
If no matching entries are found, the server returns an error and writes it to the log; see "Monitoring Logs".
LdapSubjAttrMap Module
The Java class that implements the subject attribute mapper is identified as follows:
com.netscape.certsrv.ldap.LdapCertSubjMap
Figure 21.7 shows how configurable parameters for the LdapSubjAttrMap module are displayed in the CMS window.
Figure 21.7 Parameters defined in the LdapSubjAttrMap module 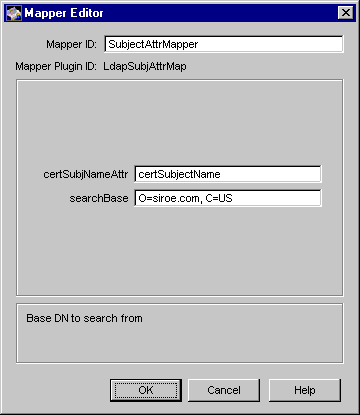
Table 21.4 describes these parameters.
|
|
Since its initial publication, the X.509 standard for CRL formats has been amended to include additional information within a CRL. Version 2, the latest version, allows you to add information as CRL extensions.
The extensions defined by ANSI X9 and ISO/IEC/ITU for X.509 v2 CRLs [X.509] [X9.55] enable you to associate additional attributes with CRLs. The Internet X.509 Public Key Infrastructure Certificate and CRL Profile (see http://www.ietf.org/rfc/rfc2459.txt) recommends a set of extensions to be used in CRLs. These extensions are called standard CRL extensions.
The standard also suggests that you can define your own extensions and include them in CRLs you issue. These extensions are called private, proprietary, or custom CRL extensions and they carry information unique to your organization or business. Keep in mind that applications may not able to validate CRLs that contain private, critical extensions, thus preventing the use of these CRLs in a general context.
Note
Some explanations in this chapter make reference to Abstract Syntax Notation
One (ASN.1) and Distinguished Encoding Rules (DER). These are specified in
the CCITT Recommendations X.208 and X.209. For a quick summary of ASN.1
and DER, see A Layman's Guide to a Subset of ASN.1, BER, and DER, which is
available at RSA Laboratories' web site (http://www.rsa.com).
Structure of CRL Extensions
A CRL extension consists of the following:
Sample CRL and CRL Entry Extensions
The following is an example of the section of a CRL containing X.509 v2 extensions. (Certificate Management System can display CRLs in human-readable format, as shown here.) As shown in the example, CRL extensions appear in sequence and only one instance of a particular extension may appear in a particular CRL; for example, a CRL may contain only one authority key identifier extension. However, CRL-entry extensions appear in appropriate entries in the CRL.
Certificate Revocation List:
Data:
Version: v2
...
Extensions:
Identifier: Authority Key Identifier
Critical: no
Key Identifier:
2c:22:c6:ae:4e:4b:91:c7:fb:4c:cc:ae:84:e8:aa:5b:46:6a:a0:ad
Extensions:
Identifier: Revocation Reason - 2.5.29.21
Critical: no
Reason: Key_Compromise
Serial Number: 0x12
Revocation Date: Tuesday, December 15, 1998 5:20:42 AM
Extensions:
Identifier: Revocation Reason - 2.5.29.21
Critical: no
Reason: CA_Compromise
Serial Number: 0x11
Revocation Date: Wednesday, December 16, 1998 4:51:54 AM
Extensions:
Identifier: Revocation Reason - 2.5.29.21
Critical: no
Reason: Key_Compromise
Serial Number: 0x10
Revocation Date: Thursday, December 17, 1998 2:37:24 AM
Extensions:
Identifier: Revocation Reason - 2.5.29.21
Critical: no
Reason: Affiliation_Changed
Serial Number: 0xA
Revocation Date: Wednesday, November 25, 1998 5:11:18 AM
...
Overview of CRL Extension Modules
To enable you issue or publish X.509 v2 CRLs (that is, CRLs with extensions), Certificate Management System provides a set of plug-in modules; each module enables you to configure the Certificate Manager to set a particular CRL or CRL-entry extension in CRLs it issues. Plug-in modules are implemented as Java classes and are registered in the CMS publishing framework. The CRL Extensions Management tab of the CMS window (Figure 21.14) lists all the modules that are registered with a Certificate Manager.
When deciding whether to add CRL extensions, keep in mind that not all applications support version 2 CRLs. Among the applications that do support extensions, not all applications will recognize every extension. For general guidelines on using these extensions in CRLs, see "Certificate Extensions" in Appendix B of Netscape Certificate Management System Installation and Deployment Guide.
Figure 21.14 Default CRL extension modules registered with a Certificate Manager 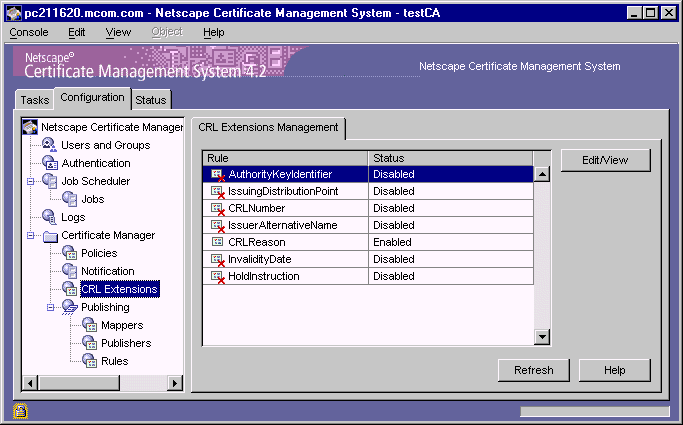
Table 21.10 lists CRL extension modules that are installed with a Certificate Manager.
For instructions on how to configure a Certificate Manager to set CRL extensions, see "Step B. Set the CRL Extensions".
AuthorityKeyIdentifier Rule
The AuthorityKeyIdentifier rule enables you to configure a Certificate Manager to set the Authority Key Identifier Extension defined in X.509 and PKIX standard RFC 2459 (see http://www.ietf.org/rfc/rfc2459.txt) in CRLs. The extension is used to identify the public key that corresponds to the private key used by a CA to sign CRLs.
The PKIX standard recommends that the CA must include this extension in all CRLs it issues. Therefore, you should consider adding this extension to all CRLs issued by the Certificate Manager. The reason for this is that in certain situations, a CA's public key may change (for example, when the key gets updated) or the CA may have multiple signing keys (either because of multiple concurrent key pairs or because of key changeover). In these cases, the CA ends up with more than one key pair. When verifying a signature on a certificate, other applications need to know which key was used in the signature. The extension, if present in a certificate, enables applications (those that can use the extension) to identify the correct key to use in situations when multiple keys exist; the extension specifies the public key to be used to verify the signature on the CRL.
For general guidelines on setting the authority key identifier extension in CRLs, see "authorityKeyIdentifier" in Appendix B of Netscape Certificate Management System Installation and Deployment Guide.
Figure 21.15 shows how configurable parameters for the AuthorityKeyIdentifier rule are displayed in the CMS window.
Figure 21.15 Parameters defined in the AuthorityKeyIdentifier rule 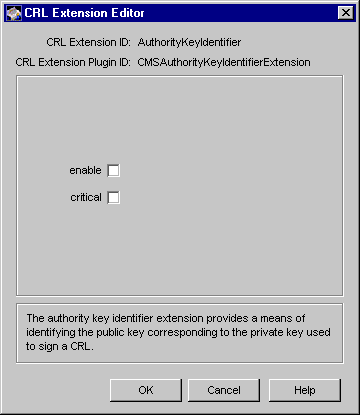
The configuration shown in Figure 21.15 specifies that the server should not set the authority key identifier extension in CRLs.
Table 21.11 describes these parameters.
CRLNumber Rule
The CRLNumber rule enables you to configure a Certificate Manager to set the CRL Number Extension defined in X.509 and PKIX standard RFC 2459 (see http://www.ietf.org/rfc/rfc2459.txt) in CRLs. This extension specifies a monotonically increasing sequence number for each CRL issued by a CA, allowing CRL users to easily determine when a particular CRL supersedes another CRL.
For general guidelines on setting the CRL number extension in CRLs, see "CRLNumber" in Appendix B of Netscape Certificate Management System Installation and Deployment Guide.
Figure 21.16 shows how the configurable parameters for the CRLNumber rule are displayed in the CMS window.
Figure 21.16 Parameters defined in the CRLNumber rule 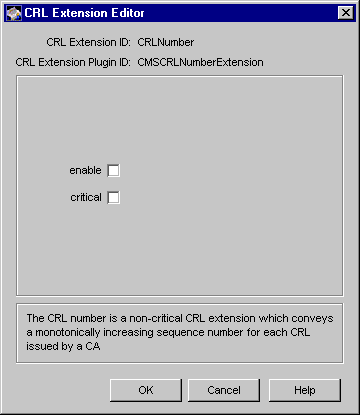
The configuration shown in Figure 21.16 specifies that the server should not set the CRL number extension in CRLs.
Table 21.12 describes these parameters.
CRLReason Rule
The CRLReason rule enables you to configure a Certificate Manager to set the CRL ReasonCode Extension defined in X.509 and PKIX standard RFC 2459 (see http://www.ietf.org/rfc/rfc2459.txt) in CRL entries. The extension is used to identify the reason for the revocation of a certificate included in the CRL.
For general guidelines on setting the CRL reason code in CRL entries, see "reasonCode" in Appendix B of Netscape Certificate Management System Installation and Deployment Guide.
The revocation reasons defined by the standard are listed in Table 21.13.
Figure 21.17 shows how the configurable parameters for the CRLReason rule are displayed in the CMS window.
Figure 21.17 Parameters defined in the CRLReason rule 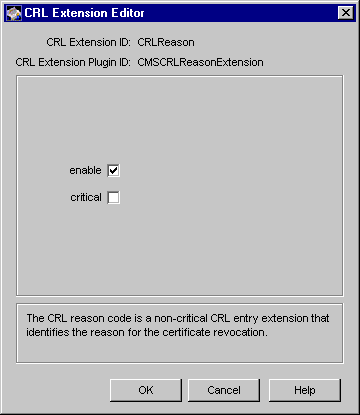
The configuration shown in Figure 21.17 specifies that the server should set the CRL reason code extension in CRL entries.
Table 21.14 describes these parameters.
HoldInstruction Rule
The HoldInstruction rule enables you to configure a Certificate Manager to set the CRL Hold Instruction Extension defined in X.509 and PKIX standard RFC 2459 (see http://www.ietf.org/rfc/rfc2459.txt) in CRLs. The extension is a non-critical CRL entry extension that is used to specify a registered instruction identifier--the identifier indicates what action the validating application should take when it encounters a certificate that has been placed on hold.
For general guidelines on setting the CRL hold instruction code in CRL entries, see "holdInstructionCode" in Appendix B of Netscape Certificate Management System Installation and Deployment Guide.
Figure 21.18 shows how the configurable parameters for the HoldInstruction rule are displayed in the CMS window.
Figure 21.18 Parameters defined in the HoldInstruction rule 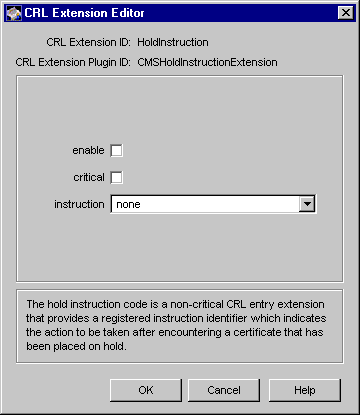
The configuration shown in Figure 21.18 specifies that the server should not set the hold instruction extension in CRL entries.
Table 21.15 describes these parameters.
InvalidityDate Rule
The InvalidityDate rule enables you to configure a Certificate Manager to set the Invalidity Date Extension defined in X.509 and PKIX standard RFC 2459 (see http://www.ietf.org/rfc/rfc2459.txt) in CRLs. The extension is a non-critical CRL entry extension that is used to specify the date on which it is known or suspected that the private key was compromised or that the certificate otherwise became invalid.
For general guidelines on setting the invalidity date extension in CRL entries, see "invalidityDate" in Appendix B of Netscape Certificate Management System Installation and Deployment Guide.
Figure 21.19 shows how the configurable parameters for the InvalidityDate rule are displayed in the CMS window.
Figure 21.19 Parameters defined in the InvalidityDate rule 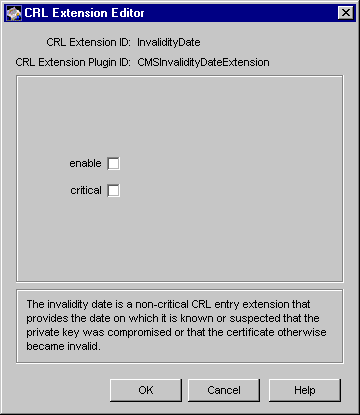
The configuration shown in Figure 21.19 specifies that the server should not set the invalidity date extension in CRL entries.
Table 21.16 describes these parameters.
IssuerAlternativeName Rule
The IssuerAlternativeName rule enables you to configure a Certificate Manager to set the Issuer Alternative Name Extension defined in X.509 and PKIX standard RFC 2459 (see http://www.ietf.org/rfc/rfc2459.txt) in CRLs. This extension enables binding of or associating alternative identities, such as Internet electronic mail address, a DNS name, an IP address, and a uniform resource indicator (URI), with the issuer of the CRL.
The IssuerAlternativeName rule enables you to associate the following identities with a CRL issuer, by including them in the extension:
For general guidelines on setting the issuer alternative name extension in CRLs, see "issuerAltName" in Appendix B of Netscape Certificate Management System Installation and Deployment Guide.
Figure 21.20 shows how configurable parameters for the IssuerAlternativeName rule are displayed in the CMS window.
Figure 21.20 Parameters defined in the IssuerAlternativeName rule 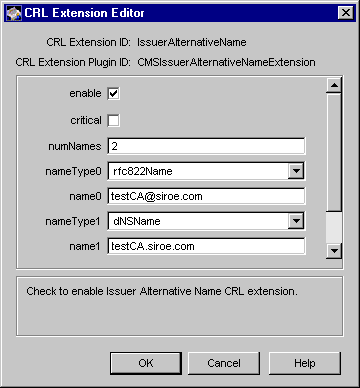
The configuration shown in Figure 21.20 specifies that the server should not set the issuing point extension in CRLs.
Table 21.17 describes these parameters.
IssuingDistributionPoint Rule
The IssuingDistributionPoint rule enables you to configure a Certificate Manager to set the Issuing Distribution Point Extension defined in X.509 and PKIX standard RFC 2459 (see http://www.ietf.org/rfc/rfc2459.txt) in CRLs. The CRL issuing point extension enables you to specify a pointer to a particular CRL and to include additional information about the CRL at that location--whether it covers revocation of end-entity certificates only, CA certificates only, or revoked certificates that have a limited set of reason codes.
By default, the pointer can be in either of these forms:
Optionally, each issuing point may contain a set of reason flags, indicating what revocation reasons are covered by the CRL at the specified location. Note that you can modify the rule to support any name form by making the appropriate changes to the sample code provided for this purpose. The sample code is located here:
<server_root>/cms_sdk/samples/CRLs/IssuingDistributionPoint
For general guidelines on setting the issuing distribution point extension in CRLs, see "issuingDistributionPoints" in Appendix B of Netscape Certificate Management System Installation and Deployment Guide.
Figure 21.21 shows how configurable parameters for the IssuingDistributionPoint rule are displayed in the CMS window.
Figure 21.21 Parameters defined in the IssuingDistributionPoint rule 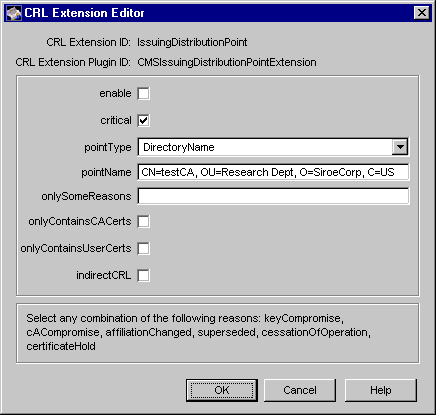
The configuration shown in Figure 21.21 specifies that the server should not set the issuing point extension in CRLs.
Table 21.18 describes these parameters.
Table 21.18 Description of parameters defined in the IssuingDistributionPoint rule
Parameter
| Description
|
|---|
enable
| Specifies whether the rule is enabled or disabled. Check the box to enable the rule. Uncheck the box to disable the rule (default).
|
critical
| Specifies whether the extension should be marked critical or noncritical in CRLs issued by the server. Check the box if you want the server to mark the extension critical (default). Uncheck the box if you want the server to mark the extension noncritical.
|
pointType
| Specifies the type (for example, URI) of the issuing distribution point.
Permissible values: By default, DirectoryName and URI.
Example: URI
|
pointName
| Specifies the name of the issuing distribution point. The name of the distribution point can be in any of the following formats:
Permissible values: Depends on the value specified for the pointType parameter.
Example:
|
onlySomeReasons
| Specifies the reason codes associated with the distribution point.
Permissible values: A combination of reason codes--unspecified, keyCompromise, cACompromise, affiliationChanged, superseded, cessationOfOperation, certificateHold, and removeFromCRL--separated by commas. Leave field blank if the distribution point contains revoked certificates with all reason codes or if you don't want to set this field (default).
Example: unspecified, keyCompromise, cessationOfOperation
|
onlyContainsCACerts
| Specifies whether the distribution point contains only revoked CA certificates. Check the box if the distribution point contains CA certificates only. Uncheck the box if the distribution point contains all types of revoked certificates (default).
|
onlyContainsUserCerts
| Specifies whether the distribution point contains only revoked user certificates. Check the box if the distribution point contains user certificates only. Uncheck the box if the distribution point contains all types of certificates (default).
|
indirectCRL
| Specifies whether the distribution point contains an indirect CRL. Check the box if the distribution point contains an indirect CRL. Uncheck the box if the distribution point doesn't contain an indirect CRL (default).
|
|